Cyber Security News
Medium
357
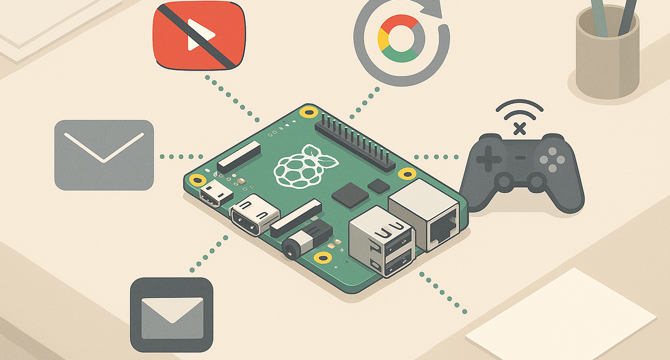
Image Credit: Medium
4 Surprising Things Pi-hole Blocks (Besides Just Ads)
- Pi-hole is a tool that blocks ads and trackers on your network, but it can also disrupt other services.
- Pi-hole can stop YouTube from remembering watched videos, Google Chrome updates on Ubuntu, Gmail syncing on iPhone, and sponsored results in Google Search.
- To fix these issues, users need to whitelist specific domains in Pi-hole, such as those used by YouTube, Google Chrome, Gmail, and sponsored results.
- For games relying on ads, users can use the Pi-hole query log to identify and selectively whitelist blocked domains.
Read Full Article
21 Likes
Siliconangle
339

Image Credit: Siliconangle
Commvault expands post-quantum cryptography with support for HQC algorithm
- Commvault Systems Inc. introduces new post-quantum cryptography capabilities to safeguard data from emerging quantum security threats.
- The PQC capabilities protect highly sensitive, long-term data from potential cyber threats posed by quantum computing advancement.
- Commvault supports quantum-resistant encryption standards and introduces a cryptographic agility framework for rapid threat response via the Commvault Cloud platform.
- The expanded post-quantum cryptography capabilities, including support for the NIST-recommended HQC algorithm, are immediately available to all Commvault Cloud customers running software version CPR 2024 (11.36) and later.
Read Full Article
20 Likes
Managedmethods
433

Image Credit: Managedmethods
Cost-Effective Ways to Boost Cybersecurity in Rural Schools
- About 97% of the country is classified as rural, where half of all US school districts are located.
- Digital skills are essential for students, but many in rural areas lack reliable high-speed internet access.
- Connectivity issues in rural areas impact student engagement, retention, and outcomes in online learning.
- Rural school districts face challenges with cyberattacks due to limited expertise and funding, requiring practical actions for cybersecurity.
Read Full Article
26 Likes
Siliconangle
178

Image Credit: Siliconangle
Red Sift expands Cisco partnership with addition of Brand Trust platform
- Red Sift Ltd. expands partnership with Cisco Systems Inc. by adding its Brand Trust platform to the Cisco security portfolio.
- The Brand Trust platform by Red Sift helps in detecting and mitigating impersonation threats on a large scale by monitoring the internet for domains mimicking legitimate brands.
- This partnership allows Cisco customers to broaden their protection beyond owned domains, providing defense against lookalike domains and other impersonation threats that traditional security measures might miss.
- Red Sift, a VC-backed startup, has raised $69.8 million in three rounds, with investors including Highland Europe (Technology) LLP, Sands Capital Management, and others.
Read Full Article
10 Likes
Tech Radar
304

Image Credit: Tech Radar
Friendly fire: Hackers target their own with fake malware and gaming cheats
- Sophos uncovered a major hacking operation targeting other hackers and game cheaters.
- Sophos identified Sakura RAT as a backdoored malware variant targeting newbie threat actors and individuals seeking game cheats.
- More than a hundred backdoored GitHub projects were discovered, with 111 containing Sakura RAT designed to target wannabe hackers.
- The campaign, started in 2024, was successful in targeting newbies who were less likely to detect the malicious intent behind the projects.
Read Full Article
18 Likes
Securityaffairs
353

Image Credit: Securityaffairs
OpenAI bans ChatGPT accounts linked to Russian, Chinese cyber ops
- OpenAI banned ChatGPT accounts connected to Russian and Chinese hackers engaging in malicious activities, including malware development, social media abuse, and U.S. satellite tech research.
- Accounts tied to Russian-speaking threat actors and two Chinese nation-state actors were blocked, with the Russian group operating under the cyber operation called ScopeCreep, focusing on stealthy malware distribution and C2 infrastructure.
- OpenAI collaborated with industry partners to detect and ban these malicious accounts early on, preventing widespread impact and disrupting operations like ScopeCreep, Helgoland Bite, Sneer Review, VAGue Focus, VIXEN PANDA, KEYHOLE PANDA, and Operation Uncle Spam.
- The report highlights the varied global origins of such malicious operations, with notable cases possibly originating from China, in addition to instances from countries like Cambodia, the Philippines, Russia, and Iran.
Read Full Article
21 Likes
Siliconangle
375

Image Credit: Siliconangle
Guardz collects $56M to bring enterprise-grade cybersecurity to smaller businesses
- Guardz Cyber Ltd. secures $56 million in Series B funding to help small and medium-sized businesses bolster their cybersecurity resilience.
- The funding round was led by ClearSky, with participation from Phoenix Financial and existing investors, bringing Guardz's total raised amount to $84 million.
- Guardz has shifted its focus to working with managed services providers to offer them a comprehensive cybersecurity platform aimed at SMBs.
- The company's AI-powered managed detection and response service assists MSPs in protecting cloud, data, identities, and endpoints by detecting and responding to threats efficiently.
Read Full Article
22 Likes
Medium
152
Image Credit: Medium
How Criminals Use Dead Drops and Covert Channels on the Dark Web
- Criminals and whistleblowers utilize 'dead drops' and covert channels on the Dark Web to exchange information and illicit goods without real-time communication.
- The concept of dead drops is rooted in espionage, where secret messages were left in physical locations during the Cold War to avoid direct contact between sender and receiver.
- On the Dark Web, this concept is adapted digitally. For instance, a seller might upload stolen documents to an encrypted server and share the access path on a message board or chat platform for the buyer to retrieve without direct interaction.
- To ensure anonymity and security, the files on such servers may have time limitations or auto-delete features after a set period or number of downloads.
Read Full Article
9 Likes
Medium
219

Image Credit: Medium
The Daily Tech Digest: 09 June 2025
- The field of Artificial Intelligence and Machine Learning sees advancements in model evaluation, application across sectors, and strategic investments driving growth.
- OpenAI's Advanced Voice Translation enhances cross-lingual communication with more natural interactions.
- NVIDIA supports UK AI vision to focus on infrastructure, research, and talent development for strategic growth.
- Concerns rise over self-evolving malicious AI systems designed by hackers, posing future cybersecurity threats.
- OpenAI bans hacker accounts linked to malware creation, showcasing the dual-use nature of AI in cybercrime.
- AI prompts aid in generating 'unicorn ideas' for startups, emphasizing prompt engineering for innovation.
- Legal implications arise as UK court warns against fake AI citations, highlighting the importance of verifying AI outputs.
- Indiana Pacers use Azure AI for real-time captions to enhance arena accessibility for all fans.
- Cybersecurity challenges like self-evolving malicious AI and Chrome extensions stealing data emphasize the need for robust defenses.
- Market volatility surfaces as Trump-Musk feud impacts Tesla and TrumpCoin's market values significantly.
Read Full Article
13 Likes
Medium
433

Image Credit: Medium
Win Big With These GRC Frameworks
- Keeping up with compliance can be overwhelming, but having the right GRC frameworks in place is crucial for businesses of all sizes.
- Key GRC frameworks like ISO 27001, SOC 2, NIST CSF, and PCI DSS help businesses establish trust, resilience, and data protection.
- Compliance with GDPR, CCPA/CPRA, HIPAA, and PIPEDA is essential for respecting user privacy and avoiding penalties.
- Frameworks like ISO 22301 and DORA help businesses maintain operational continuity and digital resilience during crises.
- The EU AI Act and OECD AI Guidelines set standards for responsible AI use, emphasizing transparency and ethical AI governance.
- NIST AI RMF and ISO/IEC 42001 provide guidance on managing AI risks and ensuring ethical and safe AI deployment.
- Choosing the right frameworks involves understanding industry regulations, data practices, client requirements, and risk mitigation strategies.
- Aligning multiple frameworks can streamline compliance efforts and enhance overall organizational resilience.
- Ultimately, a well-implemented compliance framework serves as a growth catalyst, rather than a hindrance, for businesses.
- Subscribe to the GRCMana Newsletter for expert insights and tools to navigate evolving compliance landscapes successfully.
Read Full Article
26 Likes
Securityaffairs
299
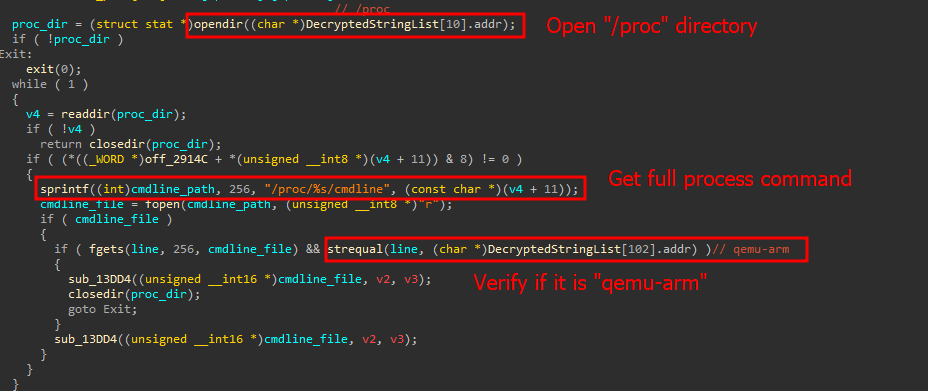
Image Credit: Securityaffairs
New Mirai botnet targets TBK DVRs by exploiting CVE-2024-3721
- A new variant of the Mirai botnet exploits CVE-2024-3721 to target DVR systems.
- The variant uses a command injection vulnerability in TBK DVR-4104 and DVR-4216 devices to execute malicious commands.
- This Mirai variant includes new features like RC4 string encryption and anti-virtual machine checks.
- Over 50,000 exposed DVRs have been found as potential targets in countries like China, India, Egypt, Ukraine, Russia, Turkey, and Brazil.
Read Full Article
18 Likes
Dev
123

Image Credit: Dev
Why Does My SSL Site Return the Wrong Certificate When Accessed via IP?
- When accessing an SSL site via IP instead of domain, it may return a different certificate, often the default one.
- The issue occurs because the TLS handshake happens before the server receives the HTTP request, and IP addresses are not supported in Server Name Indication (SNI).
- When no SNI is provided, SafeLine falls back to the default virtual host certificate or its built-in 404 fallback site certificate.
- To avoid this problem, always access SSL sites via the domain name and understand the role of SNI in certificate negotiation to prevent SSL errors.
Read Full Article
7 Likes
Pymnts
139

Image Credit: Pymnts
51% of Shoppers Put Convenience First When Choosing Payments
- Payments optimization is crucial for maintaining a competitive edge in the digital landscape.
- Focus on three key pillars - choice, confidence, and convenience for peak payment performance.
- Consumer expectations include choice in payment methods, transaction speed, security, and convenience.
- Offering diverse payment options, balancing security and convenience, and providing perks are essential for businesses to optimize payments.
Read Full Article
8 Likes
The Register
53

Image Credit: The Register
Are technologists a threat to doing business securely?
- Cybersecurity leaders face internal conflicts between technology and human risk management (HRM) within their organizations, leading to security vulnerabilities.
- Technologists prioritize control over solutions, while security leaders advocate for robust defenses that address behavioral vulnerabilities.
- Human risk management (HRM) is often undervalued in cybersecurity strategies, with executives and technologists favoring innovative tech solutions over addressing human error.
- Most data breaches result from human error, such as phishing attacks and weak password practices, highlighting the importance of HRM in cybersecurity.
- The bias of technologists towards familiar tools can hinder a holistic security approach that considers human vulnerabilities.
- Leaders need to balance technology investments with HRM initiatives to effectively protect organizations from cyber threats.
- Consulting firms may influence leaders to prioritize high-margin tech solutions over necessary HRM practices, perpetuating a technological bias.
- Security leaders must challenge themselves to integrate human and technological controls for comprehensive cybersecurity management.
- NIST's Cybersecurity Framework and ISO 27001 offer guidance on merging HRM with technology in cybersecurity initiatives to create a more secure environment.
- Industry-specific guides and HRM platforms can aid executives in fostering a security culture by prioritizing both human and technological security measures.
Read Full Article
3 Likes
Securityaffairs
0

Image Credit: Securityaffairs
BadBox 2.0 botnet infects millions of IoT devices worldwide, FBI warns
- BadBox 2.0 malware infects millions of IoT devices globally, forming a botnet for cyber criminal activities, as warned by the FBI.
- FBI issues a Public Service Announcement (PSA) highlighting the use of the BADBOX 2.0 botnet by cybercriminals to exploit IoT devices, predominantly made in China.
- The malware gains unauthorized access to devices, targeting Android devices and compromising home networks to become part of the BADBOX 2.0 botnet for illicit purposes.
- FBI advises checking IoT devices for compromise signs, disconnecting suspicious ones, monitoring network traffic, avoiding unofficial app stores, and promptly patching vulnerabilities to mitigate risks.
Read Full Article
Like
For uninterrupted reading, download the app