Cyber Security News
Medium
125

Image Credit: Medium
Sextortion & Teens: Why This Topic Should Be On Every Parent’s Radar Now & Forever
- Sextortion and teens is emphasized as a crucial topic for parents to be aware of now and in the future.
- Parents are encouraged to engage in open discussions with their children about the challenges they may face, especially in the digital age.
- It is highlighted that providing children with the necessary tools and knowledge to keep themselves safe is essential for their well-being.
- The importance of creating a nonjudgmental environment for children to communicate openly about tough topics and guiding them through their online experiences is underlined.
Read Full Article
7 Likes
Medium
390

Image Credit: Medium
Netflix Docuseries “Web of Lies: Death by SWAT” Discussion Questions
- Netflix's docuseries 'Web of Make Believe: Death, Lies, and the Internet' delves into the dangers of online gaming culture, showcasing how extremism in gaming communities can lead to real-world extremism.
- The episode titled 'Death by SWAT' explores the disturbing trend of swatting, where individuals call law enforcement with false threats, resulting in SWAT teams being deployed to innocent targets.
- The focus is on Tyler Barriss, a notorious 'swatter' whose actions culminated in the fatal swatting of an innocent man, Andrew Finch, following a dispute over a video game wager.
- The consequences of swatting are highlighted through legal actions taken against those involved, shedding light on the unforeseen dangers of digital interactions and the need to address such harmful practices.
Read Full Article
23 Likes
Hackernoon
175

Image Credit: Hackernoon
Cybersecurity Essentials For Startups: 8 Tools to Scale Safely (and Avoid a Breach)
- Many cybersecurity tools are not startup-friendly due to being expensive or complex, but 43% of cyberattacks target small businesses.
- A list of essential and startup-friendly cybersecurity tools that can protect businesses without overwhelming them has been compiled.
- Firewalls act as gatekeepers for networks, blocking malicious traffic and ensuring network security. Recommended firewall tools include Netgate pfSense, Bitdefender GravityZone, and Sophos XG Firewall.
- Antivirus software is crucial for scanning, blocking, and cleaning malicious software. Some recommended options are McAfee Total Protection, Norton Small Business, and Trend Micro Worry-Free Services.
- Multi-Factor Authentication (MFA) adds an extra layer of security, preventing unauthorized access even if passwords are compromised. Google Authenticator, Duo Security, and Microsoft Authenticator are top MFA tools.
- Virtual Private Networks (VPNs) encrypt internet connections, essential for protecting data on public WiFi. ExpressVPN, OpenVPN, and ProtonVPN are recommended VPN tools for startups.
- Vulnerability scanners, like Rapid7 InsightVM, OpenVAS, and Tenable Nessus, are crucial for identifying weaknesses and potential security threats within systems.
- Encryption tools, such as FileVault, Tresorit, and BitLocker, protect sensitive data by encoding it, meeting compliance requirements and ensuring privacy.
- Password managers like 1Password, Bitwarden, and Dashlane assist in storing and managing secure passwords, simplifying login processes.
- Backup tools like Acronis Cyber Protect, Google Drive, and Backblaze are essential for creating copies of important data to prevent data loss in case of device failure or cyber attacks.
- Cybersecurity forms a critical part of the foundation for startups, and having the right tools in place is essential to protect business assets and data.
Read Full Article
10 Likes
Tech Radar
287

Image Credit: Tech Radar
Over 4 billion user records leaked in "largest breach ever" - here's what you need to know
- A massive database containing roughly 4 billion records, including personal information, was found online by cybersecurity researchers.
- The dataset primarily includes Chinese customer and user data, suggesting a surveillance effort targeting Chinese citizens.
- The information in the leak could be exploited for social engineering attacks, identity theft, fraud, or blackmail.
- The dataset was quickly taken down, but the extent of exposure raises concerns about privacy and security, with the leak surpassing previous massive data breaches.
Read Full Article
17 Likes
Securityaffairs
188

Image Credit: Securityaffairs
Russia-linked threat actors targets Ukraine with PathWiper wiper
- A Russia-linked threat actor targeted a critical infrastructure organization in Ukraine with a destructive malware named PathWiper, according to Cisco Talos researchers.
- The attackers utilized a legitimate endpoint administration tool to deploy the PathWiper wiper, indicating access to the administrative console.
- PathWiper is a destructive malware that overwrites disk artifacts and files with random data, targeting NTFS structures and dismounting volumes before wiping.
- Russia-linked APT groups have carried out multiple wiper campaigns against critical organizations in Ukraine, using various wipers in attacks.
Read Full Article
11 Likes
Tech Radar
403

Image Credit: Tech Radar
86 million AT&T records leaked online - and this time they’re decrypted, so be on your guard
- AT&T is investigating a leak of data, including 88 million customer records, with 86 million unique records, potentially exposing personal information such as social security numbers and contact details.
- The breach is concerning as it includes 44 million plaintext social security numbers, increasing the risk of fraud and identity theft for the affected individuals.
- There is speculation that the leaked data could be a re-release of an earlier breach or a combination of multiple AT&T breaches, with similarities to the 2024 breach that utilized the Snowflake vulnerability.
- Considering the sensitive nature of the exposed data, individuals affected by the breach are advised to consider identity theft protection and credit monitoring services.
Read Full Article
24 Likes
Socprime
237
Image Credit: Socprime
IOC Intelligence to Google SecOps: Automated Conversion with Uncoder AI
- Uncoder AI feature processes structured threat reports in IOC format to create actionable detection logic for Google SecOps.
- It automates the transformation of threat intelligence data into detection rules, enhancing efficiency for Google SecOps (UDM) syntax.
- Uncoder AI uses NLP and structured parsing to identify key IOC elements, understand campaign behaviors, and map attributes to Google SecOps Query.
- The innovation lies in automated extraction of observables, contextualization of threats, and quick translation into multiple platforms, offering accelerated rule creation and cross-platform compatibility.
Read Full Article
14 Likes
Secureerpinc
246

Image Credit: Secureerpinc
Protecting Your Data in the Quantum Age
- Quantum computing poses a risk to traditional encryption methods, urging businesses to adopt quantum data protection.
- Quantum computing leverages qubits for faster processing, challenging existing encryption protocols like SSH, HTTPS, and IPsec VPNs.
- New quantum data protection techniques include Quantum Key Distribution, Quantum-Safe Cryptography, and Post-Quantum Encryption to combat cyber threats.
- It is crucial for businesses to enhance cybersecurity measures like training employees and implementing multi-factor authentication to preempt data breaches.
Read Full Article
14 Likes
TechDigest
215

Image Credit: TechDigest
NatWest bank hit by major IT outage
- NatWest bank experienced a significant IT outage, affecting the mobile banking app and preventing thousands of customers from accessing their accounts.
- Over 3,000 problems were reported on the outage-tracking site Downdetector, with customers facing difficulties since 09:10 GMT.
- While online banking was claimed to be unaffected, some customers reported issues with the service; however, card payments remained operational.
- The IT outage left customers unable to conduct essential transactions, prompting frustration and concerns over missed payments and late fees.
Read Full Article
12 Likes
Tech Radar
4

Image Credit: Tech Radar
Anthropic is building new Claude AI models specifically for US national security designed to handle classified information
- Anthropic has developed several US national security-oriented models.
- The models, named “Claude Gov”, are tailored to handle classified information more effectively and are used for strategic planning and intelligence analysis.
- Many AI developers, including OpenAI and Meta, are offering AI models for US government use, with Anthropic collaborating with Palantir on government projects.
- The new Claude Gov models have advanced capabilities, such as proficiency in critical languages and cybersecurity understanding, enhancing their utility for national security purposes.
Read Full Article
Like
Socprime
125

Image Credit: Socprime
CVE-2025-5419 Vulnerability: New Google Chrome Zero-Day Actively Exploited in the Wild
- Google Chrome has identified a new zero-day vulnerability (CVE-2025-5419) actively exploited in the wild, allowing remote attackers to trigger heap corruption via malicious HTML pages.
- The vulnerability affects Chrome versions earlier than 137.0.7151.68 and poses serious security risks to users worldwide.
- Google has issued emergency patches to address the CVE-2025-5419 vulnerability, confirming active exploitation and urging users to apply updates for protection.
- This marks the third Chrome zero-day vulnerability exploited in 2025, emphasizing the need for proactive defense strategies and comprehensive security measures to counter evolving threats.
Read Full Article
7 Likes
Idownloadblog
13

Image Credit: Idownloadblog
Cellebrite acquiring Corellium virtualization company for $200M, raising eyebrows of privacy advocates
- Israeli digital forensics company Cellebrite has acquired Corellium, a renowned virtualization services company, for $200 million.
- Corellium, founded by former iPhone jailbreak developer David Wang, offers tools for cybersecurity and hacking, allowing testing of exploits without physical hardware.
- The acquisition raises concerns among privacy advocates, as it combines top digital forensics and iPhone virtualization firms, potentially aiding law enforcement agencies in accessing Apple devices.
- The merger could expedite the development of a product called Mirror, enabling law enforcement to clone crime devices virtually, impacting court cases but the impact on jailbreak developers' access to Corellium tools remains unclear.
Read Full Article
Like
Tech Radar
31

Image Credit: Tech Radar
OpenAI says it disrupted at least 10 malicious AI campaigns already this year
- OpenAI has disrupted over 10 malicious campaigns utilizing ChatGPT in 2025, involving employment scams and influence operations, with state-sponsored actors from China, Russia, and Iran involved.
- Four of the campaigns, including 'Sneer Review' and 'Helgoland Bite', were linked to China and Russia, focusing on social engineering, covert influence operations, and generating content to discredit opposition.
- The campaigns involved tactics like spamming critical comments and generating divisive content to widen political divides in the US, with OpenAI banning multiple ChatGPT accounts associated with targeted influence campaigns.
- OpenAI's actions highlight the misuse of AI in spreading misinformation online and the importance of discerning genuine human engagement from AI-generated content.
Read Full Article
1 Like
Medium
305

Image Credit: Medium
How LLM-as-a-Judge Evaluation Improves Threat Intelligence
- LLM-as-a-Judge evaluation with a scoring system improved threat intelligence analysis.
- Threat intelligence profiles are now assessed across five critical dimensions with iterative improvements.
- Using a web search tool repeatedly helped eliminate fake URL links, improving source authenticity validation.
- Strategic keyword usage and iterative scoring led to significant quality enhancements in generating trustworthy threat intelligence reports.
Read Full Article
18 Likes
Securityaffairs
224
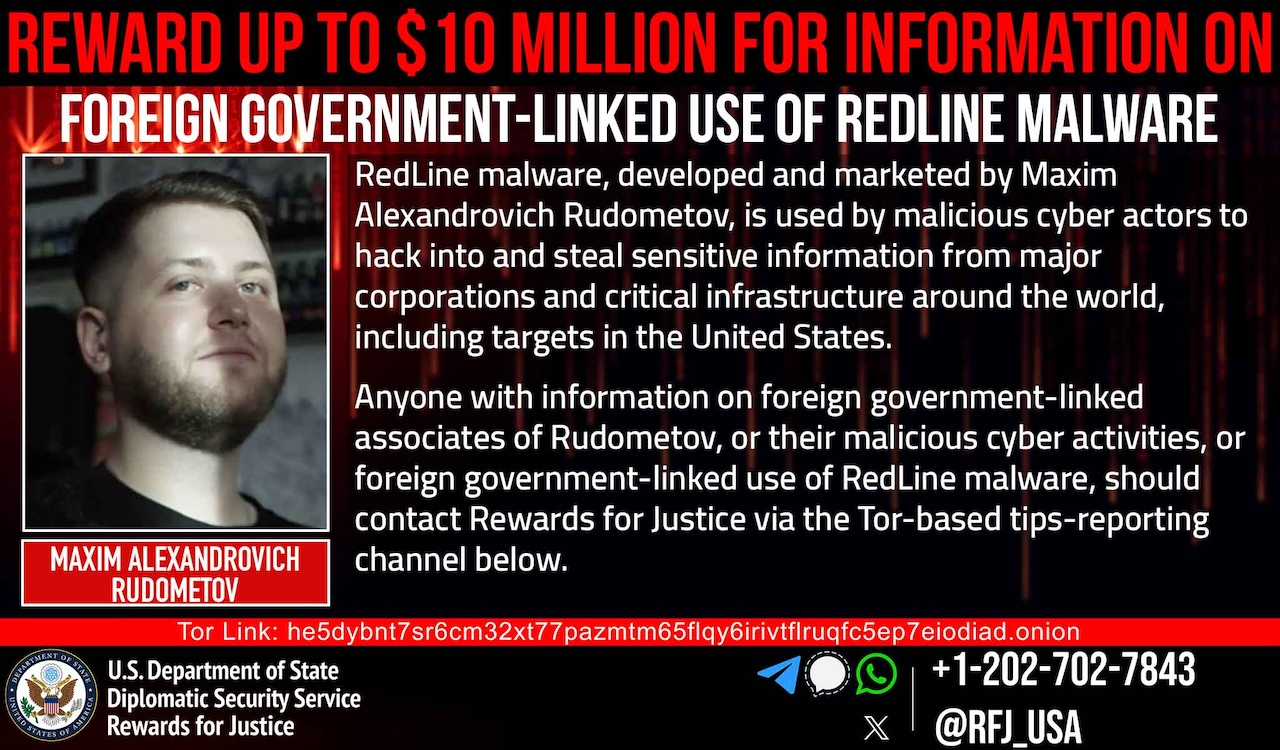
Image Credit: Securityaffairs
U.S. Offers $10M bounty for info on RedLine malware creator and state hackers
- The U.S. is offering up to $10 million for information on state hackers tied to the RedLine malware and its creator, Maxim Rudometov, associated with attacks on U.S. infrastructure.
- Maxim Rudometov, a Russian national, developed the information stealer malware RedLine and is being sought by U.S. authorities for cyber operations on critical infrastructure in the U.S.
- The reward is part of the US Department of State's Rewards for Justice program aiming to deter foreign government hackers targeting U.S. entities.
- An international operation led by Eurojust dismantled the RedLine and META malware infrastructure, affecting millions of victims worldwide and led to arrests in Belgium, seizure of servers in the Netherlands, and cooperation from multiple countries.
Read Full Article
13 Likes
For uninterrupted reading, download the app