Devops News
Dev
395
Image Credit: Dev
Affordable AI Cloud Deployment Tools for Indie Devs and Small Teams
- Affordable AI cloud deployment tools are becoming accessible for indie developers and small teams.
- These tools automate cloud deployment using AI to make decisions about the cloud environment.
- Top affordable AI cloud deployment tools for indie devs: Kuberns, Railway, Qovery, Render.
- These tools provide simplified and faster deployment processes with features like auto-configuration, one-click deployment, and smart scaling.
Read Full Article
23 Likes
Dev
284

Image Credit: Dev
🚀 Spinning Up Containers with Terraform + Docker!
- Provisioned an NGINX container using Terraform with the Docker provider
- Infrastructure as Code (IaC) makes container management efficient, consistent, and scalable
- Used Terraform to pull the official NGINX image and create a container named 'tutorial' exposed on port 8000
- This setup showcases the power of IaC in streamlining containerized development
Read Full Article
17 Likes
Dev
347

Image Credit: Dev
The "Iron Triangle" in Software Projects: Balancing Scope, Time, and Cost Without Compromising Quality
- Software development teams strive to balance scope, time, cost, and quality in projects, often depicted by the 'Iron Triangle' framework.
- The Iron Triangle comprises scope, time, and cost as primary constraints in project management.
- In the classic interpretation, scope was fixed while resources and time were variable, leading to trade-offs between quality, speed, and cost.
- Modern challenges to the Iron Triangle include the rise of Agile methodologies, quality as a crucial constraint, increased complexity, and interdependence in projects.
- Strategies for balancing the Iron Triangle include prioritizing constraints based on project context, implementing flexible scope management, adopting Agile planning techniques, and leveraging technology for automation.
- Forward-thinking organizations are moving beyond the 'Pick Two' dilemma by aligning goals, emphasizing transparency, and integrating advanced technologies.
- Case studies like McDonald's IT operations transformation showcase successful simultaneous optimization of scope, time, and cost.
- Teamcamp offers project management solutions to help teams navigate the Iron Triangle effectively by addressing scope, time, and cost management challenges.
- Practical tips for developers within the Iron Triangle include focusing on technical excellence, proactive communication, incremental delivery, and continuous improvement.
- Modern software teams understand the importance of optimizing across all dimensions of the Iron Triangle to deliver high-quality software efficiently.
Read Full Article
20 Likes
Dev
40

Image Credit: Dev
🧠 Kubernetes Learning Path (in VS Code)
- Set up your environment by installing VS Code and necessary extensions.
- Get hands-on with Kubernetes basics, including core concepts and mini-projects.
- Explore intermediate topics such as volumes, probes, namespaces, and resource limits/requests.
- Learn about Helm charts, packaging and deploying applications using Helm CLI.
- Dive into advanced topics like ingress controllers, network policies, RBAC, and custom resources.
Read Full Article
2 Likes
Discover more
- Programming News
- Software News
- Web Design
- Open Source News
- Databases
- Cloud News
- Product Management News
- Operating Systems News
- Agile Methodology News
- Computer Engineering
- Startup News
- Cryptocurrency News
- Technology News
- Blockchain News
- Data Science News
- AR News
- Apple News
- Cyber Security News
- Leadership News
- Gaming News
- Automobiles News
Dev
194
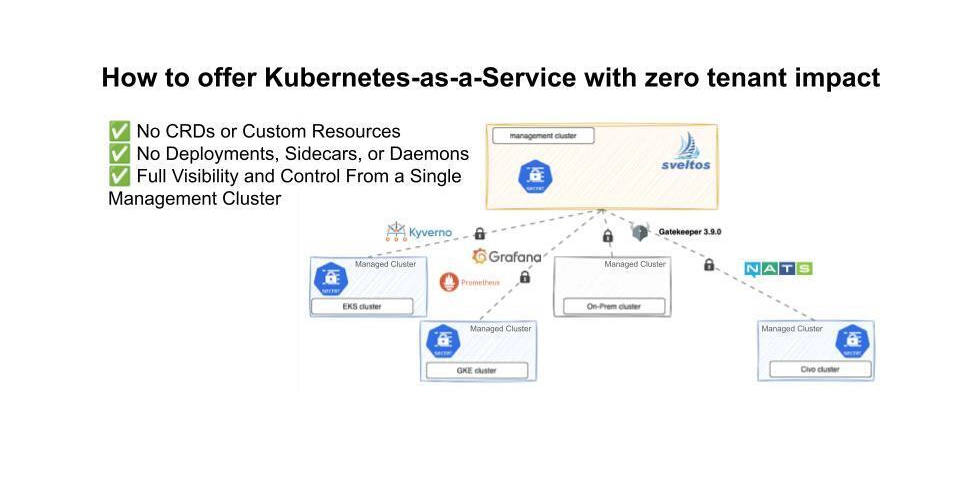
Image Credit: Dev
Your Kubernetes clusters deserve to stay clean. Your platform deserves full control. Now you can have both.
- Sveltos introduces Agentless Mode to offer clean Kubernetes clusters without installing any controllers or CRDs within customer environments.
- The new Agentless Mode by Sveltos enhances centralized management, configuration drift detection, and event monitoring without leaving any traces on managed clusters.
- Customers expect clean managed clusters free of tooling interference, driving the need for invisible control planes like the Agentless Mode.
- Sveltos now deploys drift detection and event monitoring components in the management cluster without deploying anything into the managed cluster.
- The new architecture ensures no CRDs or custom resources, deployments, sidecars, or daemons in managed clusters, offering full visibility and control from a single management cluster.
- Benefits include clean isolated clusters, lower operational risk, better performance, observability, and smarter scaling for platform engineers.
- Sveltos replaces managing multiple small operators with a unified control plane for simplified operational footprint, full control, minimized dependencies, and scalable management.
- The new Agentless Mode enhances precision, security, and elegance while retaining features like ClusterProfiles, drift detection, configuration snapshots, and event-driven automation.
- Cleaner clusters, happier customers, and stronger platforms are key outcomes of adopting the Sveltos Agentless Mode for platform engineering.
- The production-ready Agentless Mode is open source and available in the latest Sveltos version for scaling platform needs, offering installation guides and support options.
Read Full Article
11 Likes
Dev
307

Image Credit: Dev
Understanding Types of Users in Linux
- Linux is a multi-user operating system with three main types of users: root user (superuser), regular users (standard accounts), and system users (service accounts).
- The root user has unlimited access to the system and is used for administrative tasks.
- Regular users can only access their own files and directories, while system users manage background services.
- Understanding user types is important for access control, security, and maintaining system stability.
Read Full Article
18 Likes
Dev
352

Image Credit: Dev
Still Shipping 1GB Docker Images? Here’s How to Crush Them in Half an Hour
- Many Docker images are bloated with unnecessary components, causing slow CI/CD pipelines and increased security risks.
- Reducing Docker image size is crucial in 2025 due to Fargate cost limits, CI/CD bottlenecks, and supply chain risks.
- You can shrink Docker images from 1GB to under 100MB in less than 30 minutes using various techniques.
- Quick wins include using official Slim or Alpine base images, cleaning up unnecessary files, and utilizing multi-stage builds.
- Advanced techniques involve optimizing Docker layers, utilizing images like scratch or Distroless, and leveraging BuildKit for faster builds.
- Tools like Dive, DockerSlim, and BuildKit help visualize, analyze, and reduce Docker image sizes efficiently.
- Dive allows you to inspect each layer of your image, while DockerSlim helps shrink images by removing unused components.
- Using tools like BuildKit enables smarter, faster builds with features like inline secrets and better caching.
- Real-world examples demonstrate significant image size reductions with simple optimizations, leading to faster deployments and cost savings.
- By following best practices, cleaning up Dockerfiles, and utilizing efficient tools, developers can drastically reduce image sizes and improve deployment speed.
- Taking small steps to optimize Docker images can lead to substantial benefits in terms of performance, security, and efficiency.
Read Full Article
21 Likes
Dev
248

Image Credit: Dev
The Only Docker Guide You’ll Ever Need (Beginner to Expert)
- Docker simplifies packaging apps with code, libraries, and tools into portable units called containers.
- Containers are lightweight, fast, and use less system resources compared to virtual machines.
- Key Docker commands include docker ps, docker stop, docker images, and docker exec.
- Understanding the difference between images and containers is crucial for Docker proficiency.
- Dockerfiles are used to create custom Docker images, with layers aiding in efficient image building.
- Best practices include using .dockerignore, tagging images, and avoiding running containers as root.
- Volumes in Docker ensure data persistence, networks facilitate container communication, and Docker Compose simplifies multi-service app management.
- Developers utilize Docker for consistent environments, CI/CD pipelines, and real-time testing.
- Multi-stage builds, Docker Swarm, Kubernetes, security practices, and tools like Trivy are advanced Docker concepts.
- Common beginner mistakes include using :latest tags, forgetting .dockerignore, running containers as root, and not cleaning up regularly.
Read Full Article
14 Likes
Dev
411

Image Credit: Dev
Every Developer Needs to Self-Host
- Self hosting can teach developers valuable skills beyond just coding, like operational responsibilities and networking fundamentals.
- By self hosting, developers learn about service maintenance, data persistence, port management, and system operations.
- Networking skills, security considerations, and DevOps concepts are also gained through self hosting experiences.
- Self hosting fosters confidence in troubleshooting real-world problems and understanding production environments.
- Engaging in self hosting can lead to unexpected career paths in cloud infrastructure engineering or related fields.
- Starting with small self hosting projects using tools like n8n, Uptime Kuma, or Postgres can be both educational and practical.
- The experience gained from self hosting can provide developers with valuable insights and skills for their professional growth.
- Breaking and fixing things while self hosting can accelerate learning more effectively than just following tutorials.
- It is encouraged for developers to try self hosting at least once to broaden their understanding and potential career opportunities.
- Self hosting, even starting as a hobby, can lead to unexpected paths and career advancements in the tech industry.
Read Full Article
24 Likes
Dev
271
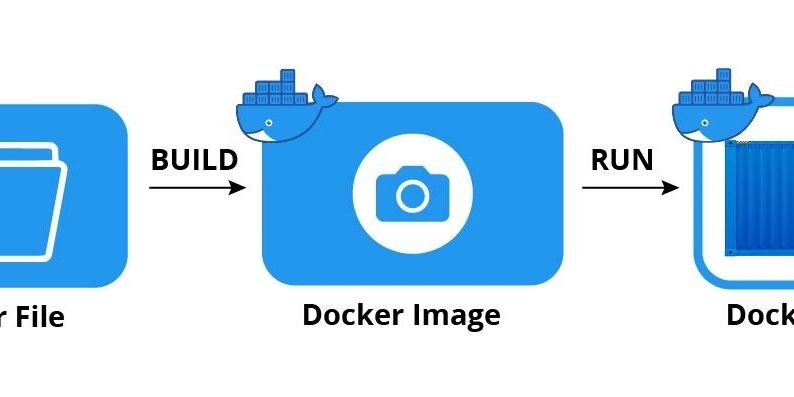
Image Credit: Dev
🐳 What is Docker, How It Works, and Why We Need It (In Simple Terms with Fun Analogies)
- Docker is like a magic shipping container for your applications. It packages your app with everything it needs to run and allows it to run anywhere.
- Docker works by giving each app its own mini-kitchen, isolated and reproducible, and created based on images.
- Docker has become popular for its consistency, speed, isolation, efficiency, and scalability.
- The top 10 Docker commands with real-world analogies include: docker build, docker run, docker ps, docker stop, docker rm, docker rmi, docker pull, docker exec, docker logs, and docker-compose up.
Read Full Article
16 Likes
Hackernoon
180

Image Credit: Hackernoon
Waiting: The Subtle Art That You Should Master
- In a workshop on Testing Pull Requests on Kubernetes with GKE and GitHub Actions, issues arose due to service dependency timing.
- Kubernetes users can face challenges when service A starts faster than service B, causing system failures.
- Kubernetes offers startup probes to tackle timing issues during pod initialization, streamlining the connection process.
- The HTTP /health endpoint can be crucial in setting up probes for web applications in Kubernetes.
- wait4x, a waiting tool, provides synchronization services like waiting for HTTP, DNS, databases, and message queues.
- Using wait4x in init containers helps ensure dependencies are met before application containers start in Kubernetes pods.
- Utilizing wait4x simplifies pod management and reduces unnecessary restarts in Kubernetes environments.
- For scenarios where waiting is mandatory, tools like wait4x can help ensure readiness before triggering subsequent actions like testing.
- GitHub Actions integrated with Docker containers, like wait4x, can enhance workflow efficiency by incorporating waiting mechanisms.
- Kubernetes startup probes and external waiting tools like wait4x play crucial roles in managing service dependencies and avoiding premature restarts.
Read Full Article
10 Likes
Dev
356
Image Credit: Dev
Task Automation with Cron, Anacron, and Systemd Timers in Red Hat Linux
- Today, I explored how Linux automates recurring tasks.
- In Red Hat Linux, you typically automate with cron, anacron, and systemd timers.
- Cron is used for time-based scheduling, anacron for missed-job recovery, and systemd timers for a modern alternative.
- Task scheduling helps automate server maintenance, create reliable backups, reduce errors, and ensure business continuity.
Read Full Article
21 Likes
Dev
234

Image Credit: Dev
# Day 3 of My 30-Day Linux Challenge: Mastering Files and Directories
- Day 3 was focused on mastering files and directories in Linux.
- Learned essential commands for creating, managing, and deleting files and directories.
- Commands like mkdir, touch, cat, cp, rm, and mv were explored.
- These skills will be applied for RHCSA certification preparation.
Read Full Article
14 Likes
Dev
248

Image Credit: Dev
Special Permissions in Linux
- SUID (Set User ID) allows users to temporarily assume the permissions of the file owner.
- SGID (Set Group ID) ensures that new files/folders within a directory inherit the group ownership of the directory.
- Sticky Bit protects files in a shared directory, allowing only the file owner to delete them.
- Numeric Mode provides a quick way to set special permissions using octal values.
Read Full Article
14 Likes
The New Stack
207
Image Credit: The New Stack
Kubernetes Powers Mastercard’s AI-Workbench for Secure Innovation
- Mastercard has built an AI-Workbench powered by Kubernetes for secure innovation.
- The AI-Workbench offers a rapid experimentation space for data engineers and scientists.
- It enables efficient machine learning model training through dynamic GPU allocation and specialized GPU cluster environments.
- The platform is built on Kubernetes and provides a dedicated ecosystem tailored for AI/ML purposes.
Read Full Article
12 Likes
For uninterrupted reading, download the app