Devops News
Dev
299
Image Credit: Dev
Measuring Developer Productivity: Metrics That Matter (and Those That Don't)
- Measuring developer productivity in software development is crucial, yet challenging due to its collaborative and creative nature.
- Commonly used metrics like lines of code, number of commits, and hours worked may not provide accurate insights into actual productivity.
- Effective productivity measurement includes DORA metrics and the SPACE framework, emphasizing speed, stability, satisfaction, performance, activity, communication, collaboration, efficiency, and flow.
- Process-focused metrics such as cycle time, PR size, code churn, and rework offer valuable insights into development team efficiency.
- Best practices for boosting developer productivity include reducing cognitive load, implementing developer playbooks, automating repetitive tasks, and matching developer strengths with projects.
- Real-world examples like Spotify's Squad Model, Google's Developer Satisfaction Survey, and Microsoft's Developer Velocity Index showcase successful strategies for enhancing productivity.
- Effective productivity measurement involves team-level metrics, leading and lagging indicators, data-driven improvement, and a focus on continuous enhancement rather than punishment.
- By prioritizing value delivery, implementing balanced frameworks, and fostering a supportive environment, organizations can cultivate sustainable, high-performing engineering cultures.
- Continuous improvement, system-level enhancements, and meaningful work assignments contribute to overall developer satisfaction and productivity in the long run.
- Measuring developer productivity should center on delivering value efficiently while maintaining developer satisfaction, ultimately leading to sustainable success in software development.
Read Full Article
17 Likes
Medium
396

Image Credit: Medium
How Value Stream Management and Product Operating Models Complement Each Other
- Value Stream Management (VSM) was introduced to the organization in late 2020, leading to insights and lessons that refined their approach.
- The evolution to VSM 1.5 involved a logical approach to redefining Value Streams, aligning teams, focusing on metrics, and documenting outcomes in Jira.
- The integration of Product Operating Model (POM) principles alongside VSM led to the foundation for operational maturity and continuous improvement.
- POM and VSM, though different on the surface, share a common spirit and offer a holistic view when combined.
- Research shows elite-performing organizations prioritize business outcomes over output metrics and are embracing outcome-driven practices and flow efficiency.
- VSM 1.5 evolved into a model harmonizing Product Operating Model's clarity with Value Stream Management's operational discipline.
- There is recognition of areas for further evolution and improvement in the journey towards outcome-driven, operationally efficient operations.
- The real transformation lies in intentionally combining both Product Operating Model and Value Stream Management for better business outcomes.
- The focus is on achieving lasting, meaningful change through the alignment of structure, flow, and outcomes in the operating model.
- The future of software delivery involves harmonizing process and structure to deliver improved, faster, and smarter results.
Read Full Article
23 Likes
Dev
432

Image Credit: Dev
🚀 Hosting a Static Website on AWS S3(After EC2)
- To host a static website using Amazon S3, you can follow the steps below:
- Step 1: Create an S3 Bucket - Head over to the AWS S3 Console, give your bucket a unique name, and click 'Create Bucket.'
- Step 2: Upload Your Website Files - Click into your bucket, click 'Upload,' select your website files, and click 'Upload.'
- Step 3: Set Public Access - Go to the Permissions tab, edit the block public access settings, and save changes.
Read Full Article
26 Likes
Dev
220

Image Credit: Dev
Local Kubernetes Development Made Easy with Telepresence Replace Mode
- Debugging Kubernetes applications locally can be overwhelming, especially dealing with complex microservices that involve environment variables, mounted volumes, and webhook traffic.
- Using Telepresence Replace mode can turn your local machine into a full Kubernetes pod, aiding in local development and debugging.
- Telepresence helps tackle challenges faced while contributing to Dapr, providing a solution for running microservices locally in Kubernetes.
- The Reflect mode offered by Telepresence removes the original pod, allowing your local machine to fully replace the pod inside the cluster.
- Telepresence also offers Intercept and Injest modes for specific development needs, but Replace mode is highlighted in this post for its power.
- Before using Telepresence, a development cluster needs to be set up, with recommended usage in environments like kind or any Kubernetes distribution.
- Telepresence's Replace mode simplifies accessing mounted volumes and environment variables, enhancing local development capabilities.
- By using Telepresence's Replace mode, one can fully replicate a pod's environment, interact with other services, and handle webhook traffic locally.
- It is crucial to limit the use of Telepresence to development clusters and understand the risks involved in exposing volumes and tokens.
- Telepresence proves to be a valuable tool for local development in Kubernetes environments, enabling efficient debugging workflows and contributing to complex projects.
Read Full Article
13 Likes
Discover more
- Programming News
- Software News
- Web Design
- Open Source News
- Databases
- Cloud News
- Product Management News
- Operating Systems News
- Agile Methodology News
- Computer Engineering
- Startup News
- Cryptocurrency News
- Technology News
- Blockchain News
- Data Science News
- AR News
- Apple News
- Cyber Security News
- Leadership News
- Gaming News
- Automobiles News
Dev
108

Image Credit: Dev
Group Management in Linux: My Journey to Organized Systems
- Effective Linux system management involves organizing users and controlling access through groups for efficiency, security, and collaboration.
- Managing groups in Linux streamlines permissions across a team, like securing code repositories through a 'developers' group.
- Essential group management commands in Linux include creating groups, adding users to groups, and verifying group membership.
- Real-world scenario: Setting up a collaborative workspace by creating a group for a team and adding team members for shared access.
- Tips for effective group management in Linux include reviewing groups regularly, using clear group names, and automating processes where possible.
- Group management is crucial for simplifying system administration, enhancing security, and fostering collaboration in Linux environments.
- Exploring group policies and designating admin roles can further optimize resource permissions and access control in Linux systems.
- Continual learning and refining of Linux administration skills through practical examples and shared experiences can enhance system organization and management.
- Stay connected for more insights on Linux administration, cloud infrastructure, DevOps, and automation to deepen your knowledge and skills.
Read Full Article
6 Likes
Dev
76

Image Credit: Dev
Dive into a real-world disaster scenario and see how Kubernetes saves the day
- Without Kubernetes, during a heavy traffic spike like Black Friday, servers can crash, resulting in site downtime, lost sales, and a negative user experience.
- Kubernetes addresses these issues by providing auto-scaling, load balancing, high availability, automatic recovery, and rolling updates without downtime.
- With Kubernetes, frontend, backend, and database replicas can be automatically scaled up based on incoming load, traffic can be evenly distributed to prevent overload, and crashed containers can be automatically restarted.
- Kubernetes also ensures app availability during updates, monitors containers' health, and replaces failed containers to maintain system stability.
Read Full Article
4 Likes
Dev
265

Image Credit: Dev
Learning Kubernetes: ReplicationController vs ReplicaSet
- A ReplicationController (RC) ensures that a specified number of pod replicas are running at any given time.
- A ReplicaSet (RS) is the next-gen version of RC, introduced with better support for label selectors.
- The key difference between ReplicationController and ReplicaSet is that ReplicaSet supports set-based label selectors.
- ReplicationControllers have been largely replaced by ReplicaSets and Deployments in modern Kubernetes environments.
Read Full Article
16 Likes
Dev
81
Image Credit: Dev
🚀 Kubernetes Pod Commands & YAML Guide – Quick Reference for Devs & DevOps
- Here’s a quick guide to working with Kubernetes Pods using the CLI and YAML definitions.
- Essential kubectl Commands for Pods.
- Create a pod, list all pods, access a running pod shell, describe pod details, delete a pod.
- Create a Pod using YAML, access shell inside Pod/Container.
Read Full Article
4 Likes
Securityaffairs
99

Image Credit: Securityaffairs
Storm-1977 targets education sector with password spraying, Microsoft warns
- Threat actor Storm-1977 is targeting the education sector with password spraying attacks on cloud tenants.
- The threat actor uses AzureChecker.exe to identify password spray targets and download encrypted data.
- Microsoft warns about the risks faced by containerized assets like Kubernetes clusters and suggests security measures to protect them.
- Key threats to containerized assets include compromised accounts, vulnerable/misconfigured images, misconfigurations exposing APIs, app-level attacks, node-level attacks, and unauthorized traffic.
Read Full Article
5 Likes
Dev
365

Image Credit: Dev
Understanding Groups in Linux: How They Shape Access & Control in Real World
- Groups in Linux are collections of users with assigned permissions.
- There are two types of groups in Linux: primary and secondary (supplementary).
- Common group management commands include creating groups, adding/removing users, and changing a user's primary group.
- Real-world examples of group usage include restricting access to project folders and separating departments.
Read Full Article
21 Likes
Dev
13
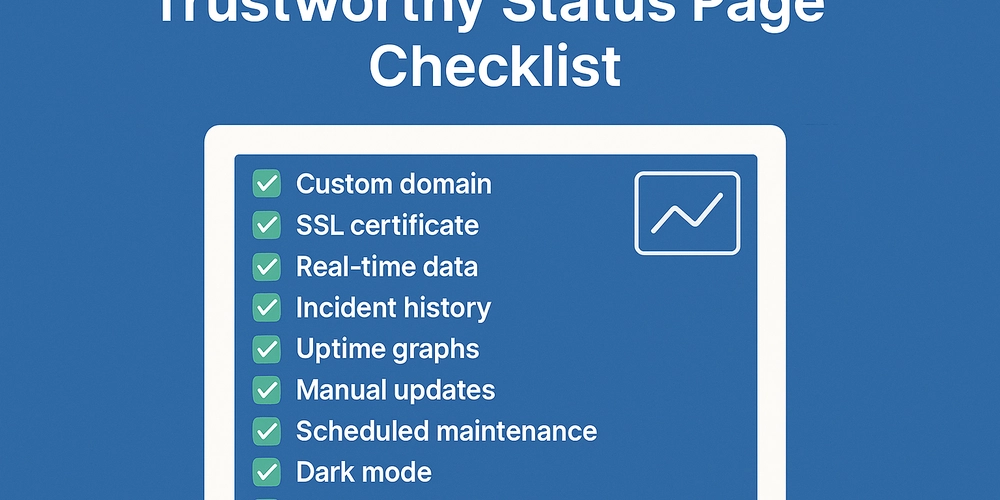
Image Credit: Dev
What Makes a Status Page Trustworthy? A Dev’s Checklist
- A trustworthy status page is crucial for building user trust and confidence.
- The checklist includes points like having a custom domain and an SSL certificate for better credibility.
- The status page should provide real-time data and incident history to keep users informed.
- Other important features include uptime graphs, manual status updates, and dark mode option.
Read Full Article
Like
Medium
171
Image Credit: Medium
Self-Hosting n8n locally with Docker Compose: Step-by-Step Setup
- This guide explains how to set up n8n locally using Docker Compose.
- n8n is a workflow automation tool that allows scheduling tasks and moving data between various apps, tools, platforms, and services.
- The setup involves creating a new directory, setting up a docker-compose.yml file, starting the services, and accessing n8n at a specific URL.
- Self-hosting n8n with Docker Compose gives complete control over the data and provides a robust foundation suitable for both development and production environments.
Read Full Article
10 Likes
Dev
112
Image Credit: Dev
Kubernetes 1.33: A Deep Dive into the Exciting New Features of Octarine
- Kubernetes 1.33, codenamed 'Octarine: The Color of Magic,' introduces 64 enhancements, with focus on security, usability, scalability, and developer experience.
- Key features include stable native sidecar container support, in-place pod vertical scaling (beta), and user namespaces enabled by default (stable) for enhanced security.
- The alpha OCI image volumes feature simplifies the mounting of container images directly as pod volumes, improving flexibility in workflows.
- Fine-grained Kubelet authorization (stable) strengthens cluster security by providing granular access controls.
- Topology-aware routing enhancements optimize resource utilization, and stable subresource support for kubectl commands enhances usability.
- Configurable backoff limits for indexed jobs (stable) and alpha validation-gen tool add reliability and ease for developers and contributors.
- Memory manager improvements, Pod Disruption Budget enhancements, and CRD validation expressions benefit the Kubernetes ecosystem.
- Kubernetes 1.33 deprecates features like the Endpoints API and removes host network support for Windows pods.
- The release signifies Kubernetes' evolution in addressing real-world challenges, offering upgrades for platform engineers, DevOps professionals, and security specialists.
- Community involvement through Kubernetes Enhancement Proposals showcases the platform's vibrancy and continuous improvement.
- For a detailed overview, users are encouraged to explore release notes, engage with the community, and embrace Kubernetes 1.33 for optimizing cloud-native workflows.
Read Full Article
6 Likes
Dev
126

Image Credit: Dev
Introduction to SQL Using PostreSQL
- SQL (Structured Query Language) is a crucial programming language for managing information in relational database management systems.
- PostgreSQL is a popular open-source RDBMS used for storing, manipulating, and retrieving data efficiently.
- Setting up PostgreSQL involves downloading the latest version, installing it based on the operating system, and configuring it for use.
- Basic database concepts like schemas, tables, rows, and columns form the foundation for understanding SQL queries and data storage.
- Creating databases, schemas, tables, inserting data, and querying data are essential SQL operations covered in the article.
- Hands-on projects like creating a Customer Order Management System help apply SQL concepts in practical scenarios.
- Pro tips on SQL data types and constraints explain the types of data each column can store and constraints for data management.
- Next steps include mastering SQL JOINs, understanding SQL indexes, and working on SQL project ideas to enhance database management skills.
Read Full Article
7 Likes
Dev
248

Image Credit: Dev
🧱Migrating from Monolith to Microservices with GKE: Core Concepts
- Transitioning from monolithic applications to microservices using Google Kubernetes Engine (GKE) can bring better scalability, resilience, and team autonomy.
- Starting with a monolithic architecture, developers face challenges such as scaling inefficiencies, deployment headaches, single points of failure, growing complexity, and technology stagnation.
- By migrating to microservices, developers can decompose the monolith into smaller, independently deployable services, enabling independent scaling, development, and ownership by specific teams.
- Google Kubernetes Engine (GKE) provides a managed Kubernetes environment that handles deployment and orchestration of containerized microservices.
Read Full Article
14 Likes
For uninterrupted reading, download the app