Devops News
Dev
292

Image Credit: Dev
Mastering AWS EC2 Automation
- In today's DevOps learning journey, we will explore how to automate the creation and management of virtual machines (EC2 instances) on Amazon Web Services (AWS).
- Logging into AWS and launching EC2 instances
- Choosing the right terminal based on your OS
- Connecting to a VM and creating files
Read Full Article
17 Likes
Dev
263

Image Credit: Dev
A Glimpse into Essential Linux Commands for DevOps & Cloud Computing
- Linux is crucial for DevOps and cloud computing in managing infrastructure and automation.
- Outlined are essential Linux commands for DevOps & cloud computing, including:
- - System monitoring & performance tuning
- - User & permission management
- - Process & service management
Read Full Article
15 Likes
Dev
59

Image Credit: Dev
An Easy Step-by-Step Guide on How to Deploy a Windows 11 Virtual Machine on Microsoft Azure
- Deploying a Windows 11 virtual machine on Microsoft Azure is quick and straightforward.
- Step 1: Log in to Azure using your Microsoft account.
- Step 2: Create a new virtual machine by configuring the basics and selecting Windows 11 Pro image.
- Step 3: Configure disks and Step 4: Networking Configuration.
Read Full Article
3 Likes
Medium
349

##Learning Python as My First Step into DevOps | A Beginner’s Journey.
- Python is a popular scripting language used in DevOps for automation and scripting.
- As a beginner, the author learned Python basics and gained clarity on logic flows in code.
- The author faced challenges with indentation errors, self method concept, and OOP concepts, but persisted and now feels more confident.
- Next, the author plans to document their learning journey and share weekly updates on GitHub and LinkedIn.
Read Full Article
21 Likes
Discover more
- Programming News
- Software News
- Web Design
- Open Source News
- Databases
- Cloud News
- Product Management News
- Operating Systems News
- Agile Methodology News
- Computer Engineering
- Startup News
- Cryptocurrency News
- Technology News
- Blockchain News
- Data Science News
- AR News
- Apple News
- Cyber Security News
- Leadership News
- Gaming News
- Automobiles News
Medium
404

Image Credit: Medium
How to Run Scheduled Cron Jobs in GitHub Workflows for Free
- GitHub Actions allows you to automate tasks using cron syntax.
- It is free for public repositories and offers generous free minutes for private repositories.
- Cron expressions can be used to schedule tasks on specific time intervals.
- GitHub Actions scheduled workflows provide a flexible way to automate recurring tasks without managing servers.
Read Full Article
24 Likes
Dev
399

Image Credit: Dev
Kubernetes Workloads & Services — Explained with an Amusement Park Analogy
- This article simplifies Kubernetes workloads and services using an amusement park analogy.
- Kubernetes workloads include Pods, ReplicaSets, Deployments, StatefulSets, Jobs, CronJobs, and DaemonSets.
- Pods are the smallest deployable units, ReplicaSets ensure the specified number of pod replicas, and Deployments handle updates.
- StatefulSets are for stateful applications, Jobs run tasks to completion, and CronJobs run tasks on a schedule.
- DaemonSets ensure one pod runs on every node, commonly used for purposes like logging or monitoring agents.
- Kubernetes services like ClusterIP, NodePort, LoadBalancer, and Ingress manage entry points and external access to pods.
- ClusterIP enables internal communication, NodePort exposes services externally, LoadBalancer distributes incoming traffic, and Ingress routes HTTP requests.
- The article uses a theme park analogy to explain different Kubernetes workloads and service types, making the concepts more relatable.
- Next chapter will cover managing microservice traffic with Istio and service mesh technology.
- Understanding Kubernetes through analogies like amusement parks can help grasp complex systems more easily.
Read Full Article
24 Likes
Dev
104

Image Credit: Dev
Docker Images and Containers: The Core Building Block
- Docker images are pre-configured packages that contain everything required to run an application.
- Docker containers are running instances of Docker images, isolated and executable environments.
- A Docker image can spawn multiple containers, each functioning independently.
- Differentiating between CMD and RUN commands in Dockerfile is important.
Read Full Article
6 Likes
Dev
109
Image Credit: Dev
Day 10: My first GitHub action
- GitHub Actions is a powerful automation tool that helps automate repetitive tasks like testing, building, and deploying code.
- Workflows in GitHub Actions are defined in YAML files and can be triggered by events like push, pull request, etc.
- Jobs in GitHub Actions are groups of steps that run on the same machine, and each job runs in a fresh environment.
- Steps in GitHub Actions are individual tasks executed in order within a job.
- Creating a GitHub Action involves writing a YAML file in the repository, defining workflows, jobs, and steps.
- Resources like GitHub Actions documentation and LinkedIn Learning courses can help in understanding and implementing GitHub Actions.
- GitHub Actions are beneficial for both beginners and experienced developers in automating tasks and deploying applications.
- It simplifies the process of automation in development and allows for deploying projects easily directly from the GitHub repository.
- GitHub Actions can handle both simple and complex workflows, making it versatile for various automation needs.
- Exploring GitHub Actions is recommended for anyone starting their DevOps journey or looking to enhance automation skills.
Read Full Article
6 Likes
Dev
36
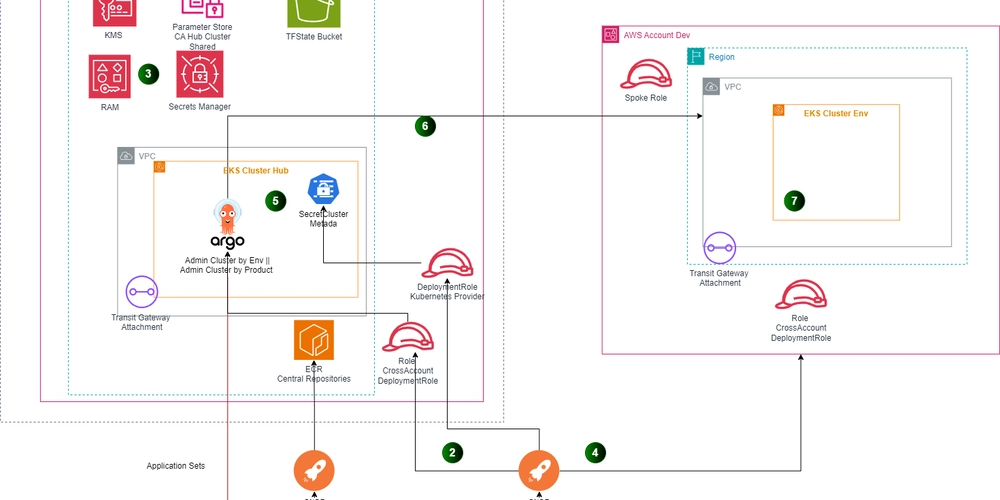
Image Credit: Dev
GitOps and IaC at Scale – AWS, ArgoCD, Terragrunt, and OpenTofu – Part 2 – Creating Spoke environments
- The article discusses deploying spokes cluster using the GitOps bridge framework with AWS enterprise capabilities and security best practices.
- Considerations include using one IaC repository for accounts, teams, or squads based on organizational structure.
- Capacity planning varies, with some organizations sharing clusters and grouping applications by namespaces.
- The architecture can have a single hub managing multiple environments or separate hubs for each environment cluster.
- Capacity planning and networking are main challenges addressed in the deployment scenarios.
- Implementations involve setting up credentials, enabling RAM as a trusted service, and creating IAM roles for authentication.
- Infrastructure is managed using tools like Terragrunt, creating parameter stores and IAM roles for authentication.
- The GitOps bridge stack includes configurations for handling secrets, enabling IRSA roles, and managing cluster authentication.
- Spoke cluster infrastructure is managed separately, allowing custom CI/CD pipelines and features for each team.
- The article concludes by emphasizing the importance of managing cluster secrets and metadata information in the spoke clusters.
Read Full Article
2 Likes
Dev
168

Image Credit: Dev
Chaos Engineering for Microservices: Resilience Testing with Chaos Toolkit, Chaos Monkey, Kubernetes, and Istio
- Chaos Engineering is crucial for ensuring resilience in cloud-native environments with microservices, Kubernetes, and Istio.
- It involves proactively introducing controlled failures to identify system weaknesses and improve reliability.
- Chaos Toolkit, Chaos Monkey, and Istio-based fault injection are valuable for Java, Node.js, Kubernetes, and Istio applications.
- Chaos Engineering lifecycle follows structured experiments to enhance system resilience continuously.
- Chaos Toolkit and Chaos Monkey have different use cases, with Chaos Toolkit suitable for Kubernetes-based testing and custom failure scenarios.
- Chaos Monkey is ideal for Spring Boot applications and lightweight, built-in failure injection for Java microservices.
- Chaos Toolkit offers a versatile framework for chaos testing in Java, Node.js, Kubernetes, and Istio.
- Chaos Monkey for Spring Boot injects failures dynamically across different layers of a Spring Boot application.
- Chaos Monkey attacks can be manually enabled to introduce latency or exceptions dynamically in Spring Boot applications.
- Chaos Engineering principles can be implemented in Node.js using Chaos Toolkit and third-party libraries like Chaos Monkey for Node.js.
Read Full Article
10 Likes
Dev
290

Image Credit: Dev
Mastering the mkdir Command in Linux (Made Simple & Practical)
- mkdir (make directory) is a Linux command used to create new folders
- In addition to creating a single folder, mkdir has several other use cases:
- It is important to use the -p flag when creating nested directories or multiple directories at once
- Proper permission settings are necessary to create new folders, and it is recommended to avoid using sudo unless necessary
Read Full Article
17 Likes
Medium
322

Image Credit: Medium
10 DevOps Terms Every ML Engineer Should Know
- DevOps bridges the gap between ML experimentation and production impact.
- ML engineers need to know important DevOps terms for deployment and scaling of models.
- Continuous Integration (CI) helps ensure smooth integration and faster iteration in ML projects.
Read Full Article
19 Likes
Dev
331

Image Credit: Dev
🚀 From Docker to Kubernetes: The Containerization Chronicles
- Docker is used for packaging and running a single application, while Kubernetes helps run multiple apps efficiently, especially when scaling.
- When using Docker, running 'docker run' starts an isolated container with necessary app components, sharing the host OS kernel for lightweight performance.
- Internally, Docker utilizes Linux namespaces, cgroups, and a Union File System to manage containers efficiently.
- Kubernetes complements Docker by managing multiple containers, enabling deployment, scaling, updates, and self-healing in a microservices environment.
- Kubernetes doesn't replace Docker but works with it to orchestrate container lifecycles in a distributed system.
- To deploy a Spring Boot microservice on Kubernetes, build and push a Docker image, then create YAML files for Deployment and Service configurations.
- YAML files specify deployment replicas, container images, ports, and services to expose application functionality.
- For multiple microservices and databases, separate Deployments and Services are created, with optional Ingress to manage external traffic routing.
- Docker builds and runs containers, while Kubernetes orchestrates containers across nodes in production, offering autoscaling and resilience.
- Understanding Docker's internals, Kubernetes basics, deploying microservices, and reading YAML manifests are key takeaways for building cloud-native apps.
- The combined use of Docker and Kubernetes forms the foundation for developing scalable, cloud-native applications.
Read Full Article
19 Likes
Dev
418

Image Credit: Dev
How to Create and Connect to a Linux VM Using a Public Key
- Creating a Linux VM in Azure and connecting to it using a public key is a secure method for managing cloud-based systems.
- To create a Linux VM in Azure, you need to log in to the Azure Portal, create a virtual machine, and configure the necessary settings.
- To connect to the Linux VM using SSH, you can download the private key, open your terminal or PowerShell, and run the SSH command with the key and IP address.
- After connecting to the VM, you can update the server and install a web server like Nginx to host websites or web apps.
Read Full Article
25 Likes
Dev
90

Image Credit: Dev
How to Compress Web Assets in Real-Time Using Brotli with NGINX
- Brotli compression provides better compression ratios than gzip for text-based assets such as HTML, CSS, and JavaScript.
- To enable Brotli compression with NGINX, install Brotli and enable it in the NGINX configuration.
- You can test the configuration and combine Brotli with static precompression for further optimization.
- By enabling Brotli compression, you can enhance website performance and optimize page delivery.
Read Full Article
5 Likes
For uninterrupted reading, download the app