Devops News
Dev
326
Image Credit: Dev
How to Build Comprehensive Dashboards for Your SaaS and Cloud Apps
- Creating comprehensive dashboards for SaaS/Cloud apps is crucial for troubleshooting and visibility of system components.
- Architecture diagrams provide a high-level view, but detailed information is essential for deployment and troubleshooting.
- MechCloud dashboards use AWS and System Info UI components to collect data from AWS, Cloudflare, Kubernetes, and Docker via REST APIs.
- Exemplifying an app on self-managed Kubernetes on AWS Lightsail connected via Cloudflare tunnels, with Docker serving cloudflared on Lightsail VM.
- Dashboard setup involves creating cards for Cloudflare, Docker, Kubernetes, and AWS Lightsail to display relevant system data.
- Processes include creating teams, frames, sites, and pages using MechCloud page designer.
- Utilizing CSS Grid with MechCloud AWS and System Info components, setting grid area labels for each card for layout.
- Configuring Cloudflare, Docker, Kubernetes, and AWS system accounts with appropriate details in the MechCloud console.
- Customizing System Info components for Cloudflare, Kubernetes, Docker, and AWS Info with prompts to fetch specific data.
- A well-designed dashboard enhances visibility, collaboration, and operational efficiency for SaaS and Cloud applications.
Read Full Article
19 Likes
Devopsonline
103

Image Credit: Devopsonline
Critical skills for tomorrow’s workforce
- AI foundational skills across all roles and departments are important to effectively integrate AI technologies into operations.
- Quantum mechanics, algorithms, and programming principles are crucial skills for organisations to pioneer advancements in quantum innovation.
- Soft skills development is essential for technical staff to effectively communicate, negotiate, and represent their team.
- Implementing continuous learning 'in the flow of work' enables access to relevant learning materials in real-time and improves employee engagement and productivity.
Read Full Article
6 Likes
Dev
126

Image Credit: Dev
Scaling Globally? Here's Why IP Geolocation API Should Be in Your Stack
- When building applications for a global audience, understanding user locations is crucial for content customization, fraud prevention, and compliance.
- Integrating IP-based location data tools like IP geolocation APIs enables personalized experiences at scale.
- These tools allow for real-time detection of user locations, enhancing features like localized content delivery and security measures.
- IP geolocation APIs are essential for serving hundreds of thousands of location-based decisions daily when scaling globally.
- Consider factors like low latency, uptime, global coverage, API call limits, and advanced features when choosing a service.
- Look for providers with flexible pricing, generous free limits, and scalable options to meet growing demands.
- Premium features to consider include city-level geolocation, ISP info, timezone detection, and proxy/vpn detection.
- Responsive customer support, easy integration, SDK availability, and real-time/batch processing capabilities are important criteria.
- IP-based geolocation data is accurate to the city level in most countries and complies with privacy laws like GDPR or CCPA.
- Choose a provider that offers burst tolerance and quick plan scaling to handle API rate limits during traffic spikes.
- Integrating IP geolocation APIs early on saves from scalability issues later and enhances user experience globally.
Read Full Article
7 Likes
Towards Data Science
172

AWS: Deploying a FastAPI App on EC2 in Minutes
- AWS is a popular cloud provider for deploying and scaling applications, essential for software engineers and data scientists.
- This tutorial guides deploying a FastAPI application on AWS EC2, applicable to other application types.
- Considers core EC2 networking concepts, but excludes best practices for AWS usage.
- Steps include instance creation, SSH connection setup, and environment configuration.
- Demo uses t3.nano instance type, SSH authentication, and Nginx setup to redirect traffic.
- Package installation instructions, FastAPI server launch, and Nginx restart are covered.
- Exercise section details creating a FastAPI example repository with main.py and requirements.txt.
- Instructions to handle file upload issues in Nginx by adjusting client_max_body_size are provided.
- Article concludes by summarizing the process of deploying a FastAPI server on AWS EC2 for beginners.
- Next steps suggested include creating multiple EC2 instances and connecting them for further learning.
Read Full Article
9 Likes
Discover more
- Programming News
- Software News
- Web Design
- Open Source News
- Databases
- Cloud News
- Product Management News
- Operating Systems News
- Agile Methodology News
- Computer Engineering
- Startup News
- Cryptocurrency News
- Technology News
- Blockchain News
- Data Science News
- AR News
- Apple News
- Cyber Security News
- Leadership News
- Gaming News
- Automobiles News
Dev
267

Image Credit: Dev
If You Run Your CI Locally, You’ve Already Failed
- Testing GitHub workflow files is painful, so ACT allows running GitHub Actions locally.
- However, running CI locally instead of pushing it to the repo undermines the purpose of CI.
- Continuous Integration (CI) serves as a gate and referee to block code that shouldn't pass, rather than for testing code until it works.
- CI failures are not annoyances but rather bugs, indicating deeper issues with the process, not the code.
Read Full Article
16 Likes
Dev
424
Image Credit: Dev
Deploying Dapr with Kubernetes
- This guide walks you through deploying Dapr on Kubernetes using the Hello Kubernetes quickstart.
- Prerequisites: Docker, kubectl, Dapr CLI, and a Kubernetes cluster (Minikube, Docker Desktop, AKS, etc.).
- Step 1: Clone the Repository: git clone https://github.com/dapr/quickstarts.git
- Step 2: Initialize Dapr on Kubernetes: dapr init -k --dev
- Step 3: Deploy the Sample Applications: kubectl apply -f deploy/
Read Full Article
25 Likes
The New Stack
67

Image Credit: The New Stack
Kubernetes v1.33 Advances in AI, Security and the Enterprise
- The latest release of Kubernetes, v1.33, brings advancements in AI workloads, security, and enterprise use, featuring 64 enhancements.
- Key updates include support for sidecar containers and in-place resource resizing for pods, alongside dynamic resource allocation and user namespaces.
- 121 companies and 570 individuals contributed to Kubernetes v1.33 during the release cycle.
- The release introduces Sidecar Containers for handling networking, logging, and metrics gathering, streamlining the management of multi-container applications.
- Dynamic Resource Allocation (DRA) API in Beta allows for allocating non-CPU resources like GPUs, TPUs, and FPGAs, crucial for AI workloads.
- User namespaces are enabled by default for Linux pods in this release, enhancing security and resource isolation in Kubernetes.
- Kubernetes v1.33 aims to make clusters more secure, scalable, and easier to manage, with improvements highlighted by technical experts.
- The update is installable via kubeadm and is available for download on GitHub, offering enhanced features for Kubernetes users.
- For full details and changes, users can refer to the release notes or attend the web presentation by the Release Team.
Read Full Article
4 Likes
Siliconangle
45

Image Credit: Siliconangle
Three insights you may have missed from theCUBE’s coverage of KubeCon + CloudNativeCon Europe
- Cloud-native observability is emerging as a key lever in managing multicloud ecosystems, addressing complexity and skill gaps.
- Observability tools help unify platforms, simplify operations, and adapt to AI-driven environments for real-time diagnostic support.
- Cloud-native observability expands into compliance monitoring, security, and decision-making to enhance performance.
- Platform engineering matures with challenges like DevSecOps adoption, platform sprawl, and managing upgrades at scale.
- Kubernetes evolves to involve a broader range of creators and integrates with AI development, offering more intuitive experiences.
- AI at scale transitions towards more cost-effective and domain-specific models, utilizing Kubernetes as the underlying infrastructure.
- Cloud-native observability becomes crucial for understanding smaller AI models and building trust for production deployment.
- Development tools are becoming more iterative and inspiring, prioritizing creativity over configuration.
- The CNCF promotes open collaboration to help cloud-native AI transition from theory to production, fostering stronger partner ecosystems.
- The article highlights key insights from theCUBE's coverage of KubeCon + CloudNativeCon Europe, emphasizing the evolving landscape of cloud-native technologies.
Read Full Article
2 Likes
Kubernetes
339

Continuing the transition from Endpoints to EndpointSlices
- Since the introduction of EndpointSlices, the Endpoints API in Kubernetes has become obsolete for new features.
- As of Kubernetes 1.33, the Endpoints API is officially deprecated, and users are encouraged to switch to EndpointSlices.
- The plan is to change Kubernetes Conformance criteria to eliminate the need for running the Endpoints controller in modern clusters.
- Users with workloads or scripts still using the Endpoints API should start migrating to EndpointSlices.
- EndpointSlice API allows Services to have multiple EndpointSlices associated with them, supporting features like dual-stack networking.
- EndpointSlices are used to represent endpoints of a single IP family, handle changes in port configurations, and manage a large number of endpoints efficiently.
- When fetching EndpointSlices, users should use labels to associate them with the corresponding Service rather than by name.
- Migrating to EndpointSlices involves updating code to fetch and process EndpointSlices instead of Endpoints.
- For generating EndpointSlices, a new YAML format is required, including explicit address types and conditions for each endpoint.
- EndpointSlices offer new features like topology hints and terminating endpoints, enhancing functionality beyond the Endpoints API.
Read Full Article
20 Likes
Medium
118

Image Credit: Medium
✅ Day 3 Topic: Mastering Windows Event Viewer for DevOps & SRE
- Event Viewer is a valuable tool for DevOps and SRE professionals to troubleshoot issues on Windows systems.
- It logs everything, including successes, failures, warnings, and audits.
- Users can navigate different categories within Event Viewer, such as Windows Logs, to identify specific issues.
- Creating custom views and exporting logs are useful features for recurring scenarios.
Read Full Article
7 Likes
Medium
5

Image Credit: Medium
Mastering Terraform: 5 Essential Commands for AWS Cloud Provisioning
- Terraform is an Infrastructure as Code (IaC) tool developed by HashiCorp.
- It allows you to automate the creation, management, and versioning of cloud infrastructure.
- The top 5 essential Terraform commands for AWS cloud provisioning are: terraform init, terraform plan, terraform apply, terraform destroy, and terraform fmt.
- Using Terraform, AWS cloud engineers or DevOps students can automate and scale infrastructure at a professional level.
Read Full Article
Like
Dev
312

Image Credit: Dev
Setting Up My Linux Lab with RHEL 9 (30-Day RHCSA Journey)
- Day 1 of the RHCSA + Ansible Fast Track Training with the CloudWhistler Community focused on setting up the lab environment.
- The tasks included installing VirtualBox, downloading the RHEL 9 ISO, creating a VM, and exploring the Linux CLI.
- Some common troubleshooting issues during installation were addressed, such as VirtualBox not detecting the RHEL ISO and VM crashes.
- Setting up the lab provides valuable learning opportunities on topics like resource allocation and troubleshooting errors.
Read Full Article
18 Likes
Medium
118
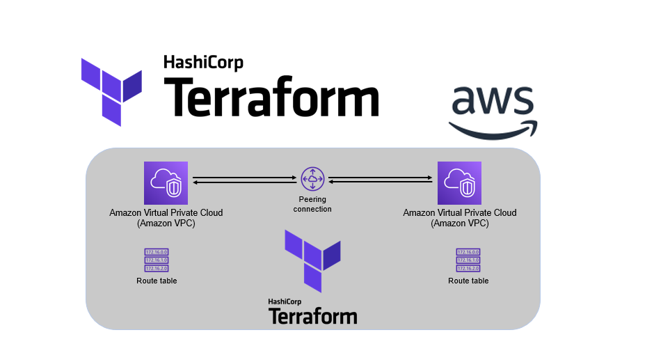
Image Credit: Medium
Terraform : Guide to create AWS EC2 and S3 setup using IAC
- This blog provides a guide on using Terraform to create an AWS EC2 instance and S3 bucket.
- Terraform is an open-source tool that allows infrastructure provisioning using a high-level configuration language called HCL.
- It acts as a bridge between code and the cloud, ensuring consistency across environments.
- The guide covers the necessary steps to define resources, create, update, destroy, and shows the benefits of Infrastructure as Code.
Read Full Article
7 Likes
Dev
94

Image Credit: Dev
Building a Secret Scanner in Julia: A GitLeaks Alternative
- A new tool called Julia aims to provide an alternative to GitLeaks for scanning secrets, passwords, and API key leaks.
- Julia offers more advanced features like specifying custom regex pattern lists, producing proper JSON output for automation, and backend use.
- The tool also allows scanning directories, GitHub repositories directly, and loading custom patterns from a YAML file.
- The project structure includes the use of Docker, Julia, and nfpm for creating DEB and RPM packages.
- A Makefile is used for handling Docker builds, Docker container operations, pushing images to Docker Hub, and creating GitHub releases.
- GitHub CLI is utilized for tagging repositories, uploading releases, and creating GitHub releases with version numbers like v1.0.0.
- Testing is done by running the script in a Docker container against a test repository that contains secret leaks.
- A GitHub pipeline is set up for automated CI/CD workflows using Docker, Make, GitHub Actions, and Makefile commands.
- Julia, Docker, and GitHub tools simplify the process of building, testing, packaging, and deploying projects, making it suitable for everyday tasks.
Read Full Article
5 Likes
Ubuntu
248

Image Credit: Ubuntu
The hitchhiker’s guide to infrastructure modernization
- The article discusses the importance of infrastructure modernization and the key takeaways from the Infra Masters 2025 event held by Canonical.
- One key lesson is to reconsider vendor relationships to speed up innovation, as demonstrated by BT shifting from vendor-consumer to partnership with Canonical.
- ESA plans to double missions by 2030 and has leveraged Canonical Kubernetes for automating deployment and freeing up resources for critical tasks.
- Open source software plays a crucial role in modernizing infrastructure, offering flexibility, scalability, and cost-effectiveness.
- BT's Network Cloud project utilized open source solutions like MAAS, Ceph, LXD, and Juju to streamline operations and focus on application development.
- The future of infrastructure lies in edge computing, containerized applications, serverless computing, and Kubernetes management.
- ESA's plan to scale satellites relies on Kubernetes and cloud-native computing for managing workloads effectively.
- Canonical's infrastructure portfolio automations improve efficiency and reduce costs, benefiting organizations without capacity or skill shortages.
- Choosing managed solutions for infrastructure can ease migration efforts and free up in-house engineers.
- Overall, the event highlighted the importance of collaboration, open source adoption, and managed solutions for successful infrastructure modernization.
- Canonical's software, such as Ubuntu, offers trusted open source options for organizations looking to optimize infrastructure and lower costs.
Read Full Article
14 Likes
For uninterrupted reading, download the app