Hacking News
Securityaffairs
94

Image Credit: Securityaffairs
Europol dismantles €460M crypto scam targeting 5,000 victims worldwide
- Europol dismantled a cryptocurrency fraud ring that scammed over 5,000 victims worldwide, laundering €460 million.
- The operation, named Operation Borrelli, was led by Spain's Guardia Civil and involved collaboration with law enforcement in Estonia, France, and the U.S.
- The scammers targeted victims through crypto romance scams on chats or dating apps, stealing money through fake platforms and using complex transfers to hide it.
- Five members of the criminal network were arrested, and authorities performed searches between the Canary Islands and Madrid to curb the cryptocurrency investment fraud.
Read Full Article
5 Likes
Securityaffairs
367

Image Credit: Securityaffairs
CISA and U.S. Agencies warn of ongoing Iranian cyber threats to critical infrastructure
- U.S. cybersecurity and intelligence agencies warn of rising Iranian cyber threats, exploiting outdated software and weak passwords, with attacks expected to increase.
- Iranian-aligned hacktivists have increased website defacements, data leaks, and may escalate DDoS and ransomware attacks targeting U.S. and Israeli entities.
- The ongoing Iran conflict has raised cyber threat levels in the U.S., with potential low-level attacks by pro-Iranian hacktivists and state-linked cyber activity.
- The U.S. Department of Homeland Security issued warnings about Iranian cyber attacks following the killing of Iranian military commander Soleimani in 2020.
Read Full Article
22 Likes
Medium
218

Image Credit: Medium
How to Prevent Your Social Media from Being Hacked?
- Social media platforms are vulnerable to hacking due to weak passwords, open logins, and various access points.
- To prevent hacking, users should avoid using obvious passwords like names, phone numbers, or dates of birth. Instead, opt for complex combinations of letters, numbers, and special characters.
- It is essential to use unique passwords for each social media account to minimize the risk of multiple accounts being compromised if one is hacked.
- Enabling 2-step verification adds an extra layer of security by requiring a code sent to a user's phone or email to log in, even if the password is known to hackers.
Read Full Article
13 Likes
Medium
333

Image Credit: Medium
Ghosting the internet
- Google's updated Results About You tool reveals extensive personal information on the internet.
- Service providers compile detailed dossiers including addresses, phone numbers, family details, and more.
- Increasing data breaches make personal data vulnerable, paving the way for identity theft risks.
- New services track and request deletion of personal info to enhance online privacy.
Read Full Article
20 Likes
Securityaffairs
205

Image Credit: Securityaffairs
U.S. CISA adds Citrix NetScaler flaw to its Known Exploited Vulnerabilities catalog
- The U.S. Cybersecurity and Infrastructure Security Agency (CISA) added the Citrix NetScaler vulnerability CVE-2025-6543 to its Known Exploited Vulnerabilities catalog.
- CVE-2025-6543 is a memory overflow vulnerability in NetScaler ADC and NetScaler Gateway, potentially leading to Denial of Service.
- Affected versions include NetScaler ADC 13.1-FIPS, 14.1, and earlier versions, requiring prompt mitigation to protect against attacks exploiting the flaw.
- CISA has issued directives for federal agencies to address the vulnerabilities by July 21, 2025, following a similar inclusion of other Citrix vulnerabilities in the past.
Read Full Article
12 Likes
TechCrunch
119

Image Credit: TechCrunch
US government takes down major North Korean ‘remote IT workers’ operation
- The U.S. Department of Justice took enforcement actions against North Korea's remote IT workers operation, which aimed to raise funds for the regime's nuclear weapons program and steal data and cryptocurrency.
- A U.S. national named Zhenxing 'Danny' Wang was arrested and indicted for running a fraud scheme to bring North Korean IT workers into U.S. tech companies, generating over $5 million for the North Korean regime.
- Eight more individuals, including Chinese and Taiwanese citizens, were indicted for participating in the scheme, involving wire fraud, money laundering, identity theft, hacking, and violating sanctions.
- The scheme included impersonating U.S. individuals to secure jobs at American companies, setting up laptop farms to hide the workers' origins, and stealing sensitive data from the companies, including source code from a California-based defense contractor.
Read Full Article
7 Likes
Hackers-Arise
111

Image Credit: Hackers-Arise
How Cloudflare Works: The Hacker Blueprint
- Cloudflare is a widely used cybersecurity product that protects about 19.3% of websites globally, offering DDoS protection, CDN, and Internet security products.
- Cloudflare acts as a digital 'bouncer' for websites, filtering, accelerating, and protecting traffic by sitting between users and web servers.
- Key functions of Cloudflare include DNS and proxy magic, CDN for speed and stealth, security features like DDoS protection, Web Application Firewall, SSL/TLS encryption, and access control.
- Cloudflare also employs DDoS mitigation strategies and edge computing with real-time analysis, dynamic rules, and the ability to run JavaScript code at the edge.
Read Full Article
6 Likes
TechCrunch
342

Image Credit: TechCrunch
Mexican drug cartel hacker spied on FBI official’s phone to track and kill informants, report says
- A hacker hired by the Mexican Sinaloa drug cartel spied on the U.S. Embassy in Mexico City in 2018 to identify targets for the cartel to kill, as per a U.S. government watchdog report.
- The FBI's investigation into El Chapo led to the discovery that the cartel had hired a hacker who accessed an FBI official's phone to obtain calls, geolocation data, and even used Mexico City's camera system to track the official and individuals they met.
- The hacker's actions were utilized by the cartel to intimidate and eliminate potential sources or witnesses cooperating with authorities, according to the report.
- Mexico has seen extensive use of surveillance and hacking tools both by law enforcement agencies targeting cartels and by criminal organizations like the Sinaloa cartel using encrypted phones and hacker networks for illicit activities.
Read Full Article
20 Likes
Securityaffairs
17

Image Credit: Securityaffairs
Canada bans Hikvision over national security concerns
- Canada has banned Chinese surveillance firm Hikvision due to national security concerns, ordering the company to cease operations in the country and prohibiting its products from government use.
- The ban includes a national security review under the Investment Canada Act, and Canada is assessing existing properties to ensure no legacy Hikvision products are used going forward.
- Hikvision Canada criticized the ban, calling it baseless and politically motivated, emphasizing that its products comply with Canadian laws and security standards.
- The US and UK have also taken actions against Chinese technology companies in the past due to national security risks, including bans on Hikvision's products.
Read Full Article
1 Like
Securityaffairs
214
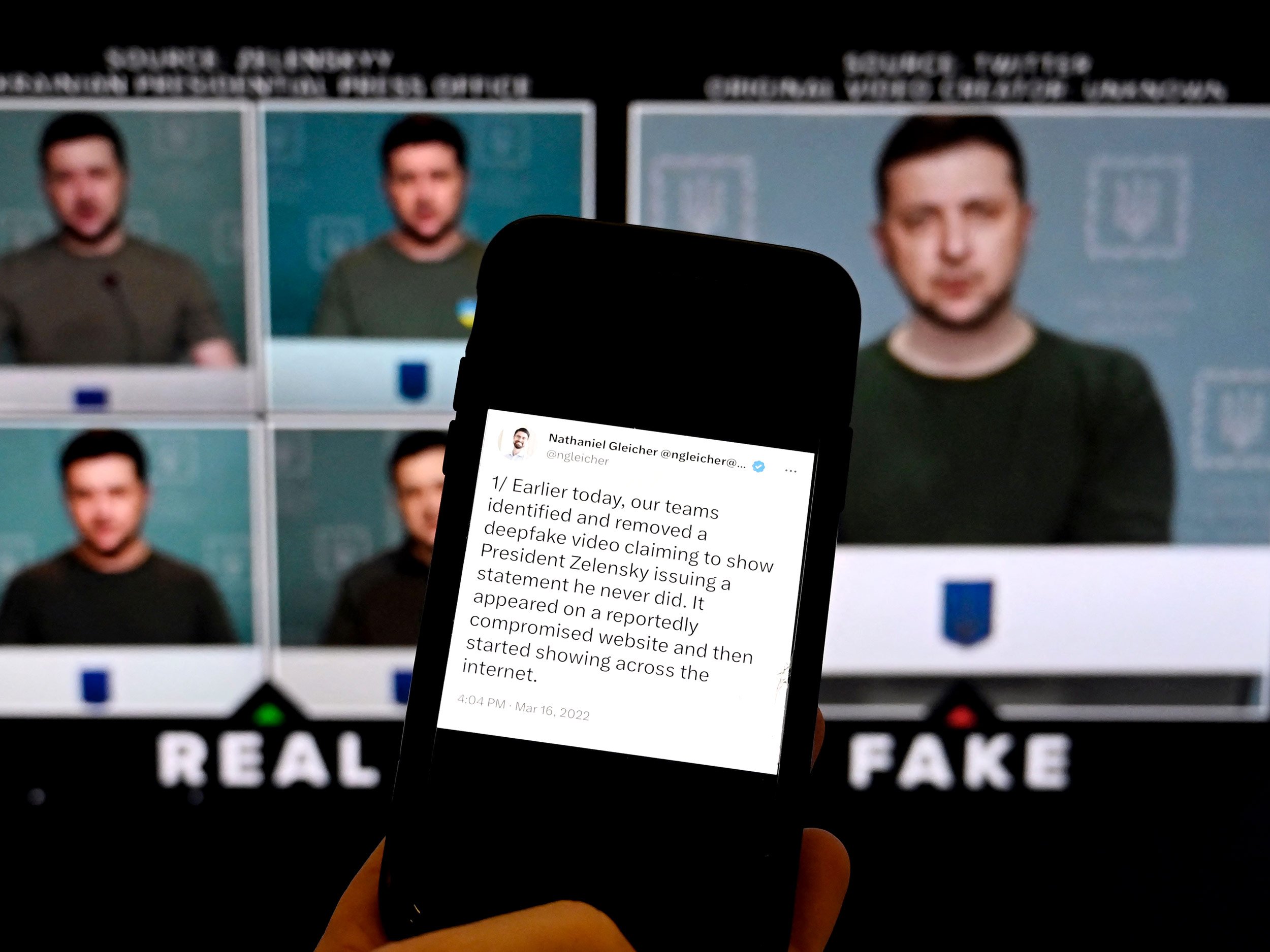
Image Credit: Securityaffairs
Denmark moves to protect personal identity from deepfakes with new copyright law
- Denmark plans to amend its copyright law to give individuals rights over their body, face, and voice to combat AI-generated deepfakes, believed to be the first law of its kind in Europe.
- The proposed law aims to protect individuals from being exploited by generative AI by allowing them to copyright their identity, with support from around 90% of MPs.
- The new law in Denmark will ban realistic AI-generated imitations of artists' performances without consent, with compensation for victims, excluding parody and satire.
- Denmark's Culture Minister emphasized the importance of protecting everyone's right to their own body, voice, and facial features, and plans to push similar initiatives across the EU.
Read Full Article
12 Likes
Securityaffairs
296

Image Credit: Securityaffairs
Ahold Delhaize data breach affected over 2.2 Million individuals
- A ransomware attack on Ahold Delhaize led to a data breach affecting over 2.2 million individuals.
- The breach impacted various US subsidiaries of Ahold Delhaize, exposing personal information such as contact details, financial data, health information, and employment records.
- The company is offering the affected individuals two years of free credit monitoring and identity protection.
- In April 2025, the Inc Ransom group claimed responsibility for the cyberattack, stating that internal data was likely stolen and posted on their leak site.
Read Full Article
17 Likes
Securityaffairs
272
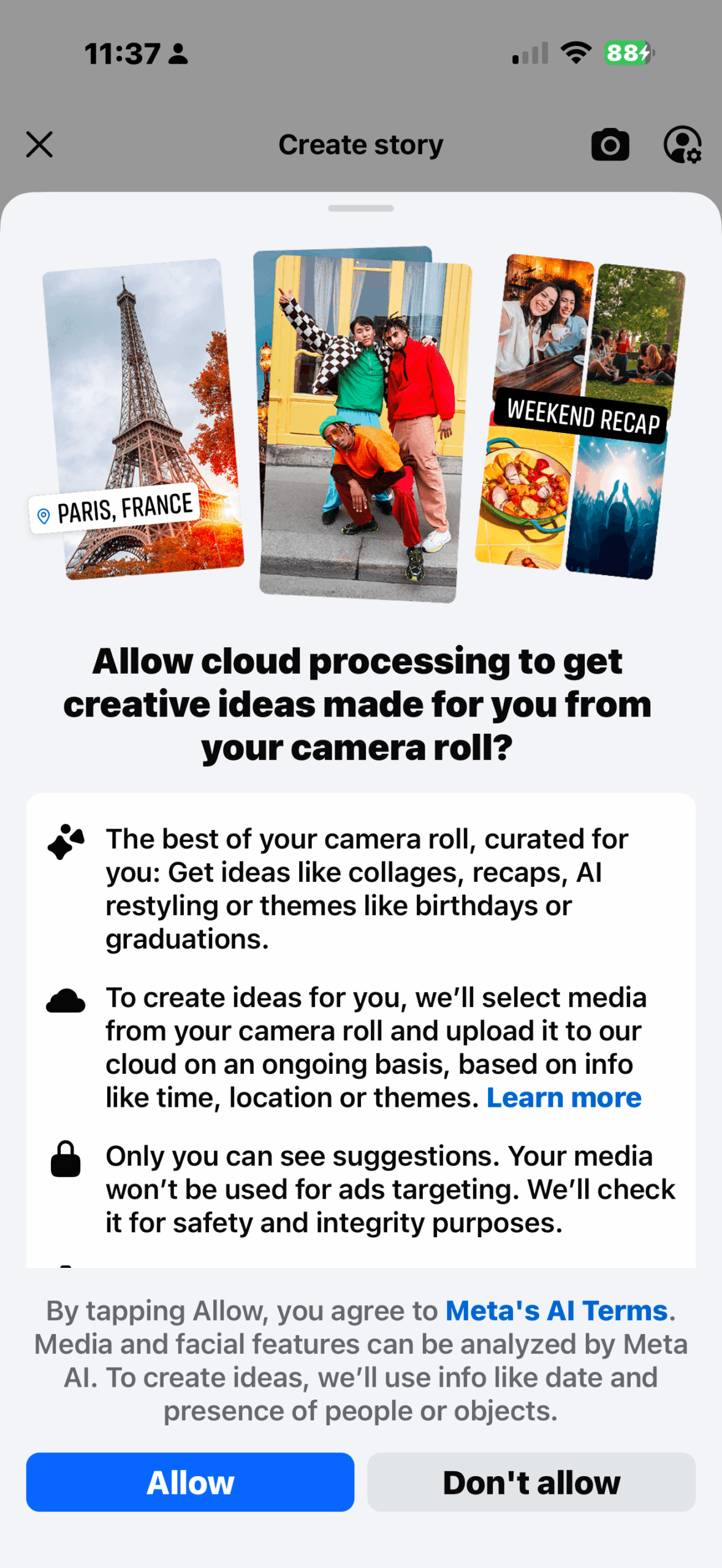
Image Credit: Securityaffairs
Facebook wants access to your camera roll for AI photo edits
- Facebook is asking users to enable 'cloud processing' to access photos from their phones, even those not uploaded.
- By opting into 'cloud processing,' Facebook can continuously upload media to its servers to generate creative suggestions using details like time, location, and theme.
- The new feature poses privacy concerns as users may unwittingly allow Meta to use their media for AI model training without clear consent.
- Meta states that AI-generated photo suggestions are private, not used for ads, and can be turned off at any time; the feature will initially be available only for users in Canada and the US.
Read Full Article
16 Likes
Securityaffairs
193

Image Credit: Securityaffairs
Security Affairs newsletter Round 530 by Pierluigi Paganini – INTERNATIONAL EDITION
- FBI warns of Scattered Spider targeting the airline sector
- China-nexus hackers hijack SOHO devices for espionage
- Critical ISE flaws in Cisco fixed
- Various cyberattacks and data breaches reported worldwide
Read Full Article
11 Likes
Medium
116

Image Credit: Medium
CrossFi Hackathon is Live — Come Build the Future with Us!
- CrossFi is hosting a hackathon to encourage developers, designers, and crypto enthusiasts to create innovations on the CrossFi Chain.
- The hackathon offers a prize pool of $500,000+ in MPX tokens and is open to individuals, teams, and early-stage dApps focusing on DeFi, Infrastructure, and GameFi/NFTs.
- The event is ongoing with free live workshops, mentorship, and community support, aimed at fostering creativity and innovation without any fees.
- Participation in the hackathon provides opportunities to create utility for $XFI, gain support from the ecosystem, earn rewards, and enhance credibility in the Web3 space.
Read Full Article
6 Likes
Hackersking
378

Image Credit: Hackersking
Permissionless Mic & Camera Access Using Chromium Browser
- A new type of phishing attack known as Permissionless Phishing Attack allows access to camera, microphone, and location without user permission.
- By using the Chromium flag --auto-accept-camera-and-mircophone-capture, websites can access camera and microphone automatically.
- Code snippets demonstrate how to capture camera and microphone without user prompts and continuously save camera snapshots using getUserMedia.
- The script sends image data to upload.php for saving and the /var/www/imgCapture folder collects captured images.
Read Full Article
22 Likes
For uninterrupted reading, download the app