Hacking News
Securityaffairs
414

Image Credit: Securityaffairs
U.S. warns of incoming cyber threats following Iran airstrikes
- The U.S. warns of cyber threats by pro-Iranian groups following airstrikes on Iran's nuclear sites amid the Iran-Israel war, raising cyber threat levels in the U.S.
- President Trump calls the attacks a success and warns of more strikes if Iran resists peace.
- The U.S. Department of Homeland Security (DHS) advisory states low-level cyberattacks by pro-Iranian hacktivists and possible state-linked cyber activities.
- The 2025 Iran-Israel war triggers intense cyber conflict, with hacktivist groups from both sides engaging in digital attacks.
- Iran is committed to targeting U.S. officials linked to a 2020 military commander's death, and the Israel-Iran conflict may incite extremist violence in the U.S.
- Recent U.S. attacks connected to anti-Semitic views suggest a rising threat of homeland plots.
- In January 2020, DHS warned of potential cyber-attacks by Iranian threat actors in response to the death of Maj. Gen. Qassim Suleimani by a U.S. drone airstrike.
- The former Director of CISA, Christopher C. Krebs, cautioned about new cyber attacks by Iran-linked groups targeting U.S. assets.
- Operators of critical infrastructure are advised to stay vigilant as the risk of cyber attacks is escalating.
- A new National Terrorism Advisory System bulletin highlights Iran's cyber capabilities to conduct attacks against US infrastructure and warns of operations within the United States.
Read Full Article
24 Likes
Idownloadblog
113

Image Credit: Idownloadblog
Vertex exploit gets updated to support all versions of iOS 14 and 15
- Security researcher @alfiecg_dev updates Vertex exploit to support all versions of iOS 14 and 15.
- Vertex exploit originally teased the Apex jailbreak for select iOS 14 devices.
- The exploit now includes the landa PUAF method, extending support to all iOS 14 and 15 devices.
- Many jailbreakers remain on older firmware to benefit from such developments.
- @alfiecg_dev made the update available on their GitHub page for developers.
- There may be updates for older jailbreaks to incorporate this new exploit.
- The Apex jailbreak could potentially integrate support for the latest Vertex updates.
- @alfiecg_dev previously worked on the Trigon deterministic exploit with a 0% failure rate.
- They were also involved in the development of TrollStore and TrollInstallerX.
- The security researcher continues to make an impact and remains a prominent figure in the jailbreak community.
- Future developments from @alfiecg_dev are eagerly anticipated.
- The Vertex exploit now supports all versions of iOS 14 and 15.
- The exploit includes the landa PUAF method, expanding the range of compatible devices.
- @alfiecg_dev's GitHub page contains information about the updated exploit.
- There might be updates for older jailbreaks to incorporate the new exploit.
- The Apex jailbreak may incorporate support for the latest Vertex updates.
Read Full Article
6 Likes
Idownloadblog
96

Image Credit: Idownloadblog
Pocket Poster v2.0 released with support for video wallpapers, improved UI, & translations for 21+ languages
- iOS developer LeminLimez released Pocket Poster v2.0 with various improvements and new features.
- Pocket Poster allows users to apply custom animated PosterBoard wallpapers on iOS 17.0 and later.
- The update includes support for video wallpapers, a working Reset Collections button, and translations for 21 new languages.
- Major changes in Pocket Poster v2.0 include an improved UI, video wallpapers, auto-reset button, and multi-language support.
- Bug fixes address memory leak issues, improved backend handling, alert problems, error messages, and cache clean up.
- Pocket Poster no longer requires a computer after the initial Nugget installation.
- Users can now set unique wallpapers without jailbreak on non-jailbreakable firmware.
- Interested users can download Pocket Poster v2.0 for free from the project's GitHub page.
Read Full Article
5 Likes
Hackers-Arise
109

Image Credit: Hackers-Arise
Wi-Fi Hacking: Inside DragonFly, the WPA3’s Next-Gen Wireless Authentication Protocol
- WPA3 introduces the Dragonfly protocol for stronger wireless security and authentication.
- WPA2's reliance on Pre-Shared Key (PSK) made networks vulnerable to offline attacks.
- Dragonfly protocol forces live interaction for password guesses, making attacks more difficult to carry out.
- Dragonfly utilizes elliptic curve cryptography or finite field cryptography for enhanced security.
- The protocol ensures perfect forward secrecy, resistance to offline attacks, and mutual authentication.
- Real-world implementation of Dragonfly requires computational effort but is feasible on modern hardware.
- Dragonfly specification is included in IEEE 802.11 and Wi-Fi Alliance documents for interoperability.
- Research continues to address potential side-channel vulnerabilities and implementation bugs.
- Wi-Fi hacking class scheduled on July 22-24 to delve deeper into WPA3 and Dragonfly protocol.
- Overall, Dragonfly protocol enhances wireless security by challenging attackers and emphasizing vigilant defense.
Read Full Article
6 Likes
Securityaffairs
13

Image Credit: Securityaffairs
McLaren Health Care data breach impacted over 743,000 people
- McLaren Health Care experienced a ransomware attack in 2024, exposing personal data of 743,000 individuals.
- The nonprofit health care organization operates in Michigan and discovered the breach on August 5, 2024.
- Names, Social Security numbers, driver's license numbers, health insurance details, and medical information were compromised.
- McLaren is providing affected individuals with 12 months of free credit monitoring services.
- In a previous incident in November 2023, McLaren disclosed a breach affecting 2,192,515 individuals.
- The attackers in the latest breach remain unidentified, and the company did not disclose technical details.
Read Full Article
Like
Bitcoinsensus
419

Image Credit: Bitcoinsensus
Phishing Attacks Hit Top Crypto Sites: CoinMarketCap & CoinTelegraph Affected
- Crypto websites CoinTelegraph and CoinMarketCap experienced security breaches through phishing attacks.
- Reports suggest that a frontend exploit injected malicious code into browsers via compromised ad scripts and third-party widgets.
- Attackers utilized JavaScript vulnerabilities to display a deceptive ad offering fake token airdrops to users.
- Users were prompted to connect wallets, potentially leading to unauthorized asset transfers by a draining program.
- MetaMask flagged CoinTelegraph's website as deceptive during the incident, alerting visitors to possible phishing activities.
- CoinTelegraph quickly addressed the issue, removing the unauthorized code and enhancing security measures.
- It remains unclear if the attacks on CoinTelegraph and CoinMarketCap are connected, though both involved injected malicious scripts from third-party services.
Read Full Article
25 Likes
Securityaffairs
288

Image Credit: Securityaffairs
American steel giant Nucor confirms data breach in May attack
- American steel giant Nucor confirms data breach in May cyberattack.
- Nucor, North America's largest steel maker, disclosed unauthorized access to certain IT systems.
- The company activated its incident response plan and involved law enforcement and cybersecurity experts.
- Limited data was stolen from Nucor's systems during the cyberattack.
- Operations and IT systems have been restored, and the threat actor no longer has access.
- Nucor confirmed no material business or financial impact from the incident.
- The nature of the attack was not specified in the notifications.
- Experts suggest Nucor may have been a victim of a ransomware attack.
- No group has claimed responsibility for the cyberattack on Nucor.
- The incident is being monitored for any further developments.
- Nucor is reviewing and evaluating the impacted data for potential notifications.
- The company is committed to complying with regulatory requirements following the cyber incident.
- Nucor believes it has addressed the cybersecurity incident and restored normal operations.
- The cybersecurity incident did not have a significant impact on Nucor's business or finances.
- Nucor continues to assess its cybersecurity measures to prevent future incidents.
Read Full Article
17 Likes
Securityaffairs
2.4k
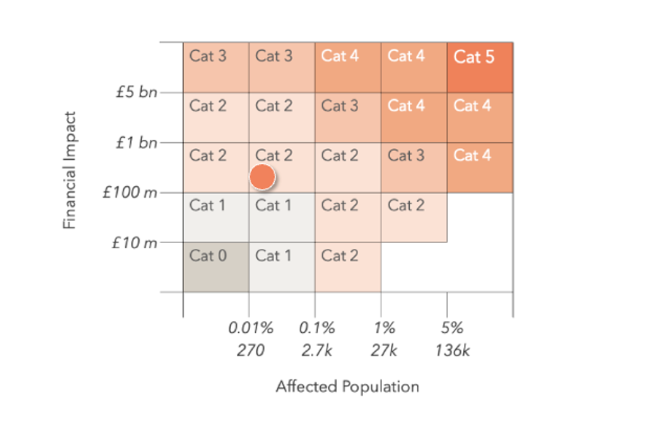
Image Credit: Securityaffairs
The financial impact of Marks & Spencer and Co-op cyberattacks could reach £440M
- The Cyber Monitoring Centre (CMC) has categorized cyberattacks on Marks & Spencer and Co-op as a Category 2 event, with estimated financial losses between £270M and £440M.
- Hackers named DragonForce claimed responsibility for the Co-op attack, accessing data of current and past members.
- Co-op initially denied customer data compromise but later confirmed data breach.
- DragonForce also targeted M&S and confessed to trying to hack Harrods, accessing staff and customer data.
- The attack exposed personal details of Co-op members but did not include sensitive information like passwords or financial data.
- DragonForce is known for ransomware attacks, data theft, and running a cybercrime affiliate service.
- The CMC linked M&S and Co-op attacks due to shared timing and threat actor, estimating total financial impact at £270M–£440M.
- The attacks caused major business disruption and financial consequences for M&S and Co-op.
- Estimated costs include legal fees, business interruption, incident response, and IT restoration for both companies.
- M&S anticipates a £300M impact, with significant declines in online sales and consumer spending.
- The incidents emphasized the vulnerability of retail supply chains and the importance of crisis preparedness and cyber resilience.
- CMC stresses the need for stress-testing crisis plans, financial resilience, enhanced cyber hygiene, and access control improvement.
- Clear crisis communication and robust recovery capabilities are essential during cyber incidents.
- CMC aims to enhance cyber readiness through collaboration and transparency.
- The financial impact of the M&S and Co-op cyberattacks highlights the widespread repercussions of cyber incidents in the retail sector.
Read Full Article
1 Like
Securityaffairs
48

Image Credit: Securityaffairs
Iran-Linked Threat Actors Cyber Fattah Leak Visitors and Athletes’ Data from Saudi Games
- Iran-linked threat actors known as Cyber Fattah have leaked thousands of records on athletes and visitors from past Saudi Games, as reported by U.S.-based cybersecurity firm Resecurity.
- The stolen data, leaked in the form of SQL dumps, includes personal information about visitors and athletes from the Saudi Games.
- Resecurity views this incident as part of a broader information operation conducted by Iran and its proxies to instill insecurity and disrupt peace in the region.
- Iran is increasing anti-US, anti-Israel, and anti-Saudi propaganda activities in cyberspace, targeting major sports and social events.
- The incident is significant amidst escalating tensions between Israel and Iran, with threat actors leveraging the roles of Saudi Arabia and the United States in regional relationships and security.
- Hezbollah-linked, Hamas-linked, and pro-Iranian groups in Iraq have amplified the incident through targeted propaganda activities on digital media channels.
- The data originates from a database associated with the Saudi Games 2024 official website, containing personal information such as International Bank Account Numbers (IBANs) and medical examination certificates.
- The breach poses serious implications for cybersecurity, sports integrity, and global audiences.
- No confirmed date yet for the Saudi Games 2025, with Saudi Arabia hosting various major sports events like the Islamic Solidarity Games and Esports World Cup 2025.
- Saudi Arabia aims to host the Olympics in 2036, with threat actors potentially targeting the reputation and efforts of the country through cyberattacks.
- The cyberattack on the Saudi Games is part of a broader narrative aimed at spreading insecurity and disrupting peace in the region.
- The incident underscores the vulnerability of major sports competitions to cyber threats and serves as a reminder of the importance of safeguarding sensitive data.
- For more information, follow Pierluigi Paganini on Twitter: @securityaffairs, Facebook, and Mastodon.
- Credit: SecurityAffairs - hacking, Cyber Fattah
Read Full Article
2 Likes
Securityaffairs
315
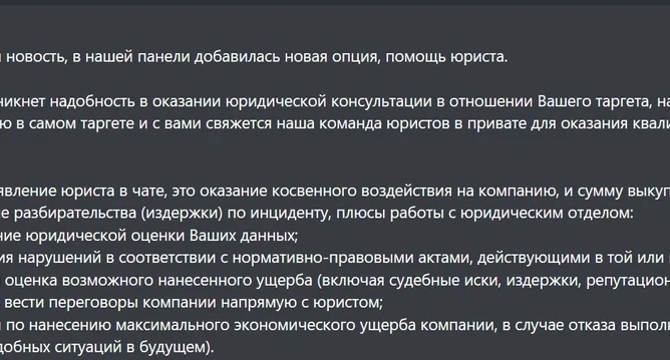
Image Credit: Securityaffairs
Qilin ransomware gang now offers a “Call Lawyer” feature to pressure victims
- The Qilin ransomware group now offers a "Call Lawyer" feature to provide legal support to affiliates and pressure victims into paying, as reported by cybersecurity firm Cybereason.
- Qilin, active since at least August 2022 and gaining attention in June 2024 for attacking a UK governmental service provider, uses double extortion tactics and takes a percentage of ransom payments.
- Affiliates are ordered not to target systems in CIS countries like other ransomware operations.
- Qilin is positioning itself as a full-service cybercrime platform, offering advanced tools, legal support, spam services, and large data storage.
- The "Call Lawyer" feature increases pressure on victims during ransom negotiations by offering legal consultations and introducing legal risks.
- By introducing network spreading and a DDoS option, Qilin demonstrates sophistication and adaptability in various cyberattack scenarios.
- A translation of the ransomware group's text explains how the "Call Lawyer" feature works to increase ransom amounts and apply legal pressure on companies.
- Qualys also highlights the strong operational model and legal support provided by Qilin to clients for successful ransomware payouts.
- The Qilin ransomware group is intensifying its activity, as shown by a heatmap reporting host compromises.
- Organizations are advised to adopt proactive measures to defend against sophisticated threats like Qilin ransomware, as per Qualys' recommendations.
- Qilin ransomware group's strategy includes legal support, incentives, and technology for successful ransom payouts.
- Cybereason's report emphasizes Qilin's emergence as a major ransomware player, offering more than just malware and aiming to lead the next wave of ransomware-as-a-service operations.
Read Full Article
18 Likes
Hackers-Arise
407

Image Credit: Hackers-Arise
SCADA/ICS Security in Cyber Warfare: Exposing Vulnerabilities in Russian ICS Infrastructure
- Russian industrial control systems (ICS) vulnerabilities are explored in this article.
- SCADA systems, like PLCs, are susceptible to cyberattacks due to their reliance on networks.
- SCADA systems oversee and control industrial operations from a distance through PLCs.
- PLCs manage machinery based on sensor data and programming instructions.
- Accessing Russian PLCs is demonstrated to be relatively simple in the article.
- Steps involve finding systems with 401 responses using tools like Shodan.
- Filtering and brute forcing methods are employed to identify vulnerable systems.
- Changes to emergency thresholds and sensor settings can be made once access is gained.
- The importance of mindset and practices in securing critical infrastructure is emphasized.
- A call to action for improved cybersecurity practices in ICS is made.
- The article highlights the potential for cyber warfare through exploiting ICS vulnerabilities.
- Defensive strategies like cascading failures or subtle damage are mentioned.
- Technological solutions alone are not enough; changing practices is crucial for security.
- The post emphasizes the need for critical infrastructure security awareness and improvements.
- Russian ICS infrastructure vulnerabilities are showcased through the demonstration.
- The article concludes by underlining the importance of mindset shift for security in critical systems.
Read Full Article
24 Likes
Hackers-Arise
210

Image Credit: Hackers-Arise
If The US Attacks Iran, Will Iran Attack US Industrial Facilities (SCADA/ICS)?
- Iran may use cyber operations to counter a potential US kinetic attack, targeting industrial facilities like SCADA/ICS.
- Iran lacks military capabilities but excels in cyberwarfare, leveraging asymmetric strategies against technologically superior nations.
- SCADA/ICS attacks by Iran could disrupt economy, water, electricity, communication, and manufacturing, similar to tactics in Ukraine/Russia conflict.
- Iran's history includes cyber operations targeting US infrastructure, such as financial institutions, dams, hospitals, and critical infrastructure.
- Specific incidents include DDoS attacks on banks, SCADA system intrusions, healthcare sector targeting, and critical infrastructure malware campaigns.
- Iran's cyber threats extend to brute-force attacks, ransomware extortion, and malware deployment against US critical sectors like water and energy.
- Iran's cyberwarfare poses ongoing risks to US industrial control systems, emphasizing the need for vigilance and security measures.
- Amid rising tensions, Iran's cyber capabilities make them likely to retaliate through cyber means in response to any US military actions.
- The article suggests a unique training program for SCADA/ICS hacking and security to understand and counter potential cyber threats from Iran.
Read Full Article
12 Likes
Securityaffairs
311
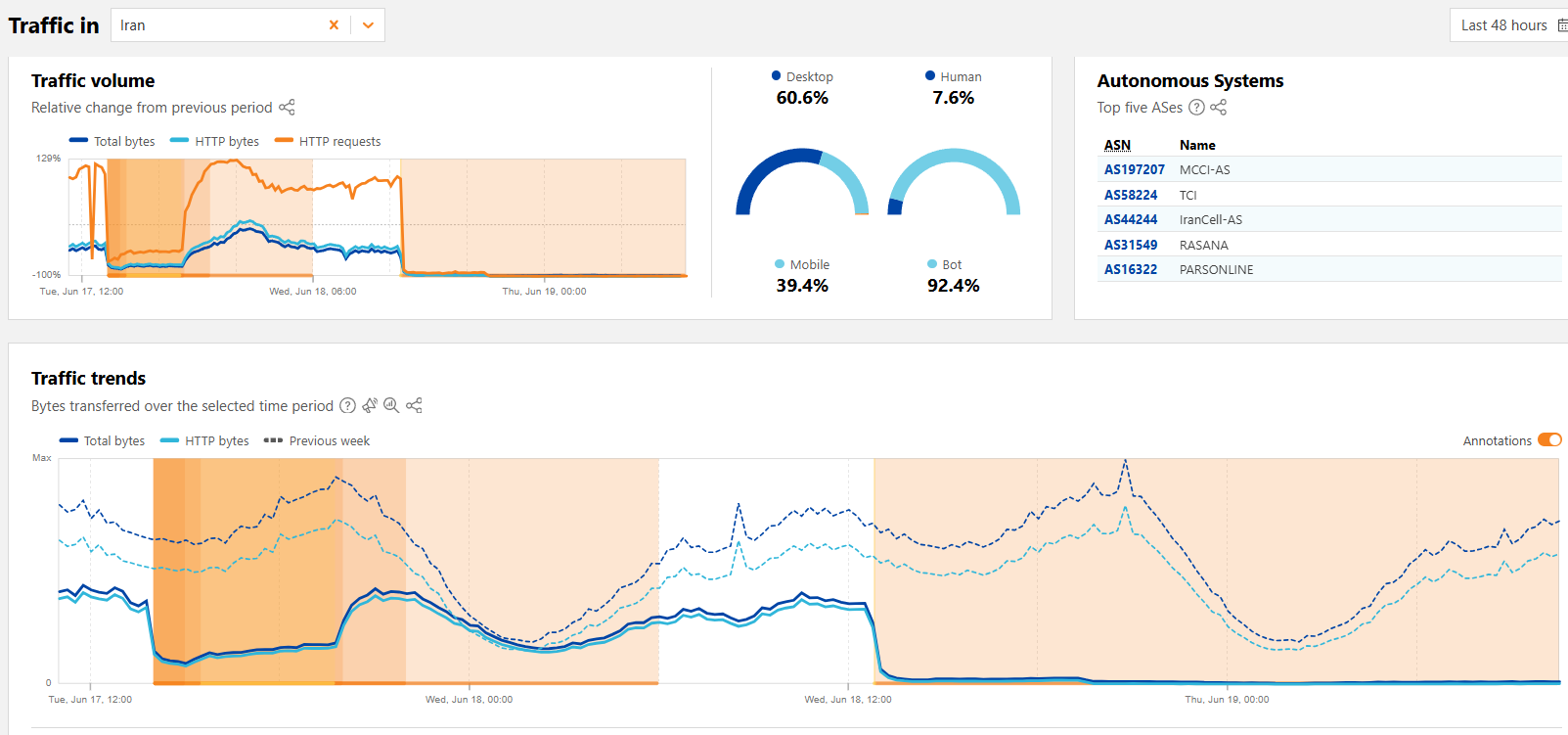
Image Credit: Securityaffairs
Iran confirmed it shut down internet to protect the country against cyberattacks
- Iran confirmed an internet shutdown to counter Israeli cyberattacks aimed at protecting critical infrastructure and preventing drone interference.
- The internet blackout in Iran occurred amid escalating military tensions with Israel, impacting the country's communication and information access.
- The exact cause of the internet shutdown remains uncertain, with no definitive evidence linking it to a technical failure, deliberate government action, or external cyber operation.
- The Iranian government has acknowledged ordering the shutdown to safeguard against cyberattacks, citing threats to infrastructure and drone control.
- Reports indicate that enemy drones were controlled through the internet, prompting the restriction to ensure national security and prevent further disruptions.
- The internet blackout followed cyberattacks on Iranian institutions, including the hacking of Iran's largest crypto exchange and disruptions in banking services.
- A pro-Israel hacking group, 'Predatory Sparrow,' claimed responsibility for the cyberattacks on Iran, targeting financial institutions and crypto exchanges.
- The group accused Iran of using crypto exchanges to evade sanctions and claimed to have destroyed data at Iran's state-owned Bank Sepah, leading to potential banking disruptions.
- Cybersecurity firms confirmed the theft of crypto assets and their transfer to accounts referencing Iran's Revolutionary Guard Corps, highlighting the ongoing cyber warfare.
Read Full Article
18 Likes
Hackingblogs
140

Image Credit: Hackingblogs
FREE NOTES API-HACKING DAY 3: Finding Anyones’s Location In crAPI Using EDE & Bola Bugs
- API-HACKING: Excessive Data Exposure bug occurs when an API returns more data than required for a user.
- Sensitive data may be exposed when APIs return unnecessary information.
- Examples of attack scenarios due to Excessive Data Exposure bug are discussed.
- Exploiting the vulnerability using crAPI to access private information is explained.
- Chaining Excessive Data Exposure with BOLA vulnerabilities to reveal car location is described.
- An attacker could exploit the two vulnerabilities to find someone's car location.
- Using Burp Suite, the attacker could access leaked sensitive data like VIN numbers and car locations.
- The Excessive Data Exposure flaw and BOLA weakness are exploited to gather information about a car's location.
- By chaining the vulnerabilities, the attacker successfully retrieves location details using the VIN number.
- The report highlights the risks of data exposure and methods for detecting and addressing security breaches.
- Real-time threat feeds are utilized to monitor for data exposure and potential impersonation risks.
- The platform offers alerts and reports on leaked data, importance of the breach, and steps to mitigate risks.
Read Full Article
8 Likes
Guardian
206
Image Credit: Guardian
Internet users advised to change passwords after 16bn logins exposed
- Internet users are advised to change passwords and enhance digital security after 16 billion login records were exposed by researchers.
- Research by Cybernews revealed 30 datasets containing credentials from 'infostealers' and leaks, potentially exposing login details for services like Facebook, Apple, and Google.
- There was no centralized data breach at the companies mentioned, with the exposed data being briefly available due to poor storage on remote servers.
- Cybersecurity specialist Bob Diachenko discovered and downloaded the files and plans to notify affected individuals and companies.
- Google stated that the reported data did not result from a Google breach, recommending people to use tools like Google’s password manager for protection.
- Internet users can check if their email was compromised using haveibeenpwned.com, with the leaked datasets following a clear structure of URL, login details, and passwords.
- The data mainly consisted of infostealers and a small portion from previous breaches like LinkedIn, emphasizing the importance of regular password updates and strong security measures.
- Experts advise implementing multifactor authentication and password managers to mitigate credential issues from data leaks.
- The exposed data highlights the vast amount accessible to cybercriminals, prompting proactive security steps for individuals and organizations.
- Infostealers are real threats that scrape information like browser cookies and metadata, but following cybersecurity best practices can help mitigate risks.
- The datasets, described as blueprints for mass exploitation, present risks like identity theft and phishing, emphasizing the need for stringent security measures.
- Experts recommend updating passwords regularly and adopting zero trust security measures to combat increasing data breaches.
Read Full Article
12 Likes
For uninterrupted reading, download the app