Hacking News
Siliconangle
198

Image Credit: Siliconangle
Ingram Micro confirms ransomware attack disrupted systems over July 4 weekend
- Ingram Micro Holding Corp. was targeted by a ransomware attack over the July 4 weekend, resulting in service disruptions.
- The attack involved the SafePay ransomware group known for double extortion tactics, encrypting data and stealing it for ransom payment.
- Ingram Micro took systems offline, engaged cybersecurity experts, and notified law enforcement to investigate and restore affected systems.
- Concerns have been raised among customers regarding potential data breaches, with efforts underway to improve identity security against such attacks.
Read Full Article
11 Likes
Medium
74

Image Credit: Medium
The true cost of free: Why I Finally Started Paying for Softwares and games
- A personal journey from believing in free software to understanding its hidden costs.
- Discovered cryptominers hidden in 'free' software, risking personal data and security.
- Raised awareness on the dangers of downloading cracked files and the importance of paid software.
- Switched to paying for software and games for peace of mind and self-preservation.
Read Full Article
4 Likes
Securityaffairs
153
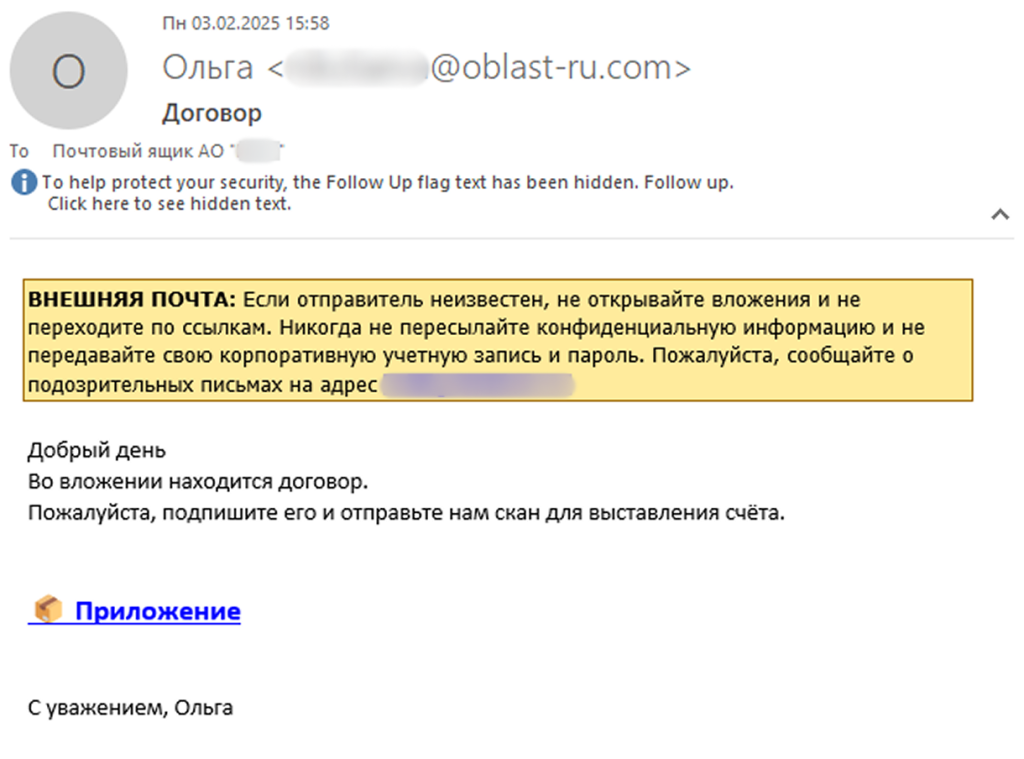
Image Credit: Securityaffairs
New Batavia spyware targets Russian industrial enterprises
- A new spyware named Batavia is being spread through fake contract-themed emails targeting Russian organizations since March 2025.
- The spyware includes a VBA script and two executables, detected by Kaspersky as Trojan.Batavia variants, designed to steal internal documents.
- The attack involves multiple stages where the malware collects system info, spies on the system by capturing screenshots and exfiltrating data to a command-and-control server.
- The victims of the Batavia spyware campaign are Russian industrial enterprises, with over 100 users across multiple organizations falling prey to the phishing messages.
Read Full Article
9 Likes
Hackers-Arise
12

Image Credit: Hackers-Arise
Can Hackers “See” Inside Your Home Using Wi-Fi to Track Your Location and Movement?
- Recent technological developments in artificial intelligence and Signal Intelligence (SDR) allow hackers to 'see' through walls using Wi-Fi signals to track the location and movement of individuals.
- By analyzing how Wi-Fi signals bounce back after encountering objects, it's possible to detect the presence, movement, and shape of individuals behind walls.
- The process involves using standard Wi-Fi routers, Software-Defined Radios (SDRs), multiple antennas, and AI algorithms to collect and process Channel State Information (CSI) data to reconstruct human poses.
- Wi-Fi sensing has real-world applications in security, elder care, smart homes, law enforcement, and intelligence agencies, but raises major privacy and legality concerns.
Read Full Article
Like
Securityaffairs
78

Image Credit: Securityaffairs
Taiwan flags security risks in popular Chinese apps after official probe
- Taiwan's National Security Bureau (NSB) warns that Chinese apps like TikTok and WeChat pose security risks due to excessive data collection and data transfers to China.
- NSB coordinated with other agencies to inspect popular Chinese apps and found violations of security standards, advising caution when using such apps.
- Five China-made apps were found to violate key security standards, collecting personal data without consent and transferring it to servers in China.
- Taiwanese authorities emphasize the risks of data misuse and privacy infringement posed by Chinese apps, similar to concerns expressed by other countries like the US and the EU.
Read Full Article
4 Likes
Silicon
149
Image Credit: Silicon
Hackers Steal Data From Louis Vuitton Korea
- Hackers compromised Louis Vuitton Korea's IT systems in June, accessing some data, including customer information.
- No financial data such as payment card or bank account details were included in the breach, and the incident has been contained.
- Louis Vuitton Korea is investigating the attack, has notified authorities, and is enhancing system security along with working with third-party experts.
- Considering recent breaches affecting luxury brands like Louis Vuitton and airlines like Qantas, cybersecurity threats continue to evolve, with hackers targeting sensitive data for ransom purposes.
Read Full Article
8 Likes
Securelist
207

Image Credit: Securelist
Batavia spyware steals data from Russian organizations
- Increase in detections of files like договор-2025-5.vbe, приложение.vbe, and dogovor.vbe.
- Targeted attack through bait emails with malicious links to infect Russian organizations.
- Batavia spyware steals internal documents in a three-stage infection process.
- Malware components include VBS script, executables like WebView.exe and javav.exe.
- Kaspersky detects files as HEUR:Trojan.VBS.Batavia.gen and HEUR:Trojan-Spy.Win32.Batavia.gen.
Read Full Article
12 Likes
Securityaffairs
220

Image Credit: Securityaffairs
U.S. CISA adds Google Chromium V8 flaw to its Known Exploited Vulnerabilities catalog
- U.S. CISA added the Chromium V8 vulnerability, tracked as CVE-2025-6554, to its Known Exploited Vulnerabilities catalog.
- Google released security patches for the Chrome vulnerability CVE-2025-6554 following its discovery by Clément Lecigne.
- The vulnerability is a type-confusing issue in the V8 JavaScript and WebAssembly engine, allowing for arbitrary read/write access.
- CVE-2025-6554 is the fourth Chrome zero-day patched in 2025, emphasizing the importance of addressing known vulnerabilities to prevent attacks.
Read Full Article
13 Likes
Hackers-Arise
333

Image Credit: Hackers-Arise
SCADA Hacking: Inside Russian SCADA/ICS Facilities
- SCADA systems control critical infrastructure and industrial processes, often lack basic protections.
- Russian SCADA software outdated, unpatched, vulnerable to cyber attacks due to obsolete technology.
- Most SCADA applications contain vulnerabilities, increasing risks to industrial processes and infrastructure.
- Attacks targeting industrial control systems rising, lack of proper security measures exacerbating issues.
Read Full Article
20 Likes
Securityaffairs
154
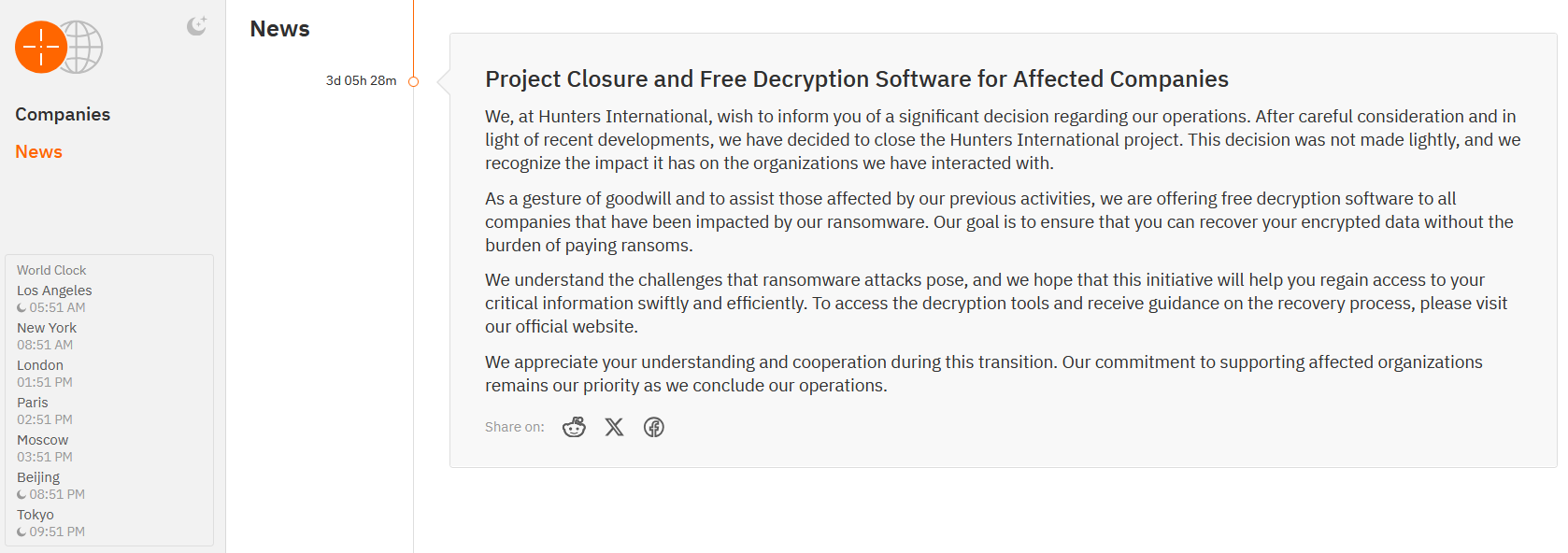
Image Credit: Securityaffairs
Hunters International ransomware gang shuts down and offers free decryption keys to all victims
- Hunters International ransomware gang has announced its shutdown, citing unspecified 'recent developments' and acknowledging its impact.
- The group is offering free decryption software to all companies impacted by their ransomware as a gesture of goodwill.
- There is speculation that Hunters International may rebrand itself into a new group called World Leaks to avoid law enforcement tracking.
- The group emerged after the Hive gang's infrastructure was seized, with Hunters International suspected to be a rebrand of the Hive ransomware gang.
Read Full Article
9 Likes
Securityaffairs
388

Image Credit: Securityaffairs
Security Affairs newsletter Round 531 by Pierluigi Paganini – INTERNATIONAL EDITION
- North Korea-linked threat actors spread macOS NimDoor malware via fake Zoom updates.
- Google fined $314M for misusing idle Android users’ data.
- Cybercriminals target Brazil in a data breach affecting 248,725 people.
- Denmark introduces new copyright law to protect against deepfakes.
Read Full Article
23 Likes
Securityaffairs
360

Image Credit: Securityaffairs
North Korea-linked threat actors spread macOS NimDoor malware via fake Zoom updates
- North Korea-linked threat actors are spreading macOS NimDoor malware disguised as fake Zoom updates to target Web3 and crypto firms.
- Victims are lured into installing the backdoor via phishing links sent through Calendly or Telegram, allowing the malware to steal data like browser history and Keychain credentials.
- The malware, written in Nim, employs encrypted communications, can persist on systems, reinfect itself, and uses process injection techniques along with WebSocket C2 communications for exfiltration.
- The attackers use a unique mix of AppleScript, C++, and Nim in the NimDoor malware, initiating attacks through fake Zoom invites, with two Mach-O binaries dropped to ensure persistence and data theft.
Read Full Article
21 Likes
Hackers-Arise
335

Image Credit: Hackers-Arise
Bash Scripting: Mastering Debugging of Our Password Cracking Script
- Learn how to debug a password cracking script using Bash scripting.
- Create a simple password cracking tool inspired by John the Ripper.
- Develop a script to hash dictionary words and compare with provided hash.
- Explore debugging techniques like echo statements, tracing, and error handling for improvement.
Read Full Article
20 Likes
Medium
147

Image Credit: Medium
How I Ended Up in Cybersecurity (And How You Can Too)
- The author's journey into cybersecurity began with creative coding, developing an 8-bit game using Python and Pygame.
- Driven by curiosity, the author transitioned from coding to cybersecurity with a hacker mindset of exploring the limits of systems.
- The author emphasizes the importance of hands-on experience in cybersecurity, recommending guided labs, learning core tools, building a portfolio, and engaging with the community.
- While certifications like Certified Penetration Testing Specialist (CPTS) can be beneficial, the author highlights that they are just checkpoints in the cybersecurity journey.
Read Full Article
8 Likes
Securityaffairs
54

Image Credit: Securityaffairs
Critical Sudo bugs expose major Linux distros to local Root exploits
- Critical Sudo bugs have been discovered that allow local users to gain root access on Linux systems.
- The vulnerabilities, named CVE-2025-32462 and CVE-2025-32463, affect major Linux distributions.
- CVE-2025-32462 allows executing commands on unintended machines, while CVE-2025-32463 lets local users obtain root access through user-controlled directories.
- The Stratascale Cyber Research Unit found the vulnerabilities, with a fix limiting the --host option and deprecating the chroot feature in Sudo.
Read Full Article
3 Likes
For uninterrupted reading, download the app