Hacking News
Hackers-Arise
35

Image Credit: Hackers-Arise
CyberWar! Taking Over a Russian Corporate Mail
- Learn about a cyberattack on a Russian company's corporate mail system.
- Details on bypassing security measures like 2FA using tools like LaZagne.
- Exploration of network traffic analysis to uncover vulnerabilities and gain access.
- The post emphasizes the importance of monitoring internal traffic for potential compromises.
Read Full Article
2 Likes
Securityaffairs
147

Image Credit: Securityaffairs
U.S. CISA adds Citrix NetScaler ADC and Gateway flaw to its Known Exploited Vulnerabilities catalog
- The U.S. Cybersecurity and Infrastructure Security Agency (CISA) has added Citrix NetScaler ADC and Gateway flaw, known as CVE-2025-5777, to its Known Exploited Vulnerabilities catalog.
- The 'CitrixBleed 2' vulnerability with a CVSS v4.0 Base Score of 9.3 allows attackers to steal session cookies, similar to a past critical exploit.
- The flaw impacts NetScaler ADC and Gateway versions before specific fixed versions, exposing memory and potentially sensitive information.
- Citrix recommends updating to mitigate the risk as attacks exploiting CVE-2025-5777 have been observed since mid-June, with federal agencies required to address vulnerabilities by July 11, 2025.
Read Full Article
8 Likes
Medium
236

How to become a “HACKER”
- Avoid falling for shortcuts and clickbait promising quick hacking success; focus on real skills and knowledge instead.
- Start by mastering the basics of cybersecurity with courses like CompTIA Security+ and CompTIA Network+.
- Progress to hands-on skills through certifications like eJPT and choose a specialization in either Red Team (Attacker) or Blue Team (Defender).
- Author shares personal experience to guide beginners in cybersecurity, urging them to follow a genuine learning path to succeed.
Read Full Article
14 Likes
Securityaffairs
136

Image Credit: Securityaffairs
UK NCA arrested four people over M&S, Co-op cyberattacks
- UK NCA arrests 4, including 3 teens, linked to cyberattacks on M&S, Co-op, and Harrods.
- Arrested individuals seized in London and West Midlands for Computer Misuse Act offenses.
- Suspects face charges of blackmail, money laundering, and organized crime participation.
- Attacks caused major disruptions and financial losses for affected businesses.
- DragonForce group behind attacks, stealing data and demanding ransom from victims.
Read Full Article
8 Likes
Securityaffairs
24
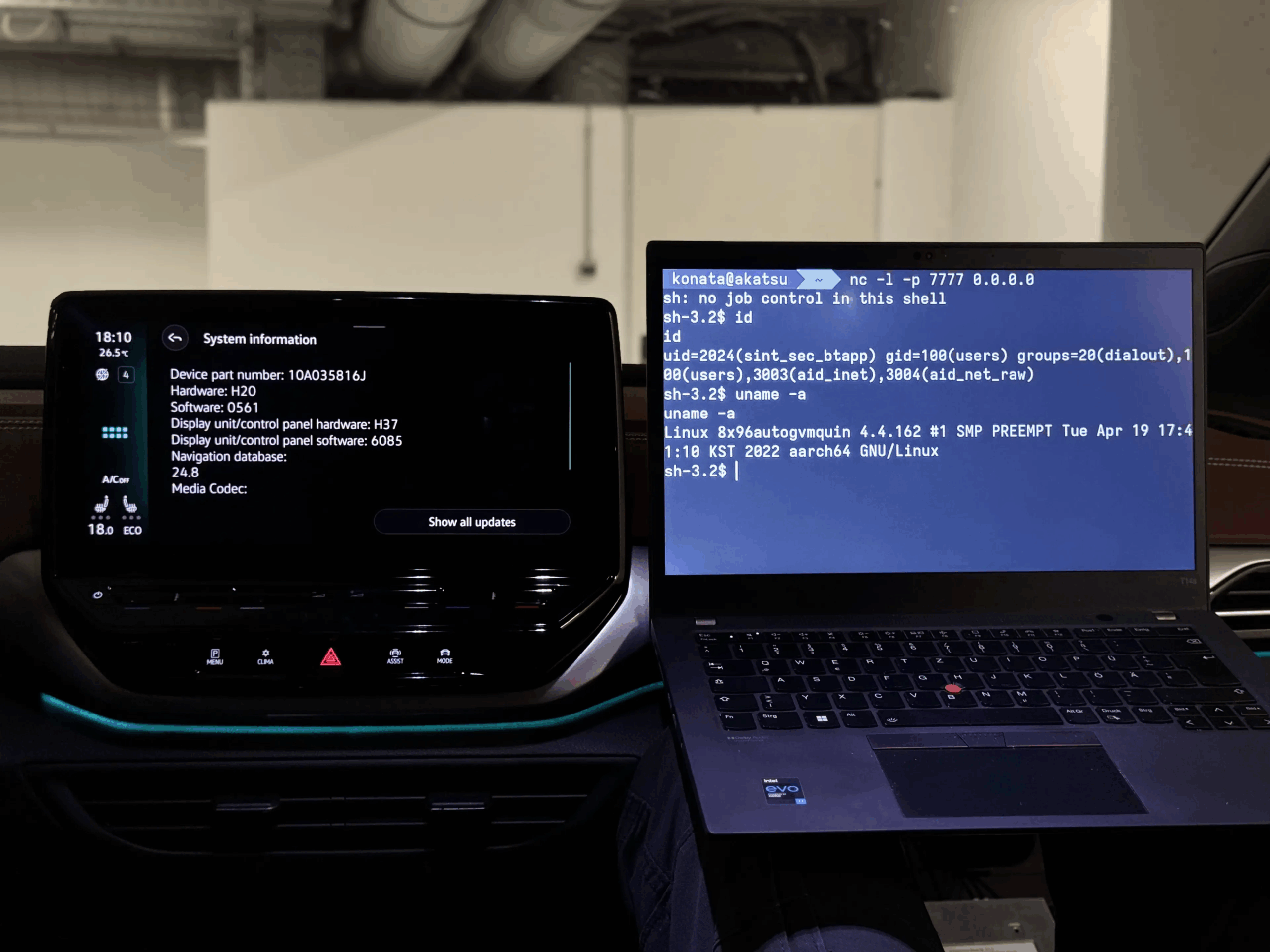
Image Credit: Securityaffairs
PerfektBlue Bluetooth attack allows hacking infotainment systems of Mercedes, Volkswagen, and Skoda
- Researchers discovered critical vulnerabilities, named PerfektBlue, in OpenSynergy BlueSDK Bluetooth stack, which could lead to remote code execution in millions of vehicles' systems.
- The vulnerabilities could allow attackers to hack into car infotainment systems remotely, potentially enabling access to sensitive data and control over functions like location tracking and audio recording.
- The OpenSynergy BlueSDK Bluetooth framework, widely used in automotive applications, is found in vehicles from vendors like Mercedes-Benz, Volkswagen, and Skoda.
- Affected vendors have received patches to address the vulnerabilities, and responsible disclosure was conducted to raise awareness and encourage timely remediation within the automotive industry.
Read Full Article
1 Like
Hackers-Arise
24

Image Credit: Hackers-Arise
SCADA Hacking: Inside Russian SCADA/ICS Facilities, Part 2
- Continuing the SCADA hacking series, accessing a Russian water tower SCADA system.
- Through password reuse and weak security, compromising a range of SCADA systems.
- Detailed infiltration process, from cracking hashes to accessing critical water towers infrastructure.
Read Full Article
1 Like
Securelist
395

Image Credit: Securelist
Code highlighting with Cursor AI for $500,000
- Attacks using malicious open-source packages are a growing threat in cybersecurity.
- A recent incident involving a fake Solidity Language extension highlights the dangers.
- The fake extension tricked developers, leading to data theft and remote control access.
- Similar attacks with different malicious packages have been identified targeting blockchain developers.
- Caution is advised when downloading open-source tools to prevent malware infections.
Read Full Article
23 Likes
Securityaffairs
320

Image Credit: Securityaffairs
Qantas data breach impacted 5.7 million individuals
- Qantas confirmed data breach impacted 5.7 million customers via third-party platform.
- Hackers accessed a call centre platform stealing names, emails, phone numbers, birth dates.
- Qantas assures no financial data or passwords were affected in the incident.
- Approximately 5.7M unique customers impacted; no credit card or passport info accessed.
- Qantas now contacting affected customers to inform them and offer necessary support.
Read Full Article
19 Likes
Hackersking
64

Image Credit: Hackersking
Exploring the Future of Communication and Travel with Apple Teleport
- Apple Teleport is a speculative concept suggesting futuristic technology Apple may pursue.
- It envisions swift data and physical teleportation using quantum and spatial computing.
- Potential applications include immersive work environments, global education accessibility, and robotic surgery.
- Despite exciting possibilities, obstacles like global infrastructure, privacy, and cost need addressing.
- While still speculative, Apple's focus on AR and spatial computing hints at immersive experiences.
Read Full Article
3 Likes
Hackersking
39

Image Credit: Hackersking
What Does the Green Dot Mean on Snapchat? A Complete Guide to Its Meaning and Use
- Snapchat's green dot indicates online status of users for real-time interaction.
- It aids in promoting engagement by showing when friends are active on the app.
- Users can disable the green dot to maintain privacy in their activity status.
- Understanding the difference between green dot and Snap Map location tracking.
- Green dot doesn't confirm message reading; it's solely an active indicator.
Read Full Article
1 Like
Securityaffairs
337
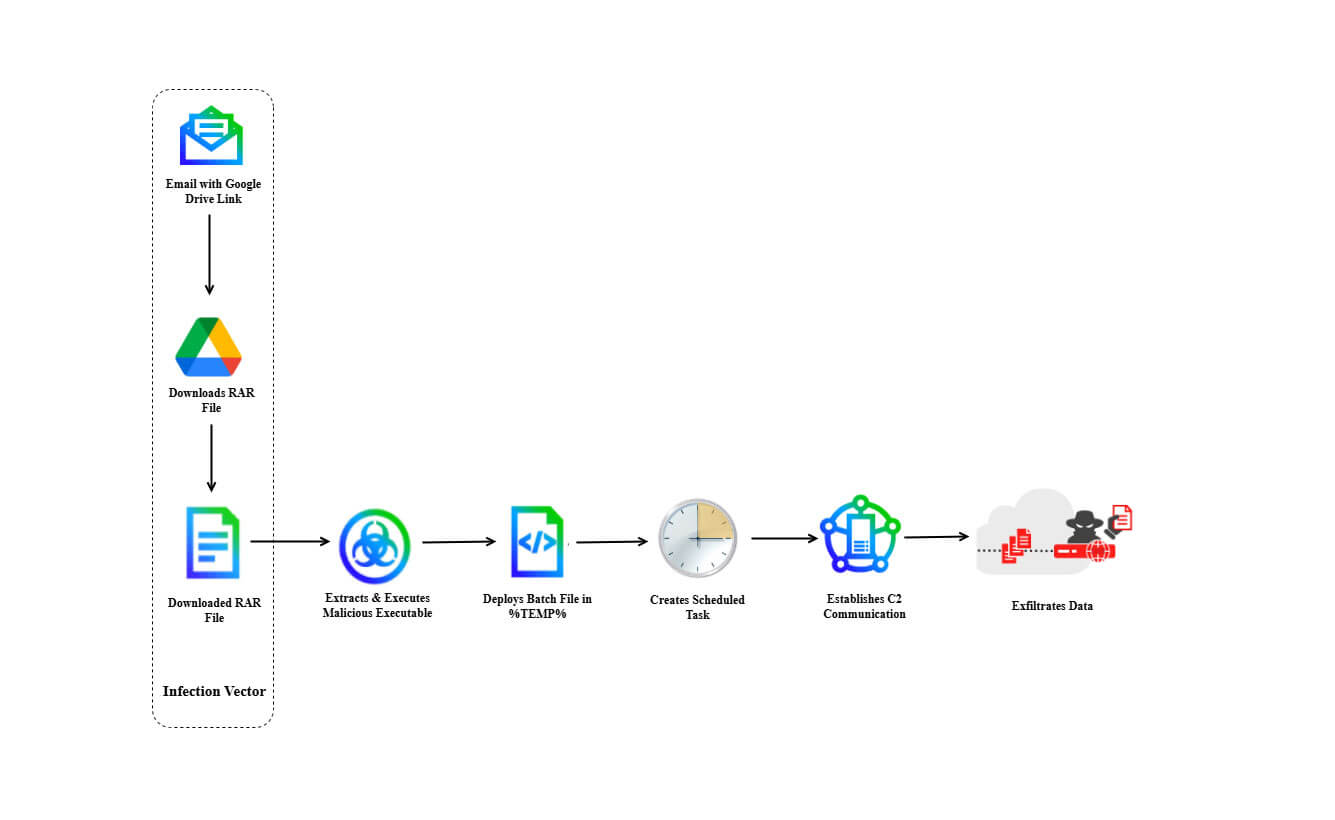
Image Credit: Securityaffairs
DoNot APT is expanding scope targeting European foreign ministries
- DoNot APT, likely linked to India, targets European foreign ministries with new malware LoptikMod.
- The group, active since 2016, focuses on government entities, foreign ministries, defense organizations, and NGOs in South Asia and Europe.
- DoNot APT conducts espionage via phishing, using LoptikMod malware for data theft in recent campaigns.
- The malware uses sophisticated techniques, such as binary string obfuscation and deceptive emails, reflecting the group's ongoing espionage efforts.
Read Full Article
20 Likes
Securityaffairs
98

Image Credit: Securityaffairs
Nippon Steel Solutions suffered a data breach following a zero-day attack
- Nippon Steel Solutions, a subsidiary of Japan’s Nippon Steel, reported a data breach caused by hackers exploiting a zero-day vulnerability in their network equipment.
- The breach led to unauthorized access and potential leaks of personal data of customers, partners, and employees, but cloud services remain unaffected.
- Compromised information includes customer names, company details, employee names, and business-related contact information.
- The company has notified affected parties, cooperated with authorities, and implemented security measures to address the breach. There is no evidence of leaked data on social media or the dark web.
Read Full Article
5 Likes
Hackers-Arise
305

Image Credit: Hackers-Arise
Mobile Forensics, Part 1: The Fundamentals and Best Tools for Mobile Forensics
- Mobile forensics plays a vital role in investigations, focusing on smartphones and tablets.
- It involves seizing, acquiring, analyzing, and reporting digital evidence from mobile devices.
- Key steps include preservation, acquisition, analysis, and reporting of data for legal scrutiny.
- Tools like Cellebrite UFED, Oxygen Forensic Detective, and Magnet AXIOM are widely used.
- Developing technical skills and keeping up with evolving technologies are crucial in mobile forensics.
Read Full Article
18 Likes
Dev
232

Image Credit: Dev
The Telegram Username Scam: How People Are Losing Thousands in TON
- A new scam on Telegram tricks users into selling usernames for fake TON tokens.
- Scammers offer enticing deals to buy usernames, request payment for network fees, and vanish.
- Users lose significant amounts to scams exploiting trust and technical jargon on Telegram.
- Legitimate username sales occur only on Fragment; beware of direct message scams.
- Protect yourself by avoiding payment requests, enabling 2FA, and reporting suspicious activity.
Read Full Article
13 Likes
Bitcoinsensus
158

Image Credit: Bitcoinsensus
GMX Hit by $42M Exploit—Cross-Chain Hack Unfolds
- GMX has reportedly been exploited for over $42 million in crypto assets.
- The attacker is moving funds from Arbitrum to Ethereum to obscure the trail.
- No official statement yet from GMX; user impact and platform response remain unclear.
- The exploit on GMX involved transferring funds to Ethereum, with at least $9.6 million successfully bridged and exchanged into DAI and ETH. The incident raises concerns about security measures and potential compensations for affected users.
Read Full Article
9 Likes
For uninterrupted reading, download the app