Hacking News
Ars Technica
102

Image Credit: Ars Technica
Critical CitrixBleed 2 vulnerability has been under active exploit for weeks
- A critical vulnerability in Citrix's network management devices has been actively exploited for more than a month, despite the vendor's advisories stating otherwise.
- The vulnerability, tracked as CVE-2025-5777, is similar to a previous flaw known as CitrixBleed, which led to the compromise of 20,000 Citrix devices two years ago.
- Citrix disclosed the newer vulnerability and released a patch on June 17 but stated they were 'currently unaware of any evidence of exploitation', while researchers found evidence of active exploitation since at least June 23.
- Security firms have criticized Citrix for withholding indicators that could help customers determine if their networks are under attack, stating that merely patching vulnerable devices is not enough and that customers should look for signs of compromise.
Read Full Article
6 Likes
Securityaffairs
102
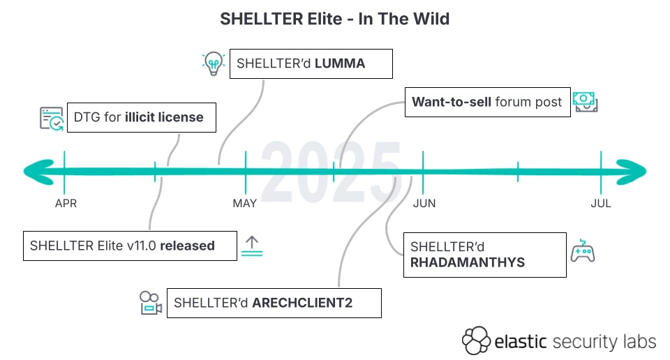
Image Credit: Securityaffairs
Hackers weaponize Shellter red teaming tool to spread infostealers
- Hackers exploit leaked Shellter Elite copy for infostealer attacks, bypassing security measures.
- Elastic Security Labs identifies malware campaigns using Shellter for evasion and malware deployment.
- Dynamic unpacker released by Elastic to detect and analyze SHELLTER-protected malware more effectively.
- Threat actors adopt Shellter for infostealer attacks, prompting efforts to counter abuse.
Read Full Article
6 Likes
Medium
196

Image Credit: Medium
My Experience as a Flow Scholar at Permissionless NYC
- The author recounts their experience as a Flow Scholar at Permissionless NYC, highlighting engaging with the Flow team, receiving feedback, and attending side events, with a special mention of a VIP dinner in Chelsea.
- The author emphasized the sense of community and team spirit that developed during the conference, particularly enjoying connecting with other like-minded founders and potential future business partners.
- Participating in a hackathon, the author collaborated with a top figure in the Top Shot ecosystem to create a casino-style baseball game with real rewards, showcasing their expertise in building on Flow and delivering great UX in web3.
- Despite initial doubts while working alongside younger participants, the author and their team ultimately succeeded at the hackathon, reinforcing their confidence in their skills and the decisions made in utilizing Flow's capabilities efficiently.
Read Full Article
11 Likes
Securityaffairs
147

Image Credit: Securityaffairs
Microsoft Patch Tuesday security updates for July 2025 fixed a zero-day
- Microsoft released Patch Tuesday security updates for July 2025 addressing 130 vulnerabilities across various Microsoft products.
- 10 of the vulnerabilities are rated Critical, with the remaining considered Important in severity.
- One of the flaws fixed is a publicly disclosed zero-day vulnerability, CVE-2025-49719, in Microsoft SQL Server.
- The updates also addressed critical issues like a wormable RCE flaw in Windows SPNEGO NEGOEX and an RCE vulnerability in Microsoft Office exploitable via the Preview Pane.
Read Full Article
8 Likes
Medium
0

Image Credit: Medium
The Call of Duty Hack: Why paying for games is not enough lol
- Hackers exploited a vulnerability in 'Call of Duty: WWII' from the Xbox Game Pass for PC, remotely controlling players' computers, and even displaying inappropriate content.
- The hackers used a Remote Code Execution (RCE) exploit to take control of users' PCs while they were playing online games, leading to Microsoft removing the game from PC Game Pass for safety reasons.
- The incident highlights the potential risks of gaming online and the importance of data security in protecting against cyber threats like ransomware attacks.
- The situation could have been worse with potential ransomware attacks, emphasizing the need for vigilance and preparedness against Advanced Persistent Threats in the future.
Read Full Article
Like
Securityaffairs
130

Image Credit: Securityaffairs
Italian police arrested a Chinese national suspected of cyberespionage on a U.S. warrant
- Italian police arrested a Chinese national, Zewei Xu (33), linked to Silk Typhoon APT group at Milan’s Malpensa Airport on a U.S. warrant.
- Xu is accused of cyberespionage, including attacks on U.S. government entities and 2020 attacks on U.S. COVID-19 vaccine research.
- Xu's family claims he is innocent and works as an IT manager in Shanghai. His wife opposes extradition, citing his Italian visa as evidence of no wrongdoing.
- Xu faces extradition proceedings in Italy for charges including wire fraud, ID theft, and unauthorized computer access, with a potential 20-year prison sentence.
Read Full Article
6 Likes
Securityaffairs
152

Image Credit: Securityaffairs
U.S. CISA adds MRLG, PHPMailer, Rails Ruby on Rails, and Synacor Zimbra Collaboration Suite flaws to its Known Exploited Vulnerabilities catalog
- U.S. Cybersecurity and Infrastructure Security Agency (CISA) adds MRLG, PHPMailer, Rails Ruby on Rails, and Synacor Zimbra Collaboration Suite flaws to its Known Exploited Vulnerabilities catalog.
- CISA included vulnerabilities such as MRLG buffer overflow, PHPMailer command injection, Rails Ruby on Rails path traversal, and ZCS SSRF in the catalog.
- The vulnerabilities pose risks of memory corruption, arbitrary code execution, file content disclosure, and SSRF, affecting various software versions.
- Federal agencies are required to address these vulnerabilities by July 28, 2025, in alignment with a security directive to mitigate the risks of known exploited vulnerabilities.
Read Full Article
9 Likes
Hackers-Arise
82

Image Credit: Hackers-Arise
Malware Evasion – Evading Russian Antiviruses
- Overwatch discusses obfuscation methods for avoiding detection by Russian antivirus software like Kaspersky, DrWeb, and others.
- The technique involves using obfuscated Meterpreter stagers to maintain control of the system while evading detection.
- Steps include generating a stager, randomizing API hashes, crafting a loader, and compiling an executable to evade known indicators of compromise.
- The method is effective in evading common Russian antivirus solutions, but Microsoft Defender may still flag it requiring adding .exe files to exclusions for persistence.
Read Full Article
4 Likes
Siliconangle
144

Image Credit: Siliconangle
Morphisec warns of Iran-backed ransomware campaign driven by political motives
- Morphisec Inc. warns of the resurgence of Pay2Key ransomware operation linked to Iran's Fox Kitten APT group, now rebranded as Pay2Key.I2P, utilizing RaaS model and Mimic ransomware techniques.
- Pay2Key.I2P has amassed $4 million from over 50 attacks within four months, with affiliates incentivized through an 80% profit share, particularly targeting adversaries of Iran for financial and ideological reasons.
- The ransomware group employs advanced evasion techniques, including a multi-stage attack chain, with recent expansions to target Linux systems and incorporate obfuscation methods to evade detection.
- While profit remains a motive, Morphisec emphasizes Pay2Key.I2P's ideological agenda, positioning the campaign as a tool of cyber warfare against Western targets aligned with Iran's geopolitical stance.
Read Full Article
8 Likes
Siliconangle
304

Image Credit: Siliconangle
Sonatype report finds 188% spike in open-source malware in the second quarter
- Sonatype Inc. reported a 188% increase in open-source malware in the second quarter of 2025, with 16,279 newly discovered malicious packages across popular ecosystems.
- Data exfiltration was the primary threat, with 55% of malicious packages designed to steal sensitive data. Malware targeting data corruption more than doubled during the quarter, now representing over 3% of all malicious packages.
- Cryptomining malware decreased to 5% of packages, indicating a shift towards more impactful outcomes like credential theft and espionage. The Lazarus Group, a North Korea-linked APT, was associated with 107 malicious packages.
- Sonatype's Open Source Malware Index noted a rise in advanced nation-state actors using open-source software for cyber espionage and financial crimes. The report is based on the company's proprietary detection systems monitoring npm, PyPI, and Maven Central.
Read Full Article
18 Likes
Siliconangle
305

Image Credit: Siliconangle
Splunk uncovers surge in social engineering through fake CAPTCHA attacks
- Splunk Inc. warns of a surge in social engineering campaigns using fake CAPTCHA systems to deliver malware without relying on software vulnerabilities.
- These attacks, dubbed 'ClickFix' and 'FakeCAPTCHA,' trick users into self-infecting their systems by exploiting familiarity with verification systems and using clipboard manipulation techniques.
- The attacks lure victims to malicious websites resembling Google's reCAPTCHA or Cloudflare CAPTCHA pages, prompting users to trigger hidden JavaScript that downloads and executes second-stage payloads.
- To combat this threat, Splunk researchers have introduced open-source tools like ClickGrab and PasteEater, along with detection queries to help organizations monitor for FakeCAPTCHA activity.
Read Full Article
14 Likes
Medium
49

Image Credit: Medium
Is your phone acting weird? Here’s what might be going on.
- Experiencing significant battery drain on your phone could be a sign of malware, especially if an unfamiliar app is consuming a large portion of the battery.
- If your phone becomes excessively warm even when not in use, it may indicate malware forcing the processor to work excessively.
- Sudden spikes in data usage without explanation could be a result of malware uploading data without your knowledge, so monitoring data usage is important.
- Unexpected behavior like apps launching on their own, random restarts, or strange messages may indicate malware presence on your phone.
Read Full Article
2 Likes
Securelist
317

Image Credit: Securelist
Approach to mainframe penetration testing on z/OS. Deep dive into RACF
- Dissecting mainframe penetration testing techniques on z/OS, particularly focused on RACF security package.
- Deep dive into RACF database structure, internal architecture, and its decision-making logic.
- Developed utility racfudit, facilitates offline analysis of RACF database, provides insights for security analysis.
- Exploring RACF profile relationships, user authorization flows within z/OS, and password hashing algorithms.
- Detailed overview of DES and KDFAES encryption algorithms for RACF password and phrase hashes.
Read Full Article
19 Likes
Securityaffairs
317

Image Credit: Securityaffairs
IT Worker arrested for selling access in $100M PIX cyber heist
- Brazilian police arrested IT worker João Roque for allegedly aiding a cyberattack that stole over $100 million through the PIX banking system.
- Roque is accused of selling system access and developing a tool for fund diversion, claiming he only communicated with criminals via phone and changed devices frequently to avoid detection.
- The cyberattack targeted multiple financial institutions, leading to at least six being impacted, resulting in the market being shaken.
- Authorities have frozen $270 million, suspended part of C&M's operations to prevent further attacks, and confirmed the company's systems were not the source of the breach.
Read Full Article
18 Likes
Hackingblogs
140
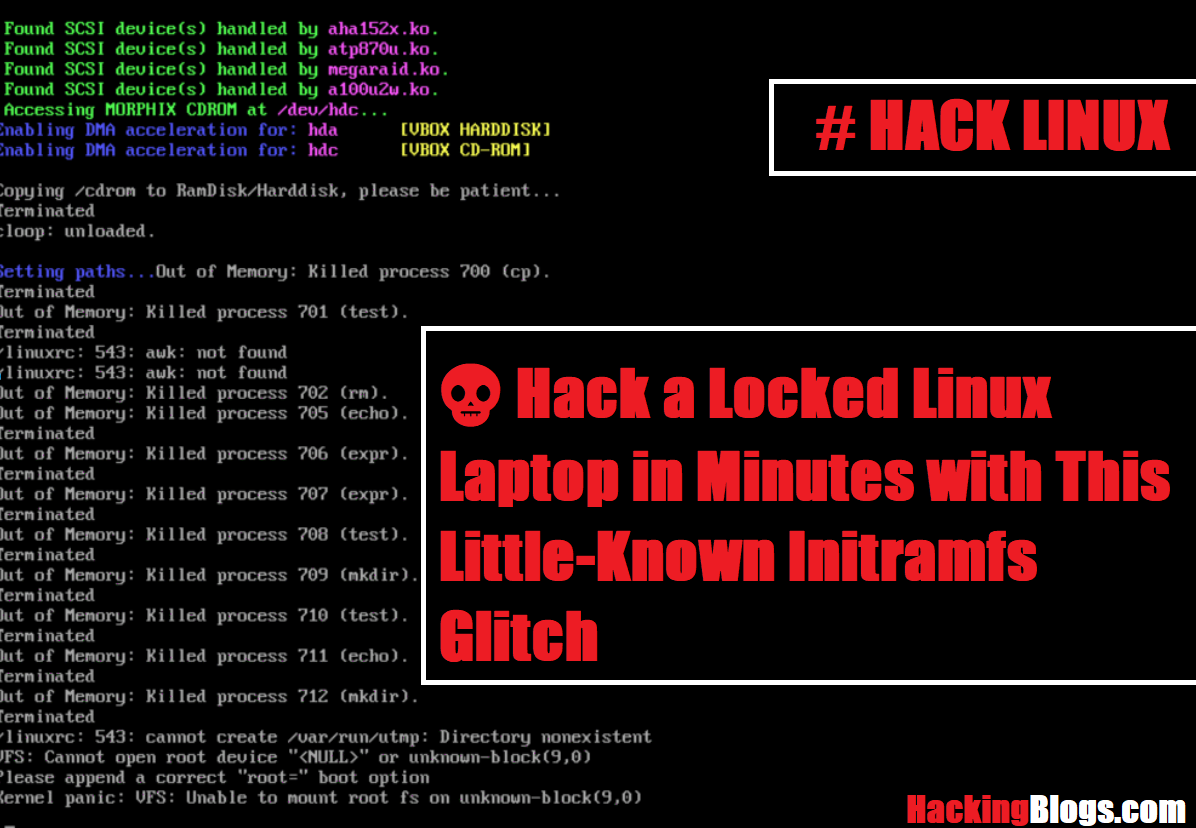
Image Credit: Hackingblogs
Hack a Locked Linux Laptop in Minutes with This Little-Known Initramfs Glitch
- Hacker exploits initramfs glitch to compromise encrypted Linux laptops in minutes.
- Attackers gain root shell access through debug shell, inject malware for persistent control.
- CVE‑2016‑4484 example highlights vulnerability across various Linux distributions to evade encryption.
- Protect systems by disabling debug shell, utilizing Secure Boot, and securing /boot partition.
- Prevent offline boot attacks by securing BIOS/UEFI with a password and disabling rescue boot options.
Read Full Article
8 Likes
For uninterrupted reading, download the app