Hacking News
Securityaffairs
54
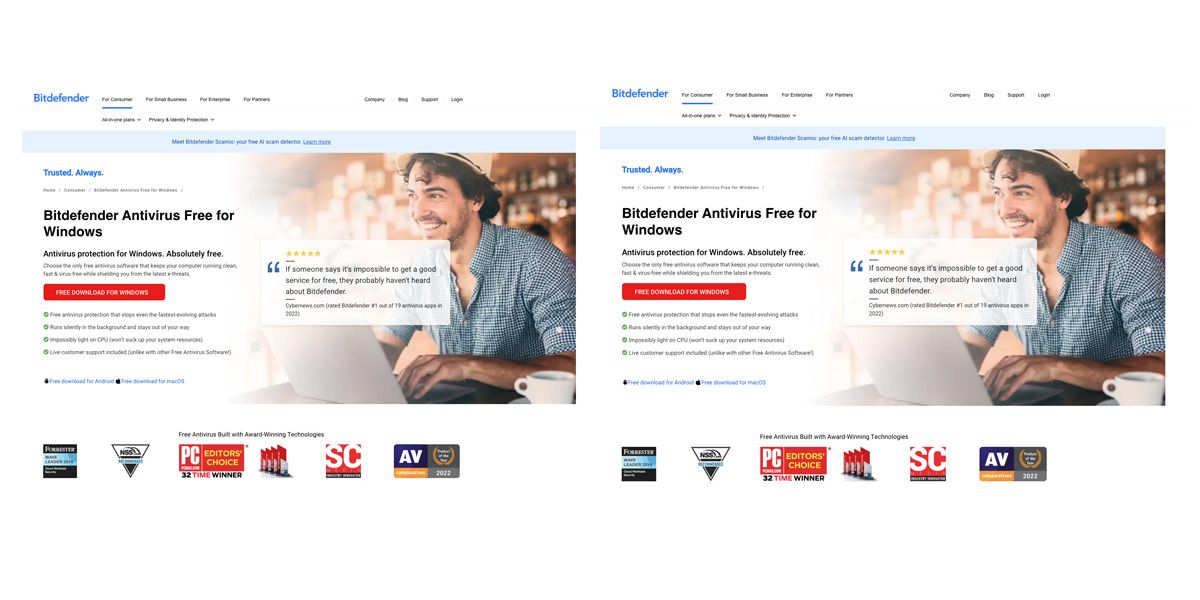
Image Credit: Securityaffairs
Crooks use a fake antivirus site to spread Venom RAT and a mix of malware
- A fake Bitdefender website has been discovered spreading the Venom RAT by deceiving users into downloading it as antivirus software.
- Researchers found a malicious campaign using the fake website to distribute Venom RAT, a Remote Access Trojan (RAT) designed for password theft and stealthy access.
- Upon clicking the fake download button, users are redirected to an Amazon S3 link to download a ZIP file containing the VenomRAT malware.
- VenomRAT, a fork of the Quasar RAT, supports remote control, credential theft, keylogging, and data exfiltration, with attackers aiming for financial gain and persistent system control.
Read Full Article
3 Likes
Coinpedia
45

Image Credit: Coinpedia
Sui Community Approves $162M Recovery Transaction for Cetus Hack Victims
- Sui validators approve a recovery plan to reclaim $162M frozen in Cetus hack, aiming to return funds to affected users.
- The recovery plan leads to a 7% increase in SUI price, sparking discussions on centralization versus quick response in decentralized networks.
- On May 22, Cetus, a popular decentralized exchange on the Sui blockchain, was hacked, resulting in a $223 million loss.
- A community proposal to return stolen assets from Cetus protocol gets over 52% approval, with funds set to be transferred to a secure multisig wallet for safe return.
Read Full Article
2 Likes
Securityaffairs
122

Image Credit: Securityaffairs
Iranian Man pleaded guilty to role in Robbinhood Ransomware attacks
- Iranian national Sina Gholinejad pleaded guilty to his role in a Robbinhood ransomware scheme that caused over $19 million in damages to Baltimore.
- The ransomware attack disrupted key services like billing and citations in cities like Baltimore and Greenville.
- Gholinejad and his co-conspirators utilized sophisticated methods like using VPNs and crypto mixers to demand Bitcoin ransoms and launder payments.
- Gholinejad faces up to 30 years in prison for computer and wire fraud conspiracy, with sentencing scheduled for August.
Read Full Article
7 Likes
Securityaffairs
4

Image Credit: Securityaffairs
DragonForce operator chained SimpleHelp flaws to target an MSP and its customers
- Sophos reports that a DragonForce ransomware operator exploited three vulnerabilities in SimpleHelp software to target a managed service provider.
- The vulnerabilities in SimpleHelp software (CVE-2024-57727, CVE-2024-57728, and CVE-2024-57726) allowed attackers to gain initial access and carry out various malicious activities.
- These vulnerabilities enabled unauthorized downloading and uploading of files, remote code execution, and privilege escalation, posing a serious security risk to customer machines.
- Arctic Wolf observed a campaign targeting SimpleHelp servers utilizing the disclosed vulnerabilities. Sophos identified an attacker using a legitimate SimpleHelp tool from an MSP to access client networks and extract sensitive information.
Read Full Article
Like
TronWeekly
399

Image Credit: TronWeekly
$223M Vanishes in Cetus Hack: Sui Uncovers Root Cause and Reacts
- A technical bug in the Cetus Protocol was identified as the root cause of the $223 million security breach with the Sui team pledging $10 million to enhance security measures.
- The Cetus hack was attributed to a bug in the protocol's math logic, not a vulnerability in Sui or the Move programming language, leading to unauthorized withdrawals of $223 million in crypto assets.
- Sui allocated $10 million for independent audits, formal verification tools, and an enlarged bug bounty program to prevent future security breaches and bolster the ecosystem's security.
- The incident was viewed as a turning point for the Sui ecosystem, prompting a focus on code reviews, formal verification, and developer education to strengthen the network resilience and community collaboration.
Read Full Article
24 Likes
Securityaffairs
49

Image Credit: Securityaffairs
Russia-linked APT Laundry Bear linked to 2024 Dutch Police attack
- A new Russia-linked APT group known as Laundry Bear has been linked to a security breach at Dutch police in September 2024.
- The breach exposed officers' work-related contact details, prompting the Dutch police to implement security measures and report the incident to the Data Protection Authority.
- The Dutch intelligence services blamed a 'state actor' for the breach and issued a joint advisory warning organizations about Laundry Bear attacks, highlighting the group's evasion tactics.
- Laundry Bear has targeted Western governments, defense contractors, cultural groups, and digital service providers since 2024, focusing on entities connected to Russia's war in Ukraine.
Read Full Article
3 Likes
TheNewsCrypto
208

Hackers Expose Solana Executive’s Personal Data Through Migos Breach
- Hackers compromised Migos' Instagram account with 13 million followers to leak Solana co-founder Raj Gokal's personal data.
- Personal data, including phone numbers, was shared by hackers to encourage followers to harass the victims.
- The incident was part of a week-long social engineering campaign targeting Gokal's digital accounts across various platforms.
- Attackers attempted to extort $2.7 million in Bitcoins from Gokal but failed; Instagram security removed compromised posts within 90 minutes.
Read Full Article
12 Likes
Securityaffairs
381
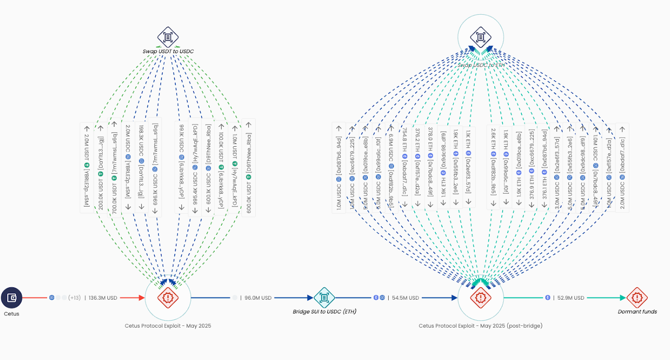
Image Credit: Securityaffairs
Crooks stole over $200 million from crypto exchange Cetus Protocol
- Cetus Protocol suffered a $223 million crypto theft and is willing to drop legal action if the stolen funds are returned.
- The platform was paused as the investigation confirmed the cyber heist last week.
- $162 million of the compromised funds have been successfully paused, and recovery efforts are underway with the Sui Foundation.
- The hack was due to a vulnerable package but has since been fixed, with the company offering a $5 million bounty for tips to identify the attacker.
Read Full Article
22 Likes
Securityaffairs
231
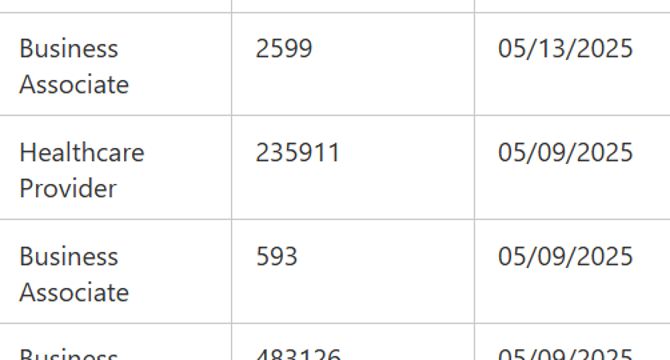
Image Credit: Securityaffairs
Marlboro-Chesterfield Pathology data breach impacted 235,911 individuals
- SafePay ransomware attacked Marlboro-Chesterfield Pathology, compromising personal data of 235,000 individuals.
- The breach occurred on January 16, 2025, leading to the unauthorized access of internal systems.
- Stolen information included names, addresses, birth dates, medical treatment details, and health insurance data.
- Marlboro-Chesterfield Pathology notified the US Department of Health and Human Services about the breach affecting 235,911 people.
Read Full Article
13 Likes
Securityaffairs
301
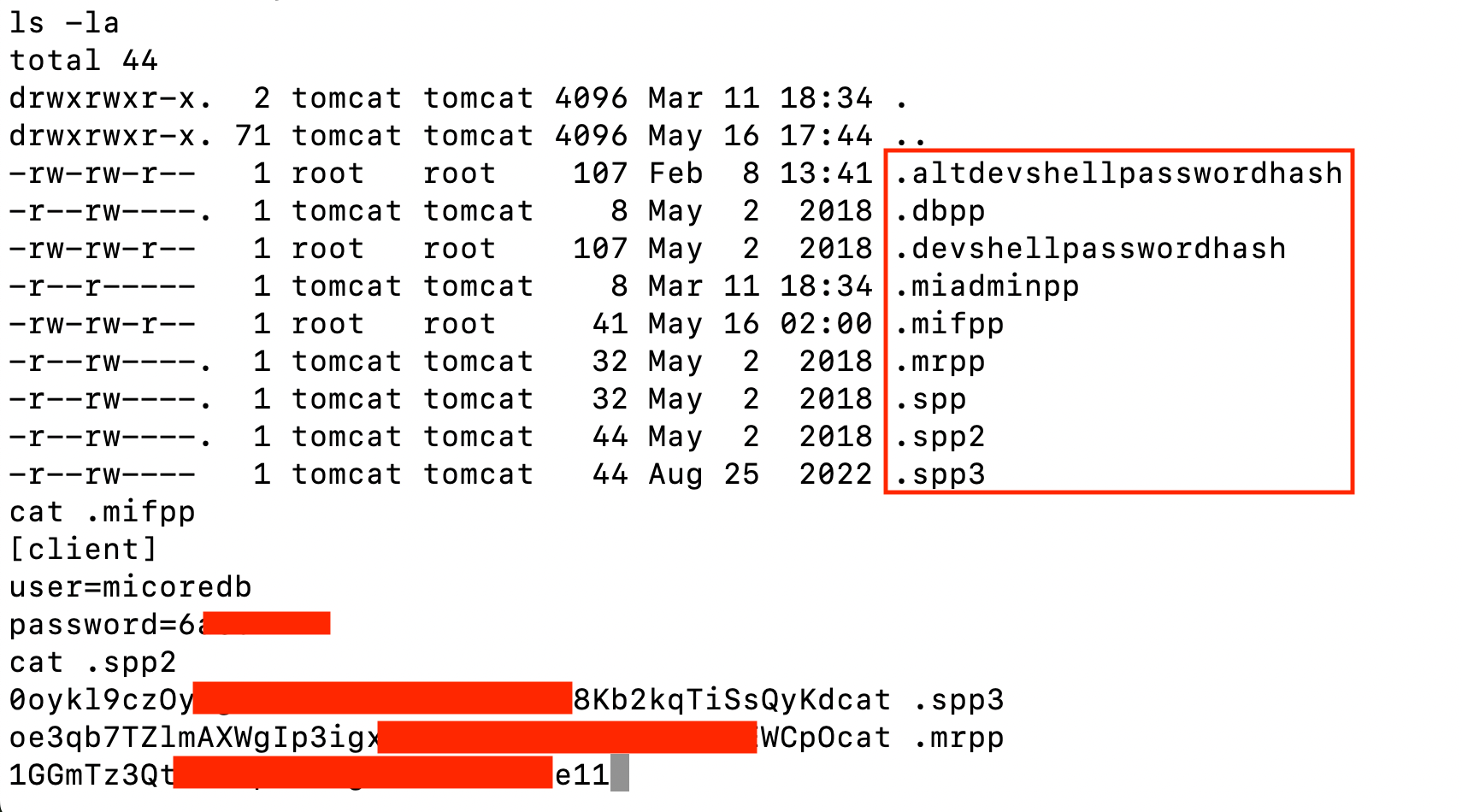
Image Credit: Securityaffairs
China-linked APT UNC5221 started exploiting Ivanti EPMM flaws shortly after their disclosure
- China-linked APT group exploits two Ivanti EPMM flaws, CVE-2025-4427 and CVE-2025-4428, to target organizations in Europe, North America, and Asia-Pacific.
- The flaws include an authentication bypass and a remote code execution vulnerability, allowing attackers to access protected resources and execute arbitrary code.
- Ivanti has released updates addressing the vulnerabilities after threat actors actively exploited them to achieve remote code execution without authentication.
- The attacks are linked to China-linked group UNC5221, which targeted critical sectors and used techniques like Java Reflection and KrustyLoader malware for espionage campaigns.
Read Full Article
18 Likes
Silicon
59

Image Credit: Silicon
UK, US Police Target Ransomware Gangs In Latest Action
- Law enforcement authorities in the UK, the US, and five other countries collaborated in a Europol-coordinated action targeting ransomware gangs.
- The action resulted in the takedown of 300 servers, seizure of 650 internet domains, and 3.5 million euros in cryptocurrency.
- Notorious malware strains like Trickbot and Danabot were neutralized, along with other malware such as Bumblebee, Lactrodectus, Qakbot, Hijackloader, and Warmcookie.
- Authorities issued international arrest warrants against 20 key actors providing or operating initial access services to ransomware gangs, with many suspects being Russian citizens or Russian-language speakers.
Read Full Article
3 Likes
Securityaffairs
231
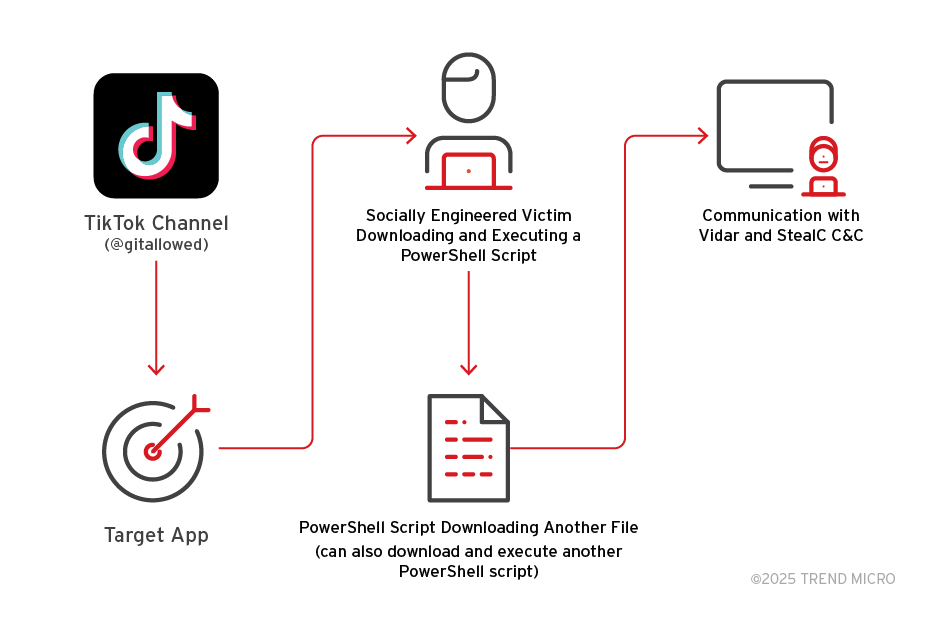
Image Credit: Securityaffairs
Fake software activation videos on TikTok spread Vidar, StealC
- Cybercriminals are using AI-generated TikTok videos to spread Vidar and StealC malware in ClickFix attacks.
- The videos trick users into executing PowerShell commands disguised as software activation steps, reaching over 500,000 views.
- Malware-laden TikTok videos provide step-by-step instructions to download Vidar or StealC malware, connecting to command-and-control servers after infection.
- Traditional security controls focusing on malicious code detection are less effective against social media-based malware distribution, highlighting the need for a more holistic defense approach.
Read Full Article
13 Likes
Silicon
413
Image Credit: Silicon
Police Probe Hacking Gang Over Retail Attacks
- British authorities are investigating hacking group Scattered Spider for recent hacks on UK retailers, including Marks & Spencer's systems breached via a third-party contractor, likely India-based TCS.
- Scattered Spider, a group of mainly English-speaking individuals in the UK and US, is known for using social engineering techniques like tricking IT help desks into clicking on links or resetting accounts.
- Investigations by the National Crime Agency suggest Scattered Spider may be involved, with past hacks on casinos and Transport for London connected to the group. TCS is internally probing its involvement in the M&S hack.
- Several arrests related to Scattered Spider have been made, including UK citizen Tyler Buchanan and others in the US and the UK. The group has worked with various hacking groups and faces charges of theft and disruption.
Read Full Article
24 Likes
Metro
213

Image Credit: Metro
Here’s how you can protect yourself from being scammed with deepfakes
- To protect against deepfake scams, individuals are advised to create secret codes with friends and family as a precaution against cybercriminals.
- Former US government adviser Cody Barrow suggests using personal passwords as a way to verify authenticity and combat online threats, especially for vulnerable users.
- Recent major data breaches at companies like M&S have raised concerns about cybersecurity, with increased risks of personal details being compromised.
- Barrow highlights the importance of implementing additional security measures like two-factor authentication to prevent cybercriminals from creating realistic scams.
Read Full Article
12 Likes
Securityaffairs
50

Image Credit: Securityaffairs
Security Affairs newsletter Round 525 by Pierluigi Paganini – INTERNATIONAL EDITION
- Silent Ransom Group targeting law firms, FBI warns.
- Leader of Qakbot cybercrime network indicted in U.S. crackdown.
- Operation RapTor results in arrest of 270 dark web vendors and buyers.
- Chinese threat actors exploit Trimble Cityworks flaw to breach U.S. local government networks.
Read Full Article
3 Likes
For uninterrupted reading, download the app