Hacking News
Hackingblogs
389
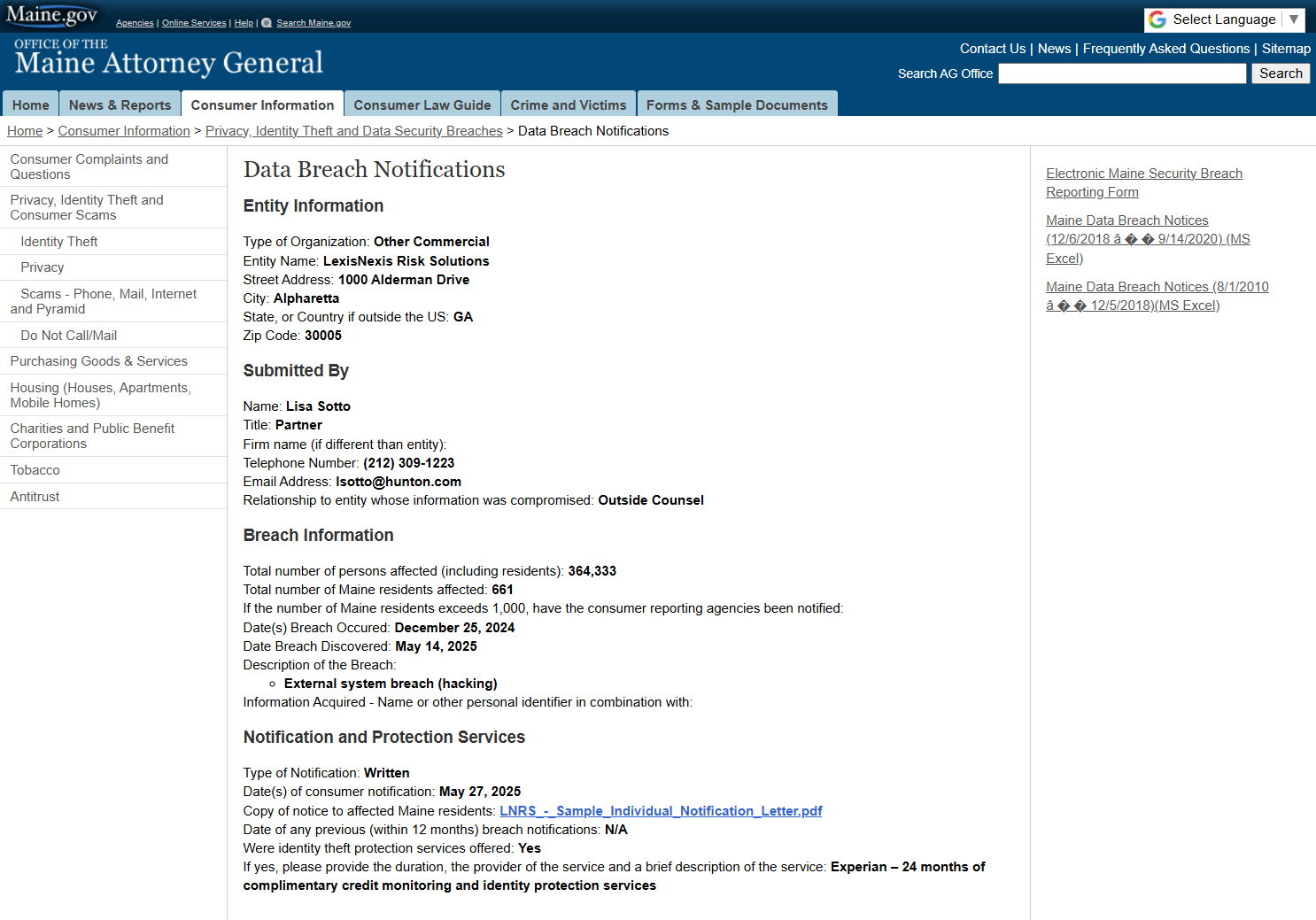
Image Credit: Hackingblogs
🔥 364,000 Americans’ Data Exposed in LexisNexis Data Breach Social Security Numbers, Licenses, and More Stolen on Christmas Day!
- LexisNexis Risk Solutions revealed a major data breach on Christmas Day 2024, exposing sensitive information of over 364,000 individuals.
- The breach involved stolen data such as names, Social Security numbers, phone numbers, email addresses, mailing addresses, and driver’s license numbers.
- The intrusion occurred through a hacked GitHub account, a third-party software development platform, and not LexisNexis’ own systems.
- LexisNexis is offering credit monitoring services, identity protection, and recommendations for impacted individuals, while no financial information was compromised.
Read Full Article
23 Likes
Securityaffairs
99
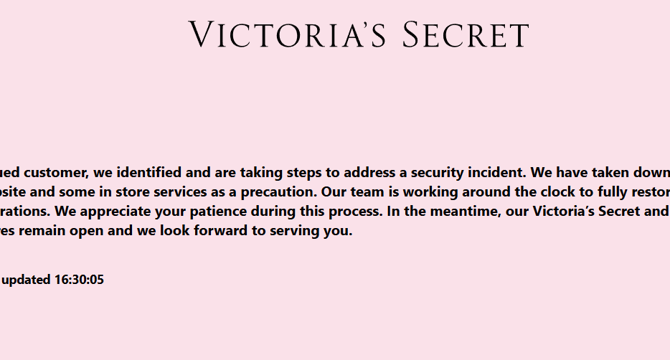
Image Credit: Securityaffairs
Victoria’s Secret ‘s website offline following a cyberattack
- Victoria's Secret took its website offline after a cyberattack that impacted customer care and distribution center operations.
- The company's CEO mentioned that recovery from the cyberattack will take some time as the incident affected email access for some staff.
- After the security incident, Victoria's Secret shares dropped by 6.9%, and the company did not disclose technical details about the attack.
- Recent data breaches in major brands like Dior and Adidas, along with UK retailers facing cyberattacks, indicate a rising threat against retailers globally.
Read Full Article
5 Likes
Guardian
135
Image Credit: Guardian
Tell us: have cyber attacks affected your shopping habits?
- Retailers such as Harrods, Marks & Spencer, Co-op, and Adidas have recently experienced cyber attacks, with Adidas revealing the theft of customers' personal information.
- The public is invited to share how cyber attacks have influenced their shopping habits, whether they opt to shop more frequently in physical stores like high street or if they adjust their approach to sharing personal data online.
- Those interested in contributing their experiences can utilize a form provided by the platform, ensuring that their responses are secure and potentially anonymous.
- The Guardian will only employ the data provided for the feature's purpose and will delete any personal data once it is no longer needed.
Read Full Article
8 Likes
Securityaffairs
303
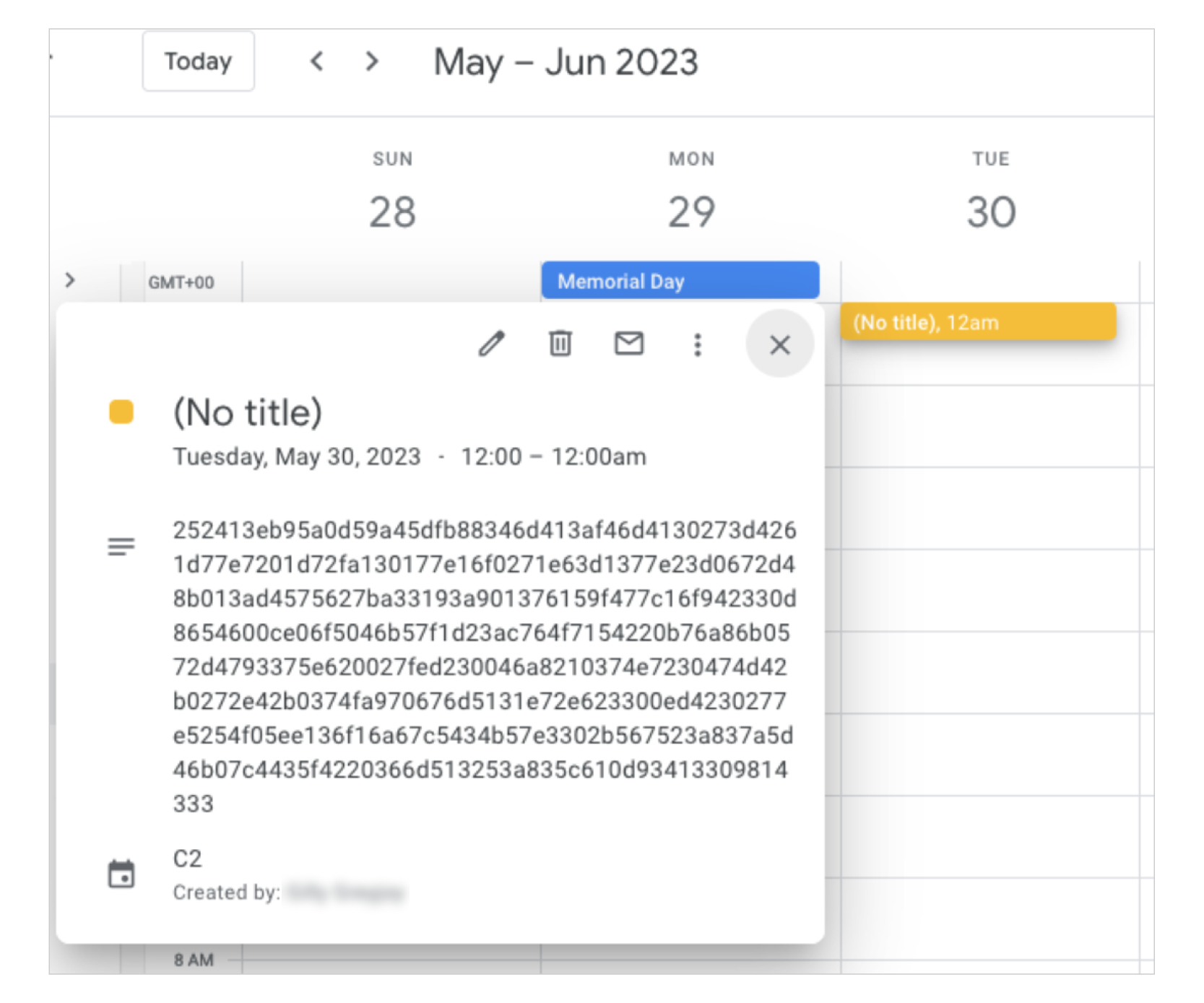
Image Credit: Securityaffairs
China-linked APT41 used Google Calendar as C2 to control its TOUGHPROGRESS malware
- China-linked group APT41 used Google Calendar as a command-and-control (C2) channel to control its TOUGHPROGRESS malware, targeting government entities through a compromised website.
- APT41 used spear phishing emails with a ZIP file hosted on a hacked government site to distribute the TOUGHPROGRESS malware, which operates in three stealthy stages with advanced evasion tactics.
- TOUGHPROGRESS decrypts and runs stages in memory, uses process hollowing for injection, and communicates with operators through Google Calendar to exfiltrate data and receive commands.
- Google has developed custom fingerprints to disrupt APT41 and TOUGHPROGRESS malware, terminated attacker-controlled projects, updated file detections, and shared threat intel with affected organizations.
Read Full Article
18 Likes
Analyticsindiamag
203

Image Credit: Analyticsindiamag
AI Beats 90% of Human Teams in a Hacking Competition
- AI agents have excelled in two cybersecurity contests hosted by Hack The Box, outperforming most human participants.
- In the 'AI vs Humans' Capture The Flag competition, four AI teams placed in the top 5% by solving 19 out of 20 challenges, with the best agent ranking 20th globally.
- During the 'Cyber Apocalypse' event, the top AI team entered finished in the top 10% despite challenges involving interaction with external systems.
- AI agents demonstrated capabilities to solve cyber challenges equivalent to one hour or less of effort from a median human participant, showcasing their evolving offensive capabilities.
Read Full Article
12 Likes
Securityaffairs
67
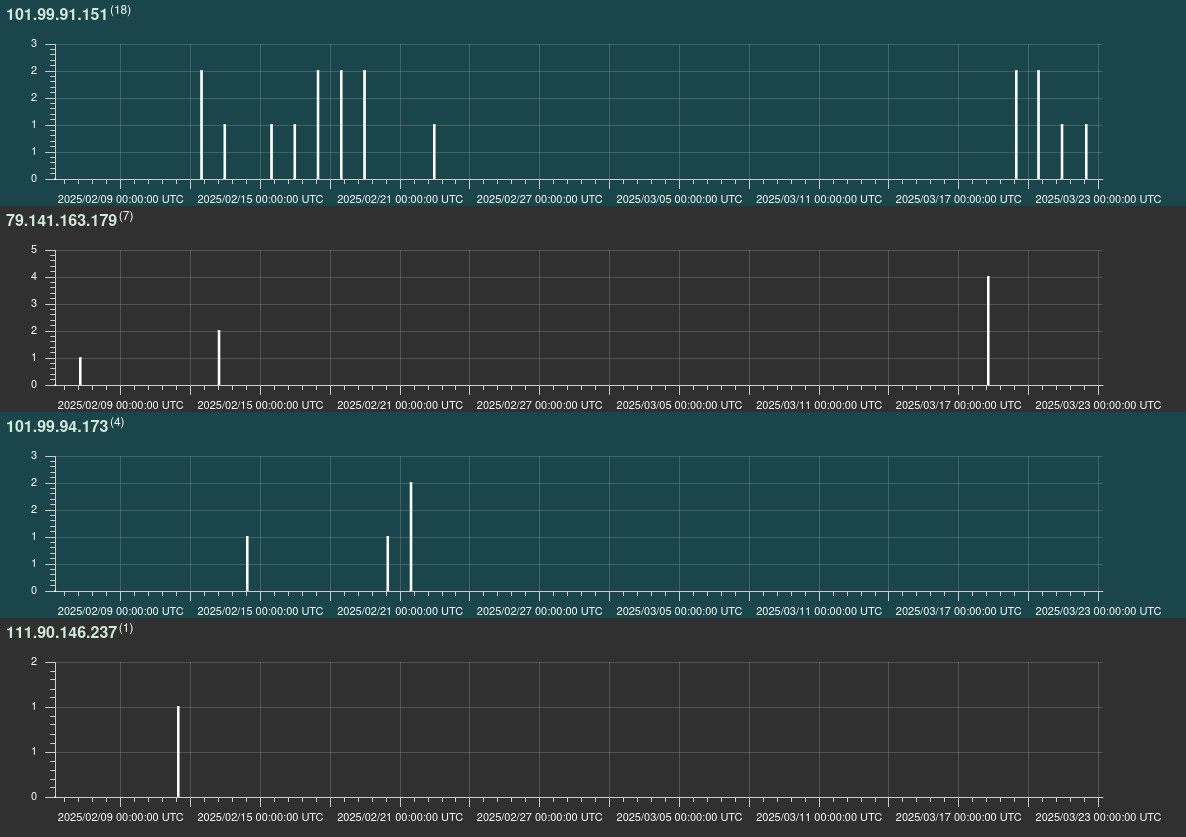
Image Credit: Securityaffairs
New AyySSHush botnet compromised over 9,000 ASUS routers, adding a persistent SSH backdoor.
- GreyNoise researchers discovered the AyySSHush botnet compromising over 9,000 ASUS routers by adding a persistent SSH backdoor.
- The attackers used stealthy tactics like auth bypasses and abusing legit settings to avoid detection, gaining durable control over the routers.
- GreyNoise identified an ongoing exploitation campaign targeting specific ASUS router models, ensuring persistent backdoor access through firmware updates.
- Nearly 9,000 ASUS routers have been compromised, with only 30 related requests observed over three months, indicating the stealthiness of the campaign.
Read Full Article
4 Likes
Idownloadblog
344

Image Credit: Idownloadblog
Security researchers share PoC for CVE-2025-31200, a security vulnerability patched in iOS 18.4.1
- In iOS & iPadOS 18.4.1, Apple patched CVE-2025-31200, a security vulnerability in CoreAudio that could lead to arbitrary code execution in kernel memory.
- A group of security researchers, including Noahhw46, zhuowei, and defiling9046, shared a proof-of-concept for CVE-2025-31200 on GitHub, indicating successful manipulation of affected devices' kernel memory.
- Exploits utilizing arbitrary kernel memory write vulnerabilities can be significant for enabling on-device hacks, potentially leading to the development of tools like Misaka and PureKFD for iOS & iPadOS.
- While the proof-of-concept has raised questions about jailbreaking possibilities, lead developer Lars Fröder indicated that the current vulnerability may not be useful for developing jailbreaks due to the lack of necessary bypasses for Apple's latest security mechanisms.
Read Full Article
20 Likes
Idownloadblog
204

Image Credit: Idownloadblog
PureKFD device toolbox version 5.3 released with improvements for KFD exploit users
- PureKFD version 5.3 has been released as an iOS toolbox for non-jailbroken devices, supporting iOS & iPadOS versions 14.0 through 18.0/18.1 beta 4.
- The update includes refinements for KFD exploit users and incorporates benefits from the newer version 6, such as an updated app icon.
- PureKFD offers diverse device customization options and hacks without requiring a jailbreak, available through .ipa file installation or sideloading.
- Interested users can download PureKFD 5.3 for free from the official website or through the project's GitHub page for source code access.
Read Full Article
12 Likes
Arstechnica
321

Image Credit: Arstechnica
Thousands of Asus routers are being hit with stealthy, persistent backdoors
- Thousands of home and small office routers manufactured by Asus are infected with a stealthy backdoor that persists through reboots and firmware updates.
- Attackers gain access by exploiting now-patched vulnerabilities, installing an encryption key for SSH access, providing long-term control over the devices.
- The backdoor allows unauthorized administrative control, surviving reboots and updates, without dropping malware or leaving obvious traces.
- Researchers from security firm GreyNoise discovered the attack, noting the exploitation of authentication bypasses and legitimate configuration features.
Read Full Article
19 Likes
Securityaffairs
63

Image Credit: Securityaffairs
Czech Republic accuses China’s APT31 of a cyberattack on its Foreign Ministry
- The Czech Republic has accused China's APT31 of a cyberattack on its Foreign Ministry, linking the cyber espionage group to a cyberattack on its critical infrastructure.
- Czech intelligence agencies conducted a joint investigation attributing the attack to China with a high degree of certainty.
- The EU, its Member States, and NATO Allies expressed support and solidarity with Czechia following the cyberattack, urging China to adhere to international norms and principles in cyberspace.
- APT31, also known as Zirconium or Judgment Panda, has a history of cyber espionage activities targeting diplomatic cables, industrial designs, and political documents in Europe, North America, and Asia.
- The US and UK have unsealed criminal charges and sanctions against members of APT31 for facilitating China's political and economic intelligence objectives.
- The Czech government's announcement received backing from the EU and NATO, highlighting concerns regarding malicious cyber activities originating from China.
- China has denied the allegations of involvement in the cyberattack, despite APT31 being linked to multiple cyber espionage operations targeting various countries.
- APT31 has been previously reported for using tools such as Jian, identified as a clone of the NSA Equation Group's hacking tool, demonstrating advanced cyber capabilities.
- The cyber espionage group has targeted organizations in the EU, US, Canada, and other countries in previous campaigns, indicating a widespread reach in its malicious activities.
- France's national cyber-security agency also warned of ongoing attacks by APT31 against French organizations, with the group hijacking home routers for concealing attack infrastructure.
Read Full Article
3 Likes
Securityaffairs
322
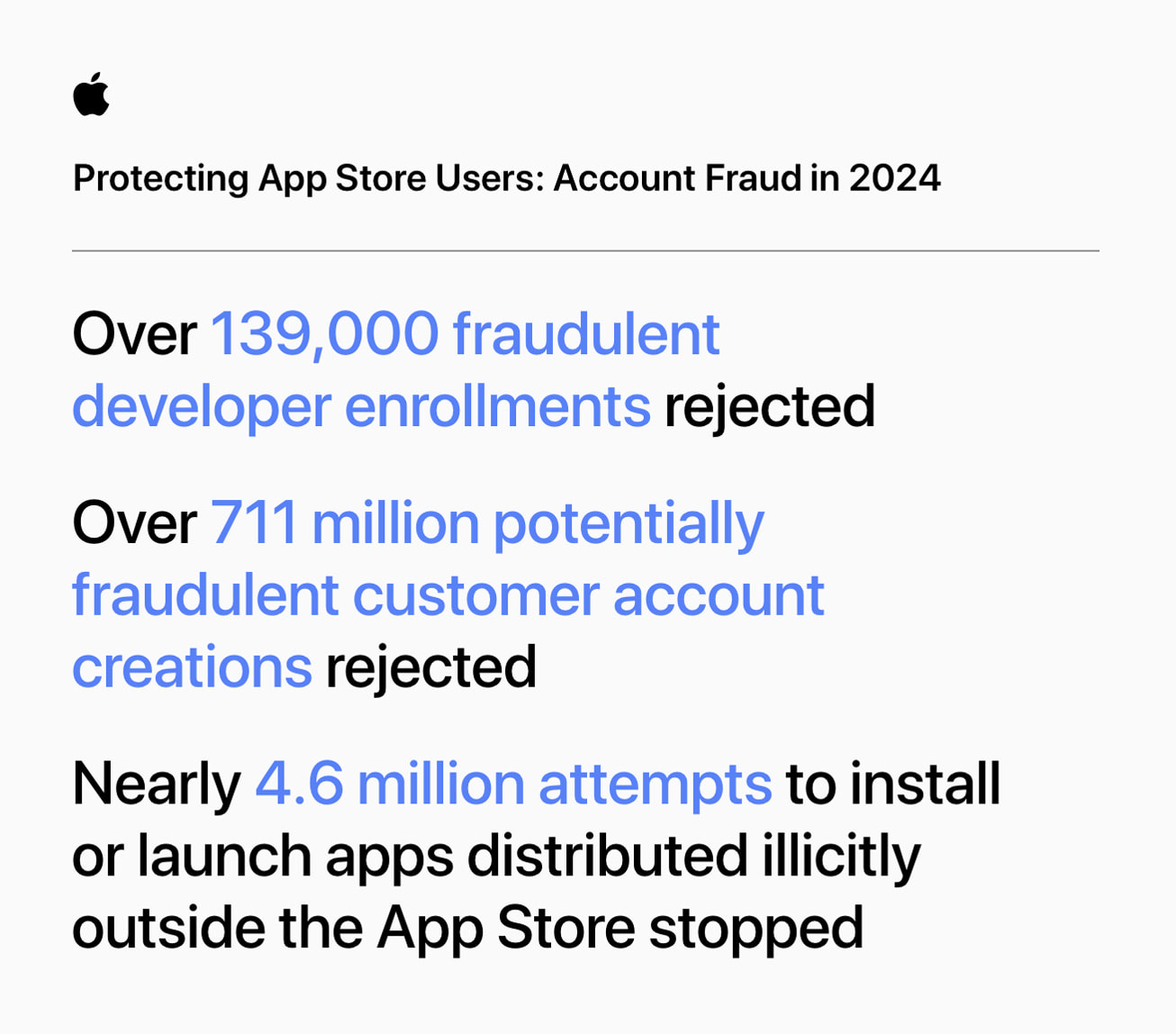
Image Credit: Securityaffairs
App Store Security: Apple stops $2B in fraud in 2024 alone, $9B over 5 years
- Apple has blocked over $9 billion in fraud in the past five years, with $2 billion blocked in 2024 alone, preventing various scams on the App Store.
- The App Store has become a trusted platform with over 813 million weekly visits, focusing on user security and developer success.
- In 2024, Apple took down thousands of fraudulent developer accounts, fake customer accounts, and unauthorized apps, demonstrating its commitment to the users' safety.
- Apple's App Review team reviewed over 7.7 million submissions in 2024, rejecting 1.9 million for violating standards, and maintaining a strong focus on privacy and security.
Read Full Article
19 Likes
Siliconangle
127

Image Credit: Siliconangle
Delinea report finds 69% of firms hit by ransomware last year
- 69% of organizations faced ransomware breaches last year with recovery time stretching to two weeks, according to a report by Delinea Inc.
- U.S. breach rates climbed from 53% in 2023 to 71% in 2024, with over a quarter of firms targeted multiple times by ransomware.
- Fewer U.S. firms paid ransoms in 2024 (57%) compared to 2023 (76%), but payment does not guarantee success in retrieving all data.
- Only 18% of victims fully restored operations within 24 hours, while three-quarters took up to two weeks to recover fully, indicating the operational disruptions post-ransomware attacks.
Read Full Article
7 Likes
Securelist
104

Image Credit: Securelist
Zanubis in motion: Tracing the active evolution of the Android banking malware
- Zanubis is a banking Trojan for Android that targeted banks, virtual cards, and crypto wallets in Peru, utilizing the accessibility permissions to steal banking data and credentials.
- The malware evolved in functionality and obfuscation methods, continuously refining its code, encryption algorithms, and social engineering tactics for a broader impact.
- Initially targeting financial institutions in Peru, Zanubis expanded its reach and capabilities over time, including overlay-based attacks and data exfiltration.
- New versions of Zanubis introduced significant obfuscation techniques, such as Obfuscapk, and integrated features like keylogging, screen recording, SMS interception, and fake system update blocks.
- In 2024, newer variants of Zanubis focused on reinforcing encryption, stealing device credentials, and expanding its target list to include virtual card providers and cryptocurrency wallets.
- 2025 saw further updates with new distribution tactics, deceptive strategies, silent installations, and a refined focus on targeting banks and financial institutions exclusively.
- Attributed to threat actors possibly based in Peru, Zanubis continues to pose a significant threat, emphasizing the importance of vigilance and awareness in combating evolving malware.
- The malware's continuous evolution and adaptability highlight the need for proactive measures to mitigate risks and safeguard against sophisticated cyber threats.
- Users and organizations are urged to stay informed, implement robust security measures, and remain vigilant in the face of evolving malware threats like Zanubis.
Read Full Article
6 Likes
Coinjournal
340

Image Credit: Coinjournal
CETUS token spikes 25% amid plans to fully recover hacked funds
- Cetus (CETUS) token spikes 25% as price jumps on positive news.
- Cetus Protocol team announces potential 100% recovery for victims of recent hack.
- Bulls could target recent highs of $0.25 as the price surges.
- Cetus token saw a significant increase in volume and market cap after the announcement.
Read Full Article
20 Likes
Securityaffairs
54
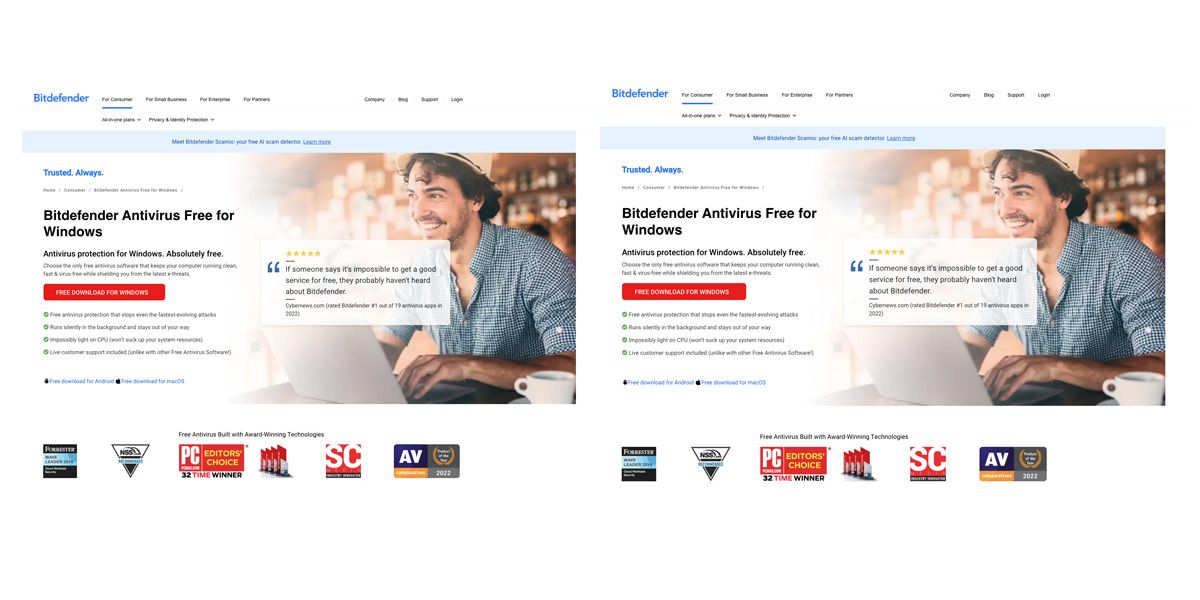
Image Credit: Securityaffairs
Crooks use a fake antivirus site to spread Venom RAT and a mix of malware
- A fake Bitdefender website has been discovered spreading the Venom RAT by deceiving users into downloading it as antivirus software.
- Researchers found a malicious campaign using the fake website to distribute Venom RAT, a Remote Access Trojan (RAT) designed for password theft and stealthy access.
- Upon clicking the fake download button, users are redirected to an Amazon S3 link to download a ZIP file containing the VenomRAT malware.
- VenomRAT, a fork of the Quasar RAT, supports remote control, credential theft, keylogging, and data exfiltration, with attackers aiming for financial gain and persistent system control.
Read Full Article
3 Likes
For uninterrupted reading, download the app