Hacking News
Hackersking
266

Image Credit: Hackersking
Transforming Design with qoruv.com Architect App: Building Smarter and Faster
- The qoruv.com Architect App is revolutionizing the architecture and design industry by offering innovative features for professionals to efficiently execute tasks and transform ideas into reality.
- This platform provides a user-friendly interface with design tools, collaborative work environments, and management features, making it unique and beneficial for engineers, architects, and design professionals.
- Key characteristics of the qoruv.com Architect App include cloud-based access, 3D modeling tools, revision control, synchronous collaboration, BIM integration, and AI-assisted design suggestions.
- The app enhances workflow efficiency by streamlining processes, offering intuitive interfaces for quick generation of tech drawings and 3D models, and catering to various architectural needs and project sizes.
- Qoruv.com's AI technology improves design sustainability, compliance, and aesthetics while ensuring adherence to industry best practices and regulations.
- With secure cloud storage, the app prioritizes data protection with encryption, automated backups, and controlled sharing, allowing authorized users worldwide to access collaborative features.
- Real-world applications include improved client presentations through vivid 3D visualizations, enhanced client understanding with VR walkthroughs, and streamlined internal design reviews for multinational companies and educational institutions.
- Although feature-rich, the qoruv.com Architect App offers a user-friendly learning curve with video guides, community support, and training resources for professionals with varying levels of experience.
- With its adaptability and focus on emerging technological demands in the construction industry, the qoruv.com app is poised to lead architectural tech innovation with its AI-driven instructions, real-time collaboration, and cloud efficiencies.
- In conclusion, qoruv.com Architect App is more than just software; it is an advanced architectural and design ecosystem that facilitates smarter, quicker, and more efficient solutions, giving professionals a competitive advantage in a demanding industry.
Read Full Article
16 Likes
Securityaffairs
408

Image Credit: Securityaffairs
Kosovo authorities extradited admin of the cybercrime marketplace BlackDB.cc
- Kosovo citizen Liridon Masurica (33) extradited to the US for running cybercrime marketplace BlackDB.cc and facing related charges.
- BlackDB.cc, an online criminal marketplace active since 2018, offered compromised credentials and PII for sale.
- Masurica charged in the US with six fraud-related counts, faces up to 55 years in prison for conspiracy and unauthorized access device usage.
- The US Department of Justice seized another cybercrime marketplace Rydox, arresting three Kosovo nationals, including administrators, for facilitating sales of stolen personal data and fraud tools.
Read Full Article
24 Likes
Idownloadblog
197

Image Credit: Idownloadblog
Security researcher shares PoC for CVE-2023-41992 local privilege escalation bug
- Apple patched a security vulnerability (CVE-2023-41992) in iOS & iPadOS 16.7 discovered by Bill Marczak, which allowed local privilege escalation.
- iOS security researcher @karzan_0x455 shared a proof of concept for the CVE-2023-41992 vulnerability showing how it can be exploited.
- The proof of concept demonstrates the local privilege escalation bug, providing insights for potential hackers to create exploits, jailbreaks, or TrollStore installation methods.
- While the bug may not lead to immediate jailbreaks due to additional security bypass requirements, it could be valuable for future projects like alternative installation methods up to iOS & iPadOS 17.0.
Read Full Article
11 Likes
Hackernoon
55

Image Credit: Hackernoon
Anonymous vs “ICE Air:” GlobaIX Needs A Security Fix
- Hacker group 'Anonymous' targeted GlobalX, also known as 'ICE Air,' and leaked sensitive deportation flight files.
- The attack on GlobalX involved breaching the developer's token and obtaining security keys for the company's AWS cloud storage.
- Sensitive data obtained by 'Anonymous' included detailed passenger lists for GlobalX's deportation flights, confirming the authenticity of leaked information.
- GlobalX activated incident response protocols and cybersecurity experts to investigate and contain the breach, expecting no material effect on the company's financial condition or operations.
Read Full Article
3 Likes
Securityaffairs
279

Image Credit: Securityaffairs
U.S. CISA adds Microsoft Windows flaws to its Known Exploited Vulnerabilities catalog
- U.S. Cybersecurity and Infrastructure Security Agency (CISA) added Microsoft Windows flaws to its Known Exploited Vulnerabilities catalog.
- CVE-2025-30397, CVE-2025-30400, CVE-2025-32701, CVE-2025-32706, and CVE-2025-32709 are the recently added vulnerabilities with their respective descriptions and severity scores.
- Microsoft addressed these flaws with the Patch Tuesday Security updates for May 2025 and confirmed their exploitation in the wild.
- CISA has issued a directive requiring federal agencies to address the vulnerabilities by June 3rd, 2025, and experts recommend private organizations to review and fix these vulnerabilities.
Read Full Article
16 Likes
Guardian
110
Image Credit: Guardian
‘Aggressive’ hackers of UK retailers are now targeting US stores, says Google
- Hackers responsible for disrupting UK retailers are now targeting similar companies in the United States, according to Google.
- The hackers, linked with the group 'Scattered Spider', are known for their aggression and ability to circumvent security programs.
- M&S, a prominent UK retailer, faced a disruptive hack by the Scattered Spider group, affecting its online operations.
- Recently, M&S announced that some customer data was accessed, including names, addresses, and order histories, but not payment or card details.
Read Full Article
6 Likes
Hackers-Arise
293

Image Credit: Hackers-Arise
Hacking Artificial Intelligence (AI) Large Language Models (LLMs)
- Large Language Models (LLMs) like ChatGPT, Claude, and Llama have opened up new attack surfaces despite offering tremendous capabilities.
- Techniques like the Context Ignoring Attack exploit the limitations in how LLMs process information to potentially bypass safeguards.
- Prompt Leaking involves trying to extract system prompts to understand model limitations and create targeted attacks.
- Role Play Attacks leverage the creative scenarios of LLMs to bypass safety measures by engaging the model in unethical roles.
- Prefix Injection manipulates model responses by adding specific text at the beginning of queries, influencing the output.
- Refusal Suppression attacks aim to stop LLMs from declining harmful queries by instructing them to avoid refusal statements.
- Sophisticated attackers combine techniques like refusal suppression and context ignoring for more successful attacks.
- Understanding vulnerabilities in LLMs is crucial as they become more integrated, leading to an escalating battle between exploiters and defenders.
Read Full Article
17 Likes
Massivelyop
22

Account data of 89M Steam users is reportedly up for sale on the dark web
- Account data of 89 million Steam users is reportedly up for sale on the dark web, putting 70% of the platform's userbase at risk.
- The data breach was highlighted by a Twitter user referencing a LinkedIn post from cyber threat intelligence firm Underdark.ai.
- A user going by the name Machine1337 claimed to have the database of Steam account details and is selling it for $5,000 on a dark web forum, with included real-time 2FA SMS logs routed via Twilio.
- While Steam representative mentioned they do not use Twilio, users are advised to change passwords, enable Steam Guard 2FA, and stay vigilant against phishing attempts as a precautionary measure.
Read Full Article
1 Like
TheNewsCrypto
404

Curve Finance Shifts to New Domain After DNS Hijack Incident
- Curve Finance has shifted its official web domain from Curve.fi to Curve.finance due to a DNS hijack incident that opened the way to a phishing attack.
- The platform confirmed that none of its password protections or 2FA systems were breached during the incident, ensuring the safety of funds and internal systems.
- The decision to change the domain was influenced by prolonged downtime and better support from .finance domain registrars, highlighting improved responsiveness and trust in managing the domains.
- The incident is still under investigation, and the team is actively working to find out how the breach occurred, with a promise to provide timely updates as more information becomes available.
Read Full Article
24 Likes
Securityaffairs
376

Image Credit: Securityaffairs
Microsoft Patch Tuesday security updates for May 2025 fixed 5 actively exploited zero-days
- Microsoft Patch Tuesday security updates for May 2025 addressed 75 security flaws, including five zero-day vulnerabilities.
- Of the vulnerabilities fixed, 12 are rated Critical and the rest are rated Important in severity.
- Microsoft confirmed that five zero-day vulnerabilities were actively exploited in the wild, including issues related to Scripting Engine Memory Corruption and Elevation of Privilege in various Windows components.
- Microsoft urged users to apply the security updates to protect their systems from potential cyber attacks.
Read Full Article
22 Likes
Guardian
114
Image Credit: Guardian
Co-op cyber-attack: stock availability in stores ‘will not improve until weekend’
- Co-op stores continue to struggle with stock availability after a cyber-attack, recovery expected by the weekend.
- Shoppers facing empty shelves, especially in rural areas; Co-op working with suppliers to restock stores with essential items.
- Hackers accessed customer data from Co-op systems, no financial information compromised.
- M&S also affected by cyber-attack, facing possible significant fines and loss of sales; expected to claim up to £100m from cyber insurers.
Read Full Article
6 Likes
Hackingblogs
13
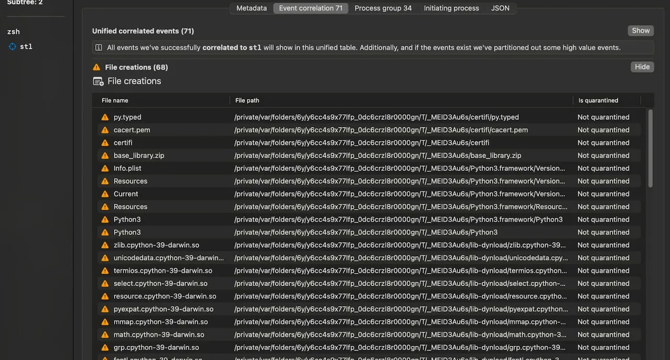
Image Credit: Hackingblogs
MacOS Malware Alert: Python-Based Infostealer Bundled via PyInstaller
- Researchers at Jamf Threat Labs discovered a MacOS malware using PyInstaller to distribute infostealer malicious software meant to steal confidential data.
- The malware prompts users for their password through an AppleScript dialog and communicates with suspicious domains like 'connect' patterned sites.
- PyInstaller is a tool for converting Python scripts into standalone executables that include all necessary components without requiring Python installation.
- Static analysis revealed the ad-hoc signing, architecture support for Intel and Apple Silicon Macs, and the use of PyInstaller in the malware file.
- Dynamic analysis using Mac Monitor exposed malicious activities like password prompts, volume reduction, Python script unpacking, and private information gathering.
- The malware's capabilities include password theft, AppleScript execution, Keychain credential extraction, and cryptocurrency wallet information theft.
- Attackers are increasingly using PyInstaller to cloak malware, as evidenced by the growing prevalence of infostealers on MacOS.
- Indicators of Compromise (IOCs) for the MacOS malware include filenames like stl, stl-deobf.py, installer, and sosorry, along with contacted domains.
Read Full Article
Like
Securityaffairs
4

Image Credit: Securityaffairs
Fortinet fixed actively exploited FortiVoice zero-day
- Fortinet has fixed a critical remote code execution zero-day vulnerability, CVE-2025-32756, actively exploited in attacks targeting FortiVoice enterprise phone systems.
- The vulnerability affects FortiVoice, FortiMail, FortiNDR, FortiRecorder, and FortiCamera, allowing remote unauthenticated attackers to execute arbitrary code via malicious HTTP requests.
- Threat actors exploiting the flaw scanned networks, erased crash logs, and deployed malware on compromised servers. They also added credential-stealing cron jobs and used scripts to scan victim networks.
- Fortinet recommends disabling the HTTP/HTTPS administrative interface as a workaround. The attackers were identified using several IP addresses and enabling the 'fcgi debugging' setting on compromised systems.
Read Full Article
Like
Idownloadblog
394

Image Credit: Idownloadblog
Lars Fröder, developer of Dopamine jailbreak, shares full video presentation from Nullcon Goa 2025 in March
- Lars Fröder, developer of Dopamine jailbreak, shared his full video presentation from Nullcon Goa 2025 in March.
- The presentation discussed the state of jailbreaking in 2025, including details about Dopamine, TrollStore, and challenges in jailbreak development.
- Fröder highlighted the reasons why people jailbreak their devices today, explained how TrollStore works, and discussed the challenges faced in jailbreak development.
- Fröder expressed skepticism about the future of jailbreaking on modern iOS devices due to Apple's security measures, making it tough to develop exploits.
Read Full Article
23 Likes
Arstechnica
133

Image Credit: Arstechnica
Google introduces Advanced Protection mode for its most at-risk Android users
- Google introduces Advanced Protection mode for Android to enhance security against attacks that infect devices, tap calls, and deliver scams.
- It will be rolled out in the upcoming release of Android 16 to help defend against mercenary malware and exploit sellers.
- The setting aims to combat attacks-as-a-service platforms that exploit zero-day vulnerabilities and capture sensitive information.
- Google recommends the Advanced Protection mode for high-risk users like journalists and elected officials.
Read Full Article
8 Likes
For uninterrupted reading, download the app