Hacking News
Securityaffairs
440

Image Credit: Securityaffairs
How Interlock Ransomware Affects the Defense Industrial Base Supply Chain
- Interlock Ransomware attack on a defense contractor exposed global defense supply chain details, risking operations of top contractors and their clients.
- Interlock Ransomware uncovered supply chain details of top defense contractors globally, leading to potential exposure of classified information and interest from foreign intelligence agencies and espionage groups.
- Numerous documents related to global defense corporations were found in the leaked dataset released by Interlock Ransomware.
- Ransomware attacks on defense contractors can have profound implications for national security, operational efficiency, financial stability, trust, and brand reputation, highlighting the need for robust cybersecurity measures and CMMC implementation.
Read Full Article
26 Likes
Securityaffairs
362

Image Credit: Securityaffairs
Marks and Spencer confirms data breach after April cyber attack
- Marks and Spencer confirms data breach after April cyber attack, where threat actors stole customer data.
- The cyber incident led to temporary changes in store operations and affected card payments, gift cards, and Click and Collect service.
- The stolen data includes customer contact details, birthdate, order history, and masked card details, but not full payment info.
- M&S recommends caution against phishing attempts, resetting passwords, and staying updated on security practices post-breach.
Read Full Article
21 Likes
Silicon
349
Image Credit: Silicon
Marks & Spencer Warns Customers Over Data Theft
- Marks & Spencer informed online customers of data theft during a cyber-attack on 25 April.
- The stolen data included contact details, dates of birth, and online order history.
- No card details, payment information, or account passwords were compromised.
- Customers are advised to change passwords as a precaution, and M&S is working on resolving the issue.
Read Full Article
21 Likes
Hackingblogs
450
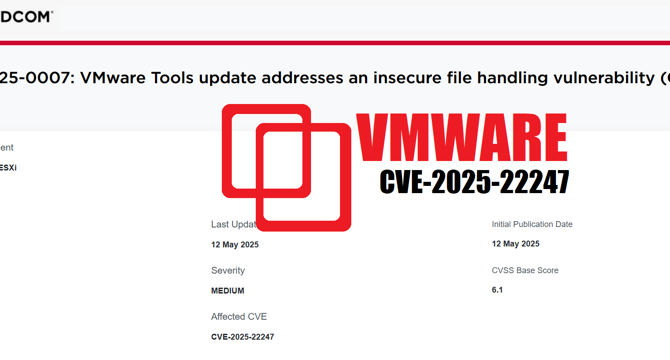
Image Credit: Hackingblogs
VMware Tools CVE-2025-22247 Vulnerability Lets Hackers Tamper with Virtual Machines: Patch Now
- VMware Tools CVE-2025-22247 Vulnerability affects VMware Tools software, allowing hackers to tamper with files inside guest VMs.
- The vulnerability impacts Windows and Linux virtual machines, but not macOS computers.
- The issue arises from the way VMware Tools processes local files within guest virtual machines.
- A patch (VMware Tools version 12.5.2) is available to address the vulnerability and organizations using VMware-based servers are advised to apply it for protection.
Read Full Article
27 Likes
Securityaffairs
45

Image Credit: Securityaffairs
Moldovan Police arrested a 45-year-old foreign man participating in ransomware attacks on Dutch companies
- A 45-year-old foreign man was arrested in Moldova for participating in ransomware attacks on Dutch companies in 2021.
- The arrest was a result of a joint international operation involving Moldovan and Dutch authorities, with the suspect wanted for cybercrimes including ransomware attacks and money laundering.
- The suspect was linked to a ransomware attack on the Netherlands Organization for Scientific Research, resulting in €4.5 million in damages, attributed to the DoppelPaymer ransomware operation.
- In a related development, Europol announced an international operation targeting key members of the DoppelPaymer ransomware group in March 2023.
Read Full Article
2 Likes
Securityaffairs
78
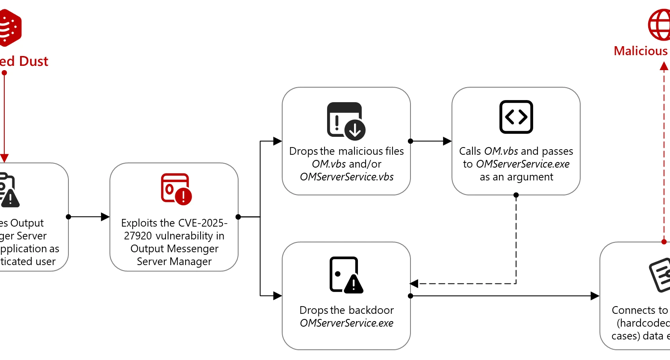
Image Credit: Securityaffairs
APT group exploited Output Messenger Zero-Day to target Kurdish military operating in Iraq
- A Türkiye-linked group, Marbled Dust, exploited a zero-day vulnerability in Output Messenger (CVE-2025-27920) to spy on Kurdish military targets in Iraq since April 2024.
- Marbled Dust, active since 2017, primarily targets organizations in Europe and the Middle East, with a history of using DNS hijacking in campaigns.
- The group targeted various entities, including government entities, Kurdish political groups, telecommunication, ISPs, NGO, and Media & Entertainment sectors.
- The exploit allowed the group to upload malicious files, gain access to user communications, steal data, compromise credentials, and deploy backdoors for exfiltration.
Read Full Article
4 Likes
Securelist
32

Image Credit: Securelist
Using a Mythic agent to optimize penetration testing
- Researchers are using post-exploitation frameworks like Mythic to enhance penetration testing practices to stay ahead of threat actors.
- A proactive approach in learning new technologies and techniques employed by threat actors is crucial for security professionals.
- Kaspersky emphasizes detecting tools and techniques used by threat actors in real-world attacks for enhanced security.
- Behavioral analysis, exploit prevention, and fileless threats protection are integral in countering sophisticated attacks.
- Layered security solutions like EDR, NDR, and XDR are essential for quick detection and response to potential threats.
- Pentesters face challenges due to the detectability of popular tools by security solutions.
- Open-source pentesting frameworks like Sliver and Havoc have limitations in payload size and stability.
- Balancing in-house solutions and open-source tools is crucial for effective pentesting.
- Pentesting payloads are divided into modules to manage execution and maintain covert communications.
- The Stage 1 module of the pentesting payload requires dynamic functionality, minimal system traces, and compliance with OPSEC principles.
Read Full Article
1 Like
TechDigest
280

Image Credit: TechDigest
M&S admits customer data was stolen in cyber attack
- Marks & Spencer has confirmed a cyber attack resulted in stolen customer data and disruptions to their operations.
- The incident affected customers' personal information, prompting password resets, but no payment details were compromised.
- The cyber attack led to online order halts, empty shelves, and a drop in M&S's share price.
- M&S is taking measures to investigate the breach, improve security, and recover from the incident that impacted its supply chain.
Read Full Article
16 Likes
Securityaffairs
41

Image Credit: Securityaffairs
Apple released security updates to fix multiple flaws in iOS and macOS
- Apple released urgent security updates for iOS and macOS to fix critical vulnerabilities that could be exploited by attackers.
- The updates address flaws in AppleJPEG, CoreMedia, ImageIO, and WebKit components that could lead to memory corruption or unexpected crashes.
- iOS 18.5 update resolved multiple critical flaws, including file-parsing issues in CoreAudio, CoreGraphics, and ImageIO.
- Updates for macOS and other Apple devices were also released to address vulnerabilities in various components like mDNSResponder, Notes, FrontBoard, iCloud Document Sharing, and Mail Addressing.
Read Full Article
2 Likes
Securityaffairs
73

Image Credit: Securityaffairs
Researchers found one-click RCE in ASUS’s pre-installed software DriverHub
- Two vulnerabilities were found in DriverHub, pre-installed on Asus motherboards, allowing remote code execution via crafted HTTP requests.
- The vulnerabilities, CVE-2025-3462 and CVE-2025-3463, were discovered by security researcher 'MrBruh' and could be exploited by a remote attacker to gain arbitrary code execution.
- The flaws in DriverHub stem from insufficient validation, enabling misuse of features such as accepting requests from unauthorized domains.
- Asus released security updates on May 9 in response to MrBruh's report, as the researcher highlighted the potential for remote code execution through the flawed DriverHub.
Read Full Article
4 Likes
Medium
160

Image Credit: Medium
Weird Leak? Favicon Caching Might Be Exposing You
- Modern browsers store favicon data in persistent caches that may not get cleared even in private or incognito mode.
- Some sites pull favicons from third-party domains, potentially exposing users' visits to these sites.
- Favicon caching could be used as a fingerprintable vector in conjunction with other metadata leaks for tracking purposes.
- Community discussion is ongoing on whether to actively block or route favicons to prevent potential privacy risks.
Read Full Article
9 Likes
Massivelyop
349

Activision lawsuit argues hackers make PC players quit Call of Duty Black Ops 6 over toxicity
- Activision has filed a lawsuit against the creators of hacking programs for Call of Duty: Black Ops 6, alleging that these hacks have made the multiplayer experience toxic for PC players.
- The lawsuit names Ryan Rothholz, Collin Gyetvai, and Jordan Newcombe Boothey for creating and distributing hacking programs like Lergware and GameHook that enable cheating in the game.
- Activision claims that attempts to engage with the creators of the hacking programs were ignored, leading to legal action being taken by the company.
- The company argues that such hacking programs not only harm the game's community but also impact its financial performance by driving players away from the PC version of Call of Duty: Black Ops 6.
Read Full Article
21 Likes
Securityaffairs
73
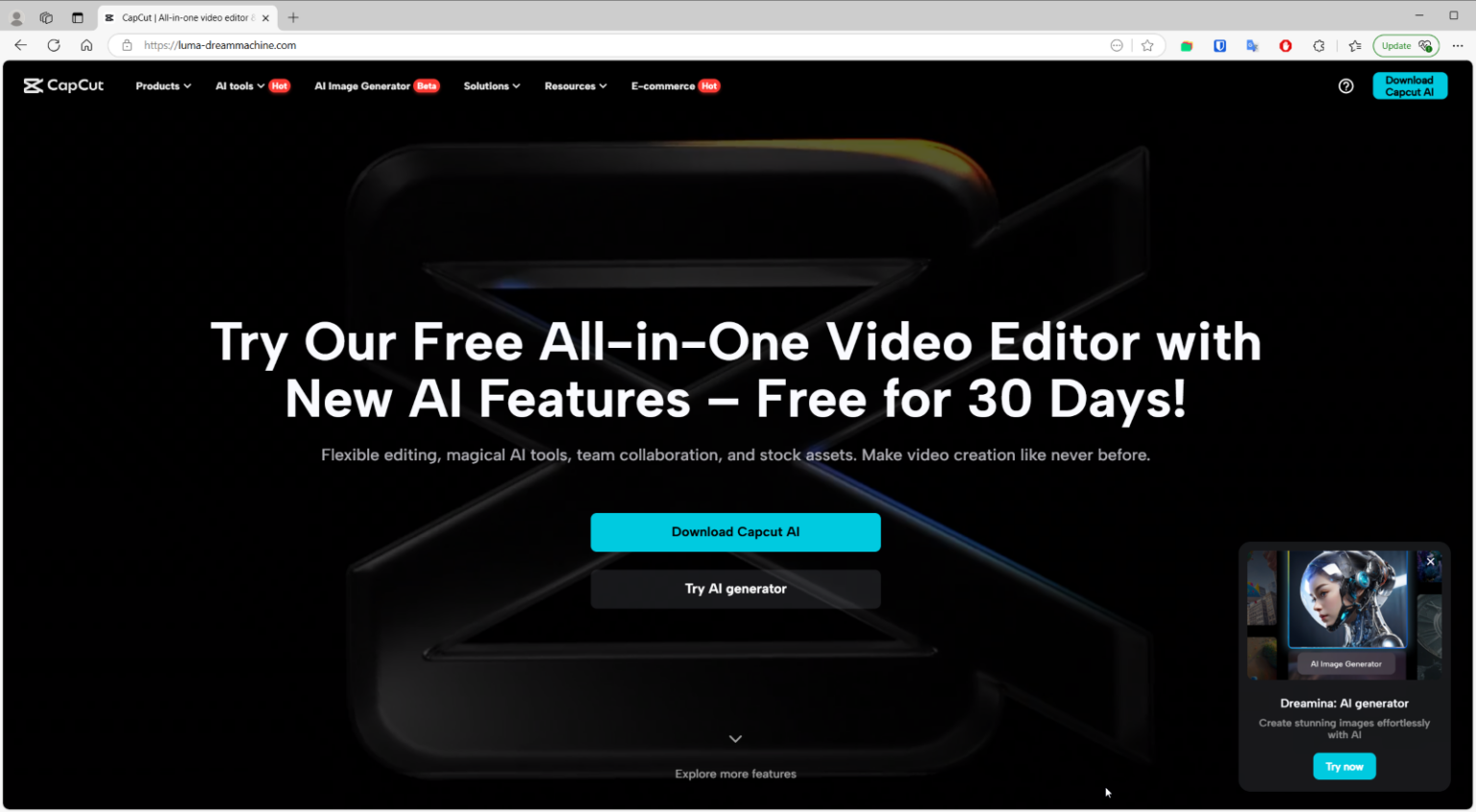
Image Credit: Securityaffairs
Threat actors use fake AI tools to deliver the information stealer Noodlophile
- Threat actors are using fake AI tools to distribute the information stealer Noodlophile, as warned by Morphisec researchers.
- Attackers exploit the AI hype through viral posts and Facebook groups to trick users into downloading Noodlophile Stealer, a new malware that steals browser credentials and crypto wallets.
- Noodlophile Stealer, a previously undisclosed malware, is being sold on cybercrime forums as part of malware-as-a-service schemes and is often bundled with tools for credential theft.
- Fake AI tools like 'Dream Machine' or 'CapCut' spread through social media, attracting users seeking free video/image editors, but instead delivering malware like Noodlophile or XWorm.
Read Full Article
4 Likes
Hackingblogs
110
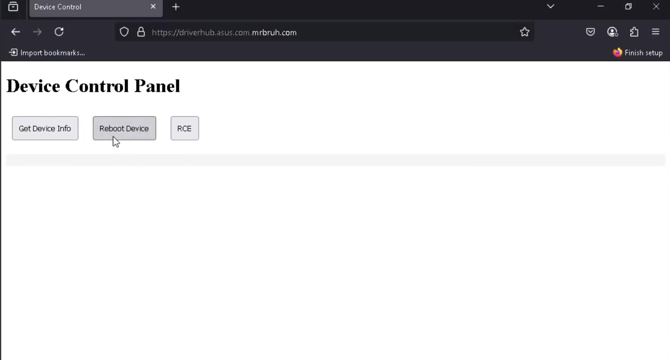
Image Credit: Hackingblogs
One-Click Exploit: ASUS DriverHub RCE Vulnerability Exposes Admin Access
- Security researcher Paul discovered a critical ASUS DriverHub RCE vulnerability that allows attackers to execute code with admin privileges by tricking users into visiting a malicious website.
- DriverHub, a background process by ASUS, interacts with the website driverhub.asus.com using Remote Procedure Calls (RPC) instead of a graphical user interface.
- Key findings of the vulnerability include DriverHub hosting a local HTTP service, vulnerability in Origin header validation, and exploitable endpoints like InstallApp and UpdateApp which is the basis of the exploit.
- The exploit chain involves making an UpdateApp request to download a harmless-looking executable, injecting INI files, and executing a signed executable with admin rights, demonstrating the severity of the ASUS DriverHub RCE vulnerability.
Read Full Article
6 Likes
Securityaffairs
50

Image Credit: Securityaffairs
German police seized eXch crypto exchange
- Germany's Federal Criminal Police (BKA) shut down the eXch crypto exchange (eXch.cx), seizing its infrastructure over money laundering and illegal trading allegations.
- The German law enforcement seized €34M in crypto and 8TB of data from the platform, marking its third-largest crypto asset seizure ever.
- eXch crypto exchange had been active since 2014, enabling anonymous crypto swaps via clearnet and darknet, avoiding Anti Money Laundering rules. Authorities suspect the platform allowed laundering $1.9B.
- eXch announced it would shut down on May 1, 2025, amid suspicions of money laundering and illegal trading. Despite the shutdown announcement, authorities swiftly seized data and crypto assets from the platform.
Read Full Article
3 Likes
For uninterrupted reading, download the app