Hacking News
Securityaffairs
419

Image Credit: Securityaffairs
U.S. CISA adds a Samsung MagicINFO 9 Server flaw to its Known Exploited Vulnerabilities catalog
- The U.S. Cybersecurity and Infrastructure Security Agency (CISA) added a Samsung MagicINFO 9 Server vulnerability, tracked as CVE-2025-4632 (CVSS score of 9.8), to its Known Exploited Vulnerabilities (KEV) catalog.
- The vulnerability is an improper limitation of a pathname to a restricted directory vulnerability that impacts Samsung MagicINFO 9 Server version before 21.1052, allowing attackers to write arbitrary files as system authority.
- CISA issued Binding Operational Directive (BOD) 22-01 to address identified vulnerabilities by June 12, 2025, for Federal Civilian Executive Branch (FCEB) agencies, urging private organizations to review the Catalog and address vulnerabilities in their infrastructure.
- This week, CISA also added Ivanti EPMM, MDaemon Email Server, Srimax Output Messenger, Zimbra Collaboration, and ZKTeco BioTime flaws to its Known Exploited Vulnerabilities catalog.
Read Full Article
25 Likes
Arstechnica
392

Image Credit: Arstechnica
Why console makers can legally brick your game console
- Nintendo recently updated their EULA, stating the right to make Switch consoles unusable for hacking or piracy violations.
- Other console makers like Sony also have clauses in their agreements allowing them to disable systems for unauthorized activities.
- Sony's System Software License Agreement for PS5 provides a range of actions for violations, including disabling access to system software and network, among others.
- Similar clauses are present in PlayStation 4 and PlayStation 3 agreements, giving manufacturers legal rights to prevent unauthorized use of their systems.
Read Full Article
23 Likes
Siliconangle
169

Image Credit: Siliconangle
Cybersecurity researcher discovers database with millions of login credentials
- A cybersecurity researcher discovered an exposed Elasticsearch database with millions of login credentials on May 6.
- The database contained 184 million records taking up 47 gigabytes of storage space, with login credentials associated with millions of accounts from various services like Google, Facebook, Roblox, Discord, and others.
- There were 220 email addresses with .gov domains linked to government agencies in at least 29 countries, including the U.S., UK, and Australia.
- The database was hosted on infrastructure operated by World Host Group, a U.K.-based hosting provider, which took it down after being notified by the researcher.
Read Full Article
10 Likes
BGR
232

Image Credit: BGR
184 million logins exposed in ‘dream come true for cyber criminals’
- Cybersecurity researcher Jeremiah Fowler discovered a publicly exposed database containing 184,162,718 unique logins and passwords, amounting to over 47GB of data.
- The database included emails, usernames, passwords, and more for services like Microsoft, Meta, Snapchat, and Roblox, as well as logins for bank accounts, health platforms, and government portals from multiple countries.
- Fowler sent a responsible disclosure notice to the hosting provider as he couldn't verify the owner's identity, which led to the database being restricted from public access.
- The leaked data was confirmed authentic by contacting email addresses listed, with concerns that it might have been gathered by infostealer malware, emphasizing the need for users to delete old emails containing sensitive information.
Read Full Article
13 Likes
Securityaffairs
346
Image Credit: Securityaffairs
New Signal update stops Windows from capturing user chats
- Signal update for Windows app blocks screenshots by default to protect user privacy from Microsoft's Recall feature.
- The new 'Screen security' setting in Signal Desktop prevents Windows from capturing screenshots of Signal chats.
- Microsoft's Recall feature captures screenshots of users' laptops every few seconds, raising privacy concerns.
- Signal's screen security can be disabled but may impact accessibility tools; the setting only applies locally on Windows 11.
Read Full Article
20 Likes
Siliconangle
123

Image Credit: Siliconangle
Picus Security launches Exposure Validation to help teams focus on exploitable vulnerabilities
- Picus Security has launched Picus Exposure Validation, a service that helps security teams verify exploitability of vulnerabilities based on their unique environments.
- The new service allows continuous testing of security controls against real-world attack techniques to identify truly exploitable vulnerabilities and prioritize them accurately.
- Picus Exposure Validation offers evidence-based, context-aware metrics to quantify actual risk by assessing how effectively current security controls mitigate real threats.
- This new capability aims to help security teams focus on vulnerabilities that truly matter, provide faster decision-making, save time, and improve mitigation efforts through automated validation.
Read Full Article
7 Likes
Securityaffairs
433
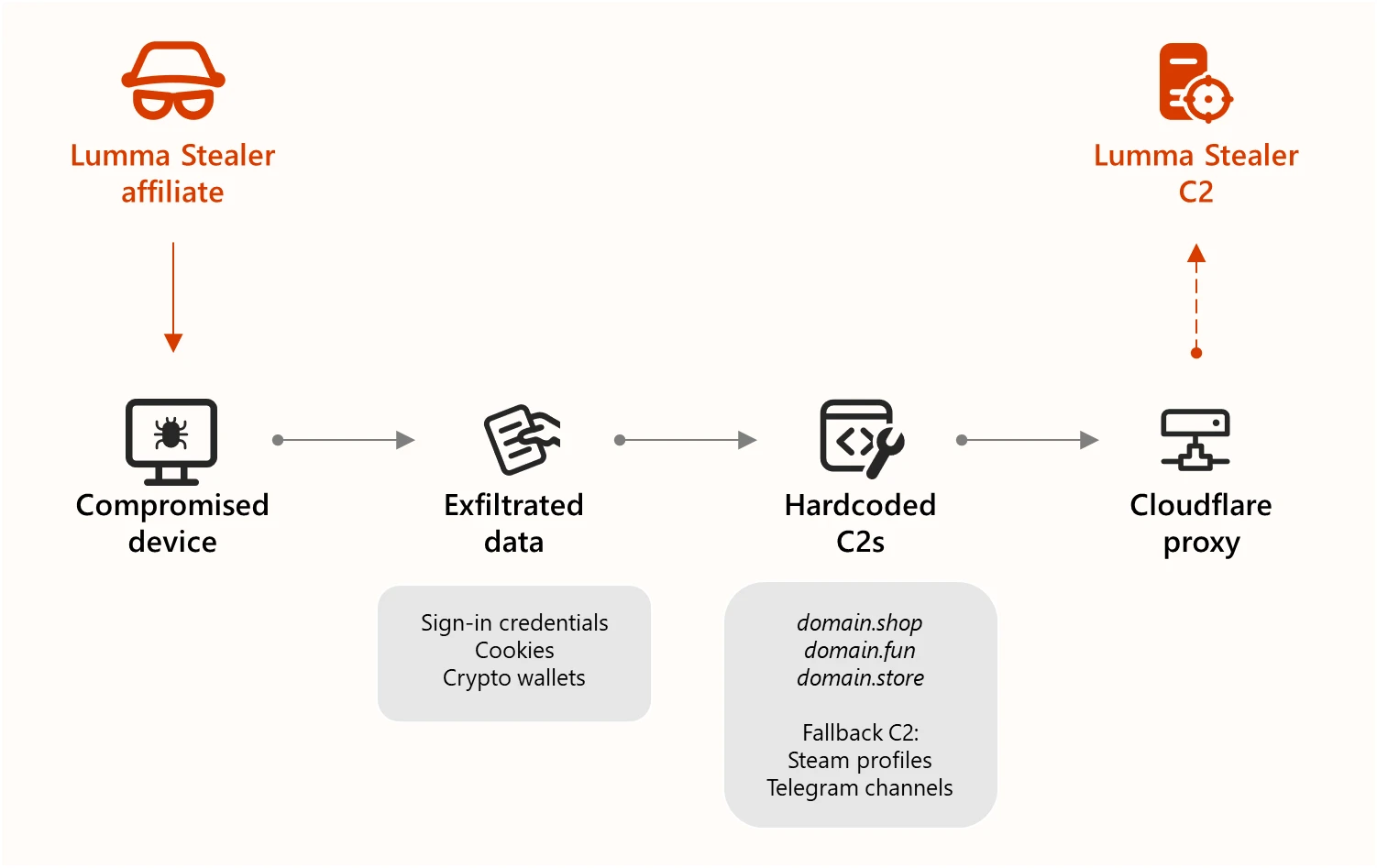
Image Credit: Securityaffairs
Law enforcement dismantled the infrastructure behind Lumma Stealer MaaS
- Law enforcement, with the help of Microsoft, Europol, and Japan’s JC3, dismantled the infrastructure behind Lumma Stealer Malware-as-a-Service (MaaS) operation, seizing 2,300 domains used for command-and-control.
- The malware, known as Lumma Stealer, targeted over 394,000 Windows systems, including those of global manufacturers, to steal sensitive data like passwords, credit card information, and crypto wallet keys.
- Microsoft's Digital Crimes Unit sinkholed over 1,300 domains used by Lumma Stealer to reroute victims to safe servers for analysis and cleanup, showcasing the collaboration between law enforcement and tech companies against cyber threats.
- The FBI and US CISA released a joint advisory containing tactics, techniques, and procedures associated with Lumma Stealer, along with indicators of compromise (IOCs), emphasizing the importance of public-private partnerships in combating cybercrime.
Read Full Article
26 Likes
Securityaffairs
132
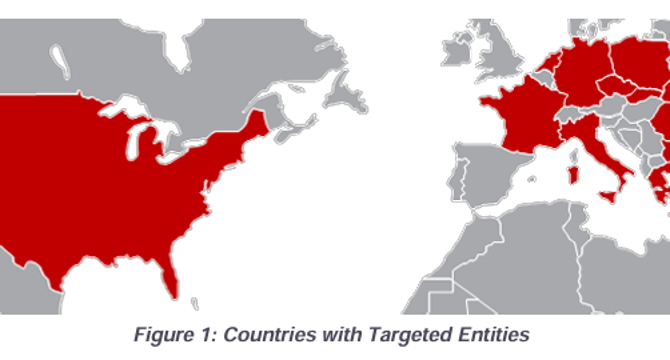
Image Credit: Securityaffairs
Russia-linked APT28 targets western logistics entities and technology firms
- CISA warns that Russia-linked APT28 is targeting Western logistics and technology companies aiding Ukraine, posing a heightened threat to supply chains.
- APT28, also known as Fancy Bear, has been active since at least 2007 and has targeted governments, militaries, and security organizations globally, including the 2016 Presidential election.
- The group operates from Russian military unit 26165 of GRU 85th Main Special Service Center, targeting Western logistics and tech firms linked to Ukraine aid across 13 countries using various tactics like spear-phishing and exploiting vulnerabilities.
- GRU Unit 26165 used tactics such as spearphishing with fake login pages, exploiting Outlook and Roundcube vulnerabilities, deploying custom malware like HEADLACE and MASEPIE, and exfiltrating data using PowerShell and APIs, targeting Western logistics and IT sectors.
Read Full Article
7 Likes
Hackersking
50
Image Credit: Hackersking
Puter The Internet OS! Free, Open-Source, and Self-Hostable
- Puter is an advanced, open-source internet operating system designed for the internet age, offering a browser-based desktop environment.
- Key features of Puter include being free, open-source, self-hostable, cross-platform compatible, lightweight, and highly customizable.
- Setting up Puter can be done locally using npm or via Docker, with instructions provided for both methods.
- Puter represents a significant advancement in operating systems, providing a flexible and user-friendly environment for various computing needs. Contribute to the project on GitHub: https://github.com/HeyPuter/puter
Read Full Article
3 Likes
Siliconangle
4

Image Credit: Siliconangle
Global law enforcement and Microsoft take down Lumma malware infrastructure
- A global law enforcement operation, supported by Microsoft Corp., has disrupted the infrastructure behind Lumma, a popular malware-as-a-service tool known for widespread information theft.
- The U.S. Department of Justice coordinated the takedown of Lumma, leading to the seizure of domains used for Lumma distribution, enabling cybercriminals to steal sensitive data globally.
- Lumma, which emerged in December 2022, was widely used due to its affordability and ease of deployment. It allowed low-skilled threat actors to conduct sophisticated attacks, targeting various data types.
- Despite the takedown, concerns remain about potential reemergence of Lumma or similar threats, as threat actors often adapt quickly with rebrands, new delivery methods, and rebuilt infrastructure.
Read Full Article
Like
Securityaffairs
210

Image Credit: Securityaffairs
A cyberattack was responsible for the week-long outage affecting Cellcom wireless network
- Cellcom, a regional wireless carrier based in Wisconsin, confirmed a cyberattack that caused a week-long outage affecting voice and text services in Wisconsin and Upper Michigan.
- The company announced it has begun restoring services and stated it had protocols in place for such incidents to address the cyberattack.
- Cellcom reported that the cyberattack impacted a network area not linked to the storage of sensitive information, and there's no evidence of customer personal or financial information being compromised.
- The company is working with external cybersecurity experts, local authorities, and aims to fully restore its services by the end of the week.
Read Full Article
12 Likes
Medium
18

Image Credit: Medium
Cybersecurity Advisory: Hackers Exploit CAPTCHA Trick on Webflow to Deliver Phishing Attacks
- Hackers are exploiting a CAPTCHA trick on Webflow to deliver phishing attacks, turning the defense mechanism into an attack vector.
- The attack is effective because it deceives users by appearing as a legitimate CAPTCHA, bypassing security measures.
- To protect against such attacks, organizations should adopt a multi-layered defense strategy, including security tools and continuous education.
- The evolving sophistication of cybercriminals underscores the importance of user vigilance and prioritizing cybersecurity to mitigate risks.
Read Full Article
1 Like
Medium
82

Image Credit: Medium
Top 3 Microsoft Office Exploits Hackers Are Using in 2025 & How to Stop Them
- 1. Phishing with Malicious Documents (The Enduring Classic): Hackers continue to use phishing emails with malicious Office documents to trick users.
- 2. Old Vulnerabilities That Won’t Die (The “Follina” and Equation Editor Legacy): Exploits like Follina and Equation Editor persist due to unpatched systems and can be delivered via phishing.
- 3. Privilege Escalation & Sandbox Escapes (The Sneaky Insiders): Attackers leverage vulnerabilities in Windows components related to Office to gain higher privileges or escape application sandboxes.
- The Bottom Line: A layered security approach combining user education, robust technical controls, continuous patching, and proactive monitoring is crucial to stay secure against Microsoft Office exploits in 2025.
Read Full Article
4 Likes
Medium
120

Image Credit: Medium
Cybersecurity Advisory: Hackers Exploit Zoom’s Remote Control Feature
- Hackers are exploiting Zoom's remote control feature, allowing them to take control of a participant's screen, keyboard, and mouse.
- The exploitation is not a flaw in the feature itself but rather how attackers misuse it through social engineering tactics.
- The widespread adoption of Zoom makes many individuals and organizations potentially vulnerable to this type of attack.
- To protect yourself, take concrete steps like being cautious of remote control requests and staying informed about cybersecurity best practices.
Read Full Article
7 Likes
Guardian
65
Image Credit: Guardian
The cyber-attack is costly and embarrassing. But M&S should pull through
- Marks & Spencer's recent cyber-attack, costing £300m, has raised questions about IT system robustness and response time for website restoration.
- CEO Stuart Machin defended M&S by attributing the incident to bad luck and assuring return to normalcy by July.
- Assessment of corporate responses to cyber-attacks is challenging, but M&S's financial resilience and solid balance sheet may help absorb the impact.
- While the long-term impact on customer behavior remains uncertain, M&S's share price saw a slight recovery post-incident, indicating investor confidence in the company's ability to navigate the situation.
Read Full Article
3 Likes
For uninterrupted reading, download the app