Hacking News
Securityaffairs
412
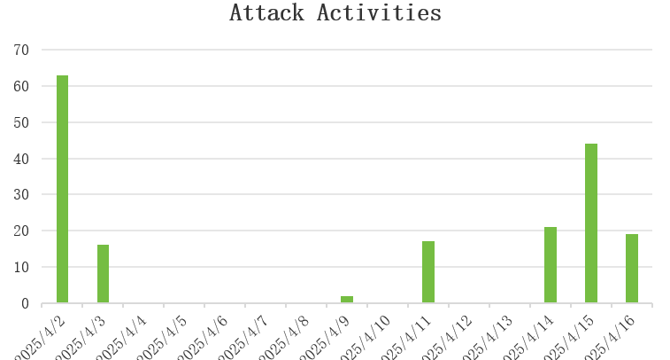
Image Credit: Securityaffairs
New botnet HTTPBot targets gaming and tech industries with surgical attacks
- A new botnet named HTTPBot is targeting China’s gaming, tech, and education sectors, as discovered by cybersecurity researchers.
- HTTPBot, a Go-based botnet detected in August 2024, intensified its activities by April 2025, engaging in highly targeted attacks using advanced DDoS tactics.
- The botnet employs various HTTP-based attack methods to conduct precise transactional DDoS attacks on critical interfaces, posing a systemic threat to industries reliant on real-time interaction.
- HTTPBot features 7 built-in DDoS attack methods, evades detection through techniques like Base64 encoding, and specifically targets the Windows platform, making it a significant threat in the cybersecurity landscape.
Read Full Article
24 Likes
Cryptopotato
430

Image Credit: Cryptopotato
Hackers Had Access to Coinbase Customer Data Since January: Report
- Hackers gained unauthorized access to sensitive customer data at Coinbase as early as January, following the recent $400 million breach.
- Attackers bribed foreign-based support staff to obtain names, birth dates, addresses, ID numbers, banking details, and more, which could be used for impersonation and unauthorized access to accounts.
- Coinbase refuted claims of constant access since January but confirmed multiple bribery incidents involving support agents. Less than 1% of monthly users were affected by the breach, with no compromise of login credentials or wallets.
- Coinbase is offering reimbursements to affected users, enhancing security measures, launching a $20 million bounty, and collaborating with authorities to pursue criminal charges against the perpetrators.
Read Full Article
25 Likes
Securityaffairs
325

Image Credit: Securityaffairs
Meta plans to train AI on EU user data from May 27 without consent
- Meta plans to train AI on EU user data from May 27 without explicit consent, facing threats of a lawsuit from privacy group noyb.
- Meta intends to use public data from EU adults for AI training, emphasizing the need to reflect European diversity.
- The company postponed AI model training last year due to data protection concerns raised by Irish regulators.
- Noyb issued a cease-and-desist letter to Meta regarding the use of EU personal data for AI systems without opt-in consent.
- Meta states it does not use private messages and excludes data from EU users under 18 for AI training.
- The Austrian privacy group argues that Meta's AI training practices may violate GDPR by not requiring opt-in consent.
- Meta defends its AI data practices, claiming compliance with European Data Protection Board guidance and Irish privacy regulations.
- Noyb insists on the necessity of opt-in consent for AI training, challenging Meta's reliance on 'legitimate interest' as inadequate.
- Meta faces potential legal risks due to its opt-out approach for AI training, risking injunctions and class action lawsuits.
- Concerns raised include Meta's decision to gather user data for AI without explicit consent and its impact on GDPR compliance.
Read Full Article
19 Likes
TheNewsCrypto
421

US DOJ Charges 12 More in $263M Bitcoin Theft and Laundering Case
- US Department of Justice (DOJ) has charged 12 more individuals in connection with a $263 million Bitcoin theft and money laundering scheme.
- The suspects allegedly used stolen BTC to fund luxurious lifestyles and engage in global fraud activities.
- The group employed various tactics like social engineering, data theft, and burglary to steal funds from victims' crypto wallets.
- The charges include Racketeer Influenced and Corrupt Organizations (RICO) Act violations, wire fraud, and money laundering, with suspects involved in lavish spending on luxury items.
Read Full Article
25 Likes
Securityaffairs
366

Image Credit: Securityaffairs
Google fixed a Chrome vulnerability that could lead to full account takeover
- Google released emergency security updates to fix a Chrome vulnerability (CVE-2025-4664) that could lead to full account takeover.
- The vulnerability, discovered by security researcher Vsevolod Kokorin, allowed for the leaking of cross-origin data via a crafted HTML page.
- Google warned of a public exploit for the high-severity flaw, and patched it in Chrome's Stable Desktop channel with updates in versions 136.0.7103.113 and 136.0.7103.114.
- In March 2025, Google addressed another high-severity vulnerability (CVE-2025-2783) actively exploited in attacks targeting organizations in Russia, related to Mojo on Windows.
Read Full Article
22 Likes
HRKatha
394

Image Credit: HRKatha
Were Coinbase employees responsible for data leak to hacker?
- A hacker has bribed Coinbase Global's contractors or employees outside the US to access confidential customer information and is now demanding a $20 million ransom.
- The hacker bribed customer-support employees to obtain customer data like names, addresses, and government identity pictures to potentially use in scams and extort money from the exchange.
- Coinbase CEO Brian Armstrong revealed the ransom demand on social media and stated that the breach may cost the exchange up to $400 million.
- Coinbase is improving security measures, offering compensation to affected users, and is ready to pay a $20 million reward for information leading to the hacker's apprehension.
Read Full Article
23 Likes
Idownloadblog
201

Image Credit: Idownloadblog
Alfiecg_dev shares details about an updated untethered iOS 14 jailbreak that uses the Trigon exploit
- Security researcher @alfiecg_dev introduces an updated untethered iOS 14 jailbreak using the Trigon exploit.
- The original Trigon exploit had limited support for older devices and firmware due to a kernel panic issue with A11 devices, which has now been resolved.
- The newer version of Trigon now supports A7-A9 and A11 devices, offering increased stability, faster response time, and cleaned up code.
- While the updated Trigon exploit will be released for all arm64 devices in the future, there is no specific timeline provided by @alfiecg_dev yet.
Read Full Article
12 Likes
99Bitcoins
348

Coinbase Hacked: Up to $400M at Risk After Insider Scam
- Coinbase is facing losses between $180 million and $400 million after a targeted insider-driven cyber attack compromised its internal systems.
- Attackers bribed contractors and employees to gain internal access and impersonated Coinbase staff to trick users into handing over crypto.
- Coinbase refused to pay a $20 million ransom, promising to reimburse affected users and investigate the breach.
- The company fired insiders involved in the scam and launched a $20 million bounty fund to track down the attackers.
- The hack emphasizes cybersecurity threats in the crypto industry, showcasing vulnerability to insider manipulation.
- Coinbase's estimated losses include breach costs, user reimbursements, and potential legal consequences.
- Investors reacted with a 4% stock drop after news of the cyber attack.
- Cryptocurrency platforms, including Coinbase, need heightened security measures to combat evolving attack tactics.
- Users are advised by Coinbase to remain vigilant against scams and report suspicious activity promptly.
- The incident serves as a warning for all crypto platforms and users to prioritize security and trust in the sector.
Read Full Article
20 Likes
Securityaffairs
64

Image Credit: Securityaffairs
Nova Scotia Power discloses data breach after March security incident
- Nova Scotia Power confirmed a data breach after a security incident in April where sensitive customer data was stolen.
- In April, Nova Scotia Power and Emera experienced a cyber attack affecting their IT systems without causing power outages.
- The companies shut down affected servers due to unauthorized network access detected on April 25, impacting customer services.
- The data breach involved theft of customer information including names, contact details, account history, driver’s license numbers, and Social Insurance Numbers.
Read Full Article
3 Likes
Medium
183

Image Credit: Medium
The Great Steam “Hack” of 2025
- Headlines blared about '89 Million Steam Accounts Hacked', causing a stir in the gaming community.
- Hackers attempted to sell secret data for $5,000, but the actual 'stolen' data turned out to be expired SMS 2FA codes and unlinked phone numbers.
- Valve dismissed the incident as no breach, clarifying that only outdated codes were involved.
- Ultimately, the hackers did not gain access to valuable information like passwords or credit card details, leaving the gaming world relieved.
Read Full Article
11 Likes
Securityaffairs
293

Image Credit: Securityaffairs
Coinbase disclosed a data breach after an extortion attempt
- Coinbase disclosed a data breach after rogue contractors stole customer data and demanded a $20M ransom.
- The breach, affecting under 1% of users, was reported to the SEC after a ransom demand was received on May 11, 2025.
- The unauthorized access was detected in previous months, leading to termination of involved personnel and implementation of heightened fraud-monitoring measures.
- Compromised data includes contact details, partial SSNs and bank info, ID images, account history, and limited internal documents but did not expose passwords, private keys, or customer funds.
Read Full Article
17 Likes
Bitcoinist
330

Image Credit: Bitcoinist
What The?! $400 Million Gone! Insider Phishing Attack Shakes Coinbase
- Coinbase faced a threat from outside attackers attempting to extort $20 million in Bitcoin, resulting in personal account details being leaked by paid off support agents.
- Less than 1% of Coinbase's monthly active traders had some of their data exposed, as a handful of customer-support contractors accessed internal tools to extract names, email addresses, and limited transaction records.
- Coinbase refused to pay the hackers' demand and instead announced a $20 million bounty to track down those responsible, and plans to set aside $180 million to $400 million for customer reimbursements for phishing scam losses.
- Phishing losses for Coinbase users are rising, estimated at over $300 million annually, prompting Coinbase to strengthen defenses by improving data controls, relocating support work, enhancing staff checks, and upgrading fraud-monitoring tools.
Read Full Article
19 Likes
Siliconangle
96

Image Credit: Siliconangle
Coinbase suffers data breach, exposing customer information to hackers
- Coinbase Global Inc. disclosed a data breach where cybercriminals bribed offshore customer service support agents to steal customer data.
- No passwords, private keys, or funds were exposed, but personal customer information such as names, addresses, phone numbers, email addresses, and limited corporate data were stolen.
- Attackers did not access login credentials or private keys to move or access customer funds.
- Coinbase refused a $20 million payoff demanded by the attackers and instead turned it into a $20 million bounty for information leading to the arrest of the criminals; estimated costs for the company range between $180 million and $400 million for reimbursement and expenses.
Read Full Article
5 Likes
Securelist
330

Image Credit: Securelist
Threat landscape for industrial automation systems in Q1 2025
- The percentage of ICS computers on which malicious objects were blocked remained stable in Q1 2025, at 21.9%.
- Quarterly figures show a decreasing trend year over year, with a decrease of 2.5 pp compared to Q1 2024.
- Biometrics sector saw an increase in malicious object blocks, the only OT infrastructure type where this occurred.
- Threat levels vary regionally, with Northern Europe at 10.7% and Africa at 29.6% affected ICS computers.
- Denylisted internet resources blocked and email threats decreased in Q1 2025, hitting a low since 2022.
- Primary threats from the internet include denylisted resources, malicious scripts, and phishing pages.
- Malicious scripts, phishing pages, and documents showed an increase in blocks in Q1 2025.
- AutoCAD malware saw the lowest percentage of blocks among ICS computers and continued to decrease.
- Web miners and malicious documents blocks increased notably in Q1 2025.
- The percentage of ICS computers on which worms, viruses, and cad malware were blocked decreased in Q1 2025.
Read Full Article
19 Likes
Securityaffairs
151

Image Credit: Securityaffairs
U.S. CISA adds a Fortinet flaw to its Known Exploited Vulnerabilities catalog
- U.S. Cybersecurity and Infrastructure Security Agency (CISA) added a Fortinet vulnerability to its Known Exploited Vulnerabilities catalog, impacting several Fortinet products.
- A critical remote code execution zero-day vulnerability, CVE-2025-32756, in FortiVoice systems was exploited by threat actors to execute arbitrary code.
- Attackers scanned networks, erased crash logs, enabled debugging, and captured login credentials after exploiting the vulnerability.
- CISA ordered federal agencies to address the identified vulnerability by June 4, 2025, in line with cybersecurity directives to protect networks and infrastructure from potential attacks.
Read Full Article
9 Likes
For uninterrupted reading, download the app