Hacking News
Metro
206

Image Credit: Metro
Supplier to Tesco, Sainsbury’s, and Aldi ‘held to ransom’ in cyber attack
- A distributor to major UK supermarkets including Tesco, Sainsbury's, and Aldi, Peter Green Chilled, was targeted by cyber hackers demanding ransom.
- The cyber attack occurred last week, leading the logistics firm to halt order processing on Thursday, affecting suppliers like Mr Emmanuel-Jones, who risk losing products like ten pallets of meat if not delivered to retailers.
- Cyber expert Tim Grieveson highlights the impact of cyber attacks on supply chains, emphasizing the potential for disrupted operations, wasted inventory, lost revenue, and food security issues like spoiled perishable goods.
- Similar cyber attacks have been reported on major supermarkets like M&S, resulting in significant financial losses and data breaches, emphasizing the critical need for cybersecurity measures to safeguard supply chain operations.
Read Full Article
12 Likes
Medium
388
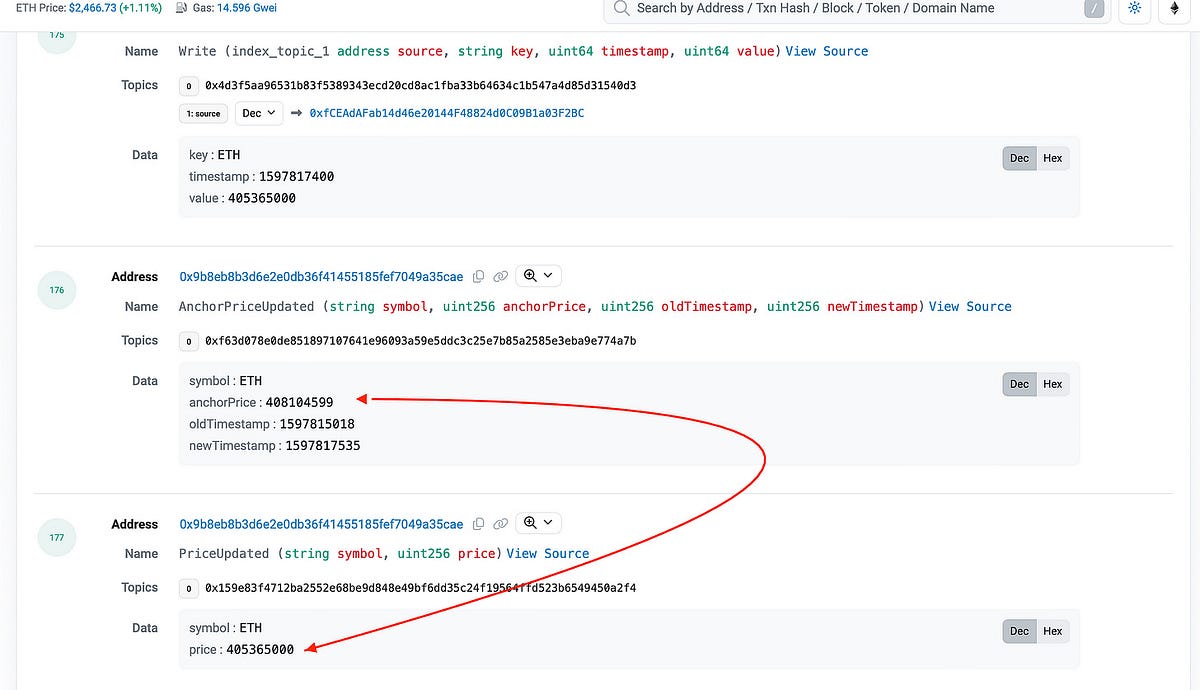
Image Credit: Medium
DeFi Summer: The Golden Days of Liquidation
- A new liquidation bot, address 0x8329F4, has been dominating the Compound v2 battlefield by winning liquidations consistently despite not being the fastest or most efficient.
- This successful performance by the new liquidator started after Compound introduced the Open Price Feed Proposal on August 20, 2020, aiming to increase transparency in asset price updates and community participation.
- The liquidator manipulated the system by posting prices and exploiting the protocol mechanics, ultimately using GasToken2 to increase profits by executing the liquidation in one atomic transaction.
- This incident showcases how understanding and leveraging protocol mechanics in DeFi can be more important than speed or gas optimization, ultimately leading to successful operations within the system.
Read Full Article
23 Likes
Securityaffairs
274

Image Credit: Securityaffairs
Mozilla fixed zero-days recently demonstrated at Pwn2Own Berlin 2025
- Mozilla addressed two critical vulnerabilities in the Firefox browser that could have been exploited to access sensitive data or achieve code execution.
- The vulnerabilities were demonstrated as zero-day flaws during the recent Pwn2Own Berlin 2025 hacking contest.
- One vulnerability, CVE-2025-4918, involved an out-of-bounds access when resolving Promise objects.
- The other vulnerability, CVE-2025-4919, pertained to an out-of-bounds access when optimizing linear sums.
Read Full Article
16 Likes
Hackersking
352

Image Credit: Hackersking
Top Entry Points for Cyber Attacks: What Every Organization Must Know
- Cyber threats are becoming more complex and frequent, emphasizing the importance of cybersecurity awareness for individuals and organizations.
- Credential-based attacks account for over half of all cyber intrusions, with common techniques including phishing, social engineering, and brute-force attacks.
- Device attacks target misconfigured or outdated systems through methods like malware attacks, zero-day exploits, and misconfiguration exploits.
- Initial infection vectors, though the smallest portion, can still lead to serious breaches and include methods like drive-by downloads, watering hole attacks, and malvertising.
Read Full Article
21 Likes
Securityaffairs
420

Image Credit: Securityaffairs
Japan passed a law allowing preemptive offensive cyber actions
- Japan has enacted the Active Cyberdefense Law, allowing preemptive offensive cyber operations to counter threats before damage occurs.
- The law permits government agencies to conduct hacking back operations to neutralize threat actors targeting Japan and its organizations.
- Japan's new Active Cyberdefense Law enables preemptive targeting of hostile infrastructure, reflecting a shift in national and allied security priorities.
- The Japanese government aims to fully implement the new legal framework by 2027 to enhance cyber defense capabilities and align with major Western powers.
Read Full Article
25 Likes
Securityaffairs
324

Image Credit: Securityaffairs
James Comey is under investigation by Secret Service for a seashell photo showing “8647”
- Former FBI chief James Comey is under investigation by the Secret Service for sharing an image of seashells arranged to display the numbers ‘8647,’ which some interpret as incitement to violence against Trump.
- The post on Instagram was later deleted, and the Secret Service is investigating the matter.
- The number '86' is slang for 'to reject' or 'to get rid of', and '47' is likely a reference to Trump being the 47th US president.
- Comey claims he did not know what the numbers meant and removed the post, stating he opposes violence.
Read Full Article
19 Likes
Securityaffairs
274

Image Credit: Securityaffairs
Pwn2Own Berlin 2025: total prize money reached $1,078,750
- Pwn2Own Berlin 2025 total prize money reached $1,078,750 over three days, with $383,750 awarded on the final day.
- Participants demonstrated 28 unique zero-days in products such as VMware Workstation, ESXi, Windows, NVIDIA, and Firefox, earning a total of $1,078,750, including 7 in the AI category.
- STAR Labs SG won the 'Master of Pwn' title with $320,000 and 35 points.
- Various participants exploited vulnerabilities, with exploits including a zero-day in ESXi earning $112,500, a heap-based buffer overflow in VMware Workstation earning $80,000, and a TOCTOU race condition in Windows earning $70,000.
Read Full Article
16 Likes
Medium
132

Building Ransomware Resilience: Why Product Strategies Must Prioritise Comprehensive Recovery Plans
- The April 2025 ransomware attacks on major retailers exposed vulnerabilities, leading to data theft and disruptions in operations.
- Recovery plans are crucial in dealing with modern ransomware, requiring more than just backups for data restoration.
- To enhance ransomware resilience, product managers must integrate recovery plans at every stage of product development.
- Key best practices include rapid system isolation, building alternative systems for failover, prioritizing secure backups, embedding incident response tools, training employees, and testing recovery plans.
Read Full Article
7 Likes
Securityaffairs
270

Image Credit: Securityaffairs
Security Affairs newsletter Round 524 by Pierluigi Paganini – INTERNATIONAL EDITION
- US Government officials targeted with texts and AI-generated deepfake voice messages impersonating senior U.S. officials
- New botnet HTTPBot targets gaming and tech industries with surgical attacks
- Google fixed a Chrome vulnerability that could lead to full account takeover
- Coinbase disclosed a data breach after an extortion attempt
Read Full Article
16 Likes
Securityaffairs
434
Image Credit: Securityaffairs
Experts found rogue devices, including hidden cellular radios, in Chinese-made power inverters used worldwide
- Chinese-made power inverters in US solar farm equipment were found to have 'kill switches', including hidden cellular radios, that could potentially allow Beijing to remotely disable power grids during a conflict.
- Experts discovered rogue devices, such as hidden cellular radios, in Chinese-made power inverters used globally, raising concerns about the possibility of remote power grid disruptions in critical infrastructure.
- US experts found undocumented communication devices like cellular radios in batteries from various Chinese suppliers, indicating a potential covert means to physically destroy power grids.
- US Representative August Pfluger emphasized the threat posed by such rogue devices, expressing the need to enhance efforts against Chinese interference in sensitive infrastructure to safeguard national security.
Read Full Article
26 Likes
Securityaffairs
151
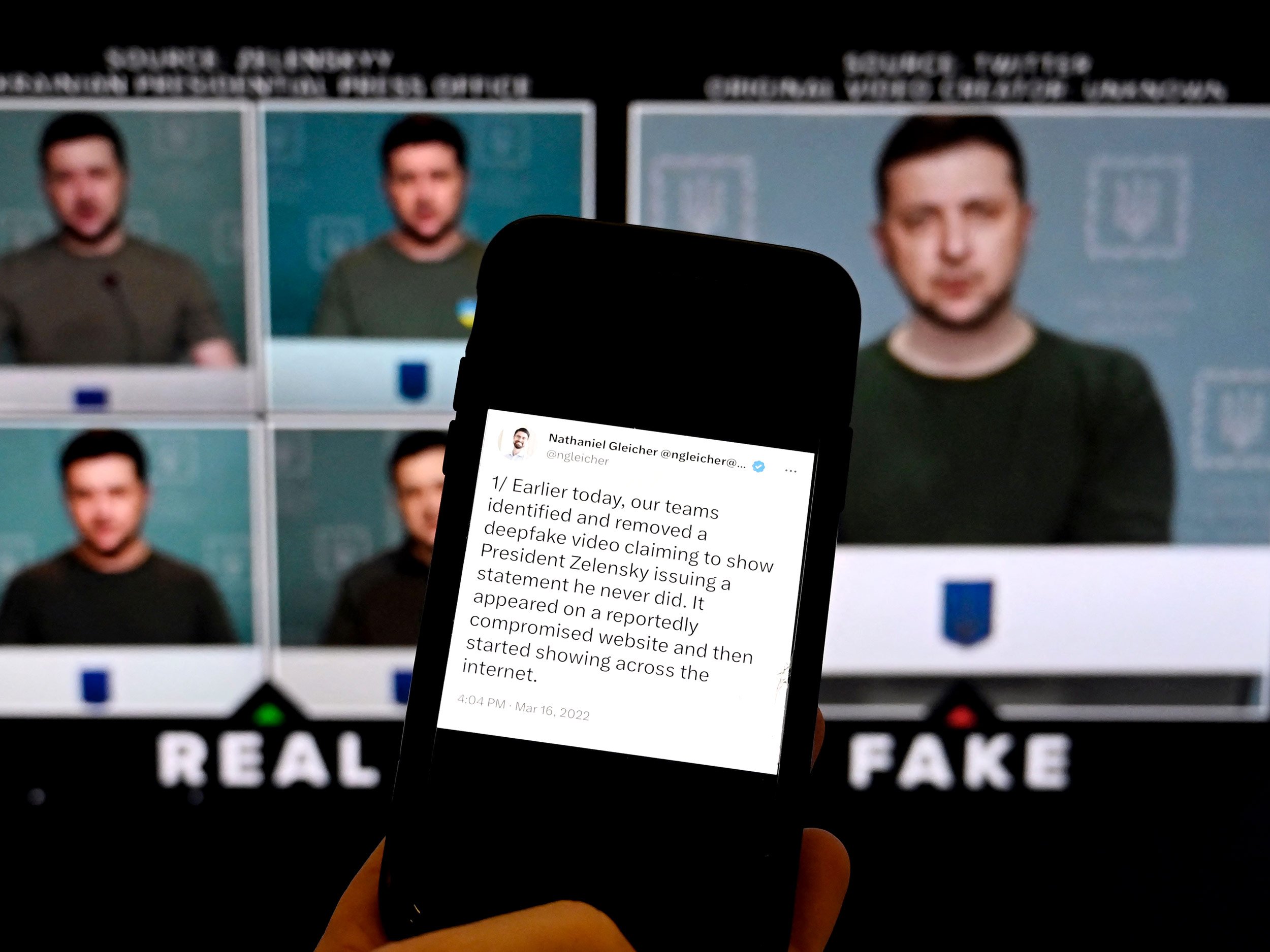
Image Credit: Securityaffairs
US Government officials targeted with texts and AI-generated deepfake voice messages impersonating senior U.S. officials
- The FBI warns ex-government officials of being targeted with deepfake texts and AI-generated voice messages impersonating senior U.S. officials.
- Threat actors have been using texts and AI voice messages since April 2025 to access personal accounts of officials and their contacts.
- Malicious links are sent to officials posing as messaging platform invites, allowing threat actors to extract data or funds through impersonation.
- To avoid falling for AI-powered scams, officials are advised to verify callers' identities, check for errors in messages, and avoid sharing sensitive information with unknown contacts.
Read Full Article
9 Likes
Securityaffairs
219

Image Credit: Securityaffairs
Shields up US retailers. Scattered Spider threat actors can target them
- Cybercrime group Scattered Spider, known for social engineering and extortion, is now targeting U.S. companies after focusing on UK retailers.
- UNC3944 (Scattered Spider) has hacked numerous organizations, including Twilio, LastPass, DoorDash, and Mailchimp, transitioning from telecoms to ransomware and broader sectors by 2023.
- Threat actors linked to Scattered Spider used DragonForce ransomware to target UK retailers, exploiting the large trove of PII and financial data held by retailers.
- Google experts suggest that UNC3944 targets sectors like Tech, Telecom, Finance, and Retail, focusing on large enterprises in English-speaking countries and beyond by using social engineering tactics for high-impact attacks.
Read Full Article
13 Likes
Hackingblogs
288

Image Credit: Hackingblogs
Metasploit 6.4.64 RCE Privilege Escalation Exploits 2025 And Critical Security Patch
- Metasploit 6.4.64 update brings new RCE exploits, privilege escalation, persistence, and information gathering modules.
- New modules include exploits in Car Rental System, WordPress SureTriggers, WP User Registration & Membership plugin, LINQPad, and POWERCOM UPSMON PRO.
- Post-exploitation capabilities enhanced with 32-bit support for injecting .NET assemblies in Metasploit.
- Key fixes include improvements in WordPress login process, SMB_to_ldap update, Yama ptrace_scope checker, and HTTP logging support for web crawler logs.
Read Full Article
17 Likes
Securityaffairs
343

Image Credit: Securityaffairs
U.S. CISA adds Google Chromium, DrayTek routers, and SAP NetWeaver flaws to its Known Exploited Vulnerabilities catalog
- U.S. CISA adds Google Chromium, DrayTek routers, and SAP NetWeaver flaws to its Known Exploited Vulnerabilities catalog.
- Critical vulnerabilities including OS command injection in DrayTek routers and insufficient policy enforcement in Google Chromium were added to the catalog.
- A flaw in SAP NetWeaver allows privileged users to upload malicious content, posing risks to system confidentiality, integrity, and availability.
- Federal agencies are required to fix the vulnerabilities by June 5, 2025, to protect their networks from potential attacks exploiting the identified flaws.
Read Full Article
20 Likes
Securityaffairs
146
Image Credit: Securityaffairs
Pwn2Own Berlin 2025 Day Two: researcher earned 150K hacking VMware ESXi
- Participants in Pwn2Own Berlin 2025 earned $435,000 by demonstrating zero-day exploits in products like SharePoint, ESXi, VirtualBox, RHEL, and Firefox.
- The total earnings for the competition reached $695,000 after the first day awarded $260,000 for 20 unique zero-days.
- Nguyen Hoang Thach of STARLabs SG used an integer overflow to hack VMware ESXi, earning $150,000 and 15 Master of Pwn points.
- Other significant earnings include Dinh Ho Anh Khoa exploiting Microsoft SharePoint for $100,000 and Edouard Bochin and Tao Yan exploiting Mozilla Firefox for $50,000.
Read Full Article
8 Likes
For uninterrupted reading, download the app