IOT News
Embedded
308

Help Shape the Future of Embedded Systems: Participate in the Embedded.com Reader Survey!
- Embedded.com is inviting engineers in the embedded space to participate in the AspenCore Embedded Markets Study to shape the content on the website.
- The survey covers various aspects such as engineers' roles, projects, technical preferences, technology trends, design tools, learning resources, and community involvement.
- Engineers' feedback will help tailor editorial coverage on Embedded.com to meet real needs and provide insights into global embedded design trends.
- Participants have the opportunity to influence the topics covered and improve the usefulness of the site for the entire community by taking the 15-20 minute survey.
Read Full Article
18 Likes
Medium
98

Image Credit: Medium
How to Start with IoT: A Beginner’s Guide from My Journey
- The beginner's guide to getting started with IoT covers choosing a platform, learning the basics, programming, cloud integration, and personal experiences.
- Starting with the ESP32 board is recommended due to its built-in Wi-Fi/Bluetooth features, simplifying wireless IoT for beginners.
- Using the Arduino IDE for programming ESP32 is suggested as it is beginner-friendly and well-supported.
- Progressing from basic electronics and small projects to connecting ESP32 to the cloud is key to building smart IoT devices.
Read Full Article
5 Likes
Securityaffairs
300
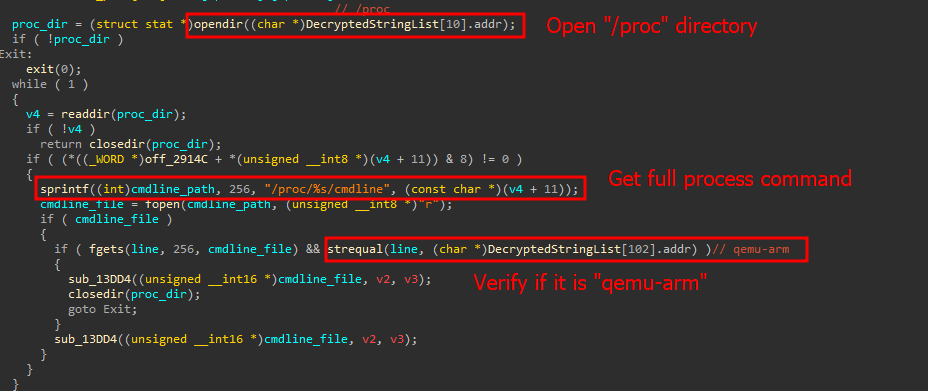
Image Credit: Securityaffairs
New Mirai botnet targets TBK DVRs by exploiting CVE-2024-3721
- A new variant of the Mirai botnet exploits CVE-2024-3721 to target DVR systems.
- The variant uses a command injection vulnerability in TBK DVR-4104 and DVR-4216 devices to execute malicious commands.
- This Mirai variant includes new features like RC4 string encryption and anti-virtual machine checks.
- Over 50,000 exposed DVRs have been found as potential targets in countries like China, India, Egypt, Ukraine, Russia, Turkey, and Brazil.
Read Full Article
18 Likes
VoIP
247

Image Credit: VoIP
Linxens & Dracula Innovate Battery-Free IoT with Smart Labels
- The partnership between Linxens and Dracula aims to develop battery-free smart labels for IoT devices to address environmental impact and move towards sustainability.
- By leveraging energy harvesting technologies like organic photovoltaic solutions and micro-energy storage, the collaboration aims to power devices using light and radio frequency energy.
- Collaboration with companies like Wiliot, Exeger, and EnOcean signifies broader efforts to create energy solutions for IoT devices, unlocking the potential of ambient energy across industry needs.
- Linxens' production of sustainable smart labels made from biodegradable materials and energy-harvesting techniques, in collaboration with Dracula, highlights the fusion of innovation and ecological responsibility in IoT development.
Read Full Article
14 Likes
Discover more
Securityaffairs
0

Image Credit: Securityaffairs
BadBox 2.0 botnet infects millions of IoT devices worldwide, FBI warns
- BadBox 2.0 malware infects millions of IoT devices globally, forming a botnet for cyber criminal activities, as warned by the FBI.
- FBI issues a Public Service Announcement (PSA) highlighting the use of the BADBOX 2.0 botnet by cybercriminals to exploit IoT devices, predominantly made in China.
- The malware gains unauthorized access to devices, targeting Android devices and compromising home networks to become part of the BADBOX 2.0 botnet for illicit purposes.
- FBI advises checking IoT devices for compromise signs, disconnecting suspicious ones, monitoring network traffic, avoiding unofficial app stores, and promptly patching vulnerabilities to mitigate risks.
Read Full Article
Like
Dev
23

Image Credit: Dev
Home Assistant: Measuring Sound and Vibration
- The article discusses integrating sound and vibration sensors with Home Assistant using ESPHome, focusing on the KY-037 and SW420 sensors.
- Hardware required includes an ESP8266 board, KY-037 sensor, SW420 sensor, and Dupont cables.
- Wiring configurations for KY-037 and SW420 sensors are detailed, including connections to ESP8266 board pins.
- ESPHome configuration for the KY-037 sensor involves custom C routines for analog output conversion and decibel measurement.
- For the SW420 vibration sensor, binary sensor configuration is implemented to measure vibration state.
- Flashing process using esphome-flasher and calibration steps for sound and vibration sensors are discussed in detail.
- The Home Assistant integration for both sensors is explained, with settings for configuring sensitivity and visualization.
- Error handling techniques for dealing with unavailable sensors, including adjusting sampling intervals, are mentioned.
- The article concludes by summarizing the key takeaways for integrating sound and vibration sensors effectively with Home Assistant.
Read Full Article
1 Like
Securelist
426
Image Credit: Securelist
Analysis of the latest Mirai wave exploiting TBK DVR devices with CVE-2024-3721
- The article discusses the exploitation of CVE-2024-3721 to deploy a Mirai bot on vulnerable DVR devices.
- CVE-2024-3721 enables execution of system commands on TBK DVRs via a specific POST request.
- The malicious POST request contains a shell script to download and execute an ARM32 binary.
- The Mirai bot variant targeting DVR devices includes features like RC4 encryption and anti-VM checks.
- RC4 key decryption is used to decrypt strings within the malware implant.
- The implant conducts checks to detect if it is running within a virtual machine environment.
- Infection statistics reveal that many infected DVR devices are located in countries like China, India, Egypt, and Ukraine.
- Over 50,000 vulnerable DVR devices have been identified online, indicating a significant attack surface.
- To mitigate such threats, updating vulnerable devices promptly and conducting factory resets for exposed devices is recommended.
- Kaspersky products detect the threat as HEUR:Backdoor.Linux.Mirai and HEUR:Backdoor.Linux.Gafgyt.
Read Full Article
25 Likes
Securelist
242

Image Credit: Securelist
IT threat evolution in Q1 2025. Non-mobile statistics
- In Q1 2025, Kaspersky products blocked over 629 million attacks, with 88 million unique links detected by Web Anti-Virus.
- File Anti-Virus blocked over 21 million malicious objects, and nearly 12,000 new ransomware variants were found.
- Phobos Aetor operation led to arrests of 8Base members for cyberattacks involving Phobos ransomware.
- Law enforcement efforts resulted in extraditing a suspected ransomware developer linked to LockBit.
- New vulnerabilities in Paragon Partition Manager were exploited for BYOVD attacks in Q1.
- Akira ransomware bypassed EDR by exploiting a webcam vulnerability and using Linux-based systems.
- HellCat utilized compromised Jira credentials for attacking companies like Ascom and Jaguar Land Rover.
- Ransomware group RansomHub remained a leader in adding new victims, followed by Akira and Clop.
- Kaspersky detected three new ransomware families and 11,733 new variants, a significant increase from the previous quarter.
- 315,701 unique users worldwide were attacked by miners in Q1 2025, with various countries facing such attacks.
Read Full Article
14 Likes
Semiengineering
405

Image Credit: Semiengineering
Multimodal AI For IoT Devices Requires A New Class Of MCU
- The rise of AI-driven IoT devices is outpacing the capabilities of existing microcontroller units (MCUs).
- Current 32-bit MCUs struggle to handle AI workloads effectively, leading to a fragmented ecosystem.
- Existing AI-enabled devices are often repurposed from other applications, not optimized for IoT's power requirements.
- Traditional AI MCUs have rigid architectures that compromise energy efficiency in IoT environments.
- To address these challenges, a new class of MCUs blending sensing and AI compute is necessary.
- Synaptics introduced the Astra SR-Series AI MCU platform for IoT, featuring a multi-gear architecture.
- The SR100 Series MCUs have three domains for different power levels: ULP Always-On, Efficiency, and Performance.
- The domains balance energy efficiency with AI processing capabilities, optimizing power consumption.
- The SR100 series employs intelligent gearing algorithms for context-aware AI computing, improving scalability and efficiency.
- Standardized development practices ensure compatibility with existing IoT ecosystems.
Read Full Article
24 Likes
Siliconangle
423
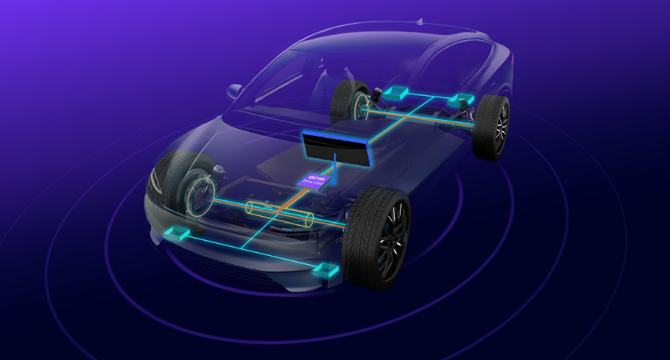
Image Credit: Siliconangle
Arm’s latest compute subsystem to accelerate automotive AI chip design by up to a year
- Arm Holdings Plc aims to speed up automotive chip development with a new design platform, potentially shortening time to market by up to 12 months.
- The new Arm Zena Compute Subsystems offer a standardized compute platform for building AI-powered cars faster, reducing development cycles.
- Zena CSS features Armv9-based Cortex-A720AE cores optimized for ADAS and infotainment, with enhanced security and communication capabilities.
- The platform allows for easier reuse of architectures and software across different vehicles, expected to streamline development and improve safety in intelligent features.
Read Full Article
25 Likes
Semiengineering
193

Image Credit: Semiengineering
Next Level Inductive Sensing For New Metallic, Waterproof And Robust HMI Touch Designs
- The need for advanced and improved human machine interfaces (HMIs) is increasing due to digitalization trends like Industry 4.0, IoT, and AIoT.
- Designers face challenges with liquid tolerance and sleek metallic designs using mechanical and capacitive sensors, prompting the use of inductive sensing.
- Inductive sensing offers opportunities for reliable touch solutions on metal surfaces and in wet environments and helps simplify designs, create attractive interfaces, and optimize costs.
- Inductive sensors enable the creation of new, robust touch HMI solutions, as depicted in Fig.1, facilitating advancements in touch technology.
Read Full Article
11 Likes
IEEE Spectrum
315

Image Credit: IEEE Spectrum
Disaster Awaits if We Don’t Secure IoT Now
- In 2015, Ukraine experienced widespread power outages due to a Russian cyberattack on critical infrastructure, signaling a decade of cyber threats on crucial systems. Attacks on infrastructures like a Kansas nuclear plant and the New York City subway have escalated concerns.
- The proliferation of IoT devices, especially Industrial IoT (IIoT) devices, poses a significant risk as the number of connected devices continues to grow exponentially. The potential impact of cyberattacks on IoT devices can extend beyond the devices themselves to cause physical-world damage to entire communities.
- Security for IoT devices is often overlooked due to their limited need for human interaction and non-sensitive information storage. However, cyberattacks on IoT devices can have severe consequences, highlighting the need for proactive security measures.
- To enhance the security of IoT devices, two key strategies are emphasized: basic cybersecurity hygiene and defense in depth. Basic cybersecurity practices include avoiding default passwords, regular software updates, and validating software integrity.
- The U.S. Government's Software Bill of Materials (SBOM) aims to provide transparency in software supply chains, aiding in identifying and addressing vulnerabilities in IoT device software. Having accurate SBOMs can enhance cybersecurity for both device suppliers and users.
- Defense in depth, a less known but crucial approach, focuses on layered security measures involving protection, detection, and remediation. Implementing a layered security model helps safeguard IoT devices against complex vulnerabilities and ensures resilience against cyberthreats.
- A vital component of IoT security is establishing a Root of Trust (RoT) to protect the device's firmware and ensure its integrity. RoT mechanisms, including hardware-based RoTs and secure boot processes, play a key role in safeguarding IoT devices from malicious attacks.
- Remote Attestation, facilitated by hardware components like the Trusted Platform Module (TPM), enhances the security of IoT devices by collecting and reporting evidence of device integrity during startup. This process helps validate the trustworthiness of IoT devices through cryptographic signatures.
- In case of anomalies, remediation actions for IoT devices may involve resetting the device, refreshing software, or utilizing authenticated watchdog timers to ensure device health. Practices like power-cycling and leveraging trusted components aid in mitigating security breaches and ensuring device resilience.
- As IoT cybersecurity measures evolve and become more accessible, both device designers and system integrators need to prioritize implementing robust security mechanisms to protect against cyber threats. The incorporation of high-security mechanisms and reliable software stacks enhances the overall security posture of IoT devices.
Read Full Article
19 Likes
Dev
321

Image Credit: Dev
Designing Safe Charging Algorithms for Lithium Batteries in Embedded Systems
- Lithium-ion batteries are essential for powering embedded systems but require safe and efficient charging algorithms to prevent degradation and ensure user safety.
- Key phases of a safe charging algorithm include Pre-Charge, Constant Current (CC) Phase, Constant Voltage (CV) Phase, and Termination, with temperature monitoring throughout.
- Implementing the algorithm in embedded firmware involves ADC Sampling, State Machine for charging states, Timers and Timeouts, Safety Cutoffs, and Communication Interface for smart batteries.
- Choosing the right charge controller is crucial, with options such as MCU Firmware, Battery Management ICs, or a Hybrid Approach, while following battery cell manufacturer specifications is essential for safety and performance.
Read Full Article
19 Likes
Siliconangle
135

Image Credit: Siliconangle
Meta and Anduril partner to develop wearables for the US military
- Meta Platforms Inc. and Anduril Industries Inc. are collaborating to develop wearable devices for the U.S. military.
- Anduril, a defense technology startup, received a $14 billion valuation in its recent funding round.
- The partnership aims to create a line of wearables called EagleEye, including helmets, glasses, and other devices with virtual reality and mixed reality features.
- The devices are designed to enhance hearing and vision, enable remote control of autonomous systems, and will incorporate advanced technologies like Meta's Llama algorithms and Anduril's Lattice OS and networking engine.
Read Full Article
8 Likes
Embedded
439

How to Optimize Energy Consumption in IoT Devices
- Optimizing power consumption in IoT systems is crucial, especially for devices in remote locations with limited power sources such as batteries.
- Efficient energy management solutions are necessary for prolonged device operation.
- Adopting optimized computing architectures and advanced hardware and software strategies is essential to reduce power consumption without compromising performance.
- Techniques like intelligent power management and low-power communication protocols help maximize energy efficiency.
- Careful component selection and efficient processing algorithms can extend device operational life.
- Energy optimization is vital in industrial, home automation, and smart city applications where reliability and sustainability are critical.
- Choosing a power-efficient processor architecture like Arm Cortex-M or RISC-V is the first step in designing energy-efficient IoT systems.
- Dynamic energy management techniques like dynamic voltage and frequency scaling (DVFS) are crucial to reduce device consumption.
- Low-power modes such as deep sleep and light sleep significantly extend device operational life.
- Implementing software strategies like optimizing interrupt handling and minimizing radio-frequency communication is important to reduce energy consumption.
Read Full Article
26 Likes
For uninterrupted reading, download the app