IOT News
Ubuntu
61

Image Credit: Ubuntu
What are our partners building for device makers? Explore the highlights from Ubuntu IoT Day Singapore
- Ubuntu hosted its first IoT Day event in Southeast Asia and Singapore, with over 150 participants discussing the future of IoT.
- Presentations from industry leaders like ARM, Intel, Qualcomm, and others focused on AI deployment challenges, robotics trends, and regulatory compliance.
- Challenges of deploying AI at the edge were discussed, with Qualcomm introducing the AI Hub for optimized models and Intel offering Verified Reference Blueprints for streamlined deployment.
- MediaTek showcased their Genio platform using Snap packages for secure AI application delivery, aiding OEMs and device manufacturers with updatable AI capabilities.
- Silicon and ODMs are transitioning to a software-first approach, as highlighted by companies like ARM abstracting hardware complexities with middleware like Kleidi.
- Participants explored topics on secure deployments and compliance, including discussions on the European Cyber Resilience Act and tools like DeviceON by Advantech for remote device management.
- Canonical delved into the implications of the CRA for device manufacturers, emphasizing compliance and security maintenance, while Advantech highlighted Ubuntu Pro for enhanced security.
- The event aimed to expand technical knowledge and foster professional networks among participants, with plans to continue hosting IoT days in Southeast Asia.
Read Full Article
3 Likes
Hackaday
282

Image Credit: Hackaday
BhangmeterV2 Answers The Question “Has a Nuke Gone Off?”
- A BhangmeterV2, a nuclear event detector called HSN-1000L, has been built by a user named Bigcrimping.
- The device outputs data publicly at hasanukegoneoff.com to check for nuclear explosions.
- The HSN-1000L remains available and is used for detecting gamma ray pulses preceding a nuclear event.
- The device triggers an automatic shutdown to protect electronics in case of a nuclear exchange.
- The HSN-1000L is connected to a Raspberry Pi Pico 2 W to create the BhangmeterV2.
- The BhangmeterV2 logs the time of the nuclear event detector's signal change and sends the data to the cloud.
- It can only detect nuclear events within line-of-sight, making it sensitive to nearby nuclear events.
- Future versions may include additional detection methods like a 3D-printed neutrino detector.
- If surviving a blast, users may need a radiation detector like a gamma-ray spectrometer for fallout analysis.
- The relevance of this project in the modern world hints at a cold-war vintage feel resurfacing.
- The project reflects the concerning state of affairs, and contributions from users are encouraged for similar projects.
Read Full Article
16 Likes
Embedded
371

Countering GNSS Spoofing: Innovations for IoT Security
- The integration of IoT and GNSS technology is pivotal for various sectors such as smart cities, autonomous vehicles, agriculture, and supply chain.
- Challenges arise due to the increasing risks associated with GNSS disruption by spoofing and jamming attacks.
- Spoofing involves generating false GNSS signals to deceive receivers, impacting timing and positioning data.
- Jamming attacks overpower GNSS receivers with strong signals, easier to detect but still disruptive.
- Spoofing attacks, historically limited to military, are now more accessible with low-cost technology.
- Commercial sectors like aviation and shipping are increasingly targeted by spoofing attacks, posing safety risks.
- Anti-spoofing technologies focus on signal anomaly detection, cryptographic authentication, and redundancy.
- Mitigation techniques include Receiver Autonomous Integrity Monitoring (RAIM) and signal encryption.
- Ongoing challenges include cost, scalability of anti-spoofing solutions, and the evolving nature of attacks.
- Developments like the Galileo Smart Traceability Anti-spoofing project and AI integration are addressing the evolving threat landscape.
Read Full Article
22 Likes
Embedded
393

Embedded Web Server – A Guide for Modern Connected Devices
- An embedded web server is a software component integrated into a hardware device allowing user interaction through a web browser in a constrained environment.
- It enables real-time control, monitoring, and configuration over a standard network, simplifying management of devices like routers, smart home systems, industrial controllers, and IoT nodes.
- Hardware setup for embedded web servers includes Ethernet for stable communication, Wi-Fi for wireless connectivity, and Cellular for remote or mobile deployments.
- These interfaces provide connectivity options for the embedded web server to communicate over the Internet or local networks.
- The software stack for embedded web servers follows a four-layer model: Driver Layer, TCP/IP Layer, Library Layer, and Application Layer.
- Understanding this layered approach is crucial for optimizing performance, scalability, and maintainability of embedded web server implementations.
- Popular solutions for embedded web servers include Zephyr, lwIP, and Mongoose Web Server, each offering different functionalities and support for various protocols.
- Choosing the right embedded web server solution is essential for the success of any connected device project, impacting hardware options, software architecture, and available tools.
- With the increasing demand for smart and connected devices, mastering the implementation of an embedded web server has become more crucial than ever.
- The article provides a comprehensive guide for deploying modern embedded web servers for connected devices.
- Embedded web servers simplify device management and enhance user experience by providing a user-friendly interface accessible through a web browser.
- Understanding hardware setups and software architecture is key to developing efficient embedded web server solutions.
- Various connectivity options like Ethernet, Wi-Fi, and Cellular cater to different deployment scenarios, ensuring reliable and versatile communication.
- The embedded web server software stack operates through distinct layers, from hardware interaction to application-specific logic and UI elements.
- Multiple solutions, including Zephyr, lwIP, and Mongoose Web Server, offer developers different levels of support and functionality for embedded web server development.
- Choosing the appropriate embedded web server solution is crucial for project success, given the importance of hardware compatibility, software architecture, and tool availability.
Read Full Article
23 Likes
Discover more
TechBullion
4
Image Credit: TechBullion
Latent AI Launches Groundbreaking “Latent Agent” Platform to Eliminate “Model-to-Hardware” Guessing Game for Devices
- Major enterprises face challenges deploying AI models on edge devices due to compatibility and performance issues related to memory, computing capability, latency, and power usage.
- The launch of Latent Agent by Latent AI aims to eliminate the 'model-to-hardware' guessing game and accelerate AI deployment on edge devices.
- Latent Agent empowers developers to describe deployment needs in plain English, providing optimized AI model recommendations based on real-world performance data.
- Developers can streamline the process using Latent Agent's natural language interface in Visual Studio (VS) Code, simplifying AI model optimization.
- The platform utilizes over 200,000 hours of real-world data to make precise model recommendations for edge devices, reducing deployment times significantly.
- Latent Agent's self-healing models automatically detect and resolve performance issues, ensuring uninterrupted productivity in enterprise environments.
- LEIP, Latent AI's primary edge AI modeling solution, has already shown success in industries like the United States Navy Task Force and the Future of Sports (FSP).
- Several enterprises, including Gartner Peer Insights, have benefited from Latent AI's solutions by reducing model deployment times, enhancing operations, and transforming sports venues.
- Latent Agent revolutionizes AI deployment by offering a future where scaling AI across edge devices is faster, efficient, and more reliable.
- With Latent Agent, the process of deploying AI models on edge devices becomes more straightforward and efficient, marking a significant advancement in AI technology.
Read Full Article
Like
Siliconangle
106
Image Credit: Siliconangle
With $27M in funding, Fleet wants to bring more freedom to enterprise device management
- Fleet Inc. secures $27 million in Series B funding to enhance enterprise device management.
- The funding round was led by Ten Eleven Ventures with participation from CRV, Open Core Ventures, and other investors.
- Fleet offers an open-source device management platform for companies to secure their computing devices.
- The platform provides transparency, extensibility, and repeatability compared to proprietary software.
- Fleet aims to give organizations control over device management for compliance with regulations like PCI and FedRAMP.
- It offers both hosted and on-premises deployment options.
- Netflix, Stripe, Fastly, Uber, and Reddit are among the well-known enterprises using Fleet.
- Fleet's platform supports various devices like iPhones, Android phones, laptops, and even data centers.
- Customers praise Fleet for providing flexibility and avoiding forced cloud migrations.
- The company's rapid growth is attributed to its channel partners and open-source approach.
- Fleet CEO emphasizes the company's dedication to open hosting options.
- Ten Eleven Ventures Partner endorses Fleet for its comprehensive device management capabilities.
- Fleet plans to maintain its open approach and customizable hosting solutions.
- The company has been seeing significant adoption for its device management platform.
- Flexible hosting options are generating increased interest in web searches.
- Fleet's platform is designed to cater to a wide range of operating systems and devices.
- The company's mission is to provide free, relevant, and in-depth content to the community.
Read Full Article
6 Likes
Securityaffairs
106
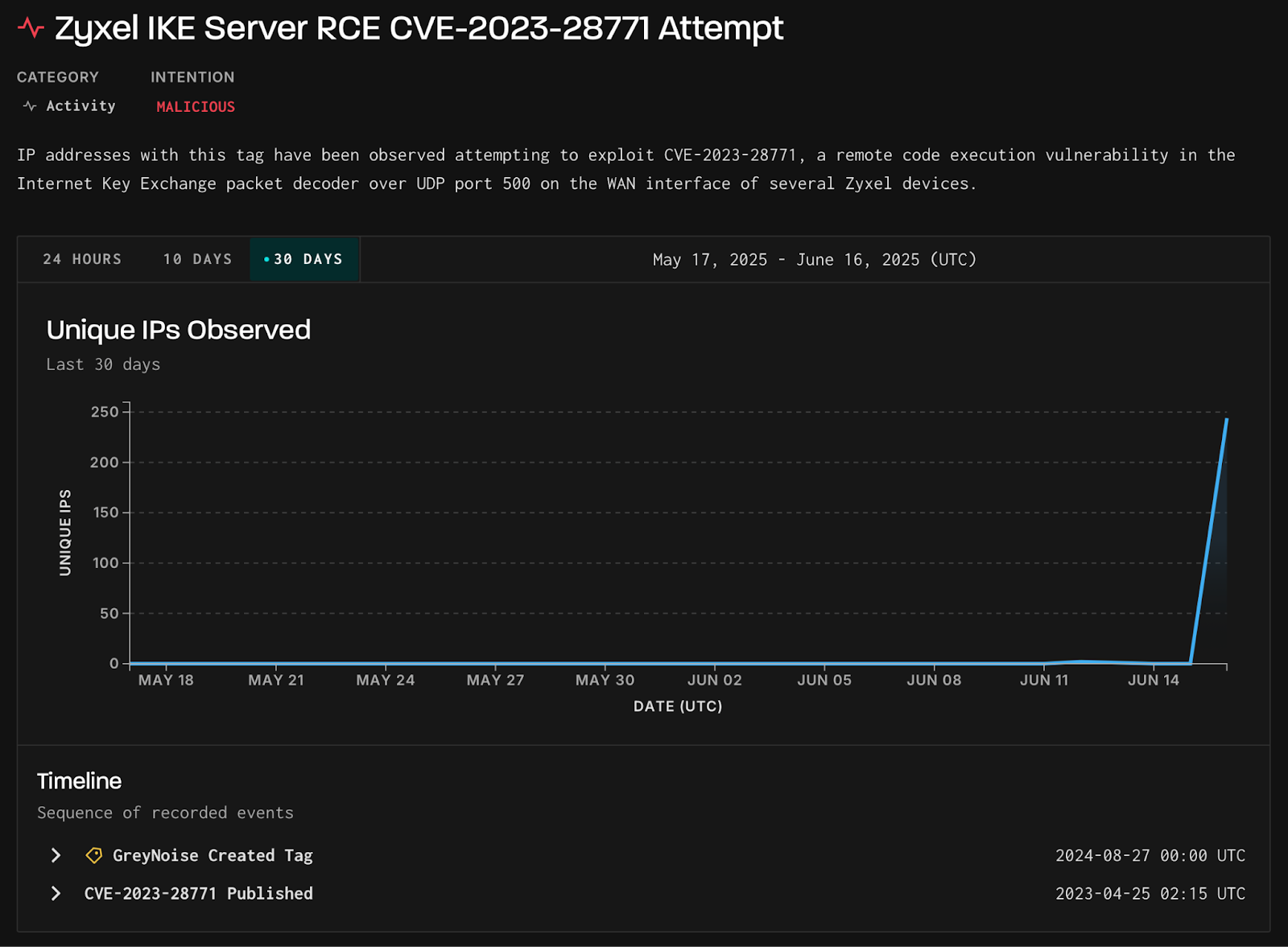
Image Credit: Securityaffairs
Attackers target Zyxel RCE vulnerability CVE-2023-28771
- Attackers are actively targeting the Zyxel RCE vulnerability CVE-2023-28771, according to GreyNoise researchers.
- On June 16, a surge in exploit attempts against the Zyxel IKE decoders vulnerability was observed, with 244 unique IPs involved.
- The main targets of the attack were the U.S., U.K., Spain, Germany, and India.
- All 244 IP addresses related to the exploitation attempts were traced back to Verizon Business in the U.S., but the use of UDP means the IPs could be spoofed.
- The exploit attempts were linked to Mirai botnet variants, as confirmed by VirusTotal.
- GreyNoise recommends blocking the identified malicious IPs, verifying device patches, monitoring for post-exploitation activities, and limiting exposure on IKE/UDP port 500.
- In April 2023, Zyxel addressed the CVE-2023-28771 vulnerability in its firewall devices and urged customers to install patches to mitigate the risk.
- The U.S. CISA added the vulnerability to its Known Exploited Vulnerability to Catalog after observing active exploitation.
Read Full Article
6 Likes
Embedded
39

CrowPanel ESP32: a Versatile Solution for IoT Projects – Display Management
- The article delves into programming the 1.28-inch CrowPanel ESP32 display for IoT projects using MicroPython, highlighting its features and applications.
- The display offers a resolution of 240×240 pixels, wireless connectivity, IPS technology, and capacitive touch sensing, suitable for interactive graphic displays in IoT applications.
- Programming can be done using MicroPython, Arduino IDE or other platforms, with specific libraries available for managing RTC, LCD, and I/O expansion.
- A simple example demonstrates interfacing a button with the LCD screen to display different content based on button press in MicroPython.
- Another example focuses on creating an analog clock interface on the display using basic functions for drawing circles and arranging hour numbers.
- The article emphasizes the ease of programming the CrowPanel ESP32, its versatility, advanced features, and compatibility with various languages and libraries, making it suitable for IoT projects.
- Overall, the CrowPanel ESP32 Display 1.28 inch stands out as a versatile solution for embedded applications, IoT dashboards, and industrial automation systems.
Read Full Article
2 Likes
Pymnts
412

Image Credit: Pymnts
Samsung Health Hub Aims to Simplify Doctor-Patient Communication
- Samsung is working on a health hub to facilitate communication between patients and their doctors, allowing patients to share health data with healthcare providers.
- The project aims to help patients remember guidance from healthcare appointments and promote better adherence to prescribed goals.
- Samsung Health executive Dr. Hon Pak highlighted the need to streamline health data and create a more cohesive user experience.
- The new health hub is still in development, but Samsung is introducing health-related features for its smartwatches in the meantime.
- The One UI 8 software update for Samsung smartwatches includes tools for measuring antioxidant levels, vascular load, a running coach, and enhanced sleep management features.
- Samsung emphasized the importance of incremental improvements in health habits and how the new features aim to support sleep, heart health, fitness, and nutrition.
- In the realm of tech and healthcare, digital twins are increasingly used in pharmaceutical trials, particularly in fields like neuroscience.
- Digital twin technology has the potential to reduce trial durations, decrease reliance on placebo groups, and expedite the development of life-saving drugs.
- The use of digital twins in healthcare can address disparities in tools and capabilities among doctors, leading to more equitable healthcare outcomes.
- There is a need for better infrastructure, medical record utilization, and doctor education to ensure that healthcare tools are understandable and trustworthy.
Read Full Article
24 Likes
Dev
804

Image Credit: Dev
What Is Edge Computing and Why It Matters
- Edge computing brings data processing closer to where it's needed, bypassing distant servers.
- It involves processing data locally on edge devices like sensors or local servers for faster and more secure systems.
- Key benefits include reduced latency, bandwidth usage, improved security, reliability, scalability, and flexibility.
- Real-world applications include IoT, autonomous vehicles, healthcare monitoring, AR/VR, and retail/surveillance.
- Challenges include complexity, security risks, limited resources, and cloud integration.
- Edge computing complements cloud technology and is crucial for instant insights and efficient operations in the future tech landscape.
Read Full Article
23 Likes
Pymnts
13

Image Credit: Pymnts
More Than Half of Gen Z Consumers Would Switch Retailers for Self-Checkout
- The self-service commerce landscape is evolving with the rise of AI and IoT technologies, providing frictionless experiences and new opportunities for businesses.
- Advanced self-service solutions are becoming essential in modern commerce, addressing previous limitations and driving digital transformation.
- Companies like Cantaloupe offer a range of self-service solutions, including micro-payment processing, mobile ordering, and connected point-of-sale systems.
- AI and IoT networks have enabled innovative self-service technologies that enhance consumer experiences and provide operational insights.
- Key data points show the growth and potential of self-service commerce, with projections indicating a doubling of self-checkout deployments by 2030.
- More than half of Generation Z consumers are willing to switch retailers for checkout-free alternatives.
- Cashless transactions are becoming increasingly common in vending machines, with cashless payments showing higher average values.
- Future self-service commerce will expand into new physical spaces, deliver personalized experiences through AI, and optimize operations using real-time data.
- Technologies like computer vision and IoT sensors will drive efficiency and reduce shrinkage in unattended retail operations.
- Self-service installations are expected to evolve into smart commerce nodes that predict consumer needs and offer convenient purchase options.
- The transformation of self-service commerce signals a move towards 'boundaryless commerce'.
- Overall, AI and IoT technologies are reshaping retail and empowering businesses to provide seamless and efficient self-service experiences.
Read Full Article
Like
Dev
285

Image Credit: Dev
How I Monitored My Lithium Battery Pack Using Python and a Raspberry Pi
- Monitoring lithium-ion battery packs is crucial for safety, health, and efficiency in various applications.
- A detailed guide on setting up a battery monitoring system using Python on a Raspberry Pi is provided.
- Components like Raspberry Pi 4, INA219 current sensor, and DS18B20 temperature sensor are used in the project.
- The article covers wiring instructions for INA219 and DS18B20 to the Raspberry Pi.
- Software setup involves installing necessary packages, enabling interfaces, and running a Python script for monitoring.
- Data visualization and analysis using Pandas and Matplotlib help track battery metrics over time.
- Building a web dashboard with Flask for remote data access is also outlined as an optional step.
- The article emphasizes accuracy, calibration, safety measures, and potential advanced extensions for the monitoring system.
- Lessons learned include the importance of sampling rate, cell balancing awareness, data normalization, and thermally-aware design.
- Monitoring lithium batteries with Python and Pi provides valuable insights for optimizing device performance and longevity.
Read Full Article
16 Likes
Securityaffairs
338

Image Credit: Securityaffairs
Exposed eyes: 40,000 security cameras vulnerable to remote hacking
- Over 40,000 internet-exposed security cameras worldwide are vulnerable to remote hacking, posing serious privacy and security risks.
- Bitsight alerts about the vulnerability of security cameras to remote hacking due to unsecured HTTP or RTSP access, enabling live feed streaming that can be easily targeted for spying, cyberattacks, and stalking.
- Identification of HTTP-based security cameras is complex due to diverse models; researchers developed a fingerprinting method using favicon hashes, HTTP headers, and HTML titles.
- Many HTTP-based cameras allow unauthenticated access to live footage through specific URIs like /out.jpg, which poses a significant privacy risk by bypassing authentication.
- RTSP-based cameras lack clear identifiers, making them harder to fingerprint; researchers analyzed RTSP Server headers and common URIs like /live.sdp to capture screenshots.
- Bitsight's internet scan revealed over 40,000 exposed cameras, mainly in the U.S., with the Telecommunications sector having the highest exposure due to extensive consumer use.
- The risk of privacy breaches and security threats extends to various sectors, including technology, media, utilities, business services, and education, as poorly secured cameras provide access to sensitive areas.
- Exposed cameras can capture live footage from homes, offices, retail spaces, factories, and critical areas, enabling spying, robbery planning, and data theft due to insecure setups.
- Bitsight warns of cybercriminals searching for exposed cameras on dark web forums and recommends users to update devices, change default passwords, disable unnecessary remote access, secure connections, and monitor unusual logins.
- The report underlines the significant exposure of devices in the Telecommunications sector, emphasizing the widespread availability of cameras for personal and professional use.
Read Full Article
20 Likes
Mit
35
Image Credit: Mit
Photonic processor could streamline 6G wireless signal processing
- MIT researchers have developed a novel AI hardware accelerator for wireless signal processing, using an optical processor that performs machine-learning computations at the speed of light, classifying wireless signals in nanoseconds.
- The photonic chip is significantly faster and more energy-efficient than digital alternatives, making it scalable and flexible for various high-performance computing applications, including future 6G wireless technologies like cognitive radios.
- This new hardware accelerator enables edge devices to perform real-time deep-learning computations, potentially revolutionizing applications like autonomous vehicles' reactions to environmental changes or continuous monitoring by smart pacemakers.
- The optical neural network architecture, named MAFT-ONN, encodes signal data and conducts all machine-learning operations in the frequency domain, achieving high efficiency and scalability for signal processing.
- MAFT-ONN can fit 10,000 neurons on a single device, performing necessary multiplications efficiently through photoelectric multiplication and achieving signal classification with high accuracy in nanoseconds.
- The researchers aim to enhance MAFT-ONN further by implementing multiplexing schemes for increased computations, expanding into complex deep learning architectures, and optimizing performance for future applications.
Read Full Article
2 Likes
Securityaffairs
106
Image Credit: Securityaffairs
Mirai botnets exploit Wazuh RCE, Akamai warned
- Akamai researchers warned that multiple Mirai botnets are exploiting the critical remote code execution vulnerability CVE-2025-24016 in Wazuh servers.
- The vulnerability allows for remote code execution on Wazuh servers, and active exploitation of the flaw has been observed via DAPI request abuse.
- Two Mirai botnet variants named 'Resbot' have been exploiting this bug since March 2025, utilizing Italian domain names and targeting IoT devices.
- Indicators of compromise and details on the exploitation of the Wazuh servers by Mirai botnets have been shared by Akamai researchers.
Read Full Article
5 Likes
For uninterrupted reading, download the app