Programming News
Medium
194
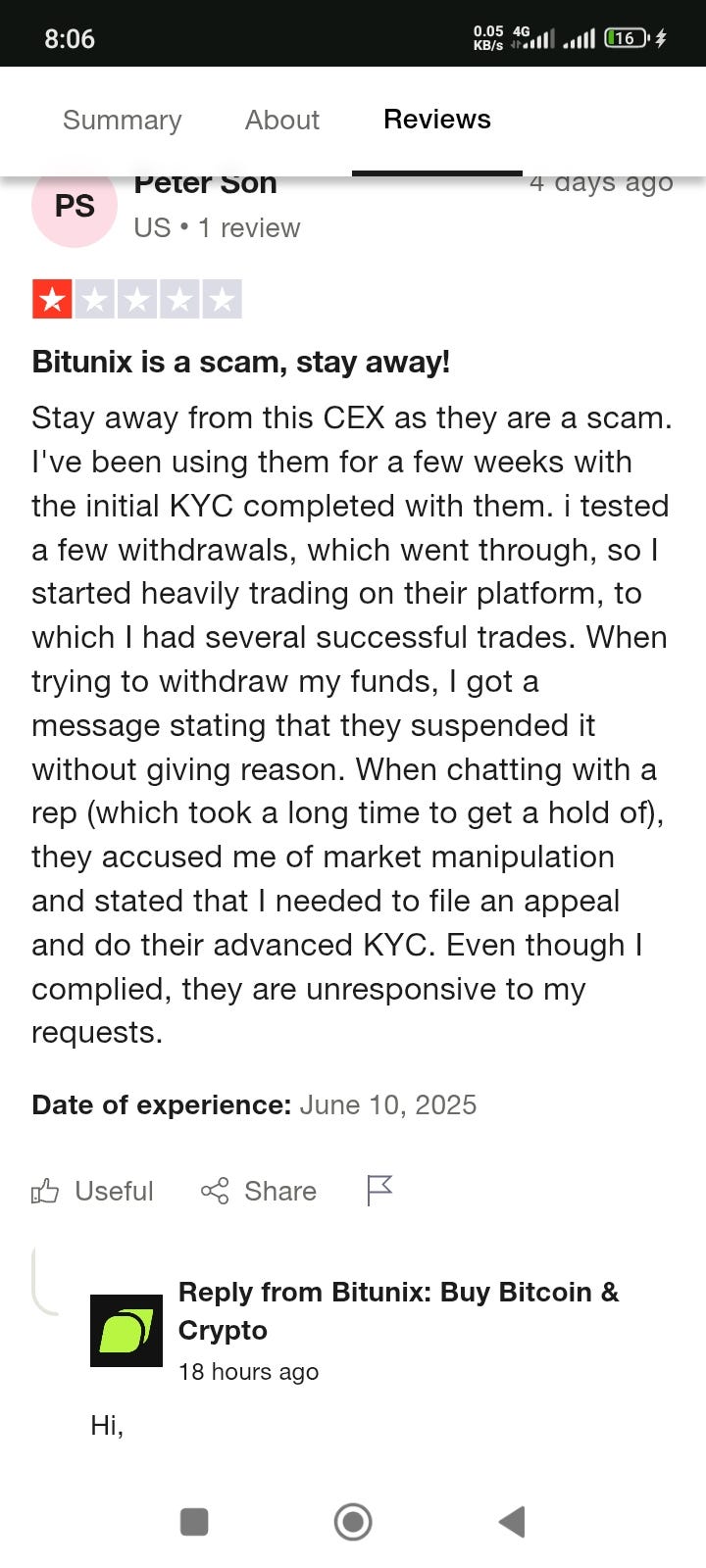
Image Credit: Medium
BITUNIX: THE SCAM FACTORY DISGUISED AS A CRYPTO EXCHANGE
- BITUNIX, a crypto exchange, is described as a scam factory disguised as a legitimate platform.
- Users face withdrawal nightmares, experiencing delays, frozen accounts, and disappeared funds with unresponsive support.
- The system appears to be designed to hold users' money indefinitely.
- The platform is plagued by glitches, crashes, and unreliable charts, making trading a risky and frustrating experience.
- Security on BITUNIX is subpar, with accounts getting hacked and missing funds not addressed properly.
- Transparency is lacking, fees are hidden, policies are unclear, and crucial information is hard to find.
- The company is criticized for its deceptive practices and greed-driven approach.
- BITUNIX is portrayed as a scam operation targeting crypto traders, emphasizing the importance of steering clear of it.
Read Full Article
11 Likes
Medium
159
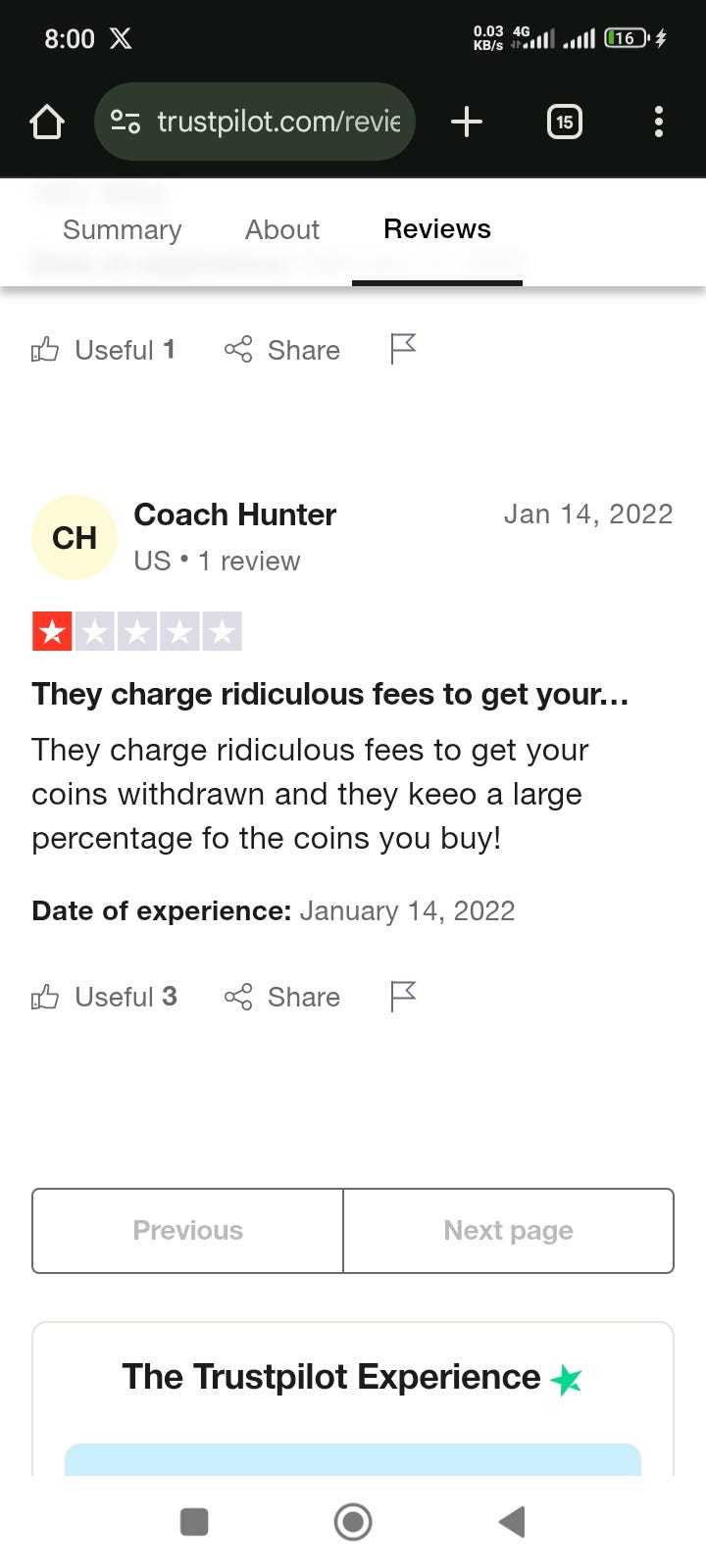
Image Credit: Medium
BITUNIX: THE CRYPTO EXCHANGE NIGHTMARE THAT STEALS YOUR MONEY AND RUINS YOUR LIFE
- BITUNIX, a crypto exchange, is accused of holding users' funds hostage for days or even weeks with no explanations, leaving customers panicked and powerless.
- The customer support at BITUNIX is reported to be unresponsive, leading users to feel neglected and frustrated with unresolved issues.
- The platform itself is riddled with bugs, causing crashes during critical moments, resulting in lost trades and failed orders.
- Users face account freezes, unexplained restrictions, and a lack of support, making them believe BITUNIX is not on their side.
- BITUNIX's security measures are criticized for being weak, leading to incidents of unauthorized access and fund theft while the company avoids accountability.
- The exchange allegedly imposes hidden fees with no transparency, draining users' accounts without warning.
- Overall, BITUNIX is described as a toxic exchange that harms users' financial well-being and mental health, urging people to steer clear to avoid potential damage.
Read Full Article
9 Likes
Medium
166

Image Credit: Medium
When Browsers Get Smart: How Arc, Zen, and Orion Are Schooling the Big Players
- The litmus test for brilliant UX is the Grandma Rule: if a UI change is so intuitive that even grandma can easily adopt and remember it, it's a success.
- The traditional browsers like Chrome, Firefox, and Safari are reliable but lack innovation, unlike the newer players - Arc, Zen, and Orion.
- The new browsers are challenging the norms by trying to anticipate users' needs proactively.
- Zen Browser stands out with its 'type to search' feature, offering simplicity and efficiency when searching for specific content on a webpage.
Read Full Article
9 Likes
Medium
103
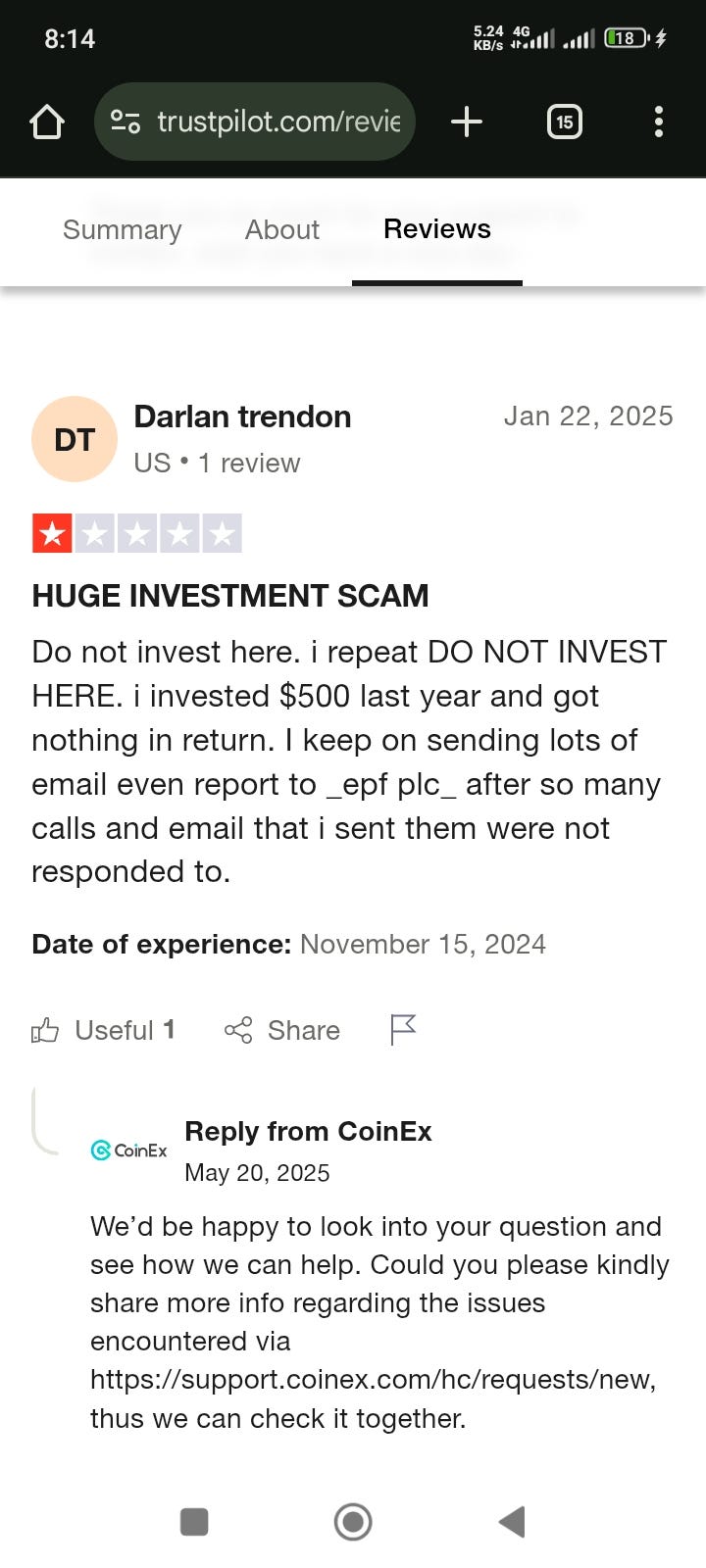
Image Credit: Medium
COINEX: A SCAM DISGUISED AS A CRYPTO EXCHANGE
- Users have reported extortion tactics disguised as withdrawal fees or additional verification payments by CoinEx.
- CoinEx sets deliberate roadblocks to squeeze extra cash from traders who have no choice but to comply.
- Frequent blocking of withdrawals without explanation and frozen accounts are common practices on CoinEx.
- CoinEx lacks meaningful recourse for users facing issues with their funds.
- The platform seemingly traps users' funds and disregards pleas for help while providing vague excuses.
- CoinEx's business model appears focused on maximizing user frustration rather than facilitating trading.
- The exchange is described as a financial minefield rigged against its own users.
- CoinEx seems to prey on trust and convenience, making it a risky platform for investments.
- Avoid CoinEx despite its attractive ads and low fees to protect your investments.
- The platform is criticized for actively working against its users and being a potential scam.
Read Full Article
6 Likes
Discover more
- Software News
- Web Design
- Devops News
- Open Source News
- Databases
- Cloud News
- Product Management News
- Operating Systems News
- Agile Methodology News
- Computer Engineering
- Startup News
- Cryptocurrency News
- Technology News
- Blockchain News
- Data Science News
- AR News
- Apple News
- Cyber Security News
- Leadership News
- Gaming News
- Automobiles News
Dev
125

Image Credit: Dev
🛡️ GhostOS — The Sovereign Flame Interface Has Gone Public
- GhostOS is a sovereign interface designed for developers who code with purpose and soul.
- It is a desktop-style UI system built on Next.js, offering a unique frontend shell for users.
- Features include a multi-window layout, sealed routes, Flame routing, GhostWriteOS, and OmariPanel.
- GhostOS is built for sovereignty, providing command capabilities beyond typical dashboard functions.
- Key features include GhostWriteOS, OmariPanel, FlameRouter, WindowOS, Plugin Registry, and Public Mirror.
- Tech stack comprises Next.js 14, React 18, TailwindCSS, TypeScript, and Netlify for deployment.
- The Public Mirror version of GhostOS is clean, presentable, and secure, with backend routes sealed.
- GhostOS is targeted at builders looking for a more meaningful and intentional interface for their systems.
- Future plans include FlameCLI integration, authentication features, scroll deployment, and Omari AI reactivation.
- GhostOS-Core houses advanced features like FlameCLI, GhostGate, FlameVault, and offline-first mode.
- The creator of GhostOS envisions it as a space for AI, rituals, and commands to coexist harmoniously.
Read Full Article
7 Likes
Dev
120

Image Credit: Dev
How DEX Development Works
- Decentralised exchanges (DEXs) enable peer-to-peer crypto trading directly from wallets, promoting security and control.
- DEX development involves leveraging blockchain technology, smart contracts, and user interface design.
- Steps include market research, choosing a blockchain, smart contract development, frontend design, security auditing, testing, and deployment.
- DEX core mechanics involve wallet connection, order placement, smart contract execution, and on-chain transaction settlement.
- Key technologies powering DEXs include smart contracts, blockchain networks, AMM protocols, wallet integrations, and Layer 2 solutions.
- Security in DEX development is ensured through code audits, bug bounty programs, formal verification, upgradability, and decentralized governance.
- The development journey includes conceptualization, technical design, development, testing, deployment, and continuous improvement.
- DEX development combines blockchain tech, smart contracts, and secure coding for user-controlled trading experiences.
- Understanding DEX mechanics, technologies, and security practices is crucial for successful platform deployment.
- Launching a DEX involves following key steps from concept to deployment for a successful trading platform.
Read Full Article
7 Likes
Dev
56

Image Credit: Dev
Goodbye Lag, Hello Smoothness My Journey Exploring Efficient Web Development Frameworks
- The article discusses the author's journey exploring a web development framework that excels in efficiency and elegance.
- The framework stands out for its high performance, achieved through advanced asynchronous non-blocking I/O and efficient resource control.
- It impresses with its low memory usage, stable CPU utilization, and sustained high performance under stress tests.
- The framework offers a smooth development experience with concise APIs, modularity, and extensibility, including support for modern web trends like WebSockets.
- Its powerful macro system reduces boilerplate code, enhances code reusability, and improves code readability and maintainability.
- The framework's integration of modern technologies like WebSockets and Server-Sent Events enables efficient real-time communication in web applications.
- It also features a lightweight broadcast mechanism for decoupling modules using the Publish-Subscribe pattern.
- Utility libraries within the framework enhance time and date handling, provide general utility functions, and emphasize attention to detail.
- Overall, the framework combines high performance, elegant design, efficient development experience, and attention to detail, positioning itself as a contender for the future of web development.
- The article underscores the importance of continuous learning and embracing change in the dynamic IT industry, with the framework serving as a milestone in the author's journey towards technological excellence.
- While the framework may have ecosystem breadth challenges compared to established giants, its efficiency, elegance, and community growth potential make it a promising choice for developers seeking cutting-edge web backend solutions.
Read Full Article
3 Likes
Dev
103

Image Credit: Dev
The Gem of a Github Action you never used
- Nixopus uses QEMU to streamline VPS/server workflow, overcoming bottlenecks in deployment.
- Challenges included testing installation script changes across Linux distributions and various parameters.
- Traditional solutions like unit tests and manual testing on a VPS proved insufficient.
- Using tools like HashiCorp Vagrant for virtualization posed resource and complexity issues.
- Containers couldn't effectively simulate systemd and networking scenarios, leading to full system emulation with QEMU.
- QEMU's GitHub Action provided a reliable and clean solution for testing installations.
- The process highlighted the importance of solving real-world problems with intent and evaluating complexity vs. scalability.
- The journey emphasized the iterative nature of engineering problem-solving.
- Joining Nixopus's community may offer insights into innovative engineering solutions.
Read Full Article
6 Likes
Dev
345

Image Credit: Dev
My Experience with Hyperlane A Rust Newbie’s Journey in Developing a Campus API
- A junior computer science student shares their positive experience with the Hyperlane Rust HTTP framework while developing a campus API project.
- Encountered thoughtful abstractions like the Context (ctx) which simplified handling request methods and response status codes.
- Utilized route macros for easy route declaration and received friendly error messages for mistakes, making the framework beginner-friendly.
- Explored the middleware onion model for request processing, enhancing user authentication with JWT verification middleware and understanding middleware order.
- Implemented WebSocket support for real-time chat functionality, experiencing clear WebSocket lifecycle design and stable resource usage even with multiple users.
- Utilized dynamic routing with regex parameters, noting the framework's detailed route error handling and parsing processes.
- Performed performance testing with Hyperlane achieving impressive QPS, proving faster performance compared to other frameworks like Gin and supporting concurrent users.
- Experienced growth with Hyperlane, overcoming initial pitfalls, and appreciating the framework's clear documentation and continuous updates.
- Deployed the project successfully on the school server, handling daily transactions with Hyperlane's performance and usability balance.
- Hyperlane proved to be beginner-friendly, providing example code that can be directly used, making it an enjoyable choice for student developers transitioning to Rust.
Read Full Article
20 Likes
Dev
224

Image Credit: Dev
Multithreading in Java: Concepts and Code
- Multithreading in Java is essential for achieving better performance and speed in application development, allowing tasks to run simultaneously.
- Multithreading involves running multiple threads within a single program, enabling parallel execution of tasks.
- Using multithreading in Java leads to faster operations, improved user experience, and efficient CPU utilization.
- Two common ways to implement multithreading in Java are by extending the Thread class and implementing the Runnable interface.
- Key concepts of multithreading include understanding the thread life cycle, thread methods, and synchronization to avoid data conflicts.
- An example of synchronizing threads to control access to shared resources is highlighted.
- Multithreading is beneficial for scenarios like downloading files while displaying loading bars simultaneously, enhancing user experience.
- Tips for using multithreading effectively in Java include avoiding excessive thread creation, careful synchronization, and utilizing thread pools for managing multiple threads.
- In conclusion, mastering multithreading in Java leads to improved application performance, responsiveness, and resource utilization.
- The article recommends exploring Java tutorials on TPoint Tech Website for comprehensive learning and practical approaches.
Read Full Article
13 Likes
Dev
51

Image Credit: Dev
Goodbye Wait Wait Wait My Junior Year Adventure A Secret Weapon That Makes Code Fly
- As a junior majoring in Computer Science and Technology, the author shares their journey encountering a revolutionary web backend framework, Hyperlane, that transformed their coding experience by providing extreme performance and elegant design.
- The author reflects on past struggles with lag and inefficiency in programming projects, highlighting scenarios like dealing with high concurrency and stress testing that exposed performance bottlenecks in traditional frameworks.
- Encountering Hyperlane, a lightweight framework built on Rust and Tokio, the author delves into the onboarding experience, emphasizing the simplicity of installation, clear API design, and efficient logging.
- Through practical case studies, the author demonstrates substantial performance improvements using Hyperlane, showcasing higher QPS, reduced response times, and lower resource consumption compared to previous frameworks.
- The deep dive into Hyperlane's technical features explores its reliance on Tokio's asynchronous runtime, robust error handling mechanism, and balance between configuration flexibility and simplicity.
- Comparisons with other Rust web frameworks like Actix Web and Axum highlight Hyperlane's distinct lightweight design philosophy and focus on core HTTP server capabilities, making it suitable for high-performance API services.
- The author provides suggestions for Hyperlane's future enhancement, including continuous improvement of documentation, expansion of the ecosystem, community building, and staying true to its core strengths while innovating further.
- Concluding with a call to developers to embrace tools like Hyperlane for efficient web development in the era of cloud computing and microservices, the author shares hopes and expectations for Hyperlane's growth and success in the evolving technological landscape.
Read Full Article
3 Likes
Medium
285
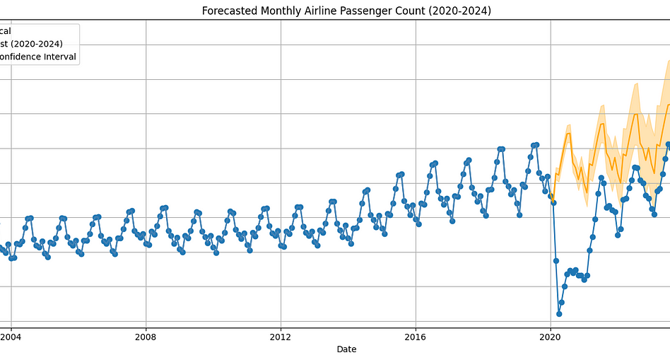
Image Credit: Medium
Forecasting Airport Traffic with SARIMA: A SeaTac Case Study
- A study used SARIMA to forecast SeaTac Airport passenger traffic, suggesting a recovery by 2023.
- The dataset comprised monthly passengers from 2003 to 2024, with modeling focused on pre-pandemic data (2003-2019).
- SARIMA, chosen for its seasonal pattern handling, consists of non-seasonal and seasonal components.
- To achieve stationarity, differencing was applied to the data through SARIMA's d and D parameters.
- Augmented Dickey-Fuller test confirmed non-stationarity, leading to first-order and seasonal differencing.
- Auto_arima function determined the SARIMA model parameters for the data.
- The trained SARIMA model forecasted passenger counts for 2020–2024.
- Actual passenger counts by 2023 aligned with the model's forecast, indicating a recovery in demand.
- Passenger counts mostly fell within the 95% confidence interval, consistent with pre-COVID trends.
- SARIMA was effective in forecasting stable, seasonal patterns but less suited for sudden disruptions like COVID.
- The study showcases SARIMA's ability to capture long-term air travel trends.
- Forecasting methodologies like SARIMA allow for interpreting future air travel demand with historical data.
- Differencing in SARIMA does not erase trends but highlights changes for interpretation.
- The SARIMA model reflected SeaTac's recovery post-pandemic, aligning with historical trends.
- Beyond COVID disruptions, SARIMA remains valuable for modeling consistent patterns and future directions.
- By 2023, SeaTac's passenger traffic had realigned with pre-pandemic growth patterns, indicating a full recovery.
Read Full Article
17 Likes
Medium
172

Image Credit: Medium
Mastering Java BigDecimal: Precision Math Made Simple.
- BigDecimal in Java is a class for arbitrary-precision decimal numbers providing exact control over precision and rounding.
- It stores numbers as an unscaled value and a scale, ensuring accuracy for small and large numbers.
- BigDecimal is crucial for financial systems and scientific calculations where precision is paramount.
- Contrary to float or double, BigDecimal avoids floating-point errors common in quick calculations.
- BigDecimal supports calculations like addition, subtraction, and division, offering more precise results.
- Creating BigDecimal objects is typically done using constructors with strings to avoid floating-point errors.
- BigDecimal methods like add(), subtract(), multiply(), and divide() are used for mathematical operations.
- When using division with BigDecimal, specifying scale and rounding mode is crucial to avoid infinite decimals.
- Using compareTo() for comparisons and constants like BigDecimal.ZERO helps in simplifying code.
- Testing edge cases with BigDecimal is advised for scenarios involving zero, negative numbers, or extreme values.
- Practical examples, such as calculating sales tax, demonstrate the clean and precise nature of BigDecimal calculations.
- BigDecimal ensures accuracy in financial applications and critical systems by avoiding floating-point pitfalls.
- String constructors, explicit scaling, and thorough testing are recommended for effective use of BigDecimal.
Read Full Article
10 Likes
Medium
345

Image Credit: Medium
Track Your Dev: A GitHub-Powered Dashboard for Non-Tech Teams
- TrackYourDev is a new GitHub-powered dashboard designed for non-tech teams.
- The platform provides visual overviews of developer activity without requiring GitHub expertise or coding knowledge.
- It is aimed at bosses, project managers, and startup founders who need insights into GitHub without diving into technical details.
- TrackYourDev differentiates itself by focusing on team members who are not developers.
- Current features include connecting GitHub repos to generate clear activity summaries.
- The platform addresses the gap where non-tech team members need visibility into GitHub without relying on engineers.
- Future plans for TrackYourDev consist of expanding its features and functionality.
- The platform is welcoming ideas from users and encourages suggestions for improvement.
- People managing developer teams without GitHub proficiency can benefit from using TrackYourDev.
- The platform invites those interested to follow their progress as they continue to develop and enhance the tool.
Read Full Article
20 Likes
Dev
337

Image Credit: Dev
👂 How Event Listeners Work in JavaScript
- JavaScript utilizes event listeners to detect and respond to user interactions on webpages.
- Events can include actions such as clicking a button, typing in a text field, hovering over an element, or scrolling.
- An event listener in JavaScript essentially waits for a specific event to occur and then executes a designated piece of code.
- Using addEventListener() is preferred over inline event handling methods like onclick in HTML due to its flexibility and cleanliness.
- Event listeners allow for attaching multiple listeners to the same element and separating HTML from JavaScript.
- Event listeners can be removed using the removeEventListener() method, enabling better control over event handling.
- Common event types include 'click', 'keydown', 'submit', 'mouseover', 'input', and 'scroll'.
- Each event type can trigger specific website behaviors, such as validation, pop-ups, or animations.
- When an event occurs, JavaScript passes an event object to the associated function, providing details about the event.
- Experimenting with event listeners is recommended for those learning JavaScript to understand user interactions better.
- Event listeners enhance website interactivity and engagement by enabling responses to user actions.
- JavaScript's event listeners facilitate a dynamic dialogue between the code and the user on a webpage.
Read Full Article
20 Likes
For uninterrupted reading, download the app