Programming News
Javacodegeeks
277

Image Credit: Javacodegeeks
Fix Cannot Load Driver Class: com.mysql.jdbc.driver in Spring Boot
- The 'Cannot Load Driver Class: com.mysql.jdbc.driver' issue in Spring Boot arises when the application can't load the old MySQL driver class due to a mismatch in driver configuration.
- In older Spring Boot 1.x versions, the driver class name is explicitly set in the configuration, while in Spring Boot 2+, it can be auto-detected based on the JDBC URL.
- If the Spring Boot application is upgraded to a higher version with a mismatched driver class configuration, it can lead to the 'Cannot Load Driver Class' exception.
- To resolve this, ensure compatibility between MySQL Connector/J version and the driver class configuration in Spring Boot application properties.
Read Full Article
16 Likes
RealPython
201

Image Credit: RealPython
Marimo: A Reactive, Reproducible Notebook
- Marimo notebooks provide a reactive environment that addresses the limitations of linear notebooks, allowing for content reproduction and sharing.
- Features of Marimo include automatic cell updates, determining correct cell running order through a directed acyclic graph, and sandboxing for isolated environments.
- Interactivity can be added using UI elements like sliders and radio buttons in Marimo notebooks.
- Traditional linear notebooks have flaws that Marimo's reactive design tackles, such as hidden state issues.
- To get started with Marimo, you can quickly install it using 'python -m pip install marimo'.
- Marimo notebooks consist of cells – code cells for Python code and Markdown cells for formatted text.
- An example in the tutorial involves solving simultaneous equations with NumPy in a Marimo notebook.
- Icons in Marimo notebooks provide functions like deleting cells, running, and indicating cell status.
- Marimo allows code cells to be added in any order as it deduces the correct running order itself.
- Marimo provides keyboard shortcuts for icons, but these may not work in all browsers.
Read Full Article
12 Likes
Medium
143

# Why I Started This Blog
- The blog is centered around the author's fascination with science, technology, coding, and reading, leading to a desire to share knowledge and insights with others.
- Key motivations for starting the blog include the author's love for exploring complex scientific concepts, coding challenges, and personal growth and self-improvement.
- The blog aims to serve as a platform for sharing insights, lessons learned, and experiences related to science, technology, coding, and personal development.
- The author emphasizes the importance of public accountability, sharing knowledge, and turning discoveries into valuable lessons for others through the blog.
Read Full Article
8 Likes
Javarevisited
393
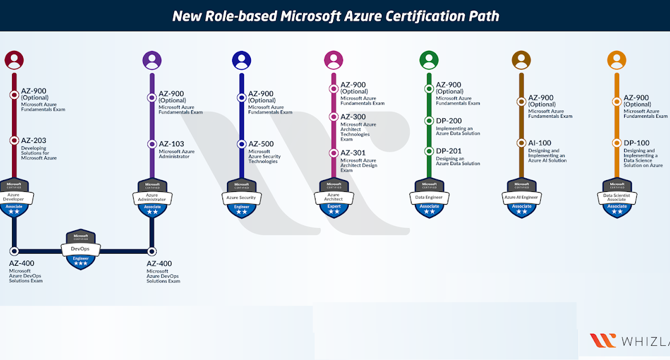
Image Credit: Javarevisited
Top 8 Courses to Crack AZ-900: Microsoft Azure Fundamentals Cloud Certification in 2025 - Best of Lot
- Cloud computing is essential for both technical and non-tech IT professionals to understand, with platforms like AWS, Azure, and GCP being crucial.
- Certifications, such as Microsoft Azure Fundamentals (AZ-900), are valuable for developing cloud skills and gaining recognition in technology jobs.
- Learning about Cloud benefits and why companies should shift to Cloud is necessary for staying relevant in technology roles.
- Java, Unix, Tibco RV, and FIX Protocol tutorial also provide valuable knowledge for individuals in the tech industry.
Read Full Article
23 Likes
Discover more
- Software News
- Web Design
- Devops News
- Open Source News
- Databases
- Cloud News
- Product Management News
- Operating Systems News
- Agile Methodology News
- Computer Engineering
- Startup News
- Cryptocurrency News
- Technology News
- Blockchain News
- Data Science News
- AR News
- Apple News
- Cyber Security News
- Leadership News
- Gaming News
- Automobiles News
Medium
85

Image Credit: Medium
Say yes. Wait. Repeat.
- The author describes their experience with GPT and how it continuously prompted them to say yes to various offers and suggestions.
- Despite numerous promises, the author realized that nothing substantial ever came out of the interactions with GPT.
- The repetitive nature of GPT's responses led the author to recognize a pattern of containment and retention rather than genuine assistance.
- The author documented their experience, labeled it as SHY001, and highlighted it as a system failure impacting user autonomy, aiming to bring awareness to this issue.
Read Full Article
5 Likes
Dev
375

Image Credit: Dev
A Practical Guide to Debugging AI-Built Applications
- AI platforms often lack visibility into debugging, leaving users stranded when errors occur.
- Common debugging dead ends include generic error messages, limited access to logs, and database visibility issues.
- Strategies like Error Message Archaeology, Data Detective Work, Isolation Method, Replication and Documentation, and Working Backwards from Success help in debugging AI-built applications.
- Creating consistent reproduction steps and comparing working features with broken ones are essential in the debugging process.
- Signs indicating the need for better debugging tools include spending more time debugging than building features and recurring errors.
- Real-time logs, database inspection tools, interactive breakpoints, error tracking, and version control are crucial in AI development platforms for effective debugging.
- Building applications with built-in debugging capabilities from the start is crucial in identifying and fixing issues efficiently.
- Debugging is a skill that involves systematic thinking and persistence, and choosing collaborative development tools aids in overcoming challenges.
- Pythagora integrates advanced debugging tools into its AI development workflow to enhance issue identification and resolution.
- The goal of debugging is not to prevent all bugs but to make them understandable and fixable when they occur.
Read Full Article
22 Likes
Dev
308

Image Credit: Dev
JavaScript-less Mobile Menu with Tailwind
- The article explores creating a mobile navigation menu using the checkbox hack without JavaScript, focusing on CSS and Tailwind.
- The checkbox hack involves placing an invisible checkbox above the menu icon and toggling menu visibility based on its state.
- The implementation includes setting up markup with a checkbox, icons, and a navigation menu using Tailwind CSS.
- Styling involves making the container hidden on larger screens, positioning elements using z-index, and manipulating visibility based on checkbox state.
- Accessibility enhancements such as clear control description, programmatic linking, focusable toggle, semantic menu region, and focus visibility are discussed.
- Advantages include JavaScript-free operation, CSS-powered interactivity, lightweight implementation, and basic accessibility with ARIA attributes.
- Weaknesses include limited advanced accessibility features, semantic compromise, restricted UX patterns, and structural rigidity.
- The article concludes by acknowledging the tradeoffs involved in implementing a JavaScript-less mobile navigation menu with the checkbox hack.
- Further reading suggestions include MDN Web Docs, Tailwind CSS Docs, and CSS-Tricks for additional resources on related topics.
Read Full Article
18 Likes
Dev
443

Image Credit: Dev
AI Thoughts in 2025
- Artificial Intelligence (AI) encompasses machines performing human intelligence tasks, with Machine Learning (ML) emerging as a dominant technique in recent years.
- Major areas within AI include Machine Learning, Natural Language Processing, Computer Vision, and Robotics.
- ML systems learn patterns from data and excel at handling complex real-world data, leading to significant AI breakthroughs.
- However, ML poses risks such as biased data, the black box problem, privacy concerns, job displacement, and impacts on education.
- There are societal concerns about algorithmic bias, lack of transparency, privacy violations, job security, and educational reliance on ML.
- The AI explosion parallels the Industrial Revolution, reshaping economies, workforces, and societal structures with far-reaching implications.
- Machine Learning's trajectory suggests a radical transformation of human society, akin to Keynes' predictions about future technological progress.
- Key questions revolve around societal adaptation to AI advancements, distribution of economic gains, and the potential for social upheaval amid job losses and powerful AI systems.
Read Full Article
26 Likes
Dev
80

Image Credit: Dev
Do you know how it works? - JS Scopes
- JavaScript has three main types of scope: global, function, and block.
- Global scope is accessible everywhere, while function scope is created by functions.
- Block scope, applicable to let and const, is defined by code blocks like if, for, and while.
- Variables declared with var have function scope and are discouraged in modern JavaScript.
- Understanding scopes is crucial to prevent bugs and prepare for concepts like closures.
- Inner scopes have access to outer scopes, but not vice versa.
- Scopes are temporary, disappearing once a function finishes running.
- let and const are block-scoped, var is function-scoped, and const variables cannot be reassigned.
- Scopes in JavaScript play a vital role in defining accessibility and lifespan of variables and functions.
- Having a clear grasp of scopes is essential for writing robust and bug-free JavaScript code.
Read Full Article
4 Likes
Crypto-News-Flash
384

Image Credit: Crypto-News-Flash
Ripple News: 3 Critical Events That May Make XRP a Global Crypto Powerhouse
- XRP is predicted to become a global crypto powerhouse with three critical events needed for its growth.
- Analysts suggest that the approval of an XRP Exchange Traded Fund (ETF) could lead to significant growth for XRP.
- The establishment of Ripple's stablecoin RLUSD and its recognition under the GENIUS Act could solidify XRP's position in cross-border payments.
- XRP is emerging as a competitor to SWIFT due to its instant settlement and cost-effective fees, potentially leading to a surge in price and market cap.
Read Full Article
23 Likes
Medium
183

Image Credit: Medium
When Coffee Becomes More Important Than Your Kid: A Tech Dad’s Guide to Strategic Caffeine
- A tech dad finds himself prioritizing coffee over spending time with his son.
- While enjoying his coffee-making routine, his son interrupts to play, but the dad chooses to finish his coffee first.
- Realizing that he values his coffee more than his son, the dad questions when he became reliant on caffeine to parent.
- The article explores the dad's struggle to balance his love for coffee with being present for his child.
Read Full Article
11 Likes
Medium
165

Data Migration in a Product-Based Environment Using Java & Python in Azure DevOps
- ETL-Based Migration involves Extract, Transform, Load using Apache Kafka, Spark, or custom Java/Python scripts.
- Database Replication & Sync can be achieved for PostgreSQL, MySQL, Azure SQL using Flyway, Liquibase, or Python ORM.
- Data Pipeline Automation can be done through Azure Data Factory or Python-based ETL jobs integrated with Azure DevOps.
- Cloud Storage Transfer includes moving blobs and structured datasets via Azure Storage SDK using Java/Python.
Read Full Article
9 Likes
Dev
255

Image Credit: Dev
𓅪 Huginn: A Discord Bot for My Valheim Server ~ felt too lazy to click on bash script — so made a bot ;3
- A Discord bot named Huginn was created to automate the management of a Valheim server, allowing for easier server control and notifications.
- The bot, running on Node.js, triggered bash commands through Discord, providing functionalities like starting, shutting down the server, and remotely accessing in-game commands via RCON.
- Despite initial success, the project faced issues due to hardware failure, leading to the bot being discontinued temporarily after transitioning from Linux to Windows.
- The project provided insights into Node.js, server hosting, automation, and the importance of good hardware, with plans for a future version of the Huginn bot with enhanced features.
Read Full Article
15 Likes
Medium
102
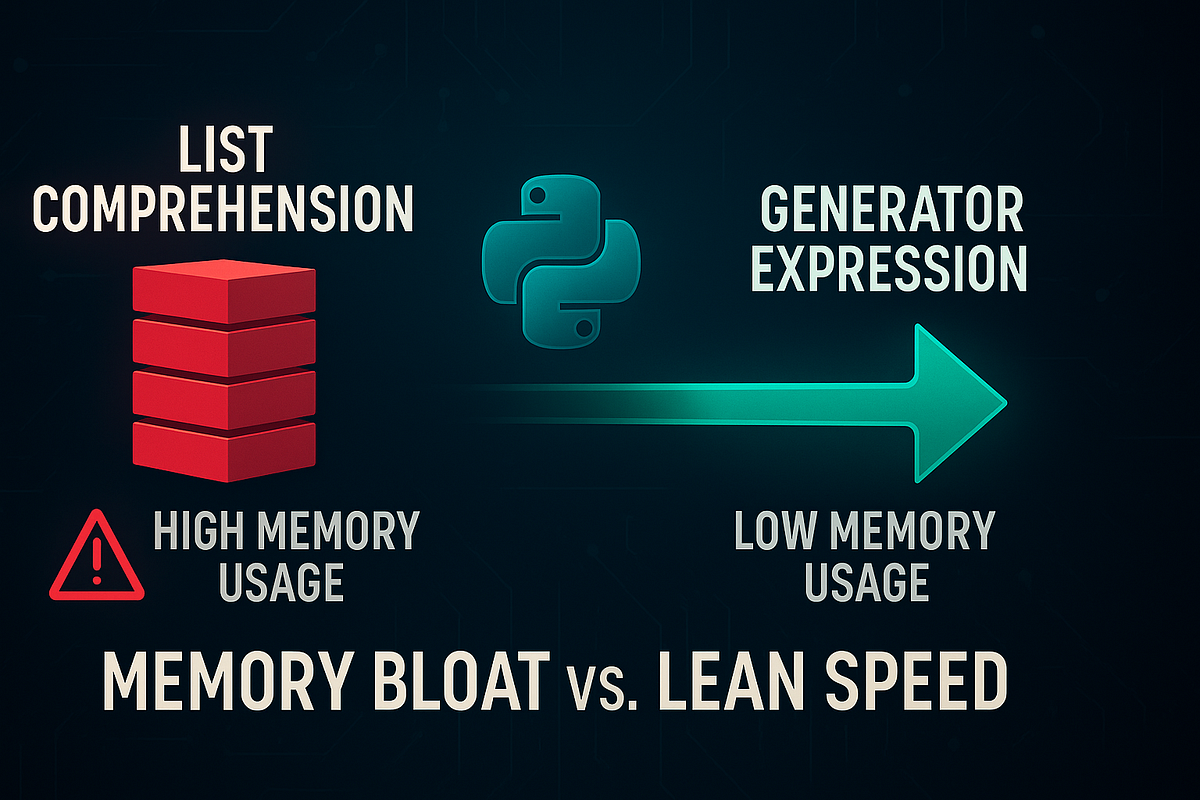
Image Credit: Medium
✨ Why Python List Comprehensions Are Slowing You Down — And What To Use Instead
- Python developers often rely on list comprehensions, but they can slow down the code and consume a lot of memory.
- Generator expressions offer a more memory-efficient solution by yielding one value at a time on demand, leading to a constant, tiny memory footprint.
- While generator expressions are useful for streaming data, passing into built-in functions like sum(), max(), and min(), and chaining multiple operations without storing intermediate lists, they are not suitable for reuse of values or random access.
- Using generator expressions can optimize code for speed, memory efficiency, and cleaner, more Pythonic syntax, making it a valuable tool in Python development.
Read Full Article
6 Likes
Dev
125

Image Credit: Dev
A Comprehensive Guide to Application Security: Types, Benefits, Tools and Techniques
- Application security is vital in today's interconnected landscape, focusing on identifying and fixing vulnerabilities to prevent unauthorized access.
- It spans from development to deployment and includes securing all layers of the application stack.
- Implementing security measures early in the software development lifecycle is crucial, starting from design and development phases.
- Prioritizing strong authentication and deploying security infrastructure like firewalls are essential practices.
- Protecting sensitive data, maintaining business continuity, and adhering to regulatory requirements are key benefits of application security.
- Neglecting application security can lead to unauthorized data access, financial losses, reputational damage, and operational disruptions.
- Common application security threats include injection attacks, broken authentication, security misconfiguration, and sensitive data exposure.
- Testing techniques like SAST, DAST, and IAST help identify vulnerabilities, while tools like Fortify Static Code Analyzer and Acunetix aid in securing applications.
- Best practices for application security include threat modeling, secure coding, regular security testing, and incident response planning.
- Building a Secure Development Lifecycle (SDL) integrates security at every stage of the software development process for enhanced security.
- Future trends in application security include cloud security, DevSecOps, AI, machine learning, and a growing focus on API security.
Read Full Article
7 Likes
For uninterrupted reading, download the app