Programming News
Medium
423

Image Credit: Medium
Hear Your Code: A Beginner’s Guide to Text-to-Speech in Python️
- Text-to-Speech (TTS) is a technology that converts written text into audible speech, and with Python, incorporating TTS into your projects is easy, even for beginners.
- TTS is utilized in virtual assistants, accessibility tools, e-learning platforms, navigation systems, and video game characters.
- Python makes it accessible for all developers without requiring an advanced understanding of AI.
- Adding TTS to your Python projects opens up opportunities for various applications like reading aloud quotes, articles, greetings, and more.
Read Full Article
25 Likes
Medium
181
Image Credit: Medium
JavaScript memory management
- JavaScript memory leaks can cause web apps to slow down, act weird, or crash over time.
- JavaScript is a garbage-collected language that automatically frees up memory not in use through the garbage collector.
- Memory leaks occur when memory that should be cleaned up is still being held onto by the code, leading to performance issues.
- These forgotten bits of memory accumulate over time and can significantly impact the app's performance.
Read Full Article
10 Likes
Medium
304

Image Credit: Medium
THE IMPORTANCE OF ASYNC PROGRAMMING
- Short runtime is crucial for software programs, especially those working with large datasets.
- Async programming can significantly reduce runtime by allowing threads to perform other tasks while waiting for responses.
- For small datasets, the impact of async programming may not be significant, but for larger datasets, it becomes necessary.
- Async programming overcame the limitation of threads idling while waiting for responses, improving efficiency in handling tasks asynchronously.
Read Full Article
18 Likes
Javacodegeeks
142
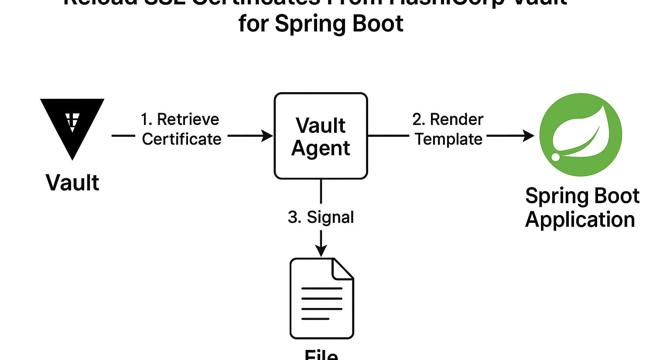
Image Credit: Javacodegeeks
Spring Boot HashiCorp Vault Reload SSL Certificates Example
- This guide explains how to use Spring Boot HashiCorp Vault to manage and rotate TLS certs securely without app restarts.
- Key concepts involve Spring Boot, HashiCorp Vault, Vault Agent, and SSL certificate reloading for automation.
- Configuration steps include setting up Vault server with PKI secrets engine, configuring Vault Agent, and configuring Spring Boot app.
- By integrating Spring Boot and HashiCorp Vault for SSL certificate management, it enhances security, automates renewal, and avoids application downtime.
Read Full Article
7 Likes
Discover more
- Software News
- Web Design
- Devops News
- Open Source News
- Databases
- Cloud News
- Product Management News
- Operating Systems News
- Agile Methodology News
- Computer Engineering
- Startup News
- Cryptocurrency News
- Technology News
- Blockchain News
- Data Science News
- AR News
- Apple News
- Cyber Security News
- Leadership News
- Gaming News
- Automobiles News
Dev
200

Image Credit: Dev
Kotlin's Performance and What it Means
- Kotlin, a modern programming language known for its concise syntax and Java interoperability, is examined for its performance compared to other languages.
- In benchmarks, Kotlin JVM consistently ranks lower in performance than other languages, even after enabling compiler optimizations.
- The benchmarks app runs programs simultaneously 25 times to calculate averages and minimum times, revealing Kotlin's slower overall performance.
- Analyzing a Bubble Sort benchmark in Kotlin Native shows decent speed but lags behind in minimum times, indicating room for improvement.
- Decompilation of Kotlin code reveals runtime metadata comparison for type/version correctness, impacting program performance.
- Kotlin's runtime features like metadata comparison and Intrinsics for null safety add overhead, potentially slowing down program execution.
- The analysis suggests that while Kotlin is a promising language, its current performance may need enhancements for higher efficiency.
- Despite the trade-offs for safety and correctness features, Kotlin's performance could see improvements in the future.
Read Full Article
12 Likes
Dev
442

Image Credit: Dev
Introducing the PullFlow Agent Experience: Streamline Your AI Collaboration
- AI agents are increasingly used in software development to streamline code reviews and developer workflows.
- Key AI agents like CodeRabbit, Greptile, Jolt AI, Entelligence AI, and Copilot are popular for code reviews, technical design assistance, code writing, and real-time code completions.
- Introducing the PullFlow Agent Experience, a centralized system in Slack to manage AI agent notifications and conversations efficiently.
- Features of PullFlow include an Agents Dashboard, Automatic Integration, Granular Notification Control, and Seamless Communication between GitHub and Slack.
Read Full Article
26 Likes
Dev
222

Image Credit: Dev
My Journey Through `this` in JavaScript: From Confusion to Clarity
- When learning JavaScript, understanding 'this' can be confusing due to its dynamic nature.
- this in JavaScript refers to the execution context of a function, determined by the call site.
- JavaScript has three main execution contexts: Global, Function, and Eval.
- Four primary ways of setting 'this' are Default, Implicit, Explicit, and new Binding.
- Arrow functions in JavaScript do not have their own 'this' and inherit it from the lexical scope.
- Common pitfalls with 'this' include losing context in callbacks and nested functions.
- Understanding 'this' involves recognizing call sites and using tools like arrow functions and bind.
- Practice and experimentation are key to mastering the behavior of 'this' in JavaScript.
- Overall, 'this' in JavaScript is a powerful tool once its behavior is understood and applied correctly.
- To dive deeper into 'this' in JavaScript, resources like MDN and 'You Don’t Know JS: this & Object Prototypes' are recommended.
Read Full Article
13 Likes
Infoq
145

Image Credit: Infoq
Presentation: Ultra-fast In-Memory Database Applications with Java
- The presentation discusses ultra-fast in-memory database processing with Java, showing how to build the fastest database applications by leveraging a framework used by gaming and banking companies for two decades.
- It emphasizes the importance of high performance, low data storage costs, simplicity for developers, and sustainability for organizations in modern applications.
- The speaker, Markus, with over 20 years of Java experience, introduces Eclipse Foundation projects like Jakarta EE, Micronaut, and Helidon before delving into current challenges in database development.
- He highlights issues like slow performance, high cloud costs, complexity, and lack of sustainability in traditional database programming.
- The talk addresses the limitations and challenges of object-relational mapping, impedance mismatches, and the compatibility issues between Java and databases.
- It explores the differences in NoSQL databases and their compatibility with Java, mentioning the need for a new approach to database development for modern applications.
- The alternative solution presented is EclipseStore, a Java-native, in-memory persistence engine that offers ultra-fast data processing, significant cost savings, and environmental benefits by eliminating the need for traditional database servers.
- Markus explains the EclipseStore workflow of seamlessly storing Java objects to disk without the need for object-relational mapping, emphasizing the simplicity and effectiveness of the approach.
- He introduces the Eclipse Serializer at the core of EclipseStore, detailing its persistence engine, handling of concurrency, and compatibility with distributed systems for high-speed data processing.
- The talk concludes by highlighting that EclipseStore, while requiring Java developers to adapt their mindset, provides a comprehensive and efficient approach to building high-performance applications with low latency and cost savings.
- The speaker invites attendees to explore free training resources for EclipseStore and emphasizes its potential as a drop-in replacement for Hibernate, suitable for various applications and enterprise use cases.
Read Full Article
8 Likes
TechCrunch
395

Image Credit: TechCrunch
Google’s Gemini chatbot can now more easily analyze GitHub projects
- Gemini, Google’s AI-powered chatbot, can now connect to GitHub for users subscribed to the $20-per-month Gemini Advanced plan.
- Gemini Advanced customers can add a public or private codebase on GitHub to allow the chatbot to generate and explain code, debug existing code, and more by directly connecting via the prompt bar.
- AI models, including Google’s, still struggle with coding quality software and may introduce security vulnerabilities and errors due to weaknesses in understanding programming logic.
- The new GitHub integration comes shortly after OpenAI introduced a GitHub connector for ChatGPT deep research, showing AI companies are rapidly adding new capabilities to differentiate their products in the competitive market.
Read Full Article
23 Likes
RealPython
27

Image Credit: RealPython
How to Get the Most Out of PyCon US
- PyCon US is a vibrant community event filled with talks, workshops, and social gatherings around Python, offering tutorials, conference talks, and sprints.
- First-time attendees may find PyCon intimidating, but this guide helps navigate the event, focusing on tutorials, conference talks, and sprints.
- PyCon US, established in 2003, has evolved to become the largest Python-centered conference, fostering a unique experience for all attendees.
- The conference involves tutorials, conference talks over three days, and sprints where attendees can apply their learning to open-source projects.
- Preparation before PyCon, such as reviewing the talks schedule, using the PyCon US mobile app for scheduling, and arriving early, enhances the conference experience.
- Attending tutorials offers in-depth learning and networking opportunities, while sprints provide a platform to apply skills and collaborate with others.
- Newcomers to PyCon can benefit from the Newcomer Orientation to understand the conference and how to engage with it.
- Planning ahead, selecting talks of interest, and using available resources like the PyCon US app contribute to maximizing the PyCon experience.
- Coming prepared with questions or problems to solve during talks helps in focusing on relevant topics that align with individual interests.
- Attending the opening reception and interacting with other attendees, speakers, and sponsors can enrich the networking experience at PyCon.
Read Full Article
1 Like
Medium
141

Image Credit: Medium
Types from Typescript
- Typescript introduces various types for defining variables:
- Primitives types like Boolean, Number, and String are similar to JavaScript.
- Typescript also includes composed types such as Array, Tuple, Enum, and Object.
- The Any type represents any other type.
- Null and Undefined have specific meanings where Null signifies empty or reset value, while Undefined is for unset values.
- Unknown type is used when the type of data from external sources is unknown.
- Void represents no type and is used for functions that don't return anything.
- Never type signifies a type that never occurs, often seen in functions that always throw errors.
- Generic type (T) allows accepting any type while enforcing type checking.
- Unions and Intersections are essential for type declaration in Typescript.
Read Full Article
8 Likes
Medium
4

Image Credit: Medium
15 core programming skills and reusable templates
- A free PDF guide compiling the top 15 Python coding patterns, including Binary Search, Sliding Window, Two Pointers, DFS & BFS, Dynamic Programming, Trie, Heaps, Union-Find, and more with real use cases and reusable code templates is available.
- The guide covers essential programming skills for FAANG-level interviews or LeetCode's toughest challenges, providing insights on when to use each pattern and offering reusable code templates.
- Some of the key patterns covered include Binary Search, Two Pointers, Sliding Window, Prefix Sum, HashMap/Set, Stack/Monotonic Stack, Backtracking, Dynamic Programming, Graph Traversal (DFS & BFS), Union-Find, Heap/Priority Queue, Trie, Bit Manipulation, Greedy Algorithms, and Topological Sort.
- The guide is a valuable resource for both beginners and those looking to enhance their skills for elite interviews, offering a comprehensive reference for various Python coding patterns and their applications.
Read Full Article
Like
Dev
404

Image Credit: Dev
How Crypto Billionaires Spend: Signals of Power, Branding, and Strategy
- Wealth in crypto circles is being spent in unconventional and symbolic ways to shape influence, personal brands, and narratives in the tech and Web3 ecosystems.
- Crypto billionaires follow strategic archetypes like the Minimalist Builder, Public-Facing Strategist, and Showman Investor for wealth allocation.
- Examples of unconventional spending include a treasure hunt with $2 million prizes, private financing of a $55 million SpaceX mission, and staged art performances by prominent figures like Justin Sun.
- Strategic spending choices in crypto not only reflect economic decisions but also serve to create brand identity, cultural impact, and global positioning for individuals within the industry.
Read Full Article
24 Likes
Dev
200

Image Credit: Dev
Supercharge Project Switching with Wrkspace
- Wrkspace is a productivity tool for developers aiming to simplify and boost workflow efficiency.
- It offers a 300% improvement in startup time and eliminates repetitive scripts by automating project setup.
- Features include full Docker container orchestration, automatic script execution, instant editor and terminal sessions, and browser page launches.
- Users like Gabriele Pini, a full-stack developer, have found Wrkspace helpful in streamlining project launches and coding processes.
Read Full Article
12 Likes
Medium
198

Image Credit: Medium
Why Clean API Design is Like Good Music: The Art of Vibe-Driven Development
- Vibe-driven development is like finding a sweet spot in coding where everything feels intuitive and productive.
- Embracing vibe-driven development can transform how code is written and boost productivity significantly.
- Vibe coding is not about relying on AI to write code for non-coders; it's about using AI to enhance developers' expertise.
- Just like good music is more than correct notes, vibe-driven development involves creating code that resonates on a deeper level.
Read Full Article
11 Likes
For uninterrupted reading, download the app