Cloud News
Dev
86

Image Credit: Dev
My 10 Years in the AWS Community
- Celebrating 10 years in AWS Community, starting from Hamburg User Group Meetup in 2015.
- Hosted over 60 meetups, including re:Invent re:Caps, growing group to 2,700 members.
- In 2022, became a founding member of Förderverein AWS Community DACH in Berlin.
- Co-founded new AWS User Group in Bonn, organized meetups, and established collaborations.
- Reflecting on 10 years of community building, innovation, and collaboration in AWS ecosystem.
Read Full Article
5 Likes
Siliconangle
388

Image Credit: Siliconangle
12 signs AI infrastructure is reshaping the IPO market: theCUBE’s RAISE Summit insights
- AI infrastructure reshaping IPO market, critical for scaling, competing, going public.
- Companies now focus on embedding AI in business models for sustainability, profitability.
- Investors prioritize durability, growth, changing playbook for IPO readiness in 2025.
- Insights on AI infrastructure from industry leaders at RAISE Summit, Paris.
Read Full Article
15 Likes
Engadget
326

Image Credit: Engadget
Amazon Prime Day deals on SSDs and external hard drives are still available: Save on Samsung, Crucial, Sandisk and more
- Upgrade your devices with discounted SSDs and external hard drives on Amazon Prime Day.
- Whether you're looking for increased storage space or faster speeds, there are deals for you.
- Grab offers on popular brands like Samsung, Crucial, Sandisk, WD, and more today.
Read Full Article
19 Likes
Siliconangle
262

Image Credit: Siliconangle
AWS believes humans and AI can be workplace allies
- Amazon Web Services Inc. (AWS) is moving forward with implementing agent workforces and AI-powered tools, despite concerns about AI causing job loss and content scraping.
- Colleen Aubrey, senior vice president of applied AI Solutions at AWS, believes in AI's transformative power in the workplace and envisions hybrid workforces where people collaborate with AI daily to enhance productivity.
- AWS's AI-native contact center, Amazon Connect, now offers AI support for various interactions, aiming to improve customer experience and streamline operations.
- AI is gaining traction in healthcare to enhance patient care and reduce administrative burdens on doctors. AWS aims for its employees to become 'AI native' and work alongside AI tools in the near future.
Read Full Article
13 Likes
Discover more
- Programming News
- Software News
- Web Design
- Devops News
- Open Source News
- Databases
- Product Management News
- Operating Systems News
- Agile Methodology News
- Computer Engineering
- Startup News
- Cryptocurrency News
- Technology News
- Blockchain News
- Data Science News
- AR News
- Apple News
- Cyber Security News
- Leadership News
- Gaming News
- Automobiles News
Tech Radar
48
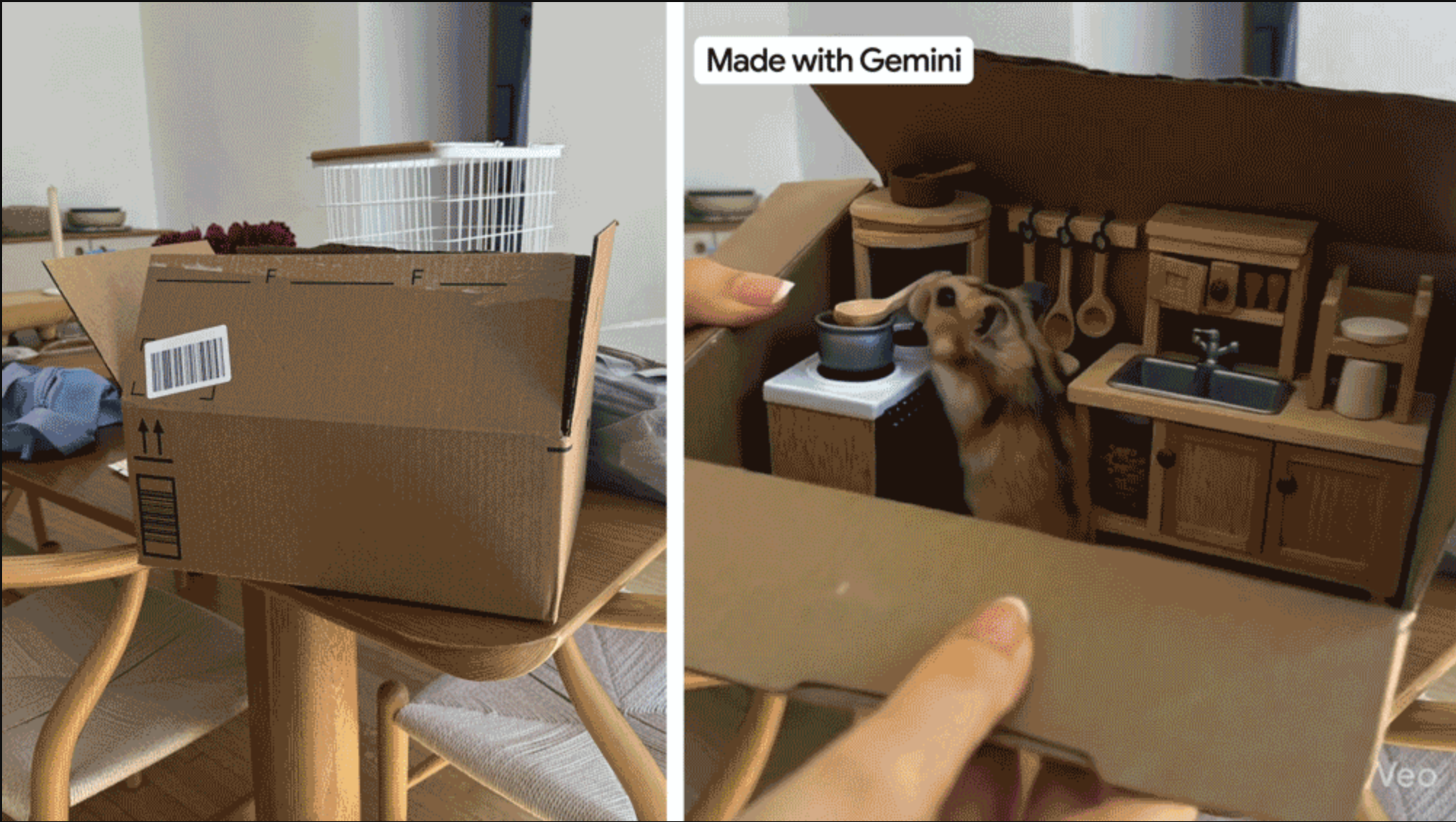
Image Credit: Tech Radar
Google releases photo-to-video Gemini Veo 3 capabilities, and it might just blow your mind
- Google has introduced a new photo-to-video feature in its Gemini Veo 3 image generation tool.
- The capability allows users to convert static photos into eight-second videos with audio, available for Google AI Pro and AI Ultra subscribers.
- Users can access this new feature through the Gemini app on the web, with plans for roll-out on iOS and Android this week.
- Veo 3's ability to sync audio to images and create videos enhances its position as a top AI video generation tool in the market.
Read Full Article
2 Likes
Tech Radar
52

Apple could use a nifty iPhone trick for Macs - updating them to the latest version of macOS while still boxed
- Apple may be working on a system to update Macs while they're still boxed, similar to the process used for iPhones.
- Clues in the macOS Tahoe 26 beta 3 suggest the groundwork for this system named Presto, which would ensure Macs leave the shelf with the latest macOS version.
- The Presto system used for iPhones involves updating the devices wirelessly without unboxing, but adapting this for Macs presents challenges due to differences in hardware and lack of NFC.
- While the feature is under consideration, its implementation for Macs remains unclear, as it would require a unique approach compared to iPhones.
Read Full Article
3 Likes
Siliconangle
417

Image Credit: Siliconangle
Data center infrastructure automation startup Spacelift gets ready for takeoff after raising $51M
- Spacelift Inc. secures $51 million funding for IT infrastructure automation enhancements.
- The startup offers IaC software for automating cloud resource provisioning and management.
- Spacelift's AI-infused platform streamlines infrastructure management, governance, and accelerates developer velocity.
- The company also contributes to open-source project OpenTofu as an alternative to Terraform.
Read Full Article
19 Likes
Tech Radar
225

Image Credit: Tech Radar
Quordle hints and answers for Friday, July 11 (game #1264)
- Quordle game #1264 offers hints and answers for word game enthusiasts.
- Hints include vowel count, repeated letters, and starting letters of the answers.
- Answers for game #1264 are LAPEL, DRAIN, FROND, GROSS. Enjoy the challenge!
Read Full Article
13 Likes
Tech Radar
278
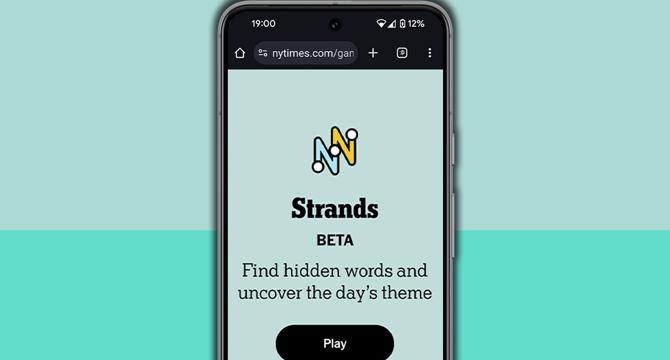
Image Credit: Tech Radar
NYT Strands hints and answers for Friday, July 11 (game #495)
- The New York Times' latest word game, Strands, released hints and answers for Friday, July 11 (game #495).
- Today's theme for NYT Strands was centered around poetry.
- The hints included words like SMILE, PILE, RACE, LACE, CHIP, and SLIP.
- The answers for game #495 were SONNET, LIMERICK, EPIC, ELEGY, HAIKU, BALLAD, ACROSTIC, with the spangram being POETRY.
Read Full Article
16 Likes
Dev
76

Image Credit: Dev
Cloud Cost Optimization: FinOps Best Practices
- Learn about FinOps for cloud cost management and optimization.
- Key practices include visibility, pricing optimization, culture shift, automation, and continuous improvement.
- Harness FinOps to empower teams, optimize commitments, foster cost awareness, automate, and iterate.
Read Full Article
4 Likes
Alvinashcraft
258

Dew Drop – July 10, 2025 (#4456)
- Microsoft's .NET MAUI Team leverages GitHub Copilot for enhanced productivity.
- A new Microsoft Learn Plan has been announced to prepare for organizations' AI workloads.
- Uno Platform introduces a new lightweight DataGrid.
- Discover India's Top Hotel Brands using .NET MAUI Lollipop Charts.
Read Full Article
15 Likes
Siliconangle
250

Image Credit: Siliconangle
Amplitude acquires Kraftful to enhance ‘Voice of Customer’ insights
- Amplitude Inc. has acquired Kraftful Inc., a 'Voice of Customer' startup, for an undisclosed price.
- Kraftful offers a platform using AI to understand and act on user feedback at scale from various channels like app store reviews, customer support tickets, etc., enabling teams to build what users need efficiently.
- Kraftful translates qualitative feedback into structured insights using AI, offering ways to analyze trends, complaints, sentiment, and feature requests with high accuracy.
- Amplitude plans to integrate Kraftful's capabilities to better analyze customer feedback, turning it into improved products; the Kraftful team will join Amplitude to embed Voice of Customer capabilities into its platform.
Read Full Article
15 Likes
Medium
157

Image Credit: Medium
10 Essential Terraform Commands Every Cloud Engineer Should Know
- Essential Terraform commands can empower cloud engineers by providing control over infrastructure deployment and management.
- Key commands include initializing the project, auto-formatting code, validating syntax, previewing changes, applying changes, and cleaning up resources.
- It is crucial to inspect the state, output values, skip confirmation prompts for automation, and use advanced functionalities like targeted resource updates and state file management.
- By leveraging these commands effectively, cloud engineers can ensure faster delivery, safer changes, and cleaner infrastructure management.
Read Full Article
9 Likes
Tech Radar
209
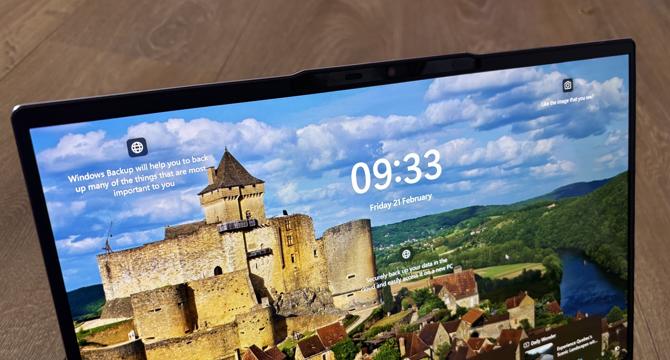
Image Credit: Tech Radar
If you haven't upgraded to Windows 11 24H2 yet, Microsoft's giving you a good reason to do so - better security
- Microsoft has improved security in Windows 11 24H2 by updating the scripting engine from JScript runtime to JScript9Legacy.
- This move makes it harder for hackers to exploit vulnerabilities within the OS.
- The new scripting engine enhances performance and security by aligning with modern web standards and implementing stricter execution policies.
- Users on Windows 11 24H2 will experience heightened security without needing to take any action.
Read Full Article
12 Likes
Arduino
238

New AWS x Arduino Opta Workshop: Connect your PLC to the Cloud in just a few steps
- Arduino has collaborated with Amazon Web Services (AWS) to offer a workshop on building cloud-connected PLCs.
- Participants will learn how to securely provision an Opta device and connect it to AWS IoT Core.
- The workshop is beginner-friendly and aims to equip individuals with the skills for industrial IoT and cloud connectivity.
- No prior AWS experience is necessary, and attendees will need an Arduino Opta device, AWS Free Tier account, basic embedded knowledge, and curiosity to participate.
Read Full Article
14 Likes
For uninterrupted reading, download the app