Cloud News
Dev
247

Image Credit: Dev
🧒🐧 Linux for Kids: From Terminal Tetris to Bash Scripting – A Parent–Child Adventure
- A parent-child adventure with Linux, starting with Bastard Tetris on the command line.
- By playing games like Bastard Tetris, kids learn to use commands, understand apt install, and realize the potential of the terminal.
- Moving beyond gaming, kids can delve into Bash scripting by creating fun commands like ASCII art and messages.
- Through this journey, kids develop logic, creativity, and coding skills while exploring the Linux terminal as a playground for learning.
Read Full Article
14 Likes
Medium
375
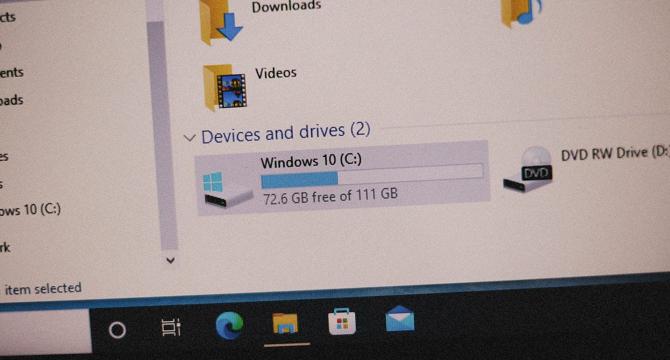
Image Credit: Medium
Still Saving Everything on Your Desktop? Here’s a Better Way
- Storing all files on your computer's desktop is dangerous, ineffective, and hampers productivity.
- Switching to cloud-based digital storage allows for easy access, sharing, and collaboration from any device.
- Cloud storage solutions are flexible, expandable, and offer features like search capabilities and customizable folders.
- Cloud services prioritize safe storage with encryption, access controls, and backups, making it a safer option than desktop storage.
Read Full Article
22 Likes
Siliconangle
146

Image Credit: Siliconangle
Rackspace’s operational turnaround accelerates, despite more revenue declines
- Rackspace Technology Inc. reported a third straight quarterly loss with revenue declines in major business segments, yet managed to improve its bottom line in the first quarter.
- The company exceeded analysts' expectations by reporting a loss of 6 cents per share and revenue of $655 million, down 4% from the previous year.
- CEO Amar Maletira highlighted meeting or beating Wall Street's targets for the 11th consecutive quarter, while expressing caution about the economy potentially affecting customer onboarding.
- Rackspace's strategic shift towards cloud consultancy resulted in operational improvements, reflected in an 83% increase in operating profit from a year ago. Investors responded positively with a 2% gain in extended trading.
Read Full Article
8 Likes
Siliconangle
206
Image Credit: Siliconangle
Appian shares rise on better-than-expected first quarter
- Appian Corp. shares rose over 5% after reporting better-than-expected revenue and earnings for the first quarter.
- Appian's sales increased by 11% to $166.4 million in the first quarter, mainly driven by the growth in its subscription segment.
- The company's platform enables automation of business tasks through visualization and automation workflows, leveraging tools like Data Fabric.
- Appian is focusing on monetizing AI capabilities, increasing profit margins, and enhancing sales efficiency to drive growth and profitability.
Read Full Article
12 Likes
Discover more
- Programming News
- Software News
- Web Design
- Devops News
- Open Source News
- Databases
- Product Management News
- Operating Systems News
- Agile Methodology News
- Computer Engineering
- Startup News
- Cryptocurrency News
- Technology News
- Blockchain News
- Data Science News
- AR News
- Apple News
- Cyber Security News
- Leadership News
- Gaming News
- Automobiles News
Tech Radar
100

Image Credit: Tech Radar
Apple will reportedly take on Ray-Ban Meta glasses in 2027
- Apple is reportedly developing a new chip to power smart glasses, expected to be ready by 2027.
- The upcoming smart glasses from Apple are likely to rival Ray-Ban Meta glasses.
- The company is also still working on a more advanced pair of smart glasses.
- Apple's focus on smart glasses with the new chip and potential competition with Meta suggests continued innovation in the wearables market.
Read Full Article
6 Likes
Digitaltrends
384

Image Credit: Digitaltrends
Epson EcoTank ET-2980 review: a quick, low-cost all-in-one printer for families
- The Epson EcoTank ET-2980 is a fast, efficient, and cost-effective inkjet tank printer, priced at $299.99.
- Pros of the EcoTank ET-2980 include three years of ink, fast document prints, good print quality, low cost per page, and an attractive design with an icy-blue tower light.
- Cons of the printer include frequent paper jams on duplex prints, inconsistent photo quality, and a tiny 1.4-inch display.
- The compact and appealing design of the ET-2980 features visible ink tanks with easy supply level monitoring and weighs just 11.5 pounds.
- The printer is equipped with PrecisionCore technology, allowing for fast print speeds of up to 15.5 ppm for black and 8 ppm for color prints.
- The EcoTank ET-2980 struggles with double-sided printing, often experiencing paper jams that necessitate manual intervention.
- The printer includes a high-resolution flatbed scanner with scanning capability ranging from 200 to 1200 dpi and supports color copying.
- Setting up the printer can be done through the Epson Smart Panel app, which streamlines the process of filling the large ink tanks provided.
- Despite some limitations like lacking an automatic document feeder (ADF), the ET-2980 offers great value with included ink lasting for thousands of pages.
- While competitors exist, the Epson EcoTank ET-2980 remains a solid choice for families seeking a reliable printer with low running costs.
- Overall, the EcoTank ET-2980 provides a good balance of speed, efficiency, and affordability, making it a practical option for various printing needs.
Read Full Article
23 Likes
Siliconangle
242

Image Credit: Siliconangle
AWS-Nutanix partnership pushes hybrid cloud to forefront of enterprise IT
- Hybrid cloud has become a current necessity for enterprise IT, with a focus on speed, scale, and seamless migration.
- A partnership between AWS and Nutanix is driving hybrid cloud strategies, enabling modernization, streamlined migrations, and support for emerging workloads like AI and containerized applications.
- Migrating to the cloud is considered a business imperative rather than a nice-to-have, with a vital importance on disaster recovery workloads, data center exits, and workload modernization.
- New product developments, like Nutanix's container-native platform, AOS, along with operational excellence and customer-centric design, underscore the collaborative efforts of AWS and Nutanix in guiding customers through infrastructure modernization and AI-driven architectures.
Read Full Article
14 Likes
Digitaltrends
435

Image Credit: Digitaltrends
Microsoft’s Surface Laptop 13 almost beat the MacBook Air. Here’s what it missed
- Microsoft introduced the 13-inch Surface Laptop and the 12-inch Surface Pro tablet to compete with Apple's offerings.
- The new Surface Laptop is thin, light, has a better port situation, and a competitive price compared to the MacBook Air.
- However, the Surface Laptop falls slightly short of being a better option despite the pricing advantage.
- It features a 60Hz LCD screen, missing out on higher refresh rate or OLED panels that could have set it apart.
- Both Microsoft and Apple receive criticism for limited storage options, with the Surface Laptop offering non-user-replaceable modules.
- Microsoft's choice of Snapdragon silicon limits user experience compared to the wider compatibility of Intel and AMD chips.
- The new design of the Surface Laptop loses the signature Surface identity, resembling the MacBook Air's aesthetics.
- Despite the changes, the Surface Laptop includes USB-C and USB-A ports, moving away from the magnetic connector.
- Microsoft may need to address internal issues to offer a more compelling choice against Apple's MacBook Air in future iterations.
Read Full Article
26 Likes
Hackernoon
242

Image Credit: Hackernoon
My First Steps With Crossplane: Crossplane 101
- In the early days of IT, manual server configuration was common, but became unscalable as infrastructures grew.
- Infrastructure-as-Code emerged to define machine states in text files, with tools like Chef, Puppet, and later Terraform.
- Terraform, a popular IaC tool, faced limitations like descriptive language constraints and lack of a central registry for automated drift correction.
- Introducing Crossplane, which leverages Kubernetes to address Terraform's shortcomings, allowing management of resources through a reconciling engine.
- Crossplane acts like an engine, managing various resources such as cloud services, Terraform, and more through configuration packages and providers.
- To start using Crossplane, one needs to install it using Helm and then set up providers like the GCP provider for managing resources like GKE clusters.
- Google authentication for Crossplane involves creating a secret for Service Account credentials and configuring Provider and ProviderConfig objects for project management.
- Creating a GKE cluster using Crossplane involves defining cluster specifications, referencing ProviderConfig, and writing connection secrets.
- You can monitor the GKE cluster creation progress using kubectl, access the cluster using the generated kubeconfig, and delete it by deleting the corresponding Cluster object.
- Crossplane's approach of using Kubernetes for resource management is highlighted in this article as a powerful tool with potential for further integrations and capabilities.
Read Full Article
14 Likes
Johndcook
293

Square root of a small number
- The recent post discusses an algorithm in quaternion and rotation matrices conversions.
- There is a risk of taking square root of a nearly negative number in floating point arithmetic.
- The post explores the need to handle cases where the argument for square root could be small or slightly negative.
- Authors suggest an alternative expression that is numerically less sensitive to avoid precision loss.
Read Full Article
17 Likes
Tech Radar
204

Image Credit: Tech Radar
Pinterest's new AI tools help you shop by visuals and vibes
- Pinterest has introduced new AI tools for visual search to explore fashion by vibe, mood, or aesthetic.
- Users can now click on highlighted outfit pieces in Pins to find similar items with descriptive terms provided by Pinterest.
- The AI tools aim to curate personalized shopping ideas using generative AI and Visual Language Models.
- Pinterest plans to expand these AI features beyond women's fashion, including a refinement bar for tweaking results and starting visual searches directly from the app.
Read Full Article
12 Likes
Tech Radar
238

Image Credit: Tech Radar
Meta's next smart glasses might have an always-on AI – I don't care how useful it is, I'm never turning it on
- Meta is reportedly working on glasses with always-on AI that can track users' every move.
- The glasses can recognize faces and remind users of things they forget, but existing models have insufficient battery life for this feature.
- Internally named Aperol and Bellini, the new glasses require a command phrase like “Hey Meta, start live AI” to activate the recording function.
- While the AI assistant could be useful, concerns about privacy and data collection have been raised by users and critics.
Read Full Article
14 Likes
Cloudwards
68

Image Credit: Cloudwards
How & Where to Watch French Ligue 1
- To watch French Ligue 1 matches in the US, viewers can use a VPN like NordVPN with a 30-day money-back guarantee to access live streams on services such as Fubo or YouTube TV.
- BeIN Sports is the primary channel for watching Ligue 1 in the US, providing live and exclusive coverage, with a free option available through BeIN Sports XTRA.
- For fans looking to watch Ligue 1 in other countries, various services like Fubo, DAZN, and Ligue 1 Pass offer coverage, with the need for a VPN to bypass geo-restrictions.
- Amazon Prime previously offered a Ligue 1 pass in France but now provides pay-per-view options for select matches including Ligue 1 games.
- The article also lists various VPN recommendations like NordVPN, Surfshark, and ExpressVPN for seamless streaming of Ligue 1 matches globally.
- The detailed TV schedule of the 2024-2025 Ligue 1 season is included, breaking down matches by date, teams, and results for each matchday.
- Viewers can use VPNs to access free streaming options like CazeTV on YouTube for Ligue 1 games, though reliability may vary due to geoblocking.
- The article concludes with FAQs about Ligue 1 streaming in the US, including methods to watch PSG matches and EFL League 1 in the country.
- Overall, the guide provides insights on where and how to watch Ligue 1 matches, emphasizing the use of VPNs to bypass geo-restrictions and access live streams globally.
- Fans are encouraged to use VPNs to access desired streaming services and enjoy watching their favorite Ligue 1 teams play, with a focus on ensuring reliable access to live matches.
Read Full Article
4 Likes
Silicon
109
Image Credit: Silicon
Google Partners Elementl Power To Develop Nuclear Projects
- Google is partnering with US-based Elementl Power LLC to develop nuclear power at three locations.
- Elementl Power will pre-position three project sites for advanced nuclear energy with the capital provided by Google.
- Google has been supporting sustainable energy for over a decade and has previously invested in solar farms and solar power plants.
- The partnership aims to accelerate the development of new safe, reliable, and affordable nuclear projects in the United States, with each project expected to generate at least 600 megawatts of power capacity.
Read Full Article
6 Likes
Tech Radar
169

Image Credit: Tech Radar
US lawmakers slam UK encryption backdoor order to Apple, warning against "systemic vulnerabilities"
- US lawmakers warn against UK encryption backdoor order to Apple, citing security risks for global users.
- UK requested Apple to create a backdoor for encryption, potentially compromising user data privacy.
- Apple removed end-to-end encryption feature from iCloud in the UK and is challenging the order in court.
- Lawmakers stress that backdoors in encryption could be exploited by cybercriminals and authoritarian regimes, posing risks to privacy worldwide.
Read Full Article
10 Likes
For uninterrupted reading, download the app