Cyber Security News
TechCrunch
173

Image Credit: TechCrunch
At TechCrunch Sessions: AI, Artemis Seaford and Ion Stoica confront the ethical crisis — when AI crosses the line
- Artemis Seaford and Ion Stoica will discuss the ethical challenges of today's AI at TechCrunch Sessions: AI on June 5 at UC Berkeley's Zellerbach Hall.
- Artemis Seaford focuses on AI safety efforts related to media authenticity and abuse prevention, while Ion Stoica specializes in building infrastructure for AI deployments.
- The session will address ethical blind spots in development cycles, embedding safety into core architectures, and the necessary roles of industry, academia, and regulation in the future of AI.
- TechCrunch Sessions: AI offers tactical insights, candid dialogues, and networking opportunities with key figures in the AI industry, with discounted tickets available for a limited time.
Read Full Article
10 Likes
Socprime
346
Image Credit: Socprime
IOC Query Generation for Microsoft Sentinel in Uncoder AI
- Uncoder AI automatically extracts malicious domains from threat reports used by adversaries for phishing and staging access to victim mailboxes.
- It generates Microsoft Sentinel search queries with the search operator to search across all logs ingested in Sentinel.
- The generated queries can be directly pasted into Microsoft Sentinel for threat hunting or investigation without manual formatting.
- Security teams can use this feature to identify phishing infrastructure connections, correlate endpoint behavior, and pivot from threat intel to detection efficiently.
Read Full Article
20 Likes
Tech Radar
442

Image Credit: Tech Radar
These dangerous fake Google Chrome extensions spoof VPNs and YouTube
- Security researchers discovered over 100 malicious browser extensions posing as legitimate tools, stealing sensitive user data and executing malicious code remotely.
- The extensions impersonated well-known products and businesses, including VPNs, AI assistants, and cryptocurrency utilities, posing a significant risk to users' security.
- Google Chrome Web Store was a distribution channel for these fake extensions, with Google removing some malware but some still posing a threat to users.
- Users are advised to only install browser extensions from trusted sources like the Chrome Web Store and remain cautious of potential malware hidden within seemingly legitimate tools.
Read Full Article
26 Likes
Socprime
428

Image Credit: Socprime
IOC-to-Query Generation for Google SecOps (Chronicle) in Uncoder AI
- Uncoder AI automates IOC extraction from threat reports, saving manual effort by parsing domains, URLs, IPs, hashes, and filenames.
- The tool generates Google SecOps-ready UDM queries using the extracted domains, facilitating tasks like hunting, rule-building, and investigation.
- Benefits include saving time, reducing errors with proper UDM field names, and enabling immediate actionable insights for security teams.
- Operational use cases include detecting phishing campaigns, monitoring traffic to attacker-controlled infrastructure, and responding to security incidents efficiently.
Read Full Article
25 Likes
Socprime
196

Image Credit: Socprime
AI-Driven IOC Conversion for Palo Alto Cortex XSIAM Queries
- Uncoder AI translates threat intelligence into Cortex XSIAM detection logic by ingesting structured IOCs and extracting relevant execution behaviors.
- Auto-generates Cortex XQL (XSIAM Query Language) detection logic targeting real-world execution patterns based on telemetry from winEventLog.
- Uncoder AI automates the creation of behavioral rules in Cortex XSIAM by recognizing execution syntaxes and correlating specific IOCs with known malware campaigns.
- Security teams using Cortex XSIAM benefit from accelerated rule creation, precision IOC-to-Telemetry mapping, and improved detection coverage with the help of Uncoder AI.
Read Full Article
11 Likes
Tech Radar
296

Image Credit: Tech Radar
Login and password details for Apple, Google and Meta accounts found in huge data breach of 184 million accounts
- Login credentials for Microsoft, Facebook, Snapchat, and other services were found in a public, non-password-protected database by security researcher Jeremiah Fowler.
- The database contained over 184 million unique logins and passwords, including email providers, Microsoft products, Facebook, Instagram, Snapchat, Roblox accounts, as well as credentials for bank, financial, health, and government accounts from various countries.
- The database's attribution was unclear due to private ownership information, and the hosting provider eventually restricted public access without revealing the owner's identity.
- The researcher suspected the data was harvested by malicious actors using infostealers to collect sensitive information, emphasizing the risks associated with storing sensitive data in email accounts.
Read Full Article
17 Likes
TechBullion
355

Image Credit: TechBullion
Sahiti Bommareddy’s Award-Winning Research Fortifies Critical Infrastructure Against Compound Threats
- Sahiti Bommareddy, a Ph.D. graduate from Johns Hopkins University, conducts award-winning research on critical infrastructure protection against compound threats.
- Her work focuses on system reliability, security, and fault tolerance in distributed computing, particularly in safeguarding vital services from cyber-physical threats.
- Bommareddy's research received the Best Paper Award at the International Symposium on Reliable Distributed Systems, showcasing her innovative approach to combating complex cyber-physical challenges.
- The award recognized her work on compound threats, a sophisticated type of cyberattack strategically launched during or after natural disasters, affecting critical infrastructure functionality.
- Bommareddy's research addresses Byzantine failures and incorporates machine learning for enhanced system reliability and intrusion detection, aiming to ensure continuity during cyberattacks.
- Her focus on practical implementations like Spire, an intrusion-tolerant SCADA system, demonstrates a commitment to real-world application of research findings.
- The award not only validated her research journey but also elevated the visibility of her work, fostering new collaborations and reinforcing the value of her research direction.
- Bommareddy's research introduces a novel threat model, compound threats, capturing the interplay of malicious cyber activity and system availability disruptions with significant implications for critical infrastructure resilience.
- Her work extends beyond defining threats to proposing a protocol designed to tolerate Byzantine faults and availability issues simultaneously, enhancing system safety and performance.
- The award-winning research bridges theoretical foundations with practical implications, emphasizing system behavior under real adversarial stress, particularly crucial for infrastructure domains like the power grid.
- Bommareddy's dedication to developing systems that rarely fail under adversarial conditions showcases her commitment to advancing resilient and secure distributed systems within critical infrastructure.
Read Full Article
21 Likes
TechBullion
322

Image Credit: TechBullion
AI Innovations Transforming Financial Fraud Detection
- Srinath Reddy Palla explores how AI is revolutionizing security protocols in the financial services sector to combat fraud amid increasing cyber threats.
- AI-driven security solutions are dynamic and proactive, offering real-time risk profiles that adapt to evolving customer behavior to counter sophisticated fraud tactics effectively.
- Behavioral analytics monitors hundreds of indicators to detect potential fraud with over 90% accuracy, supporting continuous authentication and enhancing security without compromising user experience.
- NLP applications, cloud-based monitoring systems, and AI-driven security frameworks significantly boost fraud prevention in financial services, albeit with challenges such as model explainability and privacy preservation.
Read Full Article
19 Likes
Dev
273

Image Credit: Dev
What If Web3 Was A Country?
- Web3 Nation is a hypothetical decentralized country where smart contracts are law and cryptocurrencies are the main currency.
- The constitution of Web3 Nation is written in Solidity, corruption-free, and immutable, with all decisions executed based on smart contracts.
- Immigration in Web3 Nation is permissionless and instant, with no visas required, and new citizens receiving airdropped basic income.
- Government in Web3 Nation is run by DAOs governing various sectors, with citizens voting through tokens, and infrastructure being tokenized and transparent.
Read Full Article
16 Likes
Hackernoon
132

Image Credit: Hackernoon
NexChain Presale: It’s Time to Go Security First
- June sees a rise in crypto presales due to global regulatory actions targeting illicit activities, raising awareness of compliance and reliability in the cryptocurrency industry.
- Nexchain emerges as a top crypto presale for security-conscious investors in 2025, emphasizing security, transparency, and regulatory compliance.
- Nexchain undergoes a Certik audit, implements anti-whale measures, and offers gas fee revenue sharing to enhance safety and investor benefits.
- With G7's crackdown on illicit blockchain activities, demand grows for trusted crypto presales like Nexchain, known for compliance, transparency, and simplicity in user experience.
Read Full Article
7 Likes
Global Fintech Series
273

Image Credit: Global Fintech Series
Integrating AML Surveillance with Real-Time Payment Systems at Scale
- Financial institutions are facing increased pressure to maintain robust AML surveillance as real-time payments become more prevalent.
- Traditional AML systems are inadequate for real-time payment environments due to latency issues, scalability limitations, and lack of contextual awareness.
- To address these challenges, institutions are adopting event-driven architectures with real-time risk scoring engines, dynamic rule engines, and ML-driven anomaly detection.
- Hybrid human-AI decisioning models are being used to improve detection precision and operational efficiency in AML systems integrated with real-time payment systems.
Read Full Article
16 Likes
TechDigest
4

Image Credit: TechDigest
How biometric authentication is helping prevent cybercrime in 2025
- Cybercrime has been on the rise, impacting millions of individuals and businesses, leading to financial losses and reputational damage.
- Biometric technology is evolving to enhance digital security and protect personal information in various industries.
- Biometrics offer stronger authentication, making it harder for cybercriminals to access valid accounts.
- Unique traits used in biometric authentication make it difficult for cyber attackers to generate or replicate, enhancing security.
- Biometrics simplify the enrollment process for users, making it convenient and enhancing account security.
- Forms of biometric authentication include facial recognition, fingerprint scanning, voice recognition, iris recognition, and hand scanning.
- The future of biometric technology involves concerns about criminals bypassing authentication methods and the need for improved algorithms.
- Biometric authentication systems are effective in combating cybercrime but may require additional security measures like multi-factor authentication.
- Physical tampering is a concern with biometrics, and enhancing reliability is crucial to prevent both impostor acceptance and false rejection.
- Overall, biometric authentication is a practical solution to cybercrime threats, serving as a long-term defense for digital security.
Read Full Article
Like
Securityaffairs
22
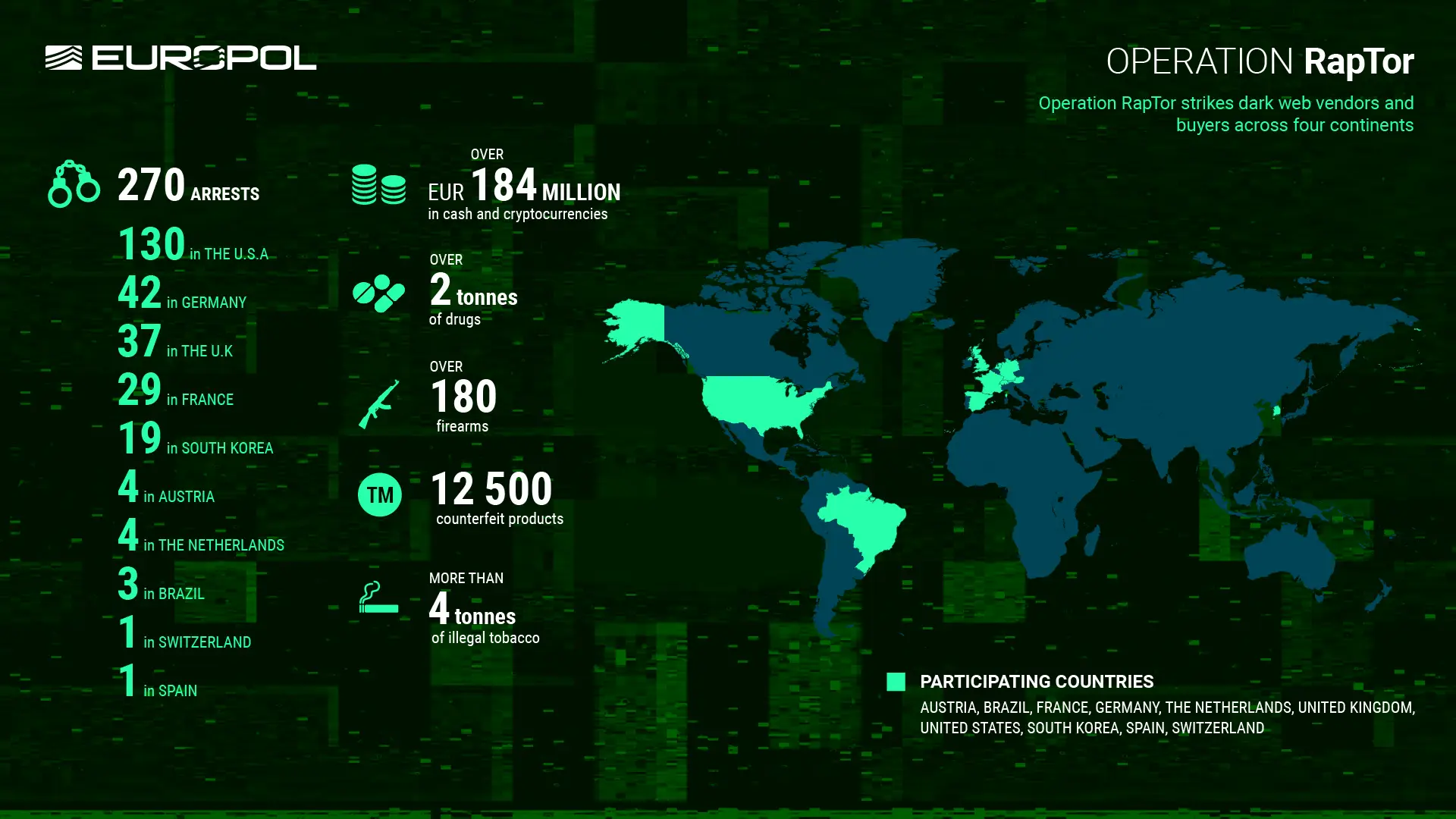
Image Credit: Securityaffairs
Operation RapTor led to the arrest of 270 dark web vendors and buyers
- Operation RapTor led to the arrest of 270 dark web vendors and buyers across 10 countries.
- The operation dismantled networks involved in trafficking drugs, weapons, and counterfeit goods.
- Europol supported the action by sharing intelligence packages with national authorities for targeted investigations.
- Authorities seized over €184M in cash and crypto, 2+ tonnes of drugs, 180+ firearms, 12,500 counterfeit items, and 4+ tonnes of illegal tobacco, striking a major blow to dark web criminal networks.
Read Full Article
1 Like
Medium
264

Image Credit: Medium
The Rising Tide of Online Content Restrictions Worldwide
- Online content restrictions are increasing globally, extending beyond nations with restrictive governance models.
- Censorship infrastructure relies on advanced technologies like AI algorithms and machine learning for real-time content monitoring.
- Traditional circumvention methods like basic VPN services are inadequate against these advanced detection systems.
- Adopting next-generation protocols like VLESS is crucial for maintaining online freedom and overcoming digital restrictions.
Read Full Article
15 Likes
Cybersafe
438

Image Credit: Cybersafe
Chinese Hackers exploit Trimble Cityworks flaw to infiltrate U.S. Local Government Systems
- Chinese state-linked threat group UAT-6382 exploited a deserialization vulnerability in Trimble Cityworks software to compromise U.S. local government networks.
- The vulnerability, CVE-2025-0994, despite being patched, has been leveraged since January by UAT-6382 to breach municipal systems and deploy Chinese-language web shells and custom malware focused on utility networks.
- UAT-6382 used tools like AntSword, Chopper, Behinder, and a Rust-based malware loader named TetraLoader to maintain access, steal sensitive files, and implant backdoors across compromised environments.
- Indicators of compromise (IOCs) have been released by Cisco Talos to help organizations detect and defend against similar intrusions, highlighting the threat posed by APTs targeting critical infrastructure through known vulnerabilities.
Read Full Article
26 Likes
For uninterrupted reading, download the app