Cyber Security News
Siliconangle
169

Image Credit: Siliconangle
Cybersecurity researcher discovers database with millions of login credentials
- A cybersecurity researcher discovered an exposed Elasticsearch database with millions of login credentials on May 6.
- The database contained 184 million records taking up 47 gigabytes of storage space, with login credentials associated with millions of accounts from various services like Google, Facebook, Roblox, Discord, and others.
- There were 220 email addresses with .gov domains linked to government agencies in at least 29 countries, including the U.S., UK, and Australia.
- The database was hosted on infrastructure operated by World Host Group, a U.K.-based hosting provider, which took it down after being notified by the researcher.
Read Full Article
10 Likes
Livebitcoinnews
50

Image Credit: Livebitcoinnews
Coinbase Insider Attack Exposes Data of 69K Users
- 69K plus consumers’ data exposed in a Coinbase breach where hackers bribed overseas support staff to steal customer information.
- Data breach exposed personal information of users but no passwords or funds were compromised; Coinbase Prime users were unaffected.
- Hackers obtained names, email addresses, addresses, phone numbers, government IDs, and transaction data, leading to an extortion request of $20 million.
- Coinbase took steps to help affected users, including reimbursement for social-engineering attack losses, offering identity protection, and enhancing security measures.
Read Full Article
3 Likes
BGR
232

Image Credit: BGR
184 million logins exposed in ‘dream come true for cyber criminals’
- Cybersecurity researcher Jeremiah Fowler discovered a publicly exposed database containing 184,162,718 unique logins and passwords, amounting to over 47GB of data.
- The database included emails, usernames, passwords, and more for services like Microsoft, Meta, Snapchat, and Roblox, as well as logins for bank accounts, health platforms, and government portals from multiple countries.
- Fowler sent a responsible disclosure notice to the hosting provider as he couldn't verify the owner's identity, which led to the database being restricted from public access.
- The leaked data was confirmed authentic by contacting email addresses listed, with concerns that it might have been gathered by infostealer malware, emphasizing the need for users to delete old emails containing sensitive information.
Read Full Article
13 Likes
TechBullion
291

Image Credit: TechBullion
T7X Strengthens Its Cybersecurity Framework with the Appointment of Sydney Truong as CTO
- Sydney Truong has been appointed as the new Chief Technology Officer at T7X to enhance the company's technology infrastructure and cybersecurity capabilities.
- Truong's expertise in cybersecurity and leadership in digital transformation will fortify T7X's digital framework and align technology strategy with long-term business goals.
- With over a decade of experience in IT leadership, Truong's focus will be on implementing advanced cybersecurity protocols and fortifying the company's technical posture at T7X.
- Pablo Penaloza, CEO of T7X, expresses confidence in Truong's leadership to elevate system security and operational efficiency, reinforcing T7X as a trusted leader in the digital services sector.
Read Full Article
17 Likes
Dataprivacyandsecurityinsider
411

College Student Behind Cyber Extortions
- Matthew D. Lane, a 19-year-old student at Assumption University, has been charged with cyber extortion conspiracy and unauthorized access to protected computers.
- Lane conspired to extort $200,000 from a telecommunications company and threatened to release data of more than 60 million students and 10 million teachers if they did not pay a ransom of approximately $2.85 million in Bitcoin.
- If convicted, Lane could face up to five years in prison for cyber extortion charges, three years of supervised release, and a fine of up to $250,000.
- The charge of aggravated identity theft carries a mandatory two-year sentence in prison, consecutive to any other imposed sentence on the computer fraud charges.
Read Full Article
24 Likes
TechCrunch
118
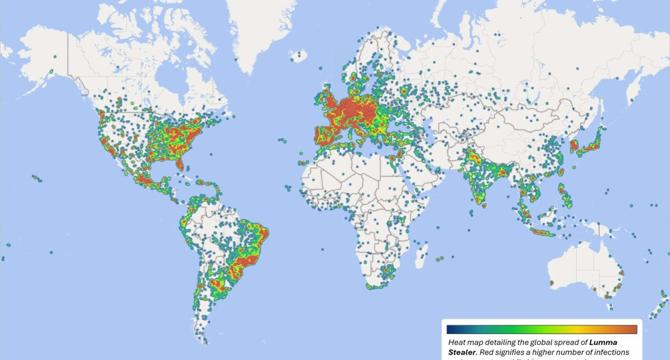
Image Credit: TechCrunch
Microsoft says Lumma password stealer malware found on 394,000 Windows PCs
- Microsoft and law enforcement conducted a court-authorized takedown of Lumma, an info-stealer malware operation found on over 394,000 Windows PCs worldwide, mainly in Brazil, Europe, and the United States.
- Civil action was taken by Microsoft to seize 2,300 domains serving as the malware's command and control servers, while the Justice Department seized five domains linked to the Lumma infrastructure.
- Lumma password stealer is typically hidden in illegitimate games or cracked applications downloaded online, stealing logins, passwords, credit cards, and cryptocurrency wallets to sell to other hackers. It can also provide a backdoor for further malware installation like ransomware.
- Such password-stealing malware, including Lumma, has been associated with cyberattacks targeting tech firms like PowerSchool and Snowflake, resulting in substantial data theft.
Read Full Article
7 Likes
Medium
447

Googled Myself. Found My Address. Here’s What I Did.
- Google can remove personal, sensitive information such as addresses, phone numbers, and financial details to protect individuals from scams, identity theft, and harassment.
- To request removal from Google, users can use the Content Removal Tool by selecting the type of content, submitting URLs, and explaining why the information is harmful.
- If Google does not remove the content, Aardvark Online Removals offers assistance in permanently eliminating harmful or unwanted content from the internet.
- Aardvark Online Removals provides discreet support and follows a pay-for-success model, ensuring clients only pay if the removal is successful.
Read Full Article
26 Likes
Hackernoon
224

Image Credit: Hackernoon
INE Security Partners With Abadnet Institute For Cybersecurity Training Programs In Saudi Arabia
- INE Security partners with Abadnet Institute for cybersecurity training programs in Saudi Arabia.
- The collaboration aims to deliver comprehensive cybersecurity education programs in the region by leveraging INE Security's training content and Abadnet's established presence.
- Abadnet Institute serves over 10,000 learners annually and offers internationally accredited programs in IT, Cybersecurity, and Networking training.
- The partnership includes launching specialized bootcamps with cybersecurity certification preparation, supporting learners in developing practical skills in penetration testing and ethical hacking.
Read Full Article
13 Likes
Hackernoon
305

Image Credit: Hackernoon
ThreatBook Named a Notable Vendor In Global Network Analysis And Visibility (NAV) Independent Report
- ThreatBook, a global leader in cyber threat and response solutions, has been recognized as a notable vendor in Forrester's Network Analysis And Visibility Solutions Landscape, Q2 2025 report.
- The recognition highlights ThreatBook's technical excellence and market performance in providing real-time security insights across various environments.
- Key features of ThreatBook's Threat Detection Platform (TDP) include bidirectional full traffic analysis, low false positive rate, integrated threat intelligence, and automated incident response.
- ThreatBook's mission is to offer high-accuracy detection, deep visibility, and efficient response to combat complex cyber threats, with a focus on enterprise-scale operations.
Read Full Article
18 Likes
VentureBeat
374

Image Credit: VentureBeat
Anthropic overtakes OpenAI: Claude Opus 4 codes seven hours nonstop, sets record SWE-Bench score and reshapes enterprise AI
- Anthropic released Claude Opus 4 and Claude Sonnet 4, showcasing AI's extended focus and collaboration capabilities in software engineering projects.
- Claude Opus 4 performed a seven-hour session on a complex refactoring project, achieving a 72.5% score on the SWE-Bench, surpassing OpenAI's GPT-4.1.
- The rise of reasoning models in 2025 signals a shift in how AI is utilized, with Anthropic's Claude models integrating tool use directly into their reasoning process.
- Anthropic's dual-mode functionality offers instant responses for simple queries and deeper analysis for complex tasks, addressing user experience friction points.
- Claude 4 models excel in memory persistence, maintaining knowledge across sessions and organizing information for optimized retrieval, enhancing problem-solving capabilities.
- The competitive AI landscape sees Anthropic challenging industry leaders with its sustained performance and professional coding applications in the enterprise sector.
- Anthropic's Claude Code integration into development workflows, GitHub Copilot partnership, and API capabilities cater to developers, marking strategic advancements.
- As AI models like Claude Opus 4 showcase extended autonomy and improved memory, the industry grapples with the challenges of transparency and oversight in AI reasoning processes.
- The evolving role of AI in knowledge work indicates a future where AI systems operate as collaborators, capable of complex tasks with minimal human intervention.
- The organizational and economic impacts of AI's enhanced capabilities, exemplified by Claude 4, are reshaping how organizations approach tasks traditionally requiring human attention.
- The workplace transformation brought by AI's advancements emphasizes the need for adaptation to a future where digital teammates may rival or surpass human productivity.
Read Full Article
22 Likes
Tech Radar
191

Image Credit: Tech Radar
Delta's lawsuit against CrowdStrike to go ahead after okay from Judge
- Delta's lawsuit against cybersecurity company CrowdStrike, due to a faulty update disrupting operations, has been given the go-ahead by a judge.
- Last year, CrowdStrike's faulty update caused disruptions for various companies including Delta, leading to extended recovery times and more grounded airplanes for Delta compared to its competitors.
- Delta sued CrowdStrike for deploying the update without permission and failing to adequately test it before release, resulting in claims of breach of contract, trespass, negligence, and fraud.
- The judge has partially denied CrowdStrike's motion to dismiss, with trespass and negligence claims deemed valid, while fraud claims were upheld in part, potentially leading to CrowdStrike having to pay 'single-digit millions' to Delta.
Read Full Article
11 Likes
Silicon
424
Image Credit: Silicon
EU Sanctions Entities, Individuals Amid Russian Hybrid Threats
- The European Union has implemented sanctions against individuals and entities engaged in Russian hybrid operations and destabilizing activities.
- 21 individuals, including politicians and military personnel, as well as six entities, such as fishing companies and news agencies, are now subject to EU restrictive measures and sanctions.
- The Council of the European Union has expanded the scope of sanctions to target tangible assets related to Russia's destabilizing activities, including vessels, aircraft, real estate, and digital communication networks.
- Sanctioned individuals and entities are accused of engaging in activities like undersea cable sabotage, media manipulation, spreading propaganda, and disrupting civil aviation.
Read Full Article
25 Likes
Arstechnica
50

Image Credit: Arstechnica
Authorities carry out global takedown of infostealer used by cybercriminals
- Global law enforcement agencies and tech companies disrupted the infostealer malware Lumma, developed in Russia.
- Lumma has been widely used by cybercriminals to steal sensitive information like passwords, credit card details, and cryptocurrency wallet information.
- Microsoft's Digital Crimes Unit seized 2,300 domains associated with Lumma and the US Department of Justice seized its command and control infrastructure.
- Europol's European Cybercrime Center and Japan's Cybercrime Control Center also participated in disrupting regional Lumma infrastructure to combat cybercriminal activities.
Read Full Article
3 Likes
BGR
273

Image Credit: BGR
Chrome will change compromised passwords for you automatically
- Hackers continue to target passwords, putting everyone at risk of data breaches.
- Password managers and browsers can now track compromised passwords and alert users.
- Google's Chrome browser will automate the process of changing compromised passwords.
- This feature aims to simplify the task of updating passwords, making it more convenient for users.
Read Full Article
16 Likes
Kaspersky
4

Image Credit: Kaspersky
A Kaspersky checklist for a safe vacation | Kaspersky official blog
- The average user spends around 2.5 months of a year on their smartphone, highlighting the significant role of mobile devices in our lives.
- Digital detoxes can improve sleep quality, reduce anxiety, stress, and phone addiction, and enhance the brain's ability to focus and process information deeply.
- While taking a break from screens is beneficial for mental health, it can pose cybersecurity risks such as account theft, unauthorized subscriptions, and personal data leaks.
- To ensure security during a digital detox, strengthen passwords, enable two-factor authentication, make backups, and notify your bank of travel plans.
- Install security updates, protect devices with reliable security software, and safeguard SIM cards from being swapped to minimize cybersecurity risks while on vacation.
- Designate trusted contacts for digital legacy access, secure IoT devices, and establish backup communication channels for personal safety during a digital detox.
- Minimize gadget use on vacation by limiting access to distracting apps, avoiding risky connections, and storing devices securely.
- After returning from a digital detox, check for updates, review notifications and logs for any suspicious activity, and assess the resilience of your digital ecosystem.
- Reflect on the experience and make necessary amendments to improve security measures for future digital detox vacations.
- Following these tips can help ensure a smooth and secure digital-detox vacation, allowing you to enjoy your time offline without compromising your cybersecurity.
Read Full Article
Like
For uninterrupted reading, download the app