Cyber Security News
Cybersafe
118

Image Credit: Cybersafe
U.S. Dismantles DanaBot Malware Network in major Global cybercrime bust
- The U.S. Department of Justice (DoJ) announced the dismantling of the DanaBot malware infrastructure and indicted 16 individuals for running a global malware-as-a-service (MaaS) operation causing over $50 million in damages.
- Operation Endgame, targeting DanaBot, led to the seizure of its command-and-control servers, with the malware infecting over 300,000 devices globally through spam emails.
- DanaBot evolved from a banking trojan into a multifunctional platform involving credential theft, keylogging, video capture, and ransomware facilitation, attracting cybercriminal affiliates through monthly fees.
- The takedown reflects a broader crackdown on cybercrime, with private sector collaboration playing a key role in disrupting criminal operations and increasing challenges for cybercriminals to operate freely.
Read Full Article
7 Likes
VentureBeat
22

Image Credit: VentureBeat
PlaySafe ID raises $1.12M to bring trust and fairness to gaming communities
- PlaySafe ID, a platform aiming to bring trust and fairness to gaming communities by keeping cheaters and predators out, secured $1.12 million in pre-seed funding.
- The funding round was led by Early Game Ventures, with participation from Hartmann Capital and Overwolf, to support rapid expansion and strategic platform integrations.
- PlaySafe ID issues verified, anonymous digital IDs that affirm users are real and have not engaged in cheating or inappropriate behavior in games, addressing key issues in online gaming.
- The platform enables developers and communities to enforce fair play across games without compromising player anonymity or creative freedom.
- PlaySafe ID is in talks with major gaming platforms for integration and plans to launch partnerships later this year to revolutionize gaming safety.
- The founder, Andrew Wailes, drew inspiration from his love for gaming and the need to combat cheating and child grooming issues in online gaming environments.
- PlaySafe ID operates by users claiming a single, verified PlaySafe ID powered by Onfido, with strict verification processes while ensuring user privacy.
- Developers notify PlaySafe ID of violations, prompting penalties like bans for cheating, botting, or inappropriate behavior, ensuring fair play across games.
- To protect user accounts, PlaySafe ID implements security features like temporary suspensions for suspicious activities, handled by Onfido.
- The platform aims to establish a trust layer for gaming and beyond, setting the foundation for a more secure and fair gaming environment globally.
Read Full Article
1 Like
TechBullion
141

Image Credit: TechBullion
Take Back Your Online Freedom with StarVPN
- StarVPN is a privacy-first technology company aiming to help users access the internet freely, securely, and without being tracked.
- Founded out of concern over digital freedom, the team behind StarVPN prioritizes speed, simplicity, and security, distinguishing itself from competitors.
- StarVPN stands out for not requiring a login, being ad-free, keeping zero logs, and working seamlessly in restricted regions.
- With a focus on user-friendliness and online security, StarVPN offers easy global connectivity and advanced encryption protocols, making it a valuable tool for internet freedom.
Read Full Article
8 Likes
Securityaffairs
223

Image Credit: Securityaffairs
Chinese threat actors exploited Trimble Cityworks flaw to breach U.S. local government networks
- Chinese threat actor UAT-6382 exploited a patched Trimble Cityworks flaw to deploy Cobalt Strike and VShell.
- The CVE-2025-0994 vulnerability in Trimble Cityworks allowed remote code execution, with a CVSS v4 score of 8.6.
- UAT-6382 breached U.S. local government networks using this vulnerability since January 2025, deploying Chinese-language web shells and custom malware.
- Talos researchers identified UAT-6382 utilizing Rust-based loaders named TetraLoader, connecting to specific domains and IPs for malicious activities.
Read Full Article
13 Likes
Medium
182
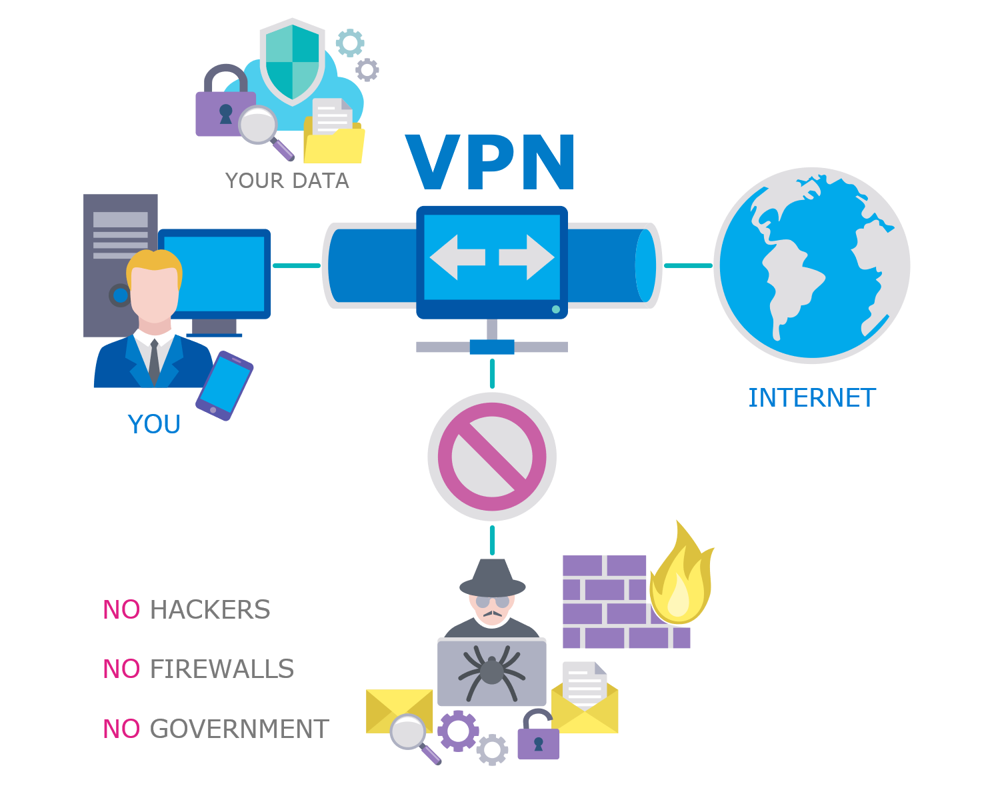
Image Credit: Medium
What Is a VPN and How It Works and 7 Powers Tips for Security in 2025
- VPNs use tunneling protocols and encryption to secure data by creating a secure tunnel to the VPN server.
- When connected to a VPN, data is encrypted and encapsulated, making it indecipherable to eavesdroppers on public Wi-Fi.
- Using a VPN hides your real IP address, masking your true location and identity to protect your privacy online.
- To ensure maximum privacy and security, it is important to choose a reputable VPN service and follow best practices like using up-to-date protocols and testing for leaks.
Read Full Article
10 Likes
Medium
451

Image Credit: Medium
The Tech Ecosystem: A Living Network
- The tech ecosystem thrives on interconnection, with APIs bridging systems, cross-chain protocols connecting blockchains, and communities sharing knowledge.
- Success in this environment requires vision, curiosity, and adaptation, where creativity, empathy, and collaboration are as important as technical skills.
- Innovation goes beyond coding to encompass problem-solving, system thinking, and understanding the broader impact of each line of code.
- Thriving in the tech ecosystem involves embracing complexity, contributing to growth, and being open to continuous learning and evolution amidst exponential technological growth.
Read Full Article
27 Likes
TronWeekly
63

Image Credit: TronWeekly
Coinbase Hacker Resurfaces with $42M BTC Transfer and Troll Comment to ZachXBT
- Coinbase hacker resurfaced in the crypto space by transferring $42 million worth of Bitcoin and trolling ZachXBT with a meme video and a mocking message 'L bozo'.
- Reports suggest the total loss amount from the Coinbase hack is estimated between $180 million and $400 million. It was revealed that the hacker swapped about 17,800 ETH for approximately $44.94 million in DAI using THORChain.
- The hacker's trolling message to ZachXBT via the Ethereum blockchain input data occurred ten days after Coinbase disclosed a security issue affecting over 69,000 user accounts, linking a meme video of NBA legend James Worthy smoking a cigar.
- ZachXBT highlighted that the same person or group behind the recent Coinbase breach exposing users' private information is likely connected to this incident. Additionally, previous reports indicated that Coinbase users lose around $300 million annually to social engineering scams.
Read Full Article
3 Likes
The Register
387

Image Credit: The Register
How lean security teams can build resilient defenses
- Security teams with limited budgets and resources face challenges in defending against advanced threats.
- Despite being understaffed, security teams are expected to handle compliance, vendor management, and emerging threats.
- Maximizing existing resources including tools like EDR, vulnerability management, and email security is crucial.
- Continuous control monitoring helps ensure foundational security practices are in place and operational.
- Lean teams need to prioritize continuous threat exposure management to evaluate if defenses can handle real-world threats.
- Implementing these methodologies can help small teams stay ahead of security gaps and operate with confidence.
- Challenges for lean teams include juggling multiple tools, manual effort overload, and lack of dedicated personnel.
- Tools like those offered by Prelude aim to simplify continuous monitoring and exposure management for security teams.
- By focusing on foundational security practices and leveraging existing tools, smaller security teams can achieve resilient defenses.
- Continuous control monitoring and exposure management provide efficient strategies for lean security teams to enhance their security posture.
Read Full Article
23 Likes
Securityaffairs
419

Image Credit: Securityaffairs
U.S. CISA adds a Samsung MagicINFO 9 Server flaw to its Known Exploited Vulnerabilities catalog
- The U.S. Cybersecurity and Infrastructure Security Agency (CISA) added a Samsung MagicINFO 9 Server vulnerability, tracked as CVE-2025-4632 (CVSS score of 9.8), to its Known Exploited Vulnerabilities (KEV) catalog.
- The vulnerability is an improper limitation of a pathname to a restricted directory vulnerability that impacts Samsung MagicINFO 9 Server version before 21.1052, allowing attackers to write arbitrary files as system authority.
- CISA issued Binding Operational Directive (BOD) 22-01 to address identified vulnerabilities by June 12, 2025, for Federal Civilian Executive Branch (FCEB) agencies, urging private organizations to review the Catalog and address vulnerabilities in their infrastructure.
- This week, CISA also added Ivanti EPMM, MDaemon Email Server, Srimax Output Messenger, Zimbra Collaboration, and ZKTeco BioTime flaws to its Known Exploited Vulnerabilities catalog.
Read Full Article
25 Likes
Medium
36

Image Credit: Medium
How to Stop Cyberbullying Before it Happens
- Cyberbullying is a growing concern as children increasingly engage in digital communication and socialization.
- Cyberbullying involves bullying through digital devices and platforms, such as texts, social media, and online forums.
- There has been a 70% increase in cyberbullying and hate speech among teens and children since the COVID-19 lockdown began.
- Parents can take preventative measures to address cyberbullying, although it is crucial to acknowledge that no approach is entirely foolproof.
Read Full Article
2 Likes
Medium
68

Image Credit: Medium
The Pros and Cons of Sharing Your Online Passwords
- Sharing online passwords can lead to various forms of online scams and threats, as well as vulnerability of personal information.
- Kids may not understand the importance of keeping passwords safe, leading to potential risks and dangers.
- The only acceptable pro of sharing a password is between concerned parents and young children to prevent harmful interactions.
- Sharing passwords with anyone other than a trusted party should be discouraged to maintain online security.
Read Full Article
4 Likes
Lastwatchdog
237

News Alert: Halo Security reaches SOC 2 milestone, validating its security controls and practices
- Halo Security has achieved SOC 2 Type 1 compliance after an audit by Insight Assurance, validating its security controls and practices.
- The certification confirms that Halo Security's security controls are properly designed to meet SOC 2 trust principles.
- SOC 2 compliance ensures that customer data is protected, security processes are implemented, and access to systems is governed by defined policies.
- Halo Security is now aiming for SOC 2 Type 2 compliance to further verify the operational effectiveness of its security controls.
Read Full Article
14 Likes
Lastwatchdog
355

News alert: INE Security, Abadnet Institute partner to deliver cybersecurity training in Saudi Arabia
- INE Security partners with Abadnet Institute for Training in Saudi Arabia to deliver cybersecurity education programs.
- The partnership combines INE Security's cybersecurity training content with Abadnet's presence in the Saudi Arabian market.
- This collaboration supports skill development in penetration testing and ethical hacking, aiming to meet the high demand in the region.
- The partnership marks INE Security’s strategic investment to enhance the digital employment ecosystem and nurture skilled cybersecurity professionals in Saudi Arabia.
Read Full Article
21 Likes
TechJuice
369

Image Credit: TechJuice
Firefox and Chrome Vulnerable to Cyber Threats, NCERT Warns
- NCERT issues urgent advisory warning of serious vulnerabilities in latest versions of Firefox and Chrome browsers.
- Firefox vulnerabilities showcased at Pwn2Own contest; Chrome's WebAssembly flaw poses significant risk.
- Several critical zero-day vulnerabilities reported with active exploitation, allowing attackers to execute arbitrary code and deploy malware.
- Users and organizations advised to apply available patches and take immediate mitigation measures to prevent cyber threats.
Read Full Article
22 Likes
Wired
278

Image Credit: Wired
Feds Charge 16 Russians Allegedly Tied to Botnets Used in Ransomware, Cyberattacks, and Spying
- The US Department of Justice has indicted 16 Russian nationals in connection with a malware operation known as DanaBot, which infected at least 300,000 machines worldwide.
- The operation allegedly involved activities ranging from ransomware attacks to cyber espionage against military and government targets.
- In addition to for-profit criminal hacking, DanaBot was used in espionage against military, government, and NGO targets.
- The malware initially functioned as a banking trojan but evolved to be used for various criminal activities, including ransomware and espionage.
- DanaBot was sold in an 'affiliate' model to hacker groups and was later used in a software supply chain attack affecting financial services, transportation, and technology sectors.
- The malware was also used in state-sponsored hacking campaigns and espionage operations targeting Western government officials and Ukrainian entities.
- Despite the takedown, the operators of DanaBot remain at large, highlighting the evolving landscape of cybercrime involving Russian state hackers.
- The disruption of DanaBot represents a significant milestone in combating Russian-origin hacking, impacting their monetization and creating disruption in their operations.
- The overlap between cybercriminal operators and Russian government entities is highlighted by DanaBot, showcasing the intersection of e-crime tooling and espionage purposes.
- The case of DanaBot illustrates the blurred lines between cybercrime, state-sponsored cyberwarfare, and espionage within the Russian hacker ecosystem.
Read Full Article
16 Likes
For uninterrupted reading, download the app