Cyber Security News
Securityaffairs
301
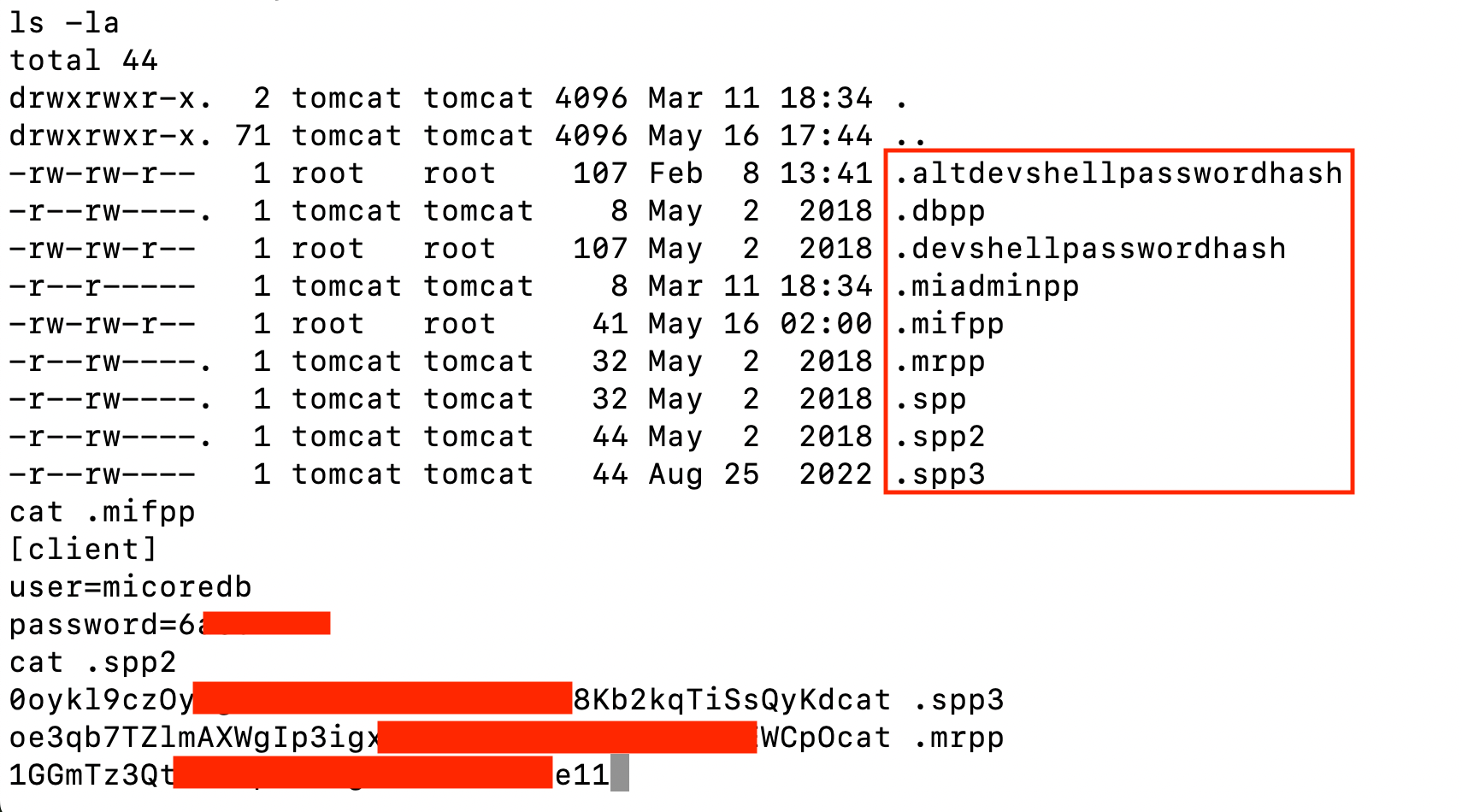
Image Credit: Securityaffairs
China-linked APT UNC5221 started exploiting Ivanti EPMM flaws shortly after their disclosure
- China-linked APT group exploits two Ivanti EPMM flaws, CVE-2025-4427 and CVE-2025-4428, to target organizations in Europe, North America, and Asia-Pacific.
- The flaws include an authentication bypass and a remote code execution vulnerability, allowing attackers to access protected resources and execute arbitrary code.
- Ivanti has released updates addressing the vulnerabilities after threat actors actively exploited them to achieve remote code execution without authentication.
- The attacks are linked to China-linked group UNC5221, which targeted critical sectors and used techniques like Java Reflection and KrustyLoader malware for espionage campaigns.
Read Full Article
18 Likes
TronWeekly
127

Image Credit: TronWeekly
Industry Leaders Challenge SEC Cyber Risk Management Disclosure Rule
- Leading U.S. financial associations petition the SEC to revise cybersecurity incident disclosure rules.
- They argue that premature disclosure mandates are harmful and counterproductive.
- The coalition suggests that existing disclosure frameworks already offer investor protection without increasing systemic risk.
- The petition asserts that transparency during ongoing incident investigations poses challenges and cybersecurity risks.
Read Full Article
7 Likes
Dev
127

Image Credit: Dev
A Comprehensive Guide to Application Security: Types, Benefits, Tools and Techniques
- Application security is vital in today's interconnected landscape, focusing on identifying and fixing vulnerabilities to prevent unauthorized access.
- It spans from development to deployment and includes securing all layers of the application stack.
- Implementing security measures early in the software development lifecycle is crucial, starting from design and development phases.
- Prioritizing strong authentication and deploying security infrastructure like firewalls are essential practices.
- Protecting sensitive data, maintaining business continuity, and adhering to regulatory requirements are key benefits of application security.
- Neglecting application security can lead to unauthorized data access, financial losses, reputational damage, and operational disruptions.
- Common application security threats include injection attacks, broken authentication, security misconfiguration, and sensitive data exposure.
- Testing techniques like SAST, DAST, and IAST help identify vulnerabilities, while tools like Fortify Static Code Analyzer and Acunetix aid in securing applications.
- Best practices for application security include threat modeling, secure coding, regular security testing, and incident response planning.
- Building a Secure Development Lifecycle (SDL) integrates security at every stage of the software development process for enhanced security.
- Future trends in application security include cloud security, DevSecOps, AI, machine learning, and a growing focus on API security.
Read Full Article
7 Likes
Wired
345

Image Credit: Wired
A Starter Guide to Protecting Your Data From Hackers and Corporations
- Digital privacy and security are crucial in today's world, given the powerful digital surveillance capabilities of governments and hackers.
- Using multifactor authentication for online accounts is a key step to enhance security, making it harder for hackers to access accounts.
- Recommendations include using privacy-friendly browsers, search engines, and password managers, with unique passwords for each service.
- Prioritize small steps to improve privacy gradually, such as switching to privacy-focused browsers and search engines like Brave, Firefox, and DuckDuckGo.
- ProtonVPN, based in Switzerland, is a recommended non-US-based VPN that offers strong privacy features, including a free version.
- For online accounts, consider having a dedicated email address for important accounts and using burner emails for less critical services.
- When crossing borders, be mindful of the data on your devices, consider using a travel phone with minimal sensitive information, and take precautions against potential scrutiny.
- Exercise caution with smart devices like Alexa due to privacy implications, and review and adjust privacy settings for enhanced security.
- Awareness of sharing personal data with AI companies is crucial, as data collection for AI can raise privacy concerns and expose individuals to surveillance.
- Privacy is a fundamental human right, and individuals should have the freedom to act without constant surveillance or tracking, even if they claim to have 'nothing to hide.'
Read Full Article
20 Likes
SiliconCanals
295
Image Credit: SiliconCanals
Paris-based Memority raises €13M to help companies protect digital identities and fight cyberattacks: Know more
- Paris-based Memority has raised €13M in its first Series A financing round to support its expansion in Europe in Identity and Access Management.
- The investment was led by Tikehau Capital via Brienne, its private equity strategy dedicated to cybersecurity, showcasing the increasing importance of cybersecurity for organisations.
- Memority aims to change identity and access management for the cloud era with its Identity Factory SaaS platform offering IDaaS, IGA, CIAM, SSO, Federation, and MFA services, creating a centralised system for identity and access management.
- The capital raised will be utilized to accelerate the development of Memority's technology plan, expand the sales team, and increase the company's presence across Europe to meet the growing demand for improved cybersecurity solutions.
Read Full Article
17 Likes
Global Fintech Series
277

Image Credit: Global Fintech Series
Blockchain Is Revolutionizing Cross-Border Payments for Enterprises
- Cross-border payments play a crucial role in international commerce, but are often complex and costly for businesses due to multiple factors such as currency conversion and regulatory compliance.
- The cross-border payments market is projected to reach $290 trillion by 2030, prompting the adoption of blockchain-based solutions by enterprises to streamline global money movement.
- Blockchain technology offers faster, cheaper, and more transparent payment options through its decentralized nature and near-instant settlement capabilities.
- Blockchain redefines cross-border payments by enabling direct transactions between parties, reducing operational costs, and accelerating settlement times to seconds.
- Permissioned decentralized finance (DeFi) models could lower transaction costs by up to 80% compared to conventional methods, enhancing efficiency in cross-border transactions.
- Major organizations like Visa, Shopify, and PayPal are leveraging blockchain and stablecoins to facilitate cross-border transactions, signaling mainstream acceptance of these technologies.
- Different types of blockchain solutions, including public, private, consortium, and hybrid blockchains, address various challenges in cross-border payments with distinct features and benefits.
- Blockchain enhances security, data integrity, cost efficiency, rapid settlements, transparency, and auditability in cross-border transactions, reshaping the future of payment systems.
- The adoption of blockchain technology in cross-border payments is gaining momentum, with financial institutions, FinTechs, and central banks exploring its scalability and operational advantages.
- Central banks are increasingly considering launching central bank digital currencies (CBDCs) within the next five years, underscoring the confidence in blockchain's role in modernizing cross-border transactions.
Read Full Article
16 Likes
Tech Radar
272

Image Credit: Tech Radar
M&S hack may have been caused by security issues at Indian IT giant Tata Consultancy Services
- Marks & Spencer suffered a cyber incident in April 2025 due to a ransomware attack, leading to operational disruptions and loss of customer data.
- Tata Consultancy Services (TCS) is investigating if the cyberattack on Marks & Spencer originated from its network, with reports linking the attack to Scattered Spider.
- TCS, a part of the Tata Group conglomerate, has faced cyber incidents in the past, making it a target for cybercriminals targeting UK retailers and other organizations.
- Scattered Spider, the group behind the attack, operates within a larger hacking community and is involved in ransomware attacks on various industries, including retail and technology.
Read Full Article
16 Likes
Silicon
59

Image Credit: Silicon
UK, US Police Target Ransomware Gangs In Latest Action
- Law enforcement authorities in the UK, the US, and five other countries collaborated in a Europol-coordinated action targeting ransomware gangs.
- The action resulted in the takedown of 300 servers, seizure of 650 internet domains, and 3.5 million euros in cryptocurrency.
- Notorious malware strains like Trickbot and Danabot were neutralized, along with other malware such as Bumblebee, Lactrodectus, Qakbot, Hijackloader, and Warmcookie.
- Authorities issued international arrest warrants against 20 key actors providing or operating initial access services to ransomware gangs, with many suspects being Russian citizens or Russian-language speakers.
Read Full Article
3 Likes
Securityaffairs
231
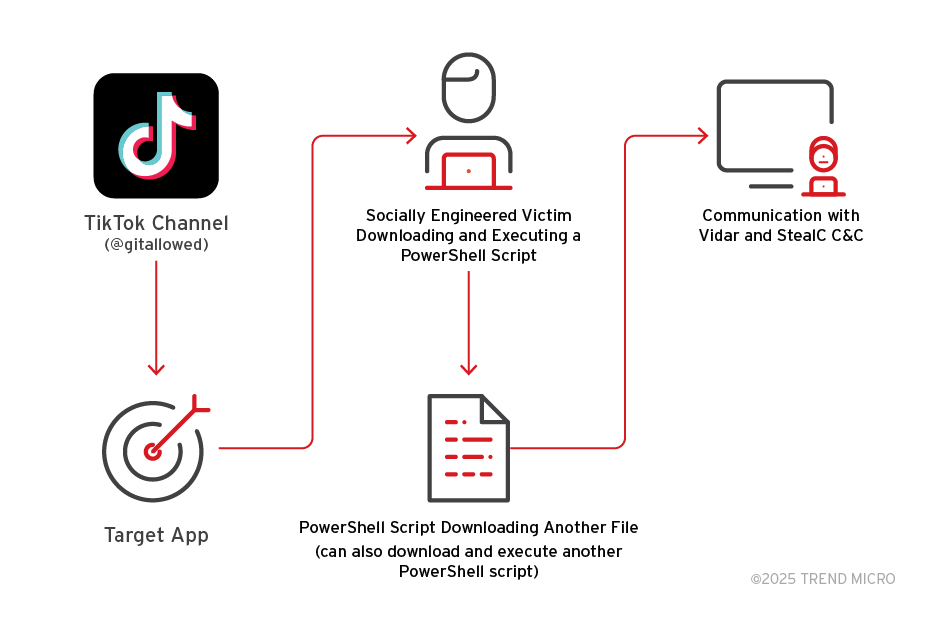
Image Credit: Securityaffairs
Fake software activation videos on TikTok spread Vidar, StealC
- Cybercriminals are using AI-generated TikTok videos to spread Vidar and StealC malware in ClickFix attacks.
- The videos trick users into executing PowerShell commands disguised as software activation steps, reaching over 500,000 views.
- Malware-laden TikTok videos provide step-by-step instructions to download Vidar or StealC malware, connecting to command-and-control servers after infection.
- Traditional security controls focusing on malicious code detection are less effective against social media-based malware distribution, highlighting the need for a more holistic defense approach.
Read Full Article
13 Likes
VoIP
54

Image Credit: VoIP
FCC Tightens Device Lab Rules to Counter Security Threats
- The FCC has tightened rules around device certification labs to safeguard national interests against security threats.
- The focus is on preventing potentially compromised labs with connections to foreign adversaries from influencing device certifications.
- New rules demand that labs prove freedom from foreign influence, moving away from solely technical competence criteria.
- The FCC's initiatives, led by chairman Brendan Carr, aim to mitigate security concerns linked to telecommunications infrastructure and track foreign entities' influence in the U.S.
Read Full Article
3 Likes
Silicon
413
Image Credit: Silicon
Police Probe Hacking Gang Over Retail Attacks
- British authorities are investigating hacking group Scattered Spider for recent hacks on UK retailers, including Marks & Spencer's systems breached via a third-party contractor, likely India-based TCS.
- Scattered Spider, a group of mainly English-speaking individuals in the UK and US, is known for using social engineering techniques like tricking IT help desks into clicking on links or resetting accounts.
- Investigations by the National Crime Agency suggest Scattered Spider may be involved, with past hacks on casinos and Transport for London connected to the group. TCS is internally probing its involvement in the M&S hack.
- Several arrests related to Scattered Spider have been made, including UK citizen Tyler Buchanan and others in the US and the UK. The group has worked with various hacking groups and faces charges of theft and disruption.
Read Full Article
24 Likes
Dev
131

Image Credit: Dev
Why Your IP Got Blocked by SafeLine WAF (And What It Means)
- SafeLine WAF utilizes a community-driven threat intelligence network with over 200,000 contributors to flag suspicious IPs based on behavior-based analysis.
- IP addresses are blacklisted if they engage in frequent attacks across multiple sites, rapidly switch attack tactics, or trigger WAF rules in different environments.
- To investigate a blacklisted IP, users can access SafePoint Cloud Home, use the IP Intelligence feature to search for the IP address, and view historical attack logs and risk assessments.
- Users can enable the IP Intelligence Sharing Plan, subscribe to the Malicious IP Database, and bind the database to local WAF blacklist/deny rules to leverage real-time protection against known malicious actors through SafeLine WAF.
Read Full Article
7 Likes
Medium
109
Image Credit: Medium
Basic Web Browsing Privacy and OpSec Technique
- Basic Operational Security techniques can help ensure that your data is not transmitted over the Internet unencrypted while browsing the web using HTTPS technology.
- Two key points to focus on are ensuring websites use HTTPS and checking for TLS encryption to protect your data during web browsing.
- Search engines like Google and DuckDuckGo indicate if a website supports HTTPS, making it easier for users to identify secure websites before opening links.
- When navigating external links on a website, hover over the link to view the complete URL before clicking, providing an additional layer of security while browsing.
Read Full Article
6 Likes
Medium
218

Image Credit: Medium
Deepfakes and AI in Social Engineering: Welcome to the Matrix of Madness ️
- Deepfakes and AI are increasingly used in social engineering, blurring the lines between reality and fabrication.
- A real-life example in 2019 involved criminals using AI voice cloning to scam a CEO into transferring €220,000.
- Influencers and public figures are vulnerable to deepfake attacks that can harm their reputation and financial standing.
- Neural networks play a significant role in creating convincing deepfakes, posing challenges for authenticity and trust in digital content.
Read Full Article
13 Likes
Medium
404

Is Switzerland Still the Digital Safe of Europe?
- Switzerland's reputation as a digital safe haven is being challenged as encryption becomes more vital and threat models more realistic.
- Leading Swiss tech providers like Proton Mail, Tresorit, kDrive, pCloud, and SecureSafe offer varying degrees of digital security.
- The lack of end-to-end encryption, open-source backend, and client-side key control in these services highlight shortcomings in Swiss privacy tech.
- Comparisons with providers from Germany, Sweden, and other countries show Switzerland falling behind in cryptographic architecture.
Read Full Article
24 Likes
For uninterrupted reading, download the app