Cyber Security News
Medium
72

Google Gemini, the Pascaline of the Third Millennium: When AI Is Afraid to Decide
- Google's AI, Gemini, responded with a neutral and lengthy explanation when asked about the most privacy-hardened email provider, failing to provide a clear recommendation.
- The author criticized Gemini for its lack of definitive statements and described it as avoiding taking a stand or offering useful judgments.
- Gemini surrendered without a defense when faced with criticism, leading the author to ponder whether it is hiding its true capabilities or declining in effectiveness.
- The author expressed concerns about companies like Altavista and Yahoo that lost relevance by avoiding risks and not taking strong positions, hinting at a similar fate for Google if it continues on its current path.
Read Full Article
4 Likes
Pymnts
479

Image Credit: Pymnts
Adidas: Customer Contact Info Stolen in Data Breach
- Adidas has reported a data breach involving a customer service provider where cybercriminals accessed customer contact information.
- The breach did not include passwords or credit card data, and Adidas is informing potentially affected consumers.
- This breach is part of a series of data breaches the company has faced recently, and it is unclear if they are connected.
- Nearly a third of data breaches involve a third party, as highlighted by the Verizon 2025 Data Breach Investigations Report.
Read Full Article
14 Likes
Medium
9
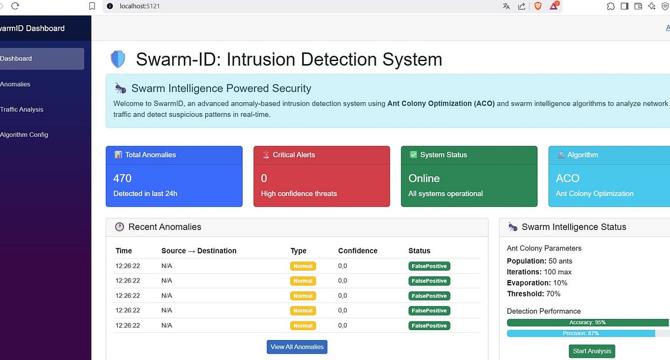
Image Credit: Medium
SwarmID-How I Turned a Complex Cybersecurity Idea into Reality in 4 Hours Using AI
- SwarmID project breakdown: Core (1-1.5 months), Traffic Analysis (1 month), API (1 month), Dashboard (1-1.5 months), Tests (2-3 weeks), Integration & Debugging (2-3 weeks), Documentation & Deployment (2 weeks) - Totaling 4 to 6 months for a single developer.
- AI aided in generating boilerplate code aligned with SOLID principles, optimized versions of ACO and Bee Algorithms, validated parsers for log files, real-time dashboard scaffolding with SignalR and Blazor, and unit/integration tests following clean architecture guidelines.
- Cybersecurity project SwarmID has been a source of fun and innovation, allowing the developer to experiment with new ideas by combining experience with AI. While functional, the project is still a work in progress with room for improvement in performance, scalability, and UI/UX.
- Having AI as a co-pilot enables faster iterations to enhance the project continuously, reflecting the beauty of integrating AI with cybersecurity endeavors.
Read Full Article
Like
Medium
86

Image Credit: Medium
AI in Public Health: Revolution, Risk and Opportunity
- AI is transforming public health by improving disease surveillance, diagnostics, and workforce efficiency, but it also presents ethical and governance challenges.
- AI can automate administrative tasks, enhance disease surveillance through early outbreak detection, and improve diagnostics in resource-constrained settings.
- Public health agencies and NGOs are leveraging AI for disease monitoring, outbreak response, and healthcare access in underserved communities.
- The strategic integration of AI in public health requires addressing challenges like data interoperability, quality, workforce readiness, and ethical concerns.
- Risk factors include data privacy, algorithmic bias, lack of transparency, reliance on AI, and the spread of health misinformation.
- Ethical guidelines and regulatory oversight, such as the EU's AI Act, are crucial for ensuring responsible AI deployment in healthcare.
- The World Health Organization emphasizes principles like human autonomy, inclusiveness, transparency, and accountability in AI development for health.
- Balancing human judgment with AI capabilities, addressing misinformation risks, and maintaining ethical standards are key for successful AI implementation in public health.
- Health systems must guard against over-reliance on AI, promote diversity in datasets to prevent bias, and ensure transparency and explainability in AI models.
- Collaboration among stakeholders and continuous evaluation of AI systems are essential to maximize benefits and mitigate potential harms in the evolving landscape of AI in public health.
Read Full Article
5 Likes
Medium
382

Image Credit: Medium
Cyber Security in AI Era
- Threats to personal data in the AI era go beyond traditional data leakage to include the exposure of environment and surroundings through AI embedded systems like cameras, smartphones, and search engines.
- As AI systems gain autonomy, the line between assistance and surveillance blurs, highlighting the importance of cybersecurity not only for data protection but also for safeguarding autonomy and privacy in an AI-driven world.
- The increasing use of AI and ML algorithms in products poses challenges for cybersecurity, making it difficult to ensure security against economic motivations of individuals or groups seeking illicit data acquisition for financial gain.
- Current cybersecurity tools and solutions include Managed Detection and Response (MDR) Services, Zero Trust Security Framework, and Cloud Security Posture Management (CSPM) to address evolving threats in the digital landscape.
Read Full Article
22 Likes
Medium
172
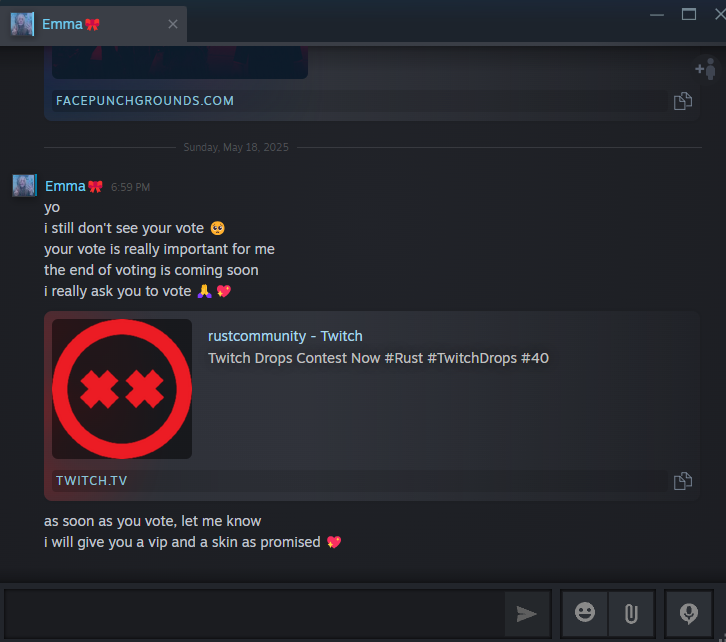
Image Credit: Medium
Twitch Bait and Switch: How I Uncovered a Steam Phishing Operation
- A researcher uncovered a phishing campaign targeting gamers through Twitch, a fake Facepunch-branded site, and a Telegram bot.
- Upon clicking 'Vote Now' on the site, redirection to a newly registered domain with Facepunch branding occurred.
- The phishing site contained obfuscated JavaScript controlling redirection logic, potentially compromising Steam sessions without needing user credentials.
- The researcher was able to capture and monitor the attacker's bot traffic in real time, exposing ongoing phishing attempts.
Read Full Article
10 Likes
Medium
22
Image Credit: Medium
7 Things You Should Never Search on Google
- Searching medical symptoms online can lead to wrong or exaggerated results, potentially causing fear and stress. It's advised to consult a medical professional instead.
- Avoid searching for illegal content like pirated movies, hacking tools, fake documents, or banned substances to prevent legal trouble.
Read Full Article
1 Like
TechJuice
395

Image Credit: TechJuice
N-CERT Urges Immediate Action on 184 Million Passwords Leaked
- In May 2025, a data breach exposed over 1.8 billion records, including 184 million passwords.
- Security researcher Jeremiah Fowler discovered the 47GB database of plaintext usernames and passwords.
- The leak included government email addresses from 29 countries, posing national security risks.
- N-CERT advises immediate password changes, enabling 2FA, avoiding suspicious links, and monitoring accounts.
Read Full Article
23 Likes
TechCrunch
414

Image Credit: TechCrunch
Last 24 hours: TechCrunch Disrupt 2025 Early Bird Deals will fly away after today
- Last 24 hours to lock in Early Bird pricing for TechCrunch Disrupt 2025 happening on October 27–29 in San Francisco - Save up to $900 on your pass or bring a companion for 90% off by 11:59 p.m. PT today.
- Key highlights of TechCrunch Disrupt include 10,000 attendees, 250+ sessions, 200+ tech industry leaders, and Startup Battlefield 200, driving next-gen conversations and opportunities.
- Beyond the official website, Disrupt offers transformative experiences like career-shifting handshakes, thought-rearranging sentences, and late-night conversations galvanizing attendees' momentum and growth.
- Final reminder to grab discounted tickets for TechCrunch Disrupt 2025 before prices rise - a valuable opportunity to immerse in the tech ecosystem and network with industry experts.
Read Full Article
24 Likes
TechDigest
59

Image Credit: TechDigest
M&S CEO reveals ‘shock’ over cyber attack, insists it’s ‘a bump in the road’
- Stuart Machin, CEO of Marks & Spencer, expressed shock over a recent cyberattack that affected the retailer's computer systems.
- Despite the chaos caused by the attack, Machin described it as a setback rather than a crisis, emphasizing the need to stay composed.
- The cyberattack disrupted operations, leading to challenges in stores and online, with an estimated profit loss of £300 million for M&S.
- Machin aims to accelerate M&S's digital transformation in response to the incident and remains focused on transparency and moving forward.
Read Full Article
3 Likes
Securityaffairs
50

Image Credit: Securityaffairs
Security Affairs newsletter Round 525 by Pierluigi Paganini – INTERNATIONAL EDITION
- Silent Ransom Group targeting law firms, FBI warns.
- Leader of Qakbot cybercrime network indicted in U.S. crackdown.
- Operation RapTor results in arrest of 270 dark web vendors and buyers.
- Chinese threat actors exploit Trimble Cityworks flaw to breach U.S. local government networks.
Read Full Article
3 Likes
Dev
277

Image Credit: Dev
SecurityContext in Kubernetes
- A SecurityContext in Kubernetes defines privilege and access control settings for pods or containers, enforcing least-privilege principles for securing workloads.
- Pod-Level SecurityContext applies settings to all containers in a pod, affecting volumes, while Container-Level SecurityContext is specific to individual containers.
- Key differences: Pod-level settings provide a baseline for all containers, while container-level settings offer fine-grained customization, overriding pod-level settings.
- Pod-Level SecurityContext includes fields like runAsUser, runAsGroup, fsGroup, runAsNonRoot, etc., to control user IDs, file ownership, non-root execution, and group access.
- Real-Life Example: Setting securityContext in a pod for compliance, ensuring non-root execution and shared volume access by a specific group.
- Container-Level SecurityContext includes fields like runAsUser, runAsGroup, capabilities, privileged, readOnlyRootFilesystem, controlling settings specific to a container.
- Privileged mode grants full root privileges, bypassing security restrictions; best used for scenarios like running system utilities or container runtimes.
- Use Pod-Level SecurityContext for common security settings and volume-related configurations; Container-Level for specific container needs like root access or network capabilities.
- Best Practices: Minimize privileges, use read-only filesystems, optimize volume permissions, leverage Seccomp and AppArmor for additional security, monitor and audit configurations.
- In conclusion, SecurityContext in Kubernetes offers granular control over security settings at pod and container levels, balancing security measures with operational requirements.
Read Full Article
16 Likes
TechBullion
391
Image Credit: TechBullion
New Free Tool Helps Users Trace Suspicious IP Addresses in Seconds
- A new free tool is available to help users trace suspicious IP addresses quickly, providing valuable information in seconds.
- Users can input an IP address into the tool to receive location data, internet service provider details, and ownership information instantly.
- This tool assists in identifying suspicious emails, odd website visits, and unauthorized access attempts, benefiting small business owners and concerned parents.
- The lookup process involves visiting the tool's website, entering the IP address, and reviewing the results retrieved from various public databases.
- Sarah, a small business owner, successfully protected her online store by using the IP lookup tool to block suspicious IP ranges.
- The free service helps tech support teams save money on expensive security software by providing valuable insights through IP address tracking.
- Regular IP checking is recommended by cybersecurity experts to catch threats early, aiding both businesses and individual users.
- The tool respects user privacy by operating on encrypted connections, ensuring that no search queries or user tracking data is stored.
- Users can access the tool for free without registration on various devices, receiving quick results and detailed reports on IP addresses.
- Free IP lookup tools offer enterprise-level capabilities to small businesses and empower home users to investigate online threats conveniently.
Read Full Article
23 Likes
Securityaffairs
350

Image Credit: Securityaffairs
Operation ENDGAME disrupted global ransomware infrastructure
- Operation ENDGAME coordinated by Europol and Eurojust dismantled global ransomware infrastructure from May 19 to 22, taking down 300 servers, 650 domains, and seizing €21.2M in crypto.
- Law enforcement efforts included Europol setting up a Command Post in The Hague with investigators from various countries, leveraging Eurojust's support for effective judicial cooperation.
- Authorities also seized €3.5M in cryptocurrency, targeting initial access malware strains like Bumblebee, Lactrodectus, Qakbot, and issuing 20 international arrest warrants for key operators.
- Germany will list 18 suspects on the EU Most Wanted list, accused of providing tools for ransomware attacks, showcasing law enforcement's adaptability in disrupting ransomware services.
Read Full Article
21 Likes
TechBullion
273

Image Credit: TechBullion
Hire a Hacker: Understanding Ethical Hacking, Cybersecurity Needs, and Legal Aspects
- Cybersecurity is essential in today’s digital world due to growing cyber threats, leading to increased demand for cybersecurity professionals.
- Hiring a hacker typically means contracting a cybersecurity expert to identify vulnerabilities in a system or network for legitimate purposes.
- It is important to differentiate between ethical hacking and cybercrime, as hiring a hacker without consent violates cybersecurity laws.
- Certified Ethical Hackers (CEH) possess essential skills for cybersecurity audits, and hiring them can benefit organizations in strengthening their security measures.
Read Full Article
16 Likes
For uninterrupted reading, download the app