Cyber Security News
Medium
336

Image Credit: Medium
AI-Powered Authorization: Leading Secure Fintech Systems for the Future
- The article discusses the importance of authorization in fintech systems and how AI is transforming them to ensure secure user experiences and mitigate risks like fraud and unauthorized access.
- The author shares their experiences in leading the design of payment platforms with a focus on scalable authorization frameworks, stakeholder alignment, and fraud detection strategies to handle millions of transactions securely under pressure.
- The evolution from Role-Based Access Control (RBAC) to Attribute-Based Access Control (ABAC) is highlighted, showcasing the need for more flexible approaches to manage permissions based on dynamic factors like device trust and geolocation for enhanced security.
- The integration of AI into authorization systems is explored, emphasizing how AI makes systems proactive and adaptive to enhance security, user trust, and overall user experience in fintech.
Read Full Article
20 Likes
Medium
2.3k
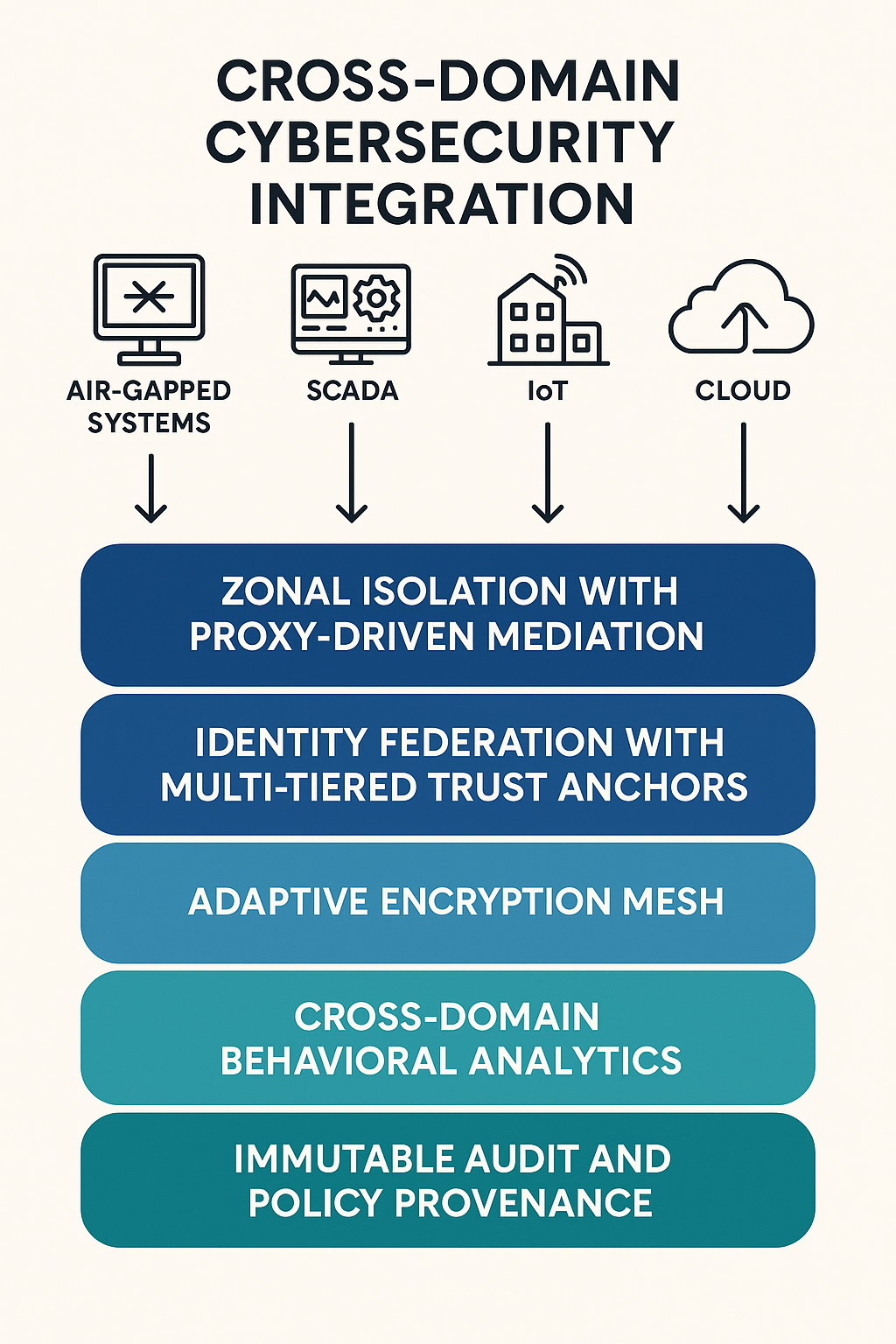
Image Credit: Medium
Cross-Domain Cybersecurity Integration: Bridging the Divide Between Air-Gapped, SCADA, IoT, and…
- Cybersecurity integration now requires a new doctrine called Cross-Domain Cybersecurity Integration (CDCI) to unify traditionally isolated domains like air-gapped systems, SCADA, IoT, and cloud ecosystems.
- Modern adversaries target integration points like Stuxnet-style air-gapped infections, IoT-based botnets, and cloud misconfigurations, making them vulnerable.
- The CDCI model proposes a five-layered strategic architecture, including domain-specific security zones, zero-trust identity models, domain-aware encryption, AI-driven baselining, and tamper-proof audit trails.
- Adopting the Cross-Domain Cybersecurity Integration model helps organizations secure interconnected smart devices, critical infrastructure controls, cloud ecosystems, and completely isolated systems.
Read Full Article
19 Likes
TechCrunch
4.2k

Image Credit: TechCrunch
Naukri exposed recruiter email addresses, researcher says
- Naukri.com, an Indian employment website, fixed a bug that exposed recruiter email addresses on its platform.
- Security researcher Lohith Gowda discovered the issue in the API used on Naukri's Android and iOS apps.
- Exposed email addresses could lead to phishing attacks, spam, and other security risks.
- Naukri confirmed fixing the bug after the researcher reported it and stated that their systems have been updated.
Read Full Article
33 Likes
Hackersking
356

Image Credit: Hackersking
Trump Administration Cybersecurity Funding Cuts: A Risky Gamble?
- The Trump administration's cybersecurity funding cuts during Donald Trump's presidency raised concerns among experts and officials, posing a potential threat to national security.
- The 2021 budget proposal included significant reductions to the Department of Homeland Security's Cybersecurity and Infrastructure Security Agency (CISA), impacting cybersecurity research, incident response, and inter-agency coordination.
- Programs crucial for defending against cyberattacks saw funding cuts, potentially limiting emergency responses and infrastructure security updates, especially concerning election security ahead of the 2020 U.S. Presidential elections.
- Criticism from lawmakers and cybersecurity analysts highlighted the risks of emboldening nation-state actors like Russia, China, and Iran, as the U.S. lagged behind in global cybersecurity investments, emphasizing the importance of continuous investment in cybersecurity.
Read Full Article
21 Likes
Dev
223

Image Credit: Dev
Why You Need Multi-Factor Authentication (MFA) on Every Account—Right Now
- Multi-Factor Authentication (MFA) is crucial in today's digital landscape to protect against cyber threats like phishing and data breaches.
- MFA requires two or more factors for login, such as something you know (password), something you have (phone), or something you are (biometric data).
- Real-world attacks like the Twitter Bitcoin Hack and Colonial Pipeline Ransomware could have been prevented with MFA.
- Setting up MFA on platforms like Google, Microsoft, and other accounts involves methods like Google Prompt, Microsoft Authenticator, and hardware keys.
- MFA methods vary in security level, with push-based MFA and hardware security keys being the most secure options.
- MFA is essential even for seemingly unimportant accounts due to password reuse and potential chain attacks by hackers.
- For developers and engineers, enabling MFA is crucial across various platforms and tools to enhance security.
- Proper backup strategies for MFA, such as saving backup codes and using multiple devices, are important to avoid getting locked out.
- MFA significantly reduces the risk of account takeovers and is a recommended security measure for personal and professional accounts.
- Take immediate steps to enable MFA on your accounts, prioritize app-based codes or hardware keys over SMS, and advocate for secure practices among peers.
Read Full Article
13 Likes
Hackersking
387

Image Credit: Hackersking
How Most Cyber Attacks Begin: The Hidden Dangers of Credential-Based Threats
- Cyber threats are increasing in quantity and sophistication, posing risks of data breaches and financial losses.
- More than 55% of breaches stem from credential attack vectors, including phishing, brute force attacks, and MFA bypass techniques.
- Phishing attacks are the most dangerous aspect of cybersecurity, targeting user login information and financial data.
- MFA bypass techniques involve methods like man-in-the-middle attacks and token pilfering to circumvent multi-factor authentication.
- Brute force attacks involve continuously guessing combinations of usernames and passwords to gain unauthorized access.
- Malware, zero-day exploits, and misconfigurations are other common cyber attack vectors.
- Recommendations for protection include regular user training, complex password policies, and adoption of multiple layers of security.
- Behavior analytics, software updates, and secure remote access are emphasized for enhanced security measures.
- Understanding cyber threats and implementing proactive defense measures are crucial in safeguarding against credential-based attacks.
- Hackersking provides resources for cybersecurity training and comprehensive cyber defense strategies.
Read Full Article
23 Likes
Dev
50

Image Credit: Dev
I Passed CompTIA Security+ (SY0-701)! Here’s How It Went
- The individual passed the CompTIA Security+ 701 exam with a score of 768 out of 900, mentioning the challenges faced due to English not being their first language and the need to adapt to working in English-speaking environments.
- The person studied for about 2–3 months, using various study materials and tools such as CompTIA Security+ Study Guide, Professor Messer’s Practice Exams, Jason Dion’s Practice Exams, ChatGPT, Anki flashcards, and GoodNotes on iPad for preparation.
- They found the real exam's Performance-Based Questions (PBQs) to be much harder than the practice exams, emphasizing the importance of not underestimating them during preparation.
- On the exam day, the individual shared their conditions, including lack of sleep due to recovering from a cold, taking Tylenol for symptoms, and using a Japanese sleeping pill for rest, and expressed their thoughts on the exam's difficulty and their preference for technical over management concepts.
Read Full Article
3 Likes
Medium
425

Image Credit: Medium
The Cybersecurity Frontier of 2025: AI, Privacy, and the New Digital Defense
- Global IT spending in 2025 is projected to reach $5.61 trillion, while data breach damages per incident surged to $4.8 million in 2024.
- Key emerging threats in cybersecurity include increasingly sophisticated ransomware attacks, AI-powered threats, and executive-targeted social engineering.
- AI is now a crucial element in cybersecurity defense, enhancing speed and scale in threat response and analysis.
- Individuals are urged to take proactive steps like using strong passwords, limiting social media sharing, and leveraging advanced protection measures like VPNs for personal privacy defense.
Read Full Article
24 Likes
Medium
450

10 Agentic AI Patterns That Are Reshaping Intelligent Systems
- Agentic AI patterns are design blueprints defining how intelligent agents behave, interact, and plan, resembling personality types for AI.
- Reflective agents review and improve their outputs autonomously, as seen in AI coding assistants like GitHub Copilot.
- Task-oriented agents focus on specific tasks, enhancing automation of business processes like appointment scheduling.
- Hierarchical agents operate within a chain of command, beneficial for orchestrating complex projects with structured control.
- Coordinating agents assign roles in team settings for efficient operations like DevOps pipelines.
- Distributed Agent Ecosystem enables autonomy at scale in decentralized networks, beneficial for IoT applications.
- Human-in-the-Loop Collaboration agents work with humans for critical decisions, enhancing safety in sectors like healthcare.
- Self-learning agents adapt based on feedback, making AI systems more responsive and user-friendly.
- RAG-Based agents retrieve external information for better responses, combining generative models with factual reliability.
- Planning agents build and execute strategies to meet user goals efficiently, suitable for complex workflows.
Read Full Article
27 Likes
TechJuice
59

Image Credit: TechJuice
Massive Data Leak Exposes Login Details of 184 Million Netizens
- Security researcher Jeremiah Fowler discovered a massive data leak in May 2025, totaling over 47 GB of data, with no identifiable metadata.
- The leaked data included plaintext usernames and passwords, indicating potential use by cybercriminals or researchers employing infostealing malware.
- Analysis of a sample of 10,000 records revealed compromised accounts from major platforms like Facebook, Google, Instagram, Roblox, Discord, Microsoft, Netflix, PayPal, and others.
- Containing email addresses with .gov domains from 29 countries, the leak poses significant national security risks, prompting swift action by the World Host Group to take the database offline.
Read Full Article
3 Likes
Medium
300

Image Credit: Medium
Securing the Legal Front Door: A Product Perspective on Verification and Trust
- Design principles for building secure, scalable identity verification and multi-factor authentication workflows are crucial for managing legal data requests.
- Balancing security, efficiency, and legal defensibility is essential due to the complexity of external data requests and the potential risks involved.
- Key components of secure verification include email verification, mobile number OTP, smart document validation, MFA, and access control measures.
- Implementing robust verification processes not only enhances security but also builds trust with customers, partners, and regulators in the realm of legal data requests.
Read Full Article
18 Likes
Medium
200
Image Credit: Medium
AI Today and Tomorrow:
- AI tools like ChatGPT, Midjourney, and DALL-E are rapidly advancing, creating human-like content in writing, artwork, and code.
- AI integration in everyday tools like Google Docs, Microsoft Office, and customer service systems is becoming more prevalent.
- The debate on AI ethics, surveillance, bias, job impact, and mental health implications is growing, emphasizing the need for a global dialogue.
- There is a call for an honest discussion on the potential benefits and risks of AI in steering it towards benefiting humanity.
- Automation through AI can eliminate mundane tasks, while enhancing creativity, decision-making, access to healthcare, education, and resource optimization.
- AI reflects the intentions of its creators and users, underscoring the importance of understanding its capabilities and influencing its direction.
- AI's practical applications in real life range from personal assistants like Siri to advanced medical diagnostics and financial services.
- AI is transforming industries through fraud detection, personalized investments, customer service, visual search, demand forecasting, and educational platforms.
- Despite its benefits, AI limitations include the lack of general intelligence, biases inherited from data, and concerns about privacy and surveillance.
- Countries like China, the U.S., Europe, India, and Africa have varied approaches to AI adoption, emphasizing ethics, regulations, and education.
- Transparency, inclusivity, regulation enforcement, and public education are key factors in shaping a responsible AI future.
Read Full Article
12 Likes
Brighter Side of News
282

Image Credit: Brighter Side of News
AI chatbots can hide secret messages invisible to surveillance
- Advancements in AI chatbots like ChatGPT have found a new use in securely sending hidden messages undetectable by surveillance systems.
- With governments seeking ways to monitor encrypted messages, the need for invisible encryption methods has become crucial.
- Researchers developed EmbedderLLM, a cryptographic method that hides encrypted messages within AI-generated text using a unique digital key.
- This method ensures secure communication for citizens under surveillance and is resilient against future threats like quantum computing.
- The technology offers flexibility to work with various AI models and can benefit journalists and activists in restrictive environments.
- While promising, widespread adoption may face challenges based on actual demand and acceptance in different regions.
- The method presents ethical considerations regarding potential misuse, but researchers remain optimistic about its secure messaging applications.
- As AI continues to develop, embedding hidden messages within text can revolutionize secure communication and privacy protection globally.
- This breakthrough highlights AI's role in enhancing privacy protections against surveillance and censorship threats globally.
- Innovative solutions like EmbedderLLM may become essential in safeguarding freedom of expression and privacy in an increasingly monitored digital world.
Read Full Article
16 Likes
Securityaffairs
63

Image Credit: Securityaffairs
Silent Ransom Group targeting law firms, the FBI warns
- The FBI warns that the Silent Ransom Group, also known as Luna Moth, has been targeting U.S. law firms for 2 years using callback phishing and social engineering tactics.
- The group gains remote access to systems and steals sensitive data to extort victims. They have previously enabled Ryuk and Conti ransomware attacks through BazarCall campaigns.
- SRG started posing as IT staff in phone calls since March 2025, tricking employees into granting remote access and exfiltrating data without needing admin privileges.
- After stealing data, SRG extorts victims with ransom emails and pressures employees into negotiations. They operate a data leak site but do not always follow through on threats to publish the data.
Read Full Article
3 Likes
Dev
309

Image Credit: Dev
AWS KMS vs. AWS Certificate Manager: The Ultimate Guide to Cloud Security Layers
- The distinction between AWS Key Management Service (KMS) and AWS Certificate Manager (ACM) is crucial for cloud security, with KMS focusing on encryption at rest and ACM on secure communication in transit.
- KMS acts as a Vault Keeper, managing encryption keys securely for data encryption, while ACM functions as a Digital Passport Office, issuing SSL/TLS certificates for secure communication.
- KMS encrypts data when stored, securing digital assets, while ACM secures data during transit, ensuring secure communication channels.
- KMS involves Customer Master Keys (CMKs) for encryption, while ACM deals with SSL/TLS certificates for authentication and encryption.
- Common pitfalls include confusion between in-transit and at-rest encryption, misconfigurations in KMS key policies, and issues with ACM DNS validation.
- Pro tips include using KMS multi-region keys for disaster recovery, implementing ACM key policies for cross-account access, and leveraging ACM Private CA for internal PKI.
- Understanding the distinct roles of KMS and ACM is essential for building secure, compliant, and resilient cloud applications on AWS.
- KMS and ACM are complementary layers in cloud security, providing fundamental building blocks for data encryption and secure communication.
- AWS KMS and AWS Certificate Manager are not competitors but partners in creating a secure cloud environment by encrypting data at rest and securing data in transit, respectively.
- To deepen knowledge, explore AWS KMS Developer Guide, AWS Certificate Manager User Guide, or consider pursuing the AWS Security Specialty certification.
Read Full Article
18 Likes
For uninterrupted reading, download the app