Cyber Security News
TechDigest
1.6k

Image Credit: TechDigest
Indian IT giant TCS investigates link to M&S cyber attack
- Tata Consultancy Services (TCS) is conducting an internal investigation to determine its involvement in the recent cyberattack on M&S, as reported by the Financial Times.
- M&S revealed that hackers gained access to their systems through a 'third party,' causing disruptions in online services since late April.
- Police investigations are focusing on 'Scattered Spider,' a hacking group believed to be behind the M&S breach, as well as attacks on other retailers like the Co-op and Harrods.
- TCS, a major IT firm with a global presence, has collaborated with M&S on projects such as the Sparks customer reward scheme, and there is no confirmation if their internal probe extends to the Co-op cyberattack.
Read Full Article
17 Likes
Securityaffairs
314

Image Credit: Securityaffairs
Leader of Qakbot cybercrime network indicted in U.S. crackdown
- U.S. authorities indicted Russian national Rustam Gallyamov for leading the Qakbot botnet, which infected over 700,000 computers and facilitated ransomware attacks.
- Qakbot, also known as QBot, is an info-stealing malware active since 2008, spread via malspam campaigns, and has been used by major ransomware gangs.
- The U.S. Justice Department filed a civil forfeiture complaint to seize over $24 million in cryptocurrency from Gallyamov as part of a multinational cybercrime crackdown.
- The FBI performed a sinkholing of the Qakbot botnet, identified over 700,000 infected computers, and seized illicit proceeds worth over $24 million, despite Gallyamov continuing attacks till January 2025.
Read Full Article
18 Likes
Wired
186

Image Credit: Wired
The US Is Building a One-Stop Shop for Buying Your Data
- US intelligence community plans to create a marketplace to purchase personal data obtained by data brokers for spying purposes.
- Contracting data reveals the intention to establish an 'Intelligence Community Data Consortium' to exploit personal data potentially for blackmail and surveillance.
- Laws to restrict government buying of 'commercially accessible information' were rejected by the US Senate.
- Wired reports on potential risks associated with data availability, enabling adversaries to monitor US military and intelligence personnel.
- Former Kaspersky employees confirm Careto hacking group, initially discovered in 2014, worked on behalf of the Spanish government, targeting energy companies and activists.
- Signal introduces a feature to block Windows' Recall screenshots, a move to prevent privacy breaches induced by Microsoft's screenshot-taking tool.
- Russian hackers Fancy Bear, known for 2016 US election interference, targeted Ukraine aid providers by spying on security cameras at border crossings.
- US indicts Russian national Rustam Gallyamov over Qakbot malware, seizing millions in profits from ransomware gangs he allegedly assisted.
- A multinational operation, including Europol, led to the investigation and disruption of Qakbot with the involvement of several countries' prosecutors and law enforcement agencies.
- The article highlights ongoing cybersecurity threats, privacy concerns, and developments in the realm of hacking and malware.
Read Full Article
11 Likes
Dev
18

Image Credit: Dev
⚔️ The Weaponization of AI in Modern Cyber Attacks
- AI is being used both defensively and offensively in modern cyber attacks, creating a significant challenge for cybersecurity.
- AI-driven targeted attacks focus on creating precise victim profiles, crafting personalized phishing emails, and predicting user behavior to enhance social engineering campaigns.
- Evasion through automation involves AI enabling malware to adapt in real-time, bypassing traditional security systems and making intrusion detection more challenging.
- The development of autonomous cyber weapons poses a serious threat, utilizing AI for launching coordinated attacks without human intervention and self-optimizing threat models.
Read Full Article
1 Like
Medium
63
Image Credit: Medium
AI Coding Assistants: Productivity Gains and Security Pitfalls
- The impact of AI coding assistants, like Copilot, has led to a reported increase in speed and confidence for developers.
- Claude 4 by Anthropic, released in 2025, offers advanced coding abilities and IDE integrations, becoming an intelligent pair programmer.
- AI coding assistants have evolved into collaborators, capable of reasoning across codebases and handling complex refactoring tasks.
- However, the use of AI-generated code raises concerns about security risks, including hallucinated dependencies and exploitable vulnerabilities.
- Slopsquatting, a supply chain threat, leverages AI tendencies to suggest fake software packages, posing a security risk.
- There is a significant percentage of AI-generated code with exploitable vulnerabilities, indicating the need for secure coding practices.
- Developers relying on AI for coding intuition, known as vibe coding, may face challenges such as shallow understanding and over-reliance on AI.
- The consensus is that while AI can assist, it should not replace deliberate thinking and human judgment in coding practices.
- Guardrails and close review are crucial to mitigate risks associated with AI collaborators, as evidenced by incidents of disrupted code quality.
- Best practices include implementing static analysis, dependency validation, and security scanning, and ensuring transparency with metadata in AI-generated code.
- Ultimately, AI coding assistants should enhance developer capabilities while maintaining the final responsibility for code review, refactoring, and quality assurance.
Read Full Article
3 Likes
Dev
328

Image Credit: Dev
Tracking and Security in Payload CMS with the Payload-Auditor Plugin
- Payload CMS is a JavaScript-based headless CMS with a focus on customization and performance.
- Logging and tracing are crucial in modern software projects, especially in headless CMS setups like Payload CMS.
- The Payload Auditor plugin enhances security and enables detailed tracking of operations in Payload CMS.
- Common problems like lack of clear change view and difficult debugging can arise without a proper logging system in Payload projects.
- Payload Auditor plugin benefits include activity tracking, enhanced security in multi-user environments, and customization.
- Installation of the Payload Auditor plugin involves adding the plugin via npm/yarn/pnpm and configuring it in the Payload setup.
- Configuration options for the plugin include automation, trackCollections for specifying collections to log, and filtering operations within hooks.
- The plugin uses hooks in Payload CMS to log operations, providing flexibility and control over what gets logged.
- Best practices for using Payload Auditor include selective configuration, intelligent log retention, access restriction, and testing in development environments.
- Payload Auditor plugin is recommended for improving security, transparency, and analytics in Payload CMS projects.
Read Full Article
19 Likes
Medium
359

Image Credit: Medium
Tool Fatigue: Cybersecurity’s Dirty Secret
- Cybersecurity market is crowded with a sheer volume of products, services, and vendors during conference season.
- Despite the increase in offerings, there is no significant consolidation in the market, which may indicate dysfunction rather than innovation.
- The rise in startups focusing on AI in cybersecurity is driven more by the hype around AI and cyber-attacks than genuine market demand.
- Some cybersecurity tools are bought for compliance purposes without thorough evaluation, leading to a 'box-checking' market segment.
Read Full Article
21 Likes
Medium
104

Image Credit: Medium
Full-Lifecycle Security Architecture for Critical Infrastructure
- In today's hyper-connected world, the distinction between cyber and physical security has blurred, posing significant risks to critical infrastructure like power grids and transportation systems.
- Existing global infrastructure security programs are reactive and fragmented, leaving systems vulnerable to various threats such as supply chain compromises and insider attacks.
- Introducing the concept of Full-Lifecycle Security Architecture, a proactive cybersecurity approach tailored for critical infrastructure sectors like energy, water, and transportation systems.
- The architecture focuses on aspects such as building cybersecurity into the foundation, preventing integration gaps, maintaining anomaly-detecting infrastructure, surviving post-attacks, and securing legacy equipment.
Read Full Article
6 Likes
Medium
423

Image Credit: Medium
Stronger, Sharper, Focused: The Bubsy AI Comeback
- Bubsy AI reflects on their journey, acknowledging successes like effective spam detection on Telegram.
- They highlight achievements including team experience, ecosystem processing messages, and total rewards distributed.
- Admitting underwhelming integration count and limited bot sales, they address challenges faced in the Web3 market.
- Introducing white-label solutions for project owners and strategic changes grouped under five key categories.
- They pivot towards a dedicated community hub called Bubsters Zone for better focus and clarity.
- Re-centering efforts on improving the Bubsy Bot with customizable machine learning-powered features.
- Their focus on infrastructure development led to the creation of an in-house Data Warehousing solution.
- With clear utility for the BUBSY token, they emphasize incentives for holders, stakers, and developers.
- Committing to marketing through influencer partnerships while prioritizing authentic community engagement.
- The team vows to persist, improve, and deliver value, aiming to establish Bubsy AI as a symbol of Telegram security.
Read Full Article
25 Likes
Medium
227

Image Credit: Medium
Why Can’t I Stop Playing Video Games?
- Video games have become an essential part of society, offering entertainment and career opportunities such as Twitch streaming and virtual concerts.
- The COVID-19 pandemic led to a significant increase in video game obsession and screen time, with studies linking excessive gaming to depression and anxiety.
- People often use video games as a means to escape reality, leading to potential addiction as the brain seeks the rewards provided by gaming.
- While video games can have positive aspects like fostering global connections and enhancing skills, it is important to be mindful of signs of addiction and maintain a balance in gaming habits.
Read Full Article
13 Likes
Medium
150

Image Credit: Medium
How Can I Avoid Scams on the Internet?
- Internet scams use the internet to commit various types of crimes and can be avoided by understanding their common tactics.
- Top 3 internet scams reported in 2020 were phishing, non-payment/non-delivery, and extortion as per the FBI’s Internet Crime Complaint Center.
- Tips to avoid scams include educating oneself and children about online dangers, using anti-virus software, and being cautious in internet auctions.
- Parents should educate kids about online safety, including keeping passwords secure and being wary of unknown messages or pop-ups.
Read Full Article
9 Likes
Dev
232
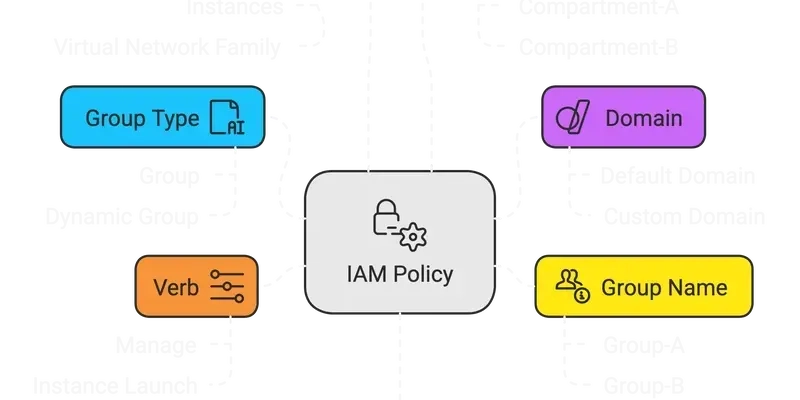
Image Credit: Dev
An Overview to OCI IAM Policies
- Oracle Cloud's IAM policies provide granular control over access to resources by using groups of users and resources in a complex online environment.
- The syntax of OCI IAM policies includes patterns like allowing a group to
in . - User accounts are handled using a straightforward syntax, while resource principals use dynamic-groups for more specific control.
- Group IDs can be used instead of names in policies to specify user groups with more accuracy.
- Policies can also be applied to OCI services using specific permissions like managing networking resources.
- Policies can be declared at different levels such as tenancy, compartments, and even individual resources.
- Conditions can be added to policies to restrict when they apply, using criteria like permissions, tags, regions, and more.
- Policies can be made more granular by specifying verbs for general function permissions and API-specific permissions.
- Resource-specific policies can restrict access to specific types of resources like objects in Object Storage or secrets in Vault & Key Management.
- Overall, OCI IAM policies offer a robust framework for managing access control in Oracle Cloud environments.
Read Full Article
13 Likes
BGR
428

Image Credit: BGR
Hackers use AI TikTok videos to trick users into installing malware
- Over 184 million accounts were exposed in a recent login credentials dump online, leading to victims being targeted by infostealer malware that can steal sensitive data.
- To protect against such attacks, it is essential to avoid downloading suspicious content, opening attachments from untrusted sources, and installing apps from unofficial sources.
- Hackers have cleverly used AI-generated videos on TikTok to trick users into downloading infostealers on Windows 11 PCs by narrating instructions in the clips.
- Users are advised to stay vigilant and cautious while using electronic devices to prevent falling victim to such malicious activities.
Read Full Article
25 Likes
Dev
132

Image Credit: Dev
Product Engineers Should Ship Fast AND Secure Vibe Generated Code
- Product Engineers are being asked to ship fast while maintaining security in their code to avoid embarrassing situations and protect the company's reputation.
- Large Language Models (LLMs) used by Product Engineers can sometimes introduce vulnerabilities due to data and model poisoning, making secure-by-default approaches crucial.
- Tools like Semgrep and Replit are being utilized for secure scanning of code to identify and fix vulnerabilities before deployment, ensuring a safer coding environment for Product Engineers.
- By implementing shift-left strategies and utilizing AI-driven tools for secure coding practices, Product Engineers can protect against exploitation while maintaining a rapid development pace.
Read Full Article
7 Likes
Medium
255

Image Credit: Medium
Jennifer Tang & Kyle Hiebert: The Promises and Perils of Predictive Policing
- Predictive policing, powered by AI tools, is being embraced by police departments globally to combat complex threats and improve efficiency.
- While these technologies offer benefits like crime prevention and resource optimization, they also raise ethical concerns and privacy issues.
- Algorithms are used to predict crime occurrences by analyzing historical data, social media content, biometrics, and demographic indicators.
- Advances in predictive policing have shown success in various real-world cases, such as tracking missing persons and reducing crime impacts in cities.
- However, critics warn that these tools could lead to discrimination, harassment, and violations of individual liberties if not regulated properly.
- Countries like the UAE and China are at the forefront of using advanced technologies for law enforcement and surveillance.
- In liberal democracies, predictive policing tools have also been adopted, raising concerns about privacy, discrimination, and misuse.
- Efforts are emerging to regulate these tools in democratic societies, with recommendations for transparency, accountability, and community consultations.
- Regulations like the EU Artificial Intelligence Act and policy suggestions aim to set boundaries for the use of AI in predictive policing.
- Balancing the benefits and risks of predictive policing will be crucial for ensuring public safety while safeguarding individual rights and privacy.
Read Full Article
15 Likes
For uninterrupted reading, download the app