Devops News
Dev
441

Image Credit: Dev
🚀 Dockerfile Best Practices – Make Your Builds 10x Faster
- Dockerfile builds can be slow and inefficient.
- This article provides Dockerfile best practices to make builds faster, use fewer system resources, and deploy faster and safer.
- Some common mistakes are discussed, along with their corresponding fixes.
- The article also provides a quick checklist for Dockerfile best practices.
Read Full Article
26 Likes
Microsoft
282

Image Credit: Microsoft
Azure Boards + GitHub: Recent Updates
- Smarter Link Management for Branches, PRs, and Commits: Azure Boards now automatically links merge commits and pull requests to associated work items, reducing the need for manual linking.
- Build Status from GitHub Repos (YAML Pipelines): Azure Boards displays the Integrated in build link from GitHub repositories when using Azure YAML pipelines, improving traceability from code to deployment.
- Increased GitHub Repository Limit: Azure DevOps project now supports connecting up to 1,000 GitHub repositories, providing better scalability for organizations.
- State Transition Support: Linking GitHub pull requests to Azure Boards work items now supports state transitions, allowing automatic updates of work item states on merge.
Read Full Article
16 Likes
Dev
382

Image Credit: Dev
150+ DevOps Interview Questions with expert tips
- Preparing for DevOps interviews can be overwhelming, but this article offers a comprehensive roadmap with 150+ categorized questions and expert tips.
- The article covers beginner, intermediate, and expert levels of DevOps questions, including real-world scenarios and tool-specific inquiries.
- It emphasizes important lessons for interview success, such as explaining the 'why,' showcasing troubleshooting skills, and highlighting the significance of soft skills in DevOps.
- Basic questions range from defining DevOps to understanding CI/CD, while intermediate questions delve into topics like container orchestration and microservices architecture.
- Advanced questions tackle complex topics like CI/CD pipeline design, disaster recovery, and balancing speed vs. stability in production environments.
- Tool-specific questions cover Docker, Kubernetes, Jenkins, as well as cloud platforms like AWS, Azure, and GCP, along with monitoring tools like Prometheus and Grafana.
- The article includes recommended resources for upskilling, emphasizing the importance of daily tool practice, explaining decision-making rationale, and sharing stories during interviews.
- DevOps roles are in high demand, and thorough preparation based on the insights provided can help candidates secure positions successfully.
- Key advice includes practicing with tools regularly, detailing reasons behind choices, and sharing experiences alongside technical skills to excel in DevOps interviews.
- The comprehensive guide offers readers a valuable toolkit for excelling in DevOps interviews and emphasizes the importance of hands-on practice and effective communication.
- The blog equips individuals with the necessary knowledge and strategies to confidently tackle various DevOps interview questions, reinforcing the significance of practical experience and soft skills.
Read Full Article
22 Likes
The New Stack
178

Image Credit: The New Stack
Tutorial: GPU-Accelerated Serverless Inference With Google Cloud Run
- Google Cloud launched GPU support for the Cloud Run serverless platform, enabling developers to accelerate serverless inference of models deployed on Cloud Run.
- The tutorial explains the steps to deploy the Llama 3.1 Large Language Model (LLM) with 8B parameters on a GPU-based Cloud Run service.
- The guide demonstrates the initialization of the environment, deploying the Text Generation Inference (TGI) server using the Hugging Face model, and performing inference using cURL or the OpenAI Python library.
- This tutorial provides insights into how to leverage GPU-acceleration for serverless inference using Google Cloud Run.
Read Full Article
10 Likes
Discover more
- Programming News
- Software News
- Web Design
- Open Source News
- Databases
- Cloud News
- Product Management News
- Operating Systems News
- Agile Methodology News
- Computer Engineering
- Startup News
- Cryptocurrency News
- Technology News
- Blockchain News
- Data Science News
- AR News
- Apple News
- Cyber Security News
- Leadership News
- Gaming News
- Automobiles News
Dzone
222

Image Credit: Dzone
Zero Trust Isn't Just for Networks: Applying Zero-Trust Principles to CI/CD Pipelines
- Zero trust has become a key element of enterprise security.
- While zero trust principles are applied to networks, user identities, and endpoints, the CI/CD pipeline often remains undersecured.
- CI/CD pipelines orchestrate code validation for production deployment and may have persistent credentials and system privileges.
- Treating pipelines as untrusted by default is essential to aligning them with the rest of the zero trust model.
Read Full Article
13 Likes
Dev
363

Image Credit: Dev
🚀 Create Reproducible Dev Environments with Vagrant in Minutes
- Vagrant enables users to create and configure lightweight, reproducible, and portable development environments.
- Vagrant is like a DevOps time machine that spins up a fully-configured virtual machine using one file and one command.
- To use Vagrant, initialize the project with a Vagrantfile and configure it, specifying the base image, network settings, synced folders, and provider-specific settings like VM name, memory, and CPUs.
- Vagrant is a useful tool for building isolated environments, creating reproducible VMs for testing installations, safely testing Ansible playbooks, and setting up disposable Proof-of-Concepts (PoCs).
Read Full Article
21 Likes
Dev
434

Image Credit: Dev
The Overengineer’s Manifesto: Saying Hello the Hard Way
- The Overengineer’s Manifesto: Saying Hello the Hard Way
- Project Complexity Score: 1,417 lines of code & docs, 264 function/class/logic blocks—just to say "Hello".
- OverHelloWorld is a cautionary tale for developers, showcasing the dangers and joys of overengineering.
- Lessons learned from overengineering: simplicity is a feature, knowing when to stop is a superpower, and overengineering is a great way to learn but a terrible way to ship.
Read Full Article
26 Likes
Dev
250

Image Credit: Dev
The Importance of a WordPress Developer for SaaS Websites
- SaaS websites play crucial roles in lead generation, onboarding, and customer support, requiring precise technical execution.
- WordPress Developers are essential for ensuring secure, high-performing, and visually appealing SaaS websites.
- They customize user experiences, streamline plugin integration, and optimize speed and core web vitals.
- WordPress Developers also focus on SEO optimization, scalability, security, third-party integrations, and conversion-focused landing pages.
- Additionally, they ensure smooth user experiences across all devices and provide ongoing maintenance and support.
- Partnering with a skilled WordPress Developer is crucial for the success of SaaS businesses.
- From tailored user experiences to scalable infrastructure, these developers are key to optimizing revenue and reputation.
- Invedus Outsourcing in India offers WordPress Developers for customized SaaS projects, catering to various skills and budgets.
Read Full Article
15 Likes
Dev
259

Image Credit: Dev
How to Dump Database Tables into Files to Speed Up Queries with esProc
- esProc can help improve query performance by exporting database data into files for subsequent computation.
- The article discusses a MySQL database containing the orders_30m table with 30 million rows of historical order data.
- Using esProc, data can be exported to files like BTX or CTX for faster query processing.
- Exporting data to BTX reduced query time from 17.69 seconds to 5.319 seconds, outperforming MySQL.
- CTC files offer higher compression ratios and can further optimize query performance compared to BTX files.
- Parallel computation using esProc with BTX or CTX files can significantly reduce query execution times.
- esProc simplifies complex operations like TopN queries and offers concise and elegant syntax for faster processing.
- Dumping data into files with esProc is recommended for static historical data analysis, providing significant speed advantages over traditional databases.
- File-based approaches can be several to dozens of times faster than database queries, making them suitable for specific scenarios.
- esProc offers mixed computation capabilities for processing new data scenarios beyond file exports.
Read Full Article
15 Likes
Dev
325
Image Credit: Dev
Demystifying Agile, Scrum, and Kanban: Which Methodology Fits Your Dev Team?
- Agile, Scrum, and Kanban are key methodologies in project management, each with unique strengths and best-fit scenarios.
- Agile is a mindset focusing on iterative cycles, constant feedback, flexibility, and collaboration within software development.
- Scrum, a framework under Agile, provides structure, sprints, and predictability through time-boxed iterations and defined roles.
- Kanban emphasizes visual flow, flexibility, and optimizing work processes through visualizing tasks and managing flow.
- Scrum suits teams needing structure and regular deliveries, while Kanban is ideal for variable workloads and flexibility.
- To choose the right methodology, consider factors like team structure, workflow visualization, and the need for continuous improvement.
- Practical tips for Scrum include setting realistic sprint goals and utilizing tools like Teamcamp for efficient management.
- For Kanban, start by visualizing workflows and implementing WIP limits to enhance productivity and address blockers effectively.
- Real-world examples show how organizations like Vanguard, VistaPrint, and Ultimate Software have benefited from using Scrum and Kanban.
- Teamcamp provides features tailored for Agile, Scrum, and Kanban teams, helping streamline project management and boost developer productivity.
Read Full Article
19 Likes
Javacodegeeks
57

Image Credit: Javacodegeeks
Maven vs. the World: Why Gradle Won (But Maven Still Rules in Banking)
- Maven remains entrenched in sectors like banking where compliance outweighs other considerations.
- Maven's XML-based POM files enforce strict conventions, making it invaluable for large organizations needing reproducibility and control.
- Gradle's Groovy/Kotlin DSL enables more expressive builds and allows for custom task graphs that are impossible in Maven without writing a full plugin.
- Maven shows more consistent performance across very large codebases, while Gradle's incremental builds are faster for typical development workflows.
Read Full Article
3 Likes
Dev
72
Image Credit: Dev
Kubernetes 1.30 Features – More Enhancements You Shouldn’t Miss
- Fine-Grained Authorization with CEL in RBAC allows adding logic to RBAC rules using CEL (Common Expression Language).
- Sidecar Containers feature (now stable) allows sidecar containers to restart independently of the main application container.
- CSI Inline Volumes Are Now GA, removing the need to create a separate PVC for defining temporary volumes inside a pod spec.
- Advanced Network Policies (Port Ranges) enable network policies to support port ranges in ingress/egress rules.
Read Full Article
4 Likes
Dev
131

Image Credit: Dev
40 days of K8s - CKA chalange (01/40)
- Day 01/40: Docker Fundamentals
- Explained the Docker life cycle and architecture.
- Diagram showcased how Docker images can be hosted in one host machine with their own resources.
- Described the workflow of creating, testing, and using Docker images in development, testing, and production environments.
Read Full Article
7 Likes
Dev
64

Image Credit: Dev
🚨 Top DevOps Mistakes Beginners Make – And How to Avoid Them
- Not learning Linux basics - Practice Linux commands daily in a sandbox
- Relying too much on GUI tools - Learn the CLI and automation
- Not using version control for infra - Use Git for everything – infra too!
- Ignoring monitoring/logging - Always set up basic alerts & logs
Read Full Article
3 Likes
Dev
172
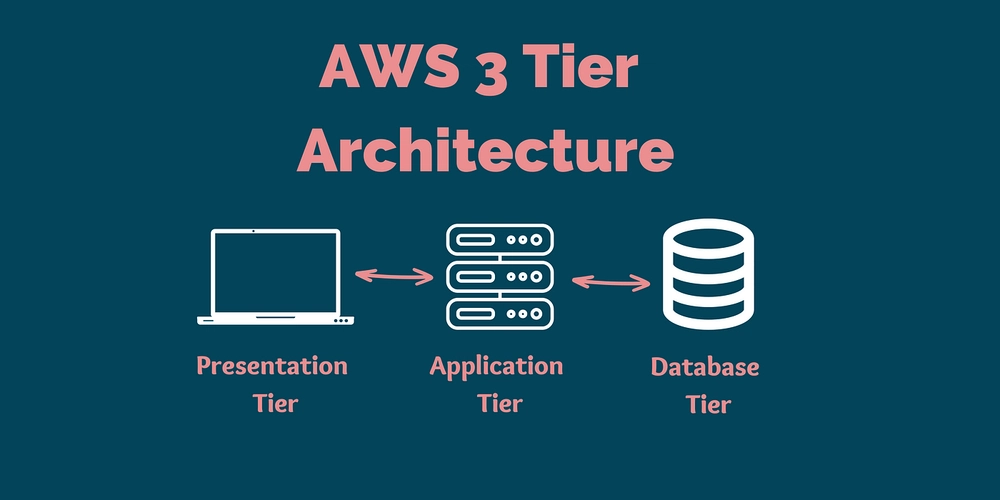
Image Credit: Dev
Building a Scalable, Secure Multi-Tier Architecture on AWS — My Recent Infrastructure Project
- This project centers around designing and deploying a highly available, secure, and scalable multi-tier architecture on Amazon Web Services (AWS).
- The architecture is built within a VPC, split across two Availability Zones (AZ-A and AZ-B) for redundancy.
- The architecture follows the standard 3-tier model: Web Tier, Application Tier, and Integration Tier.
- Key AWS services used include EC2, ALB, ELB, Auto Scaling, S3, RDS, EFS, IAM, CloudWatch, Route 53, VPC Flow Logs, and CloudFront.
Read Full Article
10 Likes
For uninterrupted reading, download the app