Info. Security News News
Krebsonsecurity
26

Lamborghini Carjackers Lured by $243M Cyberheist
- The parents of a 19-year-old Connecticut honors student accused of taking part in a $243 million cryptocurrency heist in August were carjacked a week later.
- Authorities say the couple was beaten and briefly kidnapped by six young men who traveled from Florida as part of a botched plan to hold the parents for ransom.
- The couple was targeted because the co-conspirators believed the victims’ son had access to significant amounts of digital currency.
- Approximately one week earlier, on Aug. 19, a group of cybercriminals that allegedly included the couple’s son executed a sophisticated phone-based social engineering attack in which they stole $243 million worth of cryptocurrency from a victim in Washington, D.C.
- Prosecutors allege Malone “Greavys” Lam, 20, of Miami and Los Angeles, and Jeandiel “Box” Serrano, 21, of Los Angeles conspired to steal and launder over $230 million in cryptocurrency from a victim in Washington, D.C.
- By tracing the flow of funds stolen in the heist, ZachXBT concluded that Wiz received a large percentage from the theft
- It appears that all of the suspects in the cyber heist (and at least some of the alleged carjackers) are members of The Com.
- Cybercriminals hail from all walks of life and income levels
- There is also a penchant among this crowd to call attention to their activities in conspicuous ways that hasten their arrest and criminal charging.
- As the mobile carriers seek to make their networks less hospitable to SIM-swappers, and as more financial platforms seek to harden user account security, today’s crypto thieves are finding they don’t need SIM-swaps to steal obscene amounts of cryptocurrency.
Read Full Article
1 Like
Securityaffairs
268

Image Credit: Securityaffairs
Cybercriminals Are Targeting AI Conversational Platforms
- Resecurity reports a rise in attacks on AI Conversational platforms, targeting chatbots that use NLP and ML to enable automated, human-like interactions with consumers.
- Chatbots are designed to simulate human conversations and enhance user experiences. Bots collect valuable data from users, which can be analyzed to gain insights into customer preferences and behaviors, however, data collected from users may reveal sensitive information due to personalized interactions.
- AI-powered Call Center Software and Customer Experience Suites use purpose-built chatbots to interact with consumers, which is especially significant in fintech and e-commerce industries.
- Cybercriminals could orchestrate advanced fraudulent activities and apply data and extraction techniques to acquire records of interest and use them in advanced phishing scenarios and other cyber offensive purposes by gaining access to conversational AI platforms.
- The compromised data could lead to hijacking where bad actors could intercept the session and control the dialogue further leading to fraudulent schemes.
- Resecurity forecasts a variety of social engineering schemes that could be orchestrated by abusing and gaining access to trusted conversational AI platforms.
- The experts from Resecurity outlined the need for AI trust, risk, and security management (TRiSM), as well as Privacy Impact Assessments (PIAs) to identify and mitigate potential impacts.
- The EU AI Act and other regulatory frameworks in North America, China, and India are already establishing regulations to manage the risks of AI applications. Businesses have to ensure that AI systems are trustworthy, thereby providing consumers with confidence in how their personal data is used.
- Conversational AI platforms have already become a critical element of the modern IT supply chain for major enterprises and government agencies.
- Businesses need to pay increased attention to supply chain cybersecurity and balance between traditional cybersecurity measures relevant to SaaS (Software-as-a-Service) and those specialized and tailored to the specifics of AI.
Read Full Article
16 Likes
Infoblox
425

Image Credit: Infoblox
Infoblox Universal DDI™: Your Top 12 Questions Answered
- Attendees of the virtual launch event for Infoblox Universal DDI had the opportunity to get detailed questions about the new product suite answered in the Q&A session.
- Universal DDI is focused on cohesive management of critical network services across an entire environment and provides enhanced discovery, visibility, and analysis of assets.
- Key questions addressed areas of implementation process, future of BloxOne DDI, failover/survivability options, third party integration, pricing, reporting, Infoblox portal, and compliance.
- Universal Asset Insights uses various methods to detect zombie resources, and Universal DDI Management includes all capabilities previously available in BloxOne DDI.
- The Infoblox team has built a robust, highly available and resilient cloud service with controls in place to meet SLAs.
- The company is working on establishing Universal DDI Management with Microsoft Management and works with AWS, Azure, GCP and NIOS-X.
- There is no need to purchase DNS flavours separately with Infoblox Universal DDI.
- NIOS DDI will continue as a viable option, but the Infoblox team will continue to deliver new capabilities and features as planned.
- Universal DDI helps build more agile and resilient enterprises and provides insights into asset information.
- Infoblox’s Universal DDI launch event provided a wealth of information and insights directly from the experts.
Read Full Article
25 Likes
Securityaffairs
385
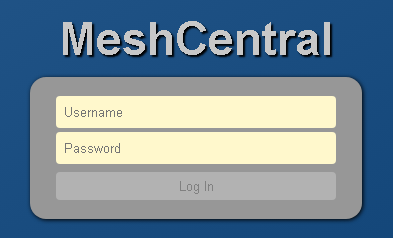
Image Credit: Securityaffairs
Awaken Likho APT group targets Russian government with a new implant
- The Awaken Likho APT group, also known as Core Werewolf and PseudoGamaredon, has targeted Russian government agencies and industrial entities.
- Kaspersky researchers discovered a new campaign by Awaken Likho from June to August 2024, in which they shifted from UltraVNC to MeshCentral for remote access.
- The group utilized a new implant delivered through phishing emails, transitioning from UltraVNC to MeshAgent.
- Awaken Likho has been active since the Russo-Ukrainian conflict, continuously refining their techniques and showing ongoing development in their latest malware version.
Read Full Article
23 Likes
Sentinelone
399

Image Credit: Sentinelone
Cloud and Container | The Attack & Defend Series
- SentinelOne’s Cloud Security Research Team has launched a new blog series, “Cloud and Container | Attack & Defend” exploring the ins and outs of cloud security from both the threat actor and the defender perspectives.
- The series will focus on the tactics, techniques and procedures employed by threat actors to compromise cloud infrastructures, and security best practices for addressing those threats.
- Organizations continue to embrace cloud technologies to look beyond traditional infrastructures and redefine how their applications are built, managed and scaled.
- Adopting cloud-native platforms, containerized apps and other modern storage solutions is driven by the need for more efficient development and deployment workflows while building resilience.
- The Com, a group of multiple actors with varying objectives and skill levels, is the most impactful threat actor of 2023, according to SentinelOne's WatchTower team.
- The Com has been observed in high-profile network intrusion and ransomware attacks, and uses cloud compromise tactics and techniques.
- The most common root causes of cloud incidents are misconfigured assets exposed to the internet, followed by compromised credentials and vulnerable web apps hosted on the cloud.
- Sophisticated cloud attacks can involve all three root causes and popular tactics include milestone distribution in attack chains.
- SentinelOne proceeds with a new Attack post focusing on Kubernetes (K8s) Privilege Escalation, a critical concern in cloud-native environments, in the next blog.
- The blog will examine how attackers can exploit misconfigurations in K8s, vulnerabilities, or over-permissive roles to escalate privileges and potentially gain unauthorised access to sensitive resources.
Read Full Article
24 Likes
Securityintelligence
279

Image Credit: Securityintelligence
Cybersecurity Awareness Month: Horror stories
- October is Cybersecurity Awareness Month and cybersecurity professionals have shared some of their most memorable and haunting cyber incidents. A construction company suffered significant theft due to the fact that a user had a habit of clicking on links in emails, repeatedly falling victim to phishing schemes. A senior executive working from a coffee shop over a weekend accessed their company’s servers via public WiFi and interacted with sensitive data, potentially exposing it to a malicious attack. A law firm suffered a ransomware attack due to a PDF downloaded from an untrusted source. An online retailer was compromised when an admin installed a WordPress blog on their e-commerce web server that remained unpatched and discovered hardcoded database credentials. A medical practice lost a laptop containing patient information and financial data subject to HIPAA protections, which was eventually found in the hands of a deceased rogue employee.
- Human behaviour is the biggest threat to cybersecurity. Cybersecurity incidents take place every day irrespective of having the most sophisticated security tools. October is Cybersecurity Awareness Month, dedicated to educating people to stay vigilant and updated about the latest threats. Employees can be the weakest link, exposing organizations to cyber threats when they are unaware of the risks of clicking on suspicious-looking links.
- A key observation from these horror stories is that investment is required in cybersecurity tools, education, and planning to stay safe from the latest cyber threats. A combination of cybersecurity tools, education and planning ahead will help organizations mitigate attacks or breaches so that the results of a cyber incident don’t have to be downright terrifying.
Read Full Article
16 Likes
Kaspersky
139

Image Credit: Kaspersky
Authentication codes from a service you don't have an account with | Kaspersky official blog
- Receiving a two-factor authentication code for a service you don't have an account with can happen if your phone number was previously owned by someone else.
- This is known as phone number recycling, where the previous owner registered an account using your current phone number.
- If you plan on creating an account with that service, contact their support team to detach the unknown account from your number.
- Under no circumstances should you use the one-time codes to access an account that doesn't belong to you, as it is illegal and unethical.
Read Full Article
8 Likes
Securityaffairs
197

Image Credit: Securityaffairs
U.S. CISA adds Windows and Qualcomm bugs to its Known Exploited Vulnerabilities catalog
- U.S. Cybersecurity and Infrastructure Security Agency (CISA) adds Windows and Qualcomm bugs to its Known Exploited Vulnerabilities catalog.
- Qualcomm addressed 20 vulnerabilities, including a potential zero-day issue tracked as CVE-2024-43047.
- The use-after-free bug in Qualcomm chipsets may lead to memory corruption and is being actively exploited.
- CISA identifies Microsoft vulnerabilities CVE-2024-43572 and CVE-2024-43573 under active exploitation and urges prompt updates.
Read Full Article
11 Likes
Medium
143
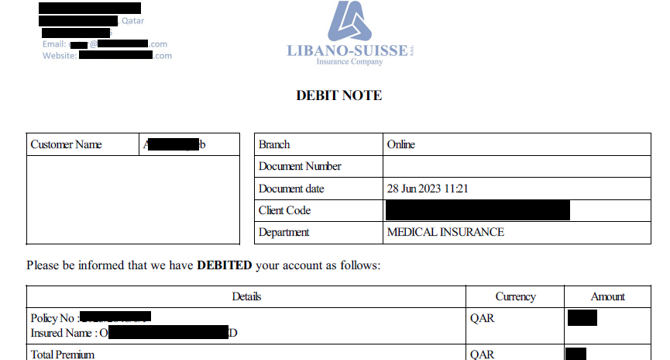
Image Credit: Medium
Libano-Suisse exposed unprotected data from an Azure Blob.
- Libano-Suisse Insurance Company exposed unprotected data from an Azure Blob.
- The company failed to respond to multiple emails notifying them about the issue.
- The incident involved the exposure of 22,000 files containing personal data.
- The exposed data included client names, passport numbers, policy details, and more.
Read Full Article
8 Likes
Hackersking
340

Image Credit: Hackersking
Supercharging Hackers Toolkits
- A hacker's toolkit is a crucial collection of software, scripts, and tools used by hackers and cybersecurity experts to test, analyze, and secure systems.
- Hackers use toolkits for tasks such as penetration testing, vulnerability assessment, physical testing, and more.
- Some popular hacking tools include USB Rubber Ducky, Wi-Fi Pineapple, Raspberry Pi, and Kali Linux Live USB, among others.
- The USB Rubber Ducky is a specialized USB device capable of executing pre-defined scripts with high speed, allowing automated tasks or attacks.
- Flipper Zero is a portable multi-tool for pen-testers and hardware hackers that combines various functionalities and can read and emulate RFID tags.
- Wi-Fi Pineapple is designed for network auditing and man-in-the-middle attacks and thus can intercept communications between users and legitimate networks.
- Raspberry Pi is a small, affordable computer popular among hackers and developers and can be configured as a network sniffer or intrusion detection system, among others.
- Kali Linux Live USB is a bootable USB drive containing a popular distribution tailored for penetration testing and ethical hacking, and it allows running a fully functional OS without affecting the host machine.
- The abundance of tools can make selecting the right ones time-consuming, especially for beginners, but they offer essential capabilities to cybersecurity professionals.
- Join the Complete Offensive-Hacking course to become a certified hacker and gain hands-on offensive hacking experience.
Read Full Article
20 Likes
Krebsonsecurity
439

Patch Tuesday, October 2024 Edition
- Microsoft released security updates addressing 117 vulnerabilities, including two actively exploited ones.
- One of the zero-day flaws, CVE-2024-43573, affects MSHTML in Internet Explorer and allows attackers to trick users into viewing malicious web content.
- The more serious zero-day, CVE-2024-43572, is a code execution bug in the Microsoft Management Console, which system administrators use to monitor and configure the system.
- Adobe patched 52 vulnerabilities across various software, while Apple fixed compatibility issues in its macOS 15 update.
Read Full Article
26 Likes
Qualys
444

Image Credit: Qualys
Microsoft and Adobe Patch Tuesday, October 2024 Security Update Review
- Microsoft has released its October 2024 Patch Tuesday updates, patching 121 vulnerabilities with 3 critical and 114 important severity vulnerabilities.
- Two zero-day vulnerabilities, known to be exploited in the wild, were addressed by Microsoft.
- Adobe has released nine security advisories to address 52 vulnerabilities in its software.
- 31 of these vulnerabilities are given critical severity ratings.
- Several flaws have been fixed in Microsoft software, including Spoofing, Denial of Service (DoS), Elevation of Privilege (EoP), Information Disclosure, Security Feature Bypass, and Remote Code Execution (RCE).
- The vulnerabilities in Microsoft Office and Components, Microsoft Management Console, Visual Studio, Windows Print Spooler Components, Windows Remote Desktop, among many others, were patched.
- Microsoft has addressed three vulnerabilities in Microsoft Edge (Chromium-based), which were patched earlier this month.
- The active exploitation of zero-day vulnerabilities and the critical vulnerabilities remain a significant threat to digital devices.
- Combining Qualys Vulnerability Management Detection Response (VMDR) and Qualys Patch Management can reduce the median time to remediate these vulnerabilities.
- The next Patch Tuesday falls on November 12 and stay tuned for the patch analysis.
Read Full Article
26 Likes
Securityaffairs
40
Image Credit: Securityaffairs
Ukrainian national pleads guilty in U.S. court for operating the Raccoon Infostealer
- Ukrainian national Mark Sokolovsky has pleaded guilty in a US court for operating the Raccoon Infostealer.
- Sokolovsky was charged with computer fraud for infecting millions of computers with the Raccoon Infostealer.
- The Raccoon Infostealer is a malware-as-a-service (MaaS) that steals sensitive data such as credit card information and email credentials.
- Authorities dismantled the Raccoon Infostealer's infrastructure, but it has resurfaced since then.
Read Full Article
2 Likes
Hackersking
210

Image Credit: Hackersking
Unlock Unlimited Internet with the Ultimate Jio VPN Trick
- In this article, we unveil the ultimate Jio VPN trick that will take your internet usage to the next level.
- With this ingenious solution, you can bypass restrictions and access blocked websites, stream content without buffering, and secure your online activities.
- Jio, one of the leading telecom providers in India, offers a wide range of services, including high-speed internet.
- However, even with Jio's impressive network, users may encounter various limitations and restrictions, such as throttled speeds, blocked websites, and content geo-restrictions.
- A VPN creates a secure and encrypted tunnel between your device and the internet, allowing you to bypass these limitations and access the online world without any restrictions.
- One of the primary benefits is the ability to bypass content restrictions and access blocked websites.
- Another significant advantage of using a Jio VPN is the enhanced security and privacy it provides.
- Setting up a VPN with Jio is a straightforward process that can be completed in just a few simple steps.
- When it comes to selecting the right VPN provider for your Jio internet connection, there are several top-tier options to consider.
- The ultimate Jio VPN trick is a game-changer for anyone seeking to unlock the full potential of their Jio internet connection.
Read Full Article
12 Likes
TechCrunch
13

Image Credit: TechCrunch
Kasperksy says it’s closing down its UK office and laying off dozens
- Kaspersky is closing down its UK office and laying off staff, following its decision to close down its U.S. operations a few months ago.
- The company plans to wind down its UK office and focus on the partner channel to remain active in the UK market.
- Kaspersky has faced allegations of close ties with the Russian government, which it has consistently denied.
- In response to a sales ban, Kaspersky had to leave the U.S. market and transfer its customer base to a newly established antivirus company called UltraAV.
Read Full Article
Like
For uninterrupted reading, download the app