Info. Security News News
Securityaffairs
202

Image Credit: Securityaffairs
Google Pixel 9 supports new security features to mitigate baseband attacks
- Google announced that its Pixel 9 has implemented new security features, and it supports measures to mitigate baseband attacks.
- Pixel phones are known for their strong security features, particularly in protecting the cellular baseband.
- Google claims that the Pixel 9 implements the most secure baseband to date, addressing a critical attack vector exploited by researchers.
- Key security measures implemented in the Pixel 9 series include Bounds Sanitizer, Integer Overflow Sanitizer, Stack Canaries, Control Flow Integrity, and Auto-Initialize Stack Variables.
Read Full Article
12 Likes
Hackingblogs
247
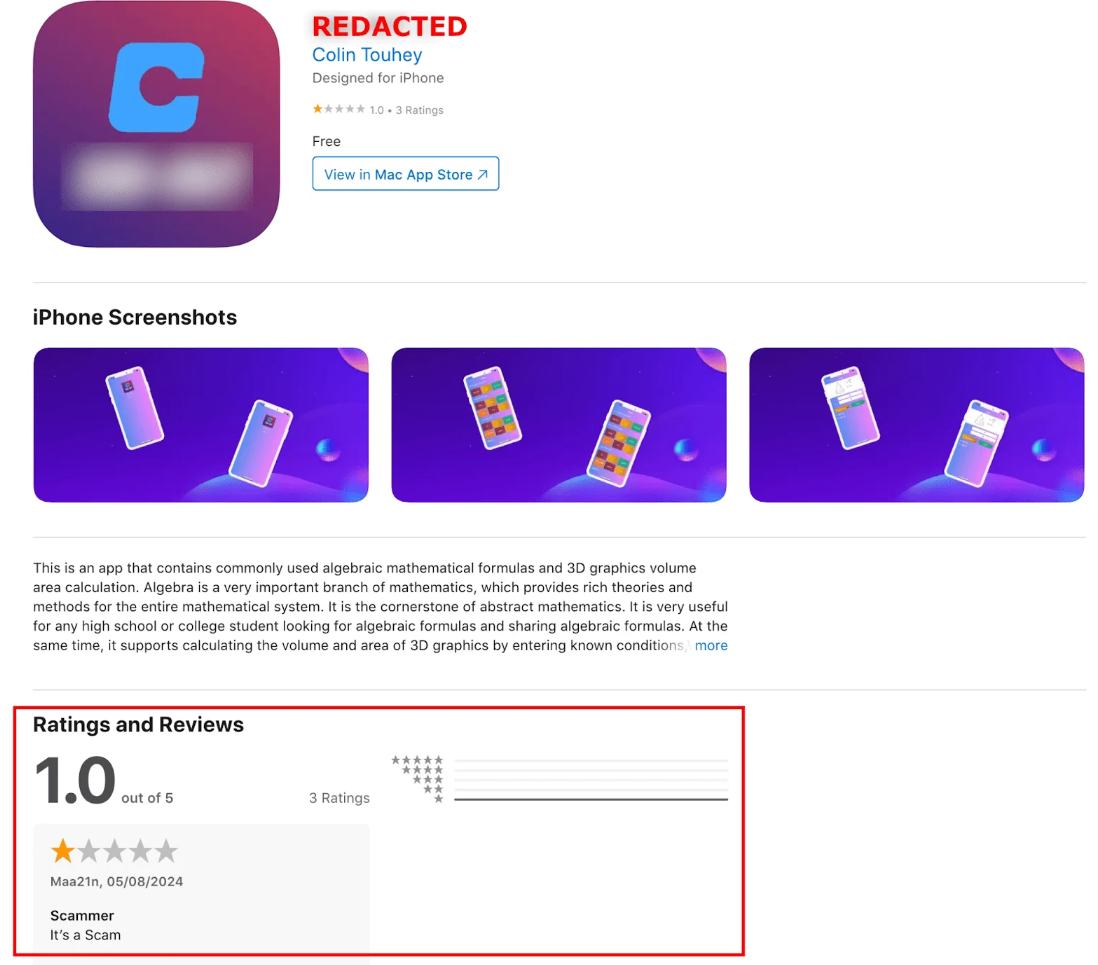
Image Credit: Hackingblogs
Beware of fake trading apps in the wild ? What is the pig-butchering trick ?
- Fake trading apps are appearing in app stores, allowing hackers to steal large amounts of money without triggering malware alarms.
- A scam called 'pig butchering' manipulates victims into complex investment schemes, often involving cryptocurrencies.
- The fraudulent apps are available on the official Google Play store and Apple App Store, using a cross-platform development framework.
- Users are tricked into providing personal information and identification documents, and the scam domains mimic legitimate financial organizations.
Read Full Article
14 Likes
Securityaffairs
158

Image Credit: Securityaffairs
WordPress LiteSpeed Cache plugin flaw could allow site takeover
- A high-severity flaw in the WordPress LiteSpeed Cache plugin could allow attackers to execute arbitrary JavaScript code under certain conditions.
- The vulnerability is a stored cross-site scripting (XSS) issue impacting versions up to 6.5.0.2.
- The flaw arises from improper sanitization of the “X-LSCACHE-VARY-VALUE” HTTP header, allowing arbitrary script injection.
- The vulnerability was addressed in version 6.5.1 on September 25, 2024.
Read Full Article
9 Likes
Securityaffairs
162

Image Credit: Securityaffairs
Google removed Kaspersky’s security apps from the Play Store
- Google removed Kaspersky's Android security apps from the Play Store and suspended its developer accounts.
- The removal is a result of restrictions imposed by the U.S. Department of Commerce's Bureau of Industry and Security.
- Kaspersky is investigating the issue and suggests users download and update their products from other stores like Galaxy Store or Huawei AppGallery.
- This is not the first time Kaspersky has faced bans from Western governments due to concerns about its ties to the Russian government.
Read Full Article
9 Likes
Hackingblogs
162
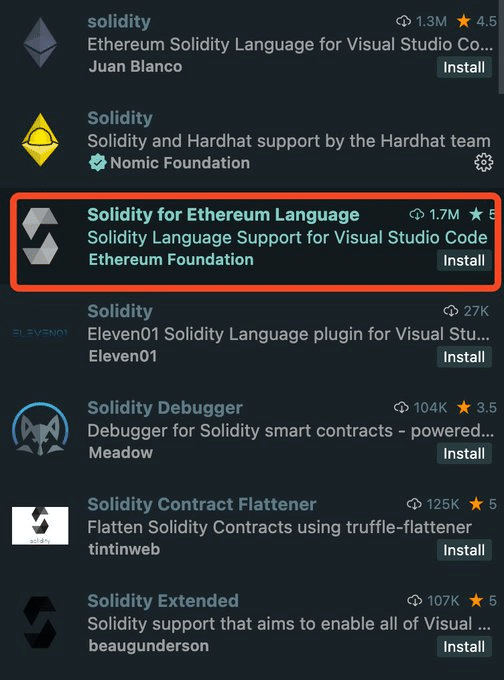
Image Credit: Hackingblogs
Fake Solidity Addon Available on VS Code will hack your windows system : Many Undetected
- A fake Solidity addon was found on the VS Code marketplace.
- The malicious extension was downloaded 1.7 million times in one day.
- The extension executes the attack fully in memory, leaving no evidence on the disk.
- It uses PowerShell for execution and recognizes VMs to protect against reverse engineering.
Read Full Article
9 Likes
Amazon
432

Image Credit: Amazon
Summer 2024 SOC 1 report now available in Japanese, Korean, and Spanish
- AWS has announced the availability of the AWS SOC 1 report in Japanese, Korean and Spanish to improve customer engagement and strengthen its alignment with regulatory requirements.
- Though these versions will not include an independent opinion issued by the auditors, stakeholders can reference the original English version for this information.
- The report will now be translated each quarter, and the newly added versions will provide year-round coverage for all languages when combined with the English versions in the spring and fall.
- Customers can download the translated reports through AWS Artifact, a self-service portal for on-demand access to compliance reports.
- The summer 2024 SOC 1 report contains 177 services in scope, with the updated list available on its website.
- AWS continuously aims to bring services in scope for its compliance programs, with its offerings accounting for customers' architectural and regulatory needs.
- For more information on compliance and security programs, see the AWS Compliance Programs website.
- AWS inspires feedback, and customers can contact the AWS Compliance team through its Contact Us page.
Read Full Article
26 Likes
Sentinelone
396

Image Credit: Sentinelone
The Good, the Bad and the Ugly in Cybersecurity – Week 40
- Three IRGC employees have been indicted by the DoJ for hacking former President Donald Trump’s campaign and targeting U.S. campaign officials, members of the media and several NGOs.
- Malicious packages have been found in the Python Package Index (PyPI), posing as cryptocurrency wallet management tools, designed to steal data and digital assets.
- CISA warns of a critical vulnerability in Ivanti's Endpoint Manager (EPM) appliances, which is being actively exploited by threat actors.
- The vulnerability, tracked as CVE-2024-29824, affects EPM’s Core server and allows unauthenticated attackers in the same network to perform remote code execution.
- A joint advisory released by U.S and U.K. cybersecurity agencies warn that IRGC actors are likely to continue using similar tactics to influence elections and target high-profile individuals.
- Threat actors are creating new schemes to drain wallets, ongoing vigilance, and a focus on continuous monitoring and community awareness continue to be critical across both the open-source software and cryptocurrency ecosystems.
- Ivanti appliances have been a frequent target of zero-day exploits this year, including a spate of attacks on the firm’s Connect Secure (ICS) and Policy Secure (IPS) network access control appliances, ZTA gateways, and Cloud Services Appliance.
- Instead of triggering malicious actions during installation, packages remain dormant until specific actions are called via names such as "trustdecoderss" and "phantomdecoderss".
- The Department of State has announced a $10 million reward for information on Jalili, Aghamiri, and Balaghi’s whereabouts.
- Ivanti's CEO outlines the company’s goals to revamp their core engineering, security, and vulnerability management practices.
Read Full Article
23 Likes
Securityaffairs
284
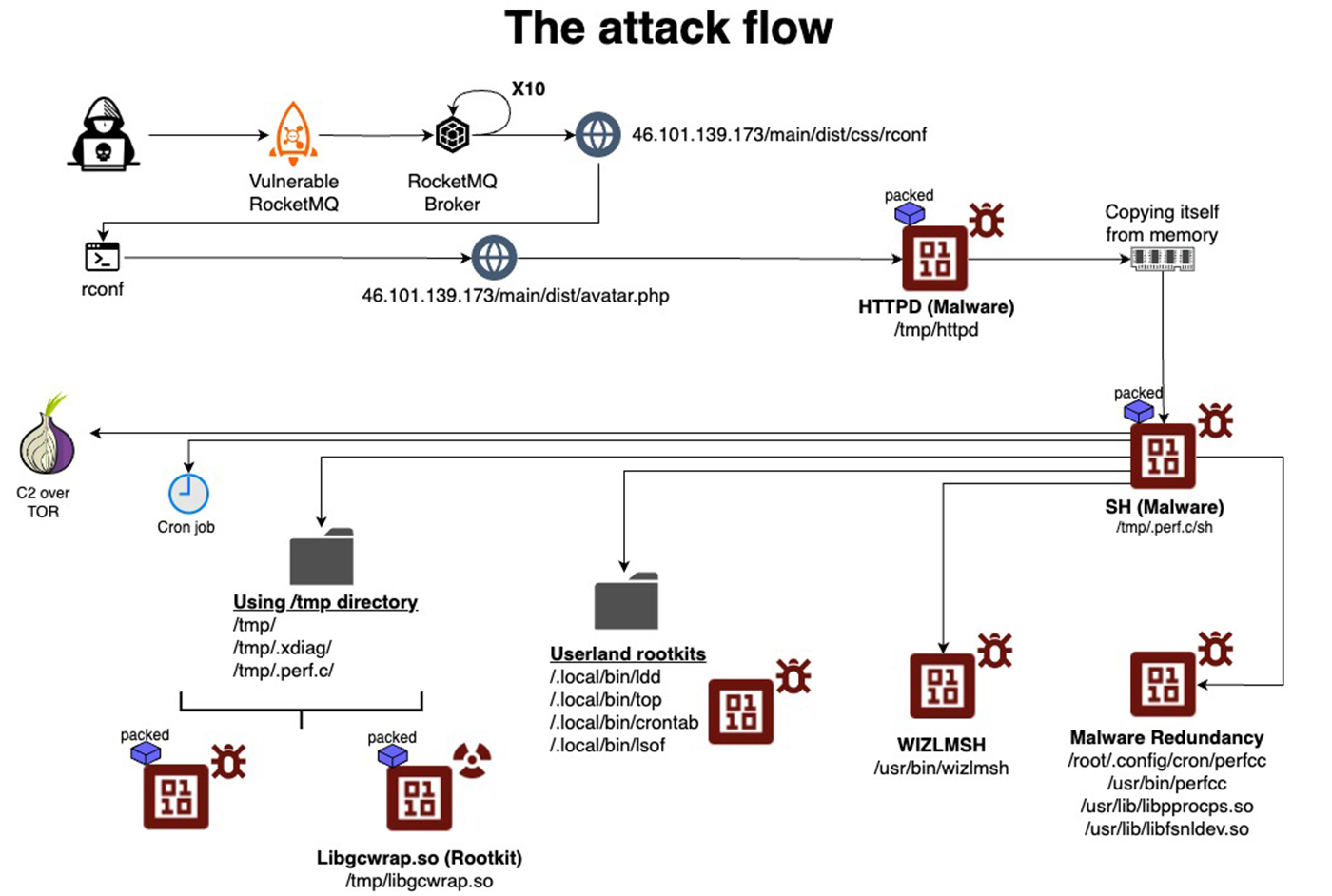
Image Credit: Securityaffairs
New Perfctl Malware targets Linux servers in cryptomining campaign
- Perfctl malware targets misconfigured Linux servers to deploy cryptocurrency miners and proxyjacking software.
- The malware employs rootkits to conceal its presence and operates as a service in the background.
- It downloads the main payload from an attacker-controlled server and utilizes advanced evasion techniques to bypass detection.
- The main impact is resource hijacking, with the malware running a monero cryptominer to exhaust CPU resources.
Read Full Article
17 Likes
Securityaffairs
9

Image Credit: Securityaffairs
Microsoft and DOJ seized the attack infrastructure used by Russia-linked Callisto Group
- Microsoft and the US Department of Justice (DoJ) have seized over 100 domains linked to Russia-based Callisto Group.
- The DoJ has also revealed a warrant to seize 41 domains used by the group for computer fraud in the US.
- Microsoft took separate action to restrain another 66 domains.
- Between January 2023 and August 2024, Callisto Group targeted over 30 civil society organisations by deploying spear-phishing campaigns.
- A partially unsealed affidavit reveals that the APT group targeted companies and employees of various US departments and military contractors.
- Microsoft also admitted that disrupting the domains will not completely stop the group’s spear-phishing activities.
- The Callisto Group, also known as Seaborgium, Star Blizzard, ColdRiver, and TA446, is an advanced persistent threat group.
- It is known to have targeted NATO countries, including the Baltics, Nordics, and Eastern Europe regions, as well as numerous other sectors, since at least 2015.
- The UK government also recently revealed that the FSB, a Russian intelligence unit, was behind the Callisto Group and its activities, which include disrupting UK politics and democratic processes.
- While dispruting the infrastructure will impact Callisto's operations, Microsoft admitted it is likely that the group will establish new infrastructure at some point.
Read Full Article
Like
Hackersking
249

Image Credit: Hackersking
Zero-Day Exploits in Social Media – The rise of unpatched vulnerabilities on platforms like WhatsApp
- Social media platforms like WhatsApp, Instagram, and Facebook are now essential for communication and business, making them prime targets for cybercriminals.
- A growing threat to these platforms is zero-day exploits—security flaws that developers haven't discovered or fixed. Hackers use these vulnerabilities to attack users, steal information, and disrupt systems.
- A zero-day exploit is a type of cyberattack that takes advantage of a security weakness in software that the developer or antivirus programs don’t know about yet.
- Some common ways attackers use zero-day exploits include web browsers, email attachments, and even hardware and IoT devices.
- Typical targets for zero-day attacks include government agencies, large companies, and ordinary users. Zero-day exploits have become a serious concern for both individuals and businesses.
- Case studies of zero-day exploits on social media include WhatsApp Pegasus Spyware Attack (2019), Facebook's User Data Breach (2018), and TikTok Account Takeover (2020).
- These attacks have had an impact on users, such as privacy breaches, account takeovers, financial loss and on the platforms, such as loss of user trust, legal actions, emergency security fixes, and cybersecurity changes.
- Challenges in addressing zero-day exploits include identifying the vulnerability, planning and delivering the attack, triggering the exploit, achieving the objective, and staying hidden.
- The future of zero-day exploits in social media is likely to become more concerning, putting millions of users at risk before a fix is available.
- Platforms like WhatsApp, Instagram, and Facebook will need to continue to improve their cybersecurity measures and bug bounties to protect users from such breaches.
Read Full Article
14 Likes
Securityaffairs
90

Image Credit: Securityaffairs
Dutch police breached by a state actor
- The Dutch government blames a 'state actor' for hacking a police system, exposing the contact details of all police officers.
- The incident occurred on September 26, 2024, and the police have reported the security breach to the Data Protection Authority.
- Attackers gained access to work-related contact details of multiple officers, including names, emails, phone numbers, and some private information.
- The Dutch police believe a state actor was behind the breach, and investigations are ongoing.
Read Full Article
5 Likes
Kaspersky
185

Image Credit: Kaspersky
How to snoop on what an Apple Vision Pro user is typing | Kaspersky official blog
- Researchers have exposed an attack that breaches the confidentiality of the sensitive information entered by users of Apple Vision Pro's headset.
- The attack, dubbed GAZEploit, intercepts text input written by the eyes' movement patterns of the headset's user, reconstructed via the avatar's mirrored movements.
- Text is input in visionOS by a virtual keyboard and eye tracking is used to mimic human eye focus on which keys are pressed.
- By using biometric data fed by Vision Pro's precise sensors, researchers identify where a user's eyes move, enabling them to reconstruct the characters entered on the keyboards.
- The system has three virtual keyboards to further disguise which keyboard is in use: passcode, QWERTY, and number & special characters.
- The neural network identifies text-input sessions and uses scenario-specific data-entry techniques to improve interpretation of where the user's gaze was trained.
- At maximum precision, only a third of entered characters are correctly identified.
- The attack can dramatically reduce the number of attempts needed to brute-force passwords and puts targeted high-profile attacks at risk.
- The vulnerability was patched in the latest versions of visionOS, but users are advised to exercise caution when entering passwords during video calls and to use a password manager to create and store them.
Read Full Article
11 Likes
Dataprivacyandsecurityinsider
58

Image Credit: Dataprivacyandsecurityinsider
Woeful Lack of Training for Chatbot Use in Workplace
- Over one-third of employees share sensitive work information with AI tools without permission.
- Generative AI models can inadvertently store and disclose sensitive or proprietary data shared by employees.
- Examples include a financial services firm experiencing a data breach due to unsecured storage by a chatbot and an employee unknowingly training Grammarly on confidential data.
- Organizations need to develop AI governance programs, provide training to employees, and approve appropriate AI tools to mitigate risks.
Read Full Article
3 Likes
Dataprivacyandsecurityinsider
397

Image Credit: Dataprivacyandsecurityinsider
T-Mobile’s $31.5 Million Data Protection and Cybersecurity Settlement with the FCC
- The FCC reached a $31.5 million data protection and cybersecurity settlement with T-Mobile.
- T-Mobile agreed to remediate security flaws and improve cyber hygiene.
- They will implement standard security safeguards and a modern zero trust architecture.
- T-Mobile will invest $15.75 million in cybersecurity and pay a civil penalty of $15.75 million.
Read Full Article
23 Likes
Dataprivacyandsecurityinsider
9

Image Credit: Dataprivacyandsecurityinsider
OCR Settles Fourth Ransomware Investigation
- The Office for Civil Rights of the Department of Health and Human Services (OCR) has reached a $250,000 settlement with Cascade Eye and Skin Centers following a ransomware attack on the organization.
- This is the fourth settlement against a victim of a ransomware attack. Ransomware and hacking are the primary cyber-threats in health care, with a significant increase in reported breaches involving ransomware attacks.
- The OCR's investigation found that 291,000 files were affected by the attack, revealing potential violations of HIPAA by Cascade for failing to conduct a risk analysis and have adequate system monitoring.
- This settlement serves as a reminder that even victims of criminal attacks must still adhere to HIPAA regulations, emphasizing the importance of having a robust compliance program in place.
Read Full Article
Like
For uninterrupted reading, download the app