Info. Security News News
Dataprivacyandsecurityinsider
147

Image Credit: Dataprivacyandsecurityinsider
Marriott and Starwood Settle on Consent Agreement with FTC for Data Breaches
- Marriott and Starwood have settled on a consent agreement with the Federal Trade Commission (FTC) for data breaches.
- The data breaches occurred between 2014 and 2020, affecting over 344 million consumers worldwide.
- Marriott failed to implement reasonable security measures, resulting in unauthorized access to personal information.
- As part of the settlement, Marriott will provide deletion options for personal information, enhance security measures, and pay a $52 million penalty to states.
Read Full Article
8 Likes
Dataprivacyandsecurityinsider
84

Image Credit: Dataprivacyandsecurityinsider
Privacy Tip #416 – Impersonation is the Most Prolific Phishing Tactic in 2024
- Phishing attacks remain a prominent cause of security incidents and data breaches. According to security software firm Egress, impersonation is the most prolific phishing tactic occurring in 2024.
- Among the phishing emails detected by Egress, 26% appeared to be sent from brands that had no business relationship with the recipient.
- Egress reports that the top-five words used in phishing include “urgent,” “sign,” ”password,” “document,” and “delivery.”
- Egress has found that employees in their initial 2-7 weeks on the job were the most targeted.
- The report states that employees are only “accurately reporting” 29% of phishing emails received.
- The most impersonated brands are Adobe, Microsoft, Chase, and Meta. Two most impersonated internal systems were e-signatures and employee feedback surveys.
- Hackers are also impersonating celebrities like Warren Buffet or Mackenzie Scott along with CEO, HR, IT, and Finance departments to increase threat outreach.
- There was a 28% increase in phishing emails sent in the second quarter of 2024 over the previous quarter, with 44% of phishing emails originating from already compromised accounts.
- Phishing emails containing QR codes are rising. Educating teams is critical to avoid these attacks.
- Appropriate cybersecurity training should be conducted to help employees identify malicious activity and potential attacks through the analysis of such phishing techniques.
Read Full Article
5 Likes
Medium
143
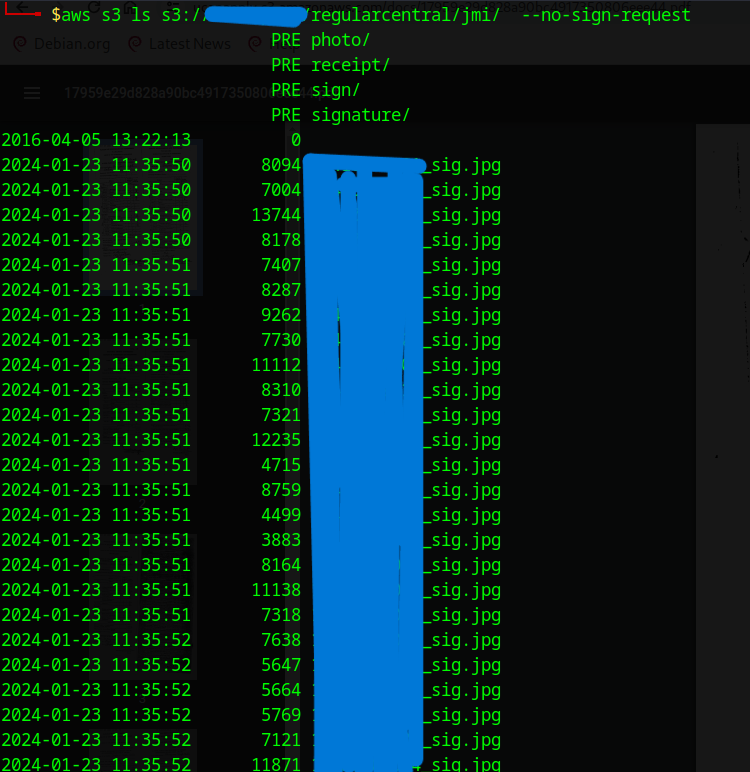
Image Credit: Medium
How a Misconfigured S3 Bucket Became a 100GB+ Data Privacy Breach
- An Amazon S3 bucket named xyz-abc.s3.amazonaws.com was found to be misconfigured and accessible.
- The misconfigured bucket contained sensitive data such as student phone numbers, certificates, signatures, and photos from various central universities and state government public service commission candidates.
- The data breach also included a banking employee offer letter with employee ID, Oracle EIN, and official email.
- The incident was reported to CERT-In (Computer Emergency Response Team-India) for investigation and action.
Read Full Article
8 Likes
Sentinelone
354

Image Credit: Sentinelone
The Good, the Bad and the Ugly in Cybersecurity – Week 41
- Mark Sokolovsky, a Ukrainian national who ran Raccoon Infostealer, has pleaded guilty, a malware-as-a-service (MaaS) linked to the theft of millions of sensitive data like PII, bank account details, and cryptocurrency information.
- Several Units of law enforcement group was able to seize two extensive dark market places: Bohemia and Cannabia.
- Two advanced toolsets used for cyberattacks on embassies and government organizations have been identified this week, attracting attention to little-known threat actor, GoldenJackal.
- GoldenJackal’s latest toolset drives malware propagation, performs data collection and leverages machine servers to stage and distribute payloads to other hosts for breaching air-gapped networks.
- Mamba 2FA, a phishing-as-a-service (PhaaS) platform, has been targeting Microsoft 365 account holders through convincing login pages and various security evasion techniques.
- Mamba 2FA phishing kit offers advanced phishing templates for services like OneDrive, SharePoint, and Microsoft login pages and enables attackers to customize phishing pages and reflect the branding of targeted organizations.
- Most recently, Mamba 2FA has improved its stealth tactics and became hard for organizations to detect unusual logins.
- To defend against sophisticated AiTM phishing tactics, organizations can implement hardware security keys, certificate-based authentication, geo-blocking, IP and device allowlisting, and limit token lifespans.
- GoldenJackal and Mamba 2FA are two ugly faces in cybersecurity.
- These events demonstrate the importance of international collaboration between law enforcement agencies to disrupt cybercriminal operations.
Read Full Article
21 Likes
Securityintelligence
120

Image Credit: Securityintelligence
How governance, risk and compliance (GRC) addresses growing data liability concerns
- Executives feel inadequate data quality, accessibility and security are exposing their businesses to unnecessary risks, as only 29% of tech leaders feel their data meets the necessary standards to scale generative AI.
- The consequences of poor data practices in the AI age can be severe, with inaccurate models, biased outputs and security vulnerabilities leading to potential financial losses for inefficient AI models, legal headaches due to data breaches, mismanagement of sensitive information or failure to comply with data regulations.
- Governance, risk and compliance (GRC) provides a solution to the growing data liability problem, with the framework aligning IT practices with business objectives to manage risks and ensure regulatory compliance is maintained. GRC creates clear policies for data governance, granting the necessary infrastructure for scaling AI applications.
- GRC streamlines processes such as risk assessments, compliance management and audits to provide businesses with a centralized way to manage data governance, track compliance with regulations and assess risks in real time. By automating GRC tasks, organizations can reduce the administrative burden on their IT teams and help them meet compliance requirements.
- The study by IBM reveals that among tech leaders, only 43% say their organizations are effective at delivering differentiated products and services and only half of tech leaders say their teams have the knowledge and skills to incorporate new technology.
- A strong compliance program keeps the organization in line with data privacy laws, such as General Data Protection Regulation (GDPR) or the California Consumer Privacy Act (CCPA).
- GRC encourages collaboration between IT, finance, legal and business units to create clear policies for data governance, which means that data is handled consistently across the organization.
- By adopting a robust GRC framework, organizations can mitigate these risks and turn data management into a competitive advantage. GRC provides the structure needed to govern data, manage risks and ensure compliance, thus enabling businesses to thrive in the AI-driven future.
- An often overlooked aspect of data liability is the role of diversity in AI development, and the IBM study highlights the need to bring more women into IT and AI roles.
- GRC software can provide valuable insights by correlating data management practices with business outcomes, helping organizations meet compliance requirements and reduce the administrative burden on their IT teams.
Read Full Article
7 Likes
Kaspersky
237

Image Credit: Kaspersky
Security and privacy settings in Strava | Kaspersky official blog
- Strava can track running, cycling and hiking. It remains independent; all other major running apps were acquired by sportswear giants.
- The app exposes sensitive data, including location, by default.
- To fix this, Strava offers privacy settings. It's strongly recommended to make profile private and set other options so that maps and location data remain hidden to either followers or only you.
- The privacy settings need to be adjusted manually as they are not retroactive, however, past activities can be manually hidden as well.
- Those who exercise often at sensitive locations can toggle off the option to contribute their activity data to de-identified, aggregate data sets.
- A feature to publicly share photos should be disabled; in case Strava decides to change things, it is best to avoid that possibility.
- Also, one should toggle 'Do Not Share My Personal Information' to prevent Strava from selling your data to third parties.
- The privacy settings as above need to be done manually according to the article.
- The Kaspersky Premium system can further maximise privacy in such situations and protect from digital identity theft.
- Readers can also review and adapt privacy settings utilizing Privacy Checker on Kaspersky's website.
Read Full Article
14 Likes
Kaspersky
147

Image Credit: Kaspersky
How to properly configure privacy in running apps | Kaspersky official blog
- Fitness apps that track data such as geolocation information can put users at risk of malicious actors accessing that information and using it for criminal or other unsavory purposes.
- To stay safe, users should exercise caution when choosing, using and selecting the privacy setting on fitness apps.
- First, users should carefully read through each app's privacy policy to learn what data is collected, for what purposes, what rights users have regarding their personal data, and what data might be shared with third parties.
- It's also recommended to install at few different apps as possible as keeping fewer apps decreases the risk of data leaks.
- Additionally, users should restrict which data fitness apps access, with the ultimate goal of limiting that access to only the data required for the app to work.
- Users should also check to whom fitness apps share data and consider if the app is sharing data with individuals or parties they do not know.
- Finally, users should routinely check their smartphone privacy and security settings to ensure apps do not have unnecessarily open access to their data.
- It is important to note that privacy settings will not protect users if someone accesses their account with their password, as most popular running apps currently do not support two-factor authentication.
- Some popular running apps that have specific guidelines about setting up privacy and protection are Strava, Nike Run Club, MapMyRun, adidas Running (formerly Runtastic), and ASICS Runkeeper.
Read Full Article
8 Likes
Schneier
26

IronNet Has Shut Down
- IronNet, the cybersecurity company founded by former NSA director Keith Alexander, has shut down.
- The company, which had a unicorn valuation of $3 billion, went bankrupt and ceased operations last year.
- IronNet's failure has led to accusations of misleading investors, questionable business practices, and associations that could have made the company vulnerable to interference.
- Former employees and analysts have expressed disappointment and shame over their involvement with the company.
Read Full Article
1 Like
Securityaffairs
134

Image Credit: Securityaffairs
Iran and China-linked actors used ChatGPT for preparing attacks
- OpenAI announced the disruption of over 20 cyber and influence operations involving Iranian and Chinese state-sponsored hackers.
- Three threat actors, including CyberAv3ngers linked to Iran's IRGC, were found to be using OpenAI's ChatGPT for launching cyberattacks.
- The observed behavior involved reconnaissance, searching for vulnerabilities, code debugging assistance, and seeking information on security tools and vulnerabilities.
- Another Iranian group, Storm-0817, used ChatGPT for Android malware development, creating an Instagram scraper, and translating LinkedIn profiles into Persian.
Read Full Article
8 Likes
Hackersking
259

Image Credit: Hackersking
Unlocking the Secrets: The Ultimate Guide to Finding Instagram Phone Number
- Finding someone's phone number on Instagram can be significant in different scenarios, such as recovering a misplaced account, detailing an issue, or reaching somebody for trade purposes.
- Instagram's privacy settings permit clients to control what data is unmistakable to others, making it troublesome for third parties to get to such subtle elements.
- A few clients may list their phone numbers or contact subtle elements in their Instagram bio, particularly for commerce accounts.
- If you're attempting to contact a commerce or influencer, the Contact button in their trade accounts is one of the most effortless ways to get in touch.
- The Instagram Offer assistance Center is the official back framework for any issues clients may confront, counting account recuperation or announcing issues.
- Although Instagram does not freely offer a coordinate phone number for client bolster, clients can reach out to the stage by means of mail.
- Online gatherings, such as Reddit or Quora, and community stages like Facebook bunches, regularly have clients who examine common Instagram issues and offer arrangements.
- Instagram is known for deferred reactions to bolster inquiries. Tirelessness is key when attempting to get help.
- Finding a phone number connected to Instagram can be a challenging prepare due to the platform's center on protection and security.
- Ultimately, it's critical to approach any look for Instagram phone numbers carefully, considering both lawful and moral concerns.
Read Full Article
15 Likes
Securityaffairs
380

Image Credit: Securityaffairs
Internet Archive data breach impacted 31M users
- The Internet Archive disclosed a data breach, impacting over 31 million users of its 'The Wayback Machine.'
- The breach exposed user records including email addresses, screen names, and bcrypt password hashes.
- The stolen data has been shared with the data breach notification service Have I Been Pwned.
- The Internet Archive founder confirmed a DDoS attack has caused service outages.
Read Full Article
22 Likes
Startupnation
246

Image Credit: Startupnation
Balancing Cybersecurity and Budget in Startups: 15 Real-Life Examples
- Start with Cost-Effective Security Measures
- Outsource Cybersecurity to Save Costs
- Prioritize Protection with Scalable Measures
- Adopt Cloud-Based Security on a Budget
- Emphasize Cybersecurity Training for Employees
- Focus on Strategic, Essential Security Measures
- Negotiate with Security Companies for Deals
- Enhance Security Through Staff Vigilance
- Select Mid-Tier SSL and Built-In Fraud Detection
- Partner with University Cybersecurity Programs
- Secure Startup-Friendly Discounts from New Firms
- Innovate with Open-Source Firewall Protection
- Hold Hackathon Contests
- Adopt Lean Data Practices
- Save with Open-Source SIEM Implementation
Read Full Article
14 Likes
Amazon
304

Image Credit: Amazon
Strengthening security in the era of generative AI: Must-attend sessions at re:Invent 2024
- AWS sees security as a foundational enabler for organizations looking to innovate with generative AI solutions quickly and securely.
- Re:Invent 2024 sessions will guide attendees on how to secure generative AI workloads to protect data and navigate governance, risk, and compliance.
- Notable keynotes and innovation talks by senior AWS leaders include CEO Keynote with Matt Garman, Security insights and innovation from AWS with Chris Betz, and Architectural methods & breakthroughs in innovative apps in the cloud with Shaown Nandi and Ben Cabanas.
- Breakout sessions, chalk talks, code talks, and workshops are designed to deepen expertise in securing generative AI.
- Some of the must-attend sessions include SEC214 for using AWS generative AI services to enhance customer experiences while navigating security challenges, and SEC327 for optimizing cloud network design to power transformative applications more securely.
- Attendees can also interact with AWS Security experts in the Security Activation area of the expo floor for one-on-one conversations on various topics, including generative AI security.
- Finally, attendees can unwind and connect at the world-renowned re:Play party.
- Register for the re:Invent 2024 event for a chance to learn from AWS security experts on securing generative AI workloads.
- Anna Montalat and Matt Saner are Senior Product Marketing Manager and Senior Manager respectively at AWS and have years of experience in the field.
Read Full Article
18 Likes
Hackingblogs
308
Image Credit: Hackingblogs
NASA Was Hacked : Projects were accessed indirectly through AOSense
- STORMOUS X Ransomware leaked data from AOSense, providing an indirect means of accessing NASA-related projects and documents.
- The ransom demand is $5 million, and around 1 terabyte of accounting data was exposed.
- The exposed data includes information on AOSense's commercial sales, subcontracts, purchasing, intellectual property, administrative data, and more.
- A portion of the recovered data will be released, with a warning that more data will be sold and leaked if no resolution is reached by the end of the week.
Read Full Article
18 Likes
Securityaffairs
8
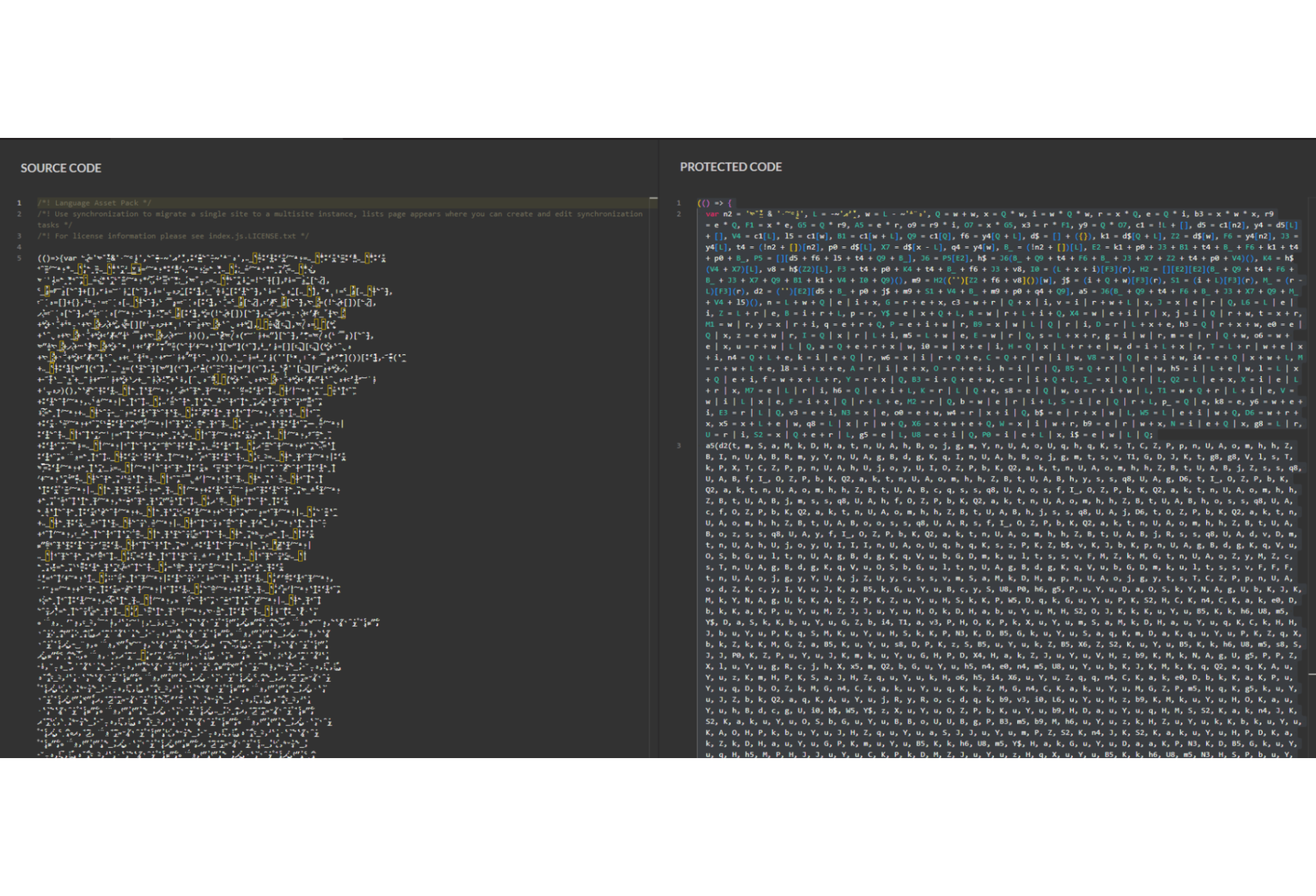
Image Credit: Securityaffairs
E-skimming campaign uses Unicode obfuscation to hide the Mongolian Skimmer
- Jscrambler researchers uncovered a skimming campaign using unique JavaScript obfuscation with accented characters to hide a skimmer named Mongolian Skimmer.
- The attackers used unusual Unicode characters for variables and function names.
- The skimmer was named “Mongolian Skimmer” after researchers found it used the Unicode character “Mongolian Letter OE” as an identifier in the code.
- The Mongolian Skimmer employs common techniques such as DOM monitoring, data exfiltration, DevTools detection, and anti-debugging measures to evade detection and tampering.
Read Full Article
Like
For uninterrupted reading, download the app