Info. Security News News
Dataprivacyandsecurityinsider
76

Image Credit: Dataprivacyandsecurityinsider
Effective October 1st: Montana’s New Consumer Data Protections Law
- Montana's new consumer data protections law, the Montana Consumer Data Privacy Act (MCDPA), came into effect on October 1st.
- The MCDPA grants Montana residents the right to access, obtain copies, and request deletion of their personal information held by online companies.
- It also allows them to opt-out of targeted advertising or sale of their data to third parties.
- The MCDPA features a universal opt-out requirement, providing users with the option to opt out across multiple websites simultaneously.
Read Full Article
4 Likes
Dataprivacyandsecurityinsider
139

Image Credit: Dataprivacyandsecurityinsider
California on the Forefront of Tackling AI Risks to Consumers
- The State of California has taken the lead in investigating the risks of generative artificial intelligence (GenAI) tools and developing policies to address them.
- Governor Gavin Newsom signed an amendment to the California Consumer Privacy Act, which includes neural data as protected data covered by the law.
- The amendment requires private companies collecting brain data to provide notice of collection, allow consumers to limit disclosure to third parties, and request deletion.
- Governor Newsom also signed 17 bills to regulate GenAI technology, including combating deepfakes, requiring AI watermarking, and protecting children and workers.
Read Full Article
8 Likes
Dataprivacyandsecurityinsider
275

Image Credit: Dataprivacyandsecurityinsider
Privacy Tip #415 – It’s National Cybersecurity Awareness Month!
- October is Cybersecurity Awareness Month, and it's a busy time for professionals in the field.
- President Biden declared October 2024 as National Cybersecurity Month, urging businesses, institutions, and individuals to take action to protect against cyber threats.
- The Cybersecurity and Infrastructure Security Agency (CISA) emphasizes the importance of raising awareness about cybersecurity and provides tips for online safety.
- Individual organizations like Webster Bank are also promoting cybersecurity awareness and sharing tips to stay safe online.
Read Full Article
16 Likes
Amazon
112
Image Credit: Amazon
Customer compliance and security during the post-quantum cryptographic migration
- Amazon Web Services has started to introduce quantum-resistant key exchange in transport protocols used by customers for long-term confidentiality. In this transition, AWS will prioritize quantum-resistant algorithms over classical ones, even if that means the introduction of a small delay to the connection. Customers must configure or use clients that negotiate the algorithms they prefer and trust when connecting to AWS services. AWS operators are responsible for enabling priority for modern algorithms in connections to their services.
- Post-quantum cryptography involves introducing post-quantum hybrid key exchanges in protocols like TLS 1.3 or SSH/SFTP, thus AWS is in the process of migrating to post-quantum cryptography in network connections to its services. New cryptographic algorithms are designed to protect against a future cryptanalytically relevant quantum computer (CRQC) which could threaten the algorithms we use today.
- Figure 1 shows how a client sends a Keyshare value for classical ECDH with P256, and a PQ-hybrid P256+MLKEM768. Now let’s say that the server supports ECDH curve P256 and PQ-hybrid P256+Kyber512, but not P256+MLKEM768. If the server does not support ML-KEM, it would select classical ECDH key exchange with P256. In these cases where the clients and servers don’t deploy the same algorithms, a connection won’t fail, but the connection will use classical-only algorithms.
- During the migration phase, AWS services will prioritize PQ hybrid algorithms for customers that advertise support for these algorithms, even if that means a small slowdown in the initial negotiation phase. While in the post-quantum migration phase, customers who choose to enable quantum-resistance have made a choice which shows that they consider the CRQC risk as important. AWS will honor the customer’s choice, assuming that quantum resistance is supported on the server side.
- Technical details for developers are provided, such as how to verify post-quantum key exchanges, how to transfer a file over a quantum-resistant SFTP connection with AWS Transfer Family and more. AWS customers are expected to enable new quantum-resistant algorithms introduced in AWS services on the client side or the server side of the customer-managed endpoint.
- Cryptographic migrations can introduce intricacies to cryptographic negotiations between clients and servers. During the migration phase, AWS services will mitigate the risks of these intricacies by prioritizing post-quantum algorithms for customers that advertise support for these algorithms. AWS customers are responsible for enabling quantum-resistant algorithms or having these algorithms enabled by default in their applications that connect to AWS.
- The Shared Responsibility Model can help relieve the customer’s operational burden as AWS operates manages and controls the components from the host operating system and virtualization layer down to the physical security of the facilities in which the service operates.
- Customers must use clients that enable algorithms and negotiate cryptographic ciphers when connecting to AWS. It is the responsibility of the customer to configure or use clients that only negotiate the algorithms the customer prefers and trusts when connecting. AWS provides Customer Compliance Guides (CCGs) to support customers, partners, and auditors understand how compliance requirements map to AWS service security recommendations.
- Incidents like the SolarWinds hack, in which attackers compromised the company’s Orion monitoring tool in to penetrate sensitive government agencies and organizations, illustrated the role that external suppliers can play, and the importance of guarding the supply-chain against sophisticated cyber attacks.
- If you have feedback or questions about this post, submit comments in the Comments section or contact AWS Support. AWS PQC efforts are open and transparent, for more details, refer to our PQC page.
Read Full Article
6 Likes
Hackersking
167
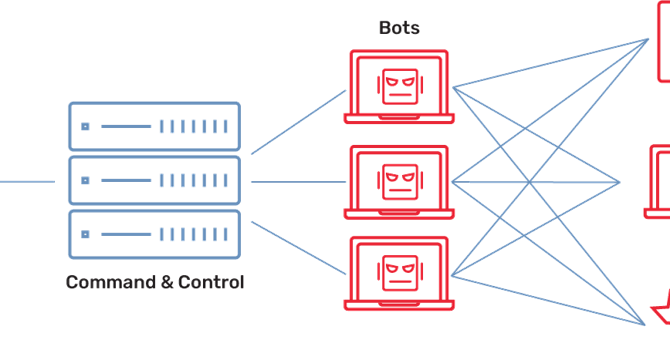
Image Credit: Hackersking
Social Media Botnets – Hackers leveraging bots for large-scale attacks.
- Hackers are leveraging social media botnets for large-scale attacks, manipulating trends, spreading disinformation, and executing social engineering attacks.
- Botnets are a network of bots, automated software programs that perform tasks on the internet, ranging from benign to malicious actions.
- Social botnets refer to bots that are specifically programmed to operate on social media platforms, used to manipulate public opinion, spread fake news, launch coordinated spam campaigns or carry out social engineering attacks.
- Social botnets spread malware, harvest intelligence on targets, and spread influence on a massive scale.
- Botnet operators create fake social media profiles, link them together, and use machine learning models to generate content mimicking human behaviour.
- Types of social botnet attacks include hashtag hijacking, trend-jacking, mass posting, click/like farming and retweet storm.
- Social botnets can be monetized by selling fake followers, engagement, ad fraud, spamming/phishing, spreading malware or political influence.
- Social botnets can negatively impact your marketing efforts and damage your brand. Their impacts include manipulating social media trends, creating false narratives, and amplifying divisive content.
- Social botnets are difficult to trace as botnet operators employ techniques to evade detection.
- Researchers have developed methods, such as data mining and machine learning techniques, to detect and classify malicious social bots.
Read Full Article
10 Likes
Infoblox
415

Image Credit: Infoblox
From Cognitive Overload to Clarity: The Infoblox Portal
- Infoblox has redesigned its Infoblox Portal to counter cognitive load and enhance the operational experience. The move is strategic and designed to streamline operations, improve productivity, and prepare Infoblox for the future of networking and security.
- The portal's new navigation model and interface are aimed at reducing cognitive load and improve capacity to manage crucial network services and security workloads, without feeling overwhelmed.
- This update is not just aesthetic, it paves the way for latest product releases and new features such as Infoblox Universal DDI Management, Infoblox Universal Asset Insights, and NIOS-X as a Service. These features will provide powerful and insightful data about users' networking environments.
- The Infoblox Portal provides out-of-the-box workspaces with custom-designed monitors, allowing users to quickly asses the health of their networking and security environments.
- The portal's UI emphasis is on user-friendliness, providing familiar designs and reducing the learning curve for new users whilst making the transition seamless for existing users.
- Infoblox Universal DDI Management enables infrastructural flexibility, minimizing the productivity loss associated with the context switching.
- Infoblox Universal Asset Insights provides valuable insight and in-depth analysis of assets and their behaviour, delivering critical data about the user's network and environment.
- NIOS-X as a Service enables rapid scaling and deployment of new resources and services.
- Infoblox Portal UI's update is aimed at empowering users to run a secure and scalable DDI solution using an intuitive experience.
- The update will also enhance user experience, make their job easier and increase efficiency and productivity.
Read Full Article
24 Likes
Securityaffairs
31
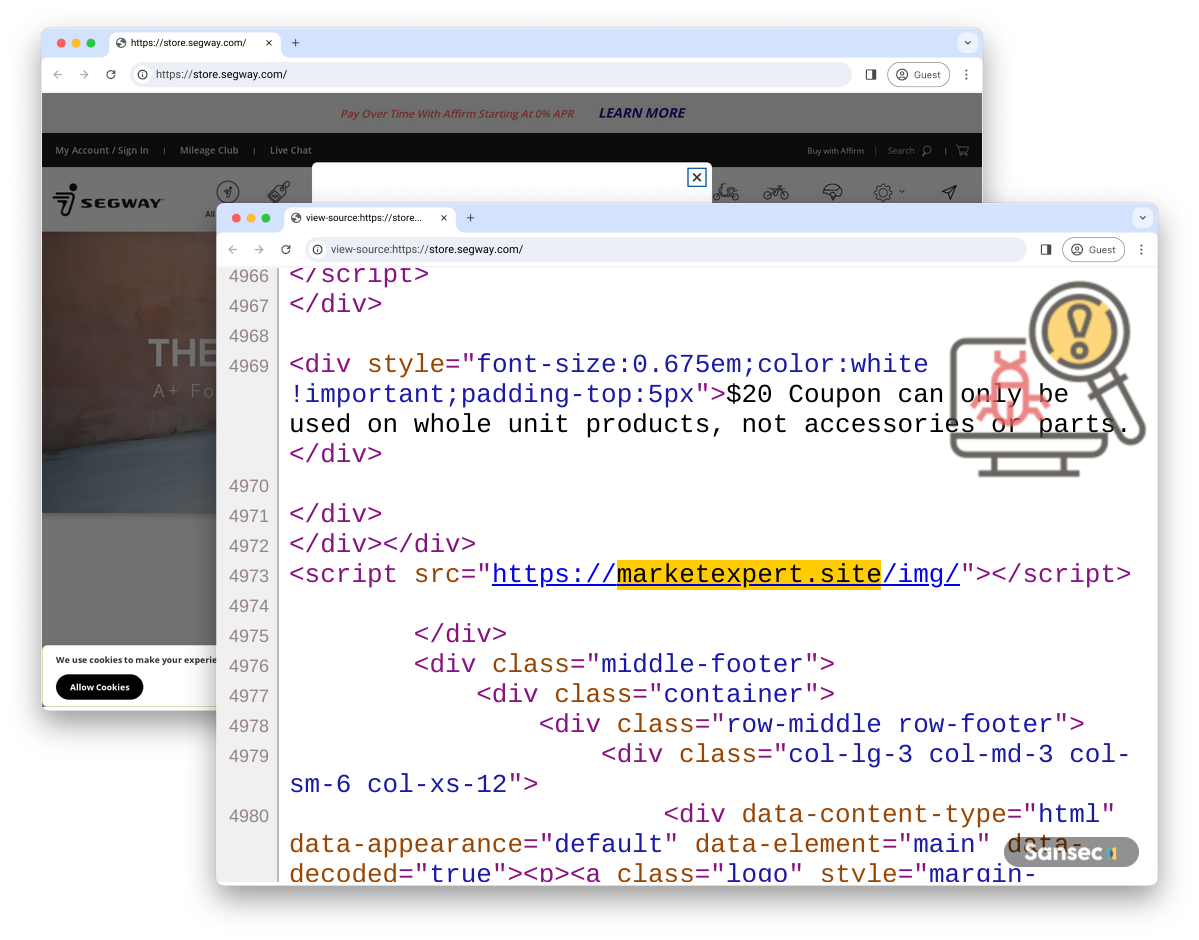
Image Credit: Securityaffairs
Thousands of Adobe Commerce e-stores hacked by exploiting the CosmicSting bug
- Over 4,000 unpatched Adobe Commerce and Magento stores have been compromised by exploiting critical vulnerability CVE-2024-34102.
- The flaw is an Improper Restriction of XML External Entity Reference (‘XXE’) vulnerability that could result in arbitrary code execution.
- CosmicSting (CVE-2024-34102) is the most severe bug impacting Magento and Adobe Commerce stores in two years, with hacks occurring at a rate of 3 to 5 per hour.
- Threat groups exploiting this vulnerability include Bobry, Polyovki, Surki, Burunduki, Ondatry, Khomyaki, and Belki.
Read Full Article
1 Like
Securityaffairs
279
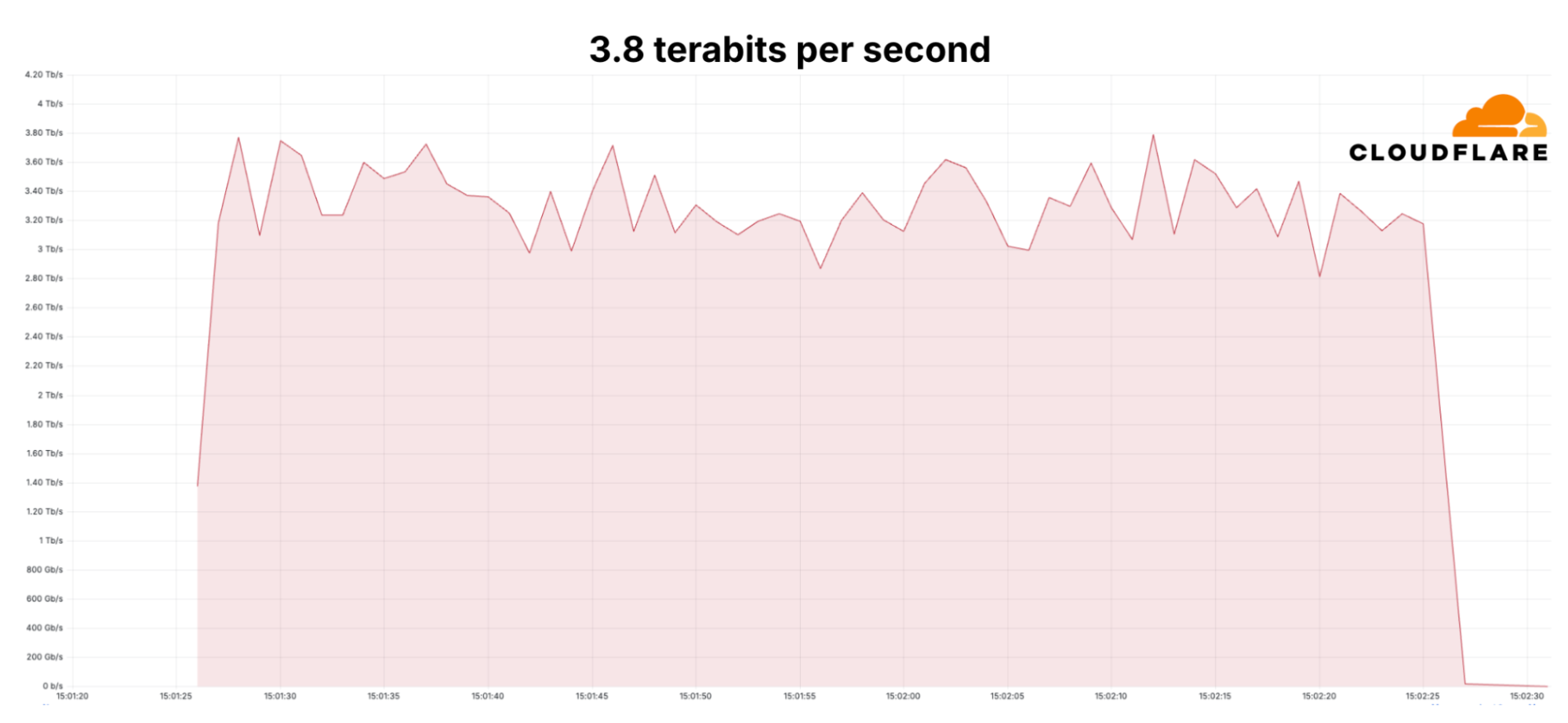
Image Credit: Securityaffairs
Cloudflare mitigated new record-breaking DDoS attack of 3.8 Tbps
- Cloudflare mitigated a record-breaking DDoS attack of 3.8 Tbps and 2.14 billion packets per second.
- Cloudflare has detected and mitigated over 100 hyper-volumetric DDoS attacks, with many exceeding 2 billion Pps and 3 Tbps.
- The attacks targeted the financial, internet, and telecom industries, originating from compromised devices globally.
- Cloudflare's network capacity and intelligent systems allow them to handle and automatically mitigate such large-scale attacks.
Read Full Article
16 Likes
Hackersking
302

Image Credit: Hackersking
Dark Web Data Markets: The Alarming Trade of Stolen Social Media Information
- The dark web serves as a marketplace for stolen data, where cybercriminals take advantage of weaknesses in popular platforms like Facebook, Instagram, and Twitter.
- Vulnerabilities in social media platforms expose users to cyber attacks, highlighting the need for proactive security measures and monitoring services.
- Hackers use various methods to profit from stolen data, including phishing and malware attacks, and compromised data is often sold for as little as $1 per account.
- Individuals must adopt strong security practices, including two-factor authentication, unique passwords, and dark web monitoring services to reduce the risks of identity theft.
- The dark web poses significant risks for personal information, with over 3,000 data breaches reported in 2023 and the anonymity of the dark web making detection and prevention difficult.
- Utilizing dark web monitoring services can detect compromised data in real-time, allowing users to take immediate action and mitigate the risk of identity theft.
- The ongoing battle for data privacy requires individuals and organizations to remain informed about emerging threats and take proactive measures to safeguard sensitive information.
- By adopting best practices for online security and utilizing monitoring services, users can significantly reduce their risk of dark web identity theft and other cyber threats.
- The fight for data privacy is ongoing, and staying vigilant is key to safeguarding personal information in an increasingly digital world.
- Following social media handles like Hackersking and exploring resources like Acronis True Image and Identity Guard can provide valuable insights into the evolving threat landscape.
Read Full Article
18 Likes
Securityaffairs
72

Image Credit: Securityaffairs
Telegram revealed it shared U.S. user data with law enforcement
- Telegram fulfilled over a dozen U.S. law enforcement data requests this year, potentially revealing the IP addresses or phone numbers of 100+ users.
- The social media platform updated its policy on data sharing with authorities, stating that it will share users' phone numbers and IP addresses in response to valid legal requests.
- The company's CEO, Pavel Durov, announced the policy update and mentioned that data shared with authorities will be included in quarterly transparency reports.
- The transparency report for the period January to September 2024 revealed 14 fulfilled requests from the U.S., affecting 108 users.
Read Full Article
4 Likes
HRKatha
81

Image Credit: HRKatha
Sajiv Nair elevated to CIO & CISO, ESDS
- ESDS Software Solution has elevated Sajiv Nair to the positions of chief information officer (CIO) and chief information security officer (CISO).
- Nair's elevation is expected to strengthen ESDS's position as a comprehensive provider of cloud, IT security, and managed services.
- With almost three decades of experience, Nair will oversee the strategic direction of information technology and security strategies at ESDS.
- Piyush Somani, founder and CEO of ESDS, believes that Nair's promotion will further consolidate the company's position as a leader in the IT and cybersecurity sectors.
Read Full Article
4 Likes
Siliconangle
939

Image Credit: Siliconangle
Metomic unveils AI-powered data classification solution for Google Workspaces
- Metomic has unveiled an AI-powered data classification solution for Google Workspaces.
- The solution allows for the discovery, classification, and securement of sensitive data at scale across Google Workspaces.
- It uses artificial intelligence to automate complex data management workflows and ensure data compliance.
- The solution enables organizations to implement effective security measures, adhere to regulations, and minimize data security risks.
Read Full Article
25 Likes
Sentinelone
189

Image Credit: Sentinelone
Singularity Cloud Native Security | Now Available in the Asia Pacific Region
- SentinelOne announces Cloud Native Security (CNS) now available in the Asia Pacific region.
- The launch includes support for the Australian Government Information Security Manual (ISM) framework.
- Cloud Native Security combines agentless and agent-based security capabilities with a focus on reducing noise and prioritizing evidence-based security.
- Customers praise CNS for its comprehensive threat detection, automated response capabilities, and ease of management.
Read Full Article
11 Likes
Securityaffairs
329

Image Credit: Securityaffairs
U.S. CISA adds Ivanti Endpoint Manager (EPM) flaw to its Known Exploited Vulnerabilities catalog
- The U.S. Cybersecurity and Infrastructure Security Agency (CISA) adds Ivanti Endpoint Manager (EPM) vulnerability to its Known Exploited Vulnerabilities catalog.
- The vulnerability (CVE-2024-29824) is an authentication bypass issue in Ivanti EPM, which could allow arbitrary code execution.
- Ivanti released security patches in May to address the vulnerability, but no reported attacks have taken place.
- CISA orders federal agencies to fix the vulnerability by October 23, 2024.
Read Full Article
19 Likes
Kaspersky
203

Image Credit: Kaspersky
How to protect schools from cyberthreats | Kaspersky official blog
- The number of cyberattacks targeting educational institutions is on the rise, with schools becoming attractive targets for cybercriminals.
- Factors contributing to schools' vulnerability include dependence on technology, valuable data, scarce resources, and low user awareness.
- Successful cyberattacks on schools can disrupt education, impact academic performance, and cause inconvenience for students and parents.
- To protect schools from cyberthreats, robust security measures, such as using dedicated cybersecurity software and conducting staff training, are recommended.
Read Full Article
12 Likes
For uninterrupted reading, download the app