Info. Security News News
Infoblox
233

Image Credit: Infoblox
Cybersecurity Awareness Month 2024 – Securing Our World Against Phishing Attacks
- October is Cybersecurity Awareness Month, and the theme for 2024 emphasizes simple, actionable steps people can take to bolster their online security.
- The National Cybersecurity Alliance outlines four key ways to stay safe online which include: use strong passwords and a password manager, turn on multifactor authentication, update software regularly and recognize and report phishing.
- Phishing is the most persistent and dangerous cyber threat used by attackers to steal personal information and security credentials.
- Infoblox leverages its DNS threat intelligence data to detect and block harmful phishing sites before users have a chance to click on any links that direct them there.
- DNS also provides an additional layer of threat defense throughout the attack lifecycle.
- The effectiveness of using DNS for threat defense is unparalleled, which is why it’s increasingly being viewed as a foundational pillar for cybersecurity.
- Governments around the world are embracing DNS as a security control to protect themselves, and Infoblox's DNS health and security assessments can help organizations elevate their DNS security posture.
- Protecting against phishing attacks is crucial for both businesses and individuals alike. Implementing core cybersecurity best practices such as strong passwords, MFA, phishing awareness, and software updates while considering advanced solutions like DNS security can help stay ahead of emerging cyber threats.
- Infoblox is dedicated to helping you secure your world.
Read Full Article
14 Likes
Securityaffairs
381

Image Credit: Securityaffairs
Qualcomm fixed a zero-day exploited limited, targeted attacks
- Qualcomm has warned of 20 flaws in its products, including a potential zero-day vulnerability in the DSP service that impacts multiple chipsets.
- The vulnerability is a use-after-free bug that could lead to memory corruption.
- The zero-day vulnerability resides in the Digital Signal Processor (DSP) service and impacts dozens of chipsets.
- Google Threat Analysis Group reports limited, targeted exploitation of the zero-day vulnerability.
Read Full Article
22 Likes
Amazon
175

Image Credit: Amazon
Improve security incident response times by using AWS Service Catalog to decentralize security notifications
- Organizations can streamline the notification process for security-related findings by using AWS Service Catalog to alert workload owners and developers. This approach offers a decentralized response that speeds up incident to resolution times by subscribing them to receive near real-time security notifications through email. The Security Hub product integrations like GuardDuty and Amazon Inspector, along with notifications of non-compliance with security standards, produce better notifications and equip teams to configure AWS resources appropriately to reduce exposure time of unsecured resources. An end-user experience is included using the least-privilege which allows users to access the shared AWS service catalog product.
- The User chooses SubscribeToSecurityNotifications, and the AWS Service Catalog product view redirects them to instructions on how to use it. Users enter their email address, minimum severity level for notifications, and can filter notifications by specifying resource tags (Critical, High, Medium, or Low). They can also choose to restrict security notifications to include or exclude specific security products.
- After the user subscribes, they receive email notifications for new Security Hub findings in near real-time without delay. Each email contains a summary of the finding in the subject line, account details, finding details, recommendations (if any), list of resources & tags affected. An IAM Identity Center shortcut link to the Security Hub finding is also included within the email notifications.
- AWS Service Catalog and AWS CloudFormation are used to set up the security notifications process. With this mechanism, workload owners can subscribe to receive near real-time Security Hub notifications through email with email notifications for new Security Hub findings via Amazon Simple Notification Service, which includes a formatted Security Hub JSON event message that is human-readable. A second and more advanced deployment option involves using an AWS Lambda function to enhance messages by doing conversions from UTC to your selected time zone.
- The solution’s deployment process requires Administrator-level access to AWS Organizations, Security Hub enabled accounts, an AWS account to host the solution, authorization that uses AWS IAM Identity Center or federated IAM role names in every AWS account for users accessing the Service Catalog product. Delegated access to organizations and delegated administrators for Service Catalog are also needed.
- There are cost implications to this solution. For example, there is a cost for each Amazon SNS email notification sent out, Service Catalog API calls, and execution of Lambda functions. Consider enabling Security Hub consolidated control findings, which prevents users from receiving multiple email notifications for a control that applies to multiple standards.
Read Full Article
10 Likes
Securityintelligence
278

Image Credit: Securityintelligence
Is AI saving jobs… or taking them?
- AI is helping to increase the demand for cybersecurity professionals in two broad ways. First, malicious actors use AI to get past security defenses and raise the overall risk of data breaches. Second, the deployment of AI expands the attack surface at organizations and the number of vectors available for attackers to exploit.
- Third, the proliferation of data across multiple environments to feed AI increases the complexity of securing it and necessitates further specialized skills, increasing job demand.
- As generative AI is integrated into cybersecurity tools and becomes more capable as an informational chatbot, development tool and more, the need for people to do a wide range of tasks diminishes.
- AI tools will partially automate penetration testing, reducing demand for lower-level or entry-level pen testers.
- AI threat intelligence is already a huge boon to security teams. AI can process and analyze vast quantities of data much faster than people, potentially reducing the demand for threat intelligence analysts.
- Generative AI tools can augment human knowledge with quickly accessible knowledge.
- AI is reducing the need for cybersecurity professionals to perform a large number of tasks that can be automated. AI is also greatly increasing the capabilities of staff by empowering them to do far more work in a shorter amount of time than without AI. But it’s also radically expanding the complexity of the overall project of cybersecurity.
- New job specialties are emerging, including AI cybersecurity specialists and cybersecurity data scientists.
- While AI handles threat detection, log analysis, vulnerability assessments and the like, the human skill set will continue to shift towards strategy, planning, problem-solving and decision-making.
- The skills gap remains, and opportunities in the cybersecurity field are myriad and expanding. While AI is a powerful and increasingly indispensable tool, human expertise, skill and judgment are still necessary.
Read Full Article
16 Likes
Socprime
13

Image Credit: Socprime
Shrouded#Sleep Campaign Detection: North Korean Hackers Linked to the APT37 Group Use New VeilShell Malware Targeting Southeast Asia
- North Korean hackers linked to the APT37 group have been using the VeilShell malware in their attacks targeting Southeast Asia.
- The APT37 group, also known as InkySquid, Reaper, RedEyes, Ricochet Chollima, or Ruby Sleet, has connections with North Korea’s Ministry of State Security.
- The SHROUDED#SLEEP campaign by APT37 involves phishing attacks using ZIP files containing malicious LNK files as initial payloads.
- The VeilShell malware allows attackers to gain full control over compromised systems through its extensive RAT features.
Read Full Article
Like
Socprime
377

Image Credit: Socprime
SOC Prime Threat Bounty Digest — September 2024 Results
- The Threat Bounty Program experienced significant growth in September, with more submissions of detection rules for verification and successful releases of the rules to the SOC Prime Platform.
- Only rules that pass the verification process can be published, and the challenge of meeting the requirements enhances the professional advancement of Program members.
- The top September rules by Threat Bounty authors include detection of RAT execution, Hadooken malware execution, suspicious Microsoft IIS configuration, detection of signed binary proxy execution, and suspicious SChannel weak certificate mapping methods.
- The top five Threat Bounty authors for September are Sittikorn Sangrattanapitak, Nattatorn Chuensangarun, Davut Selcuk, Emir Erdogan, and Osman Demir.
Read Full Article
22 Likes
Kaspersky
309

Image Credit: Kaspersky
Trust and trustworthiness in the internet of things | Kaspersky official blog
- Kaspersky has been actively involved in the development of trust principles for IoT devices as laid out by the ISO/IEC TS 30149:2024 specification.
- The ISO/IEC 30141 standard defines reference architecture for IoT solutions, reducing user dependence on the manufacturer and enabling different products to interoperate.
- Standards can describe not only the features of a finished product but also how to manufacture it, addressing both hardware and software aspects.
- Standardization based on this specification addresses how to eliminate vendor lock-in and cut the number of IoT devices with security issues.
- ISO/IEC TS 30149:2024 details how trustworthiness, trust, and risk correlate and outlines principles for IoT trustworthiness.
- Trustworthiness is ensured through specific approaches to system design and construction, covering safety, security, privacy, resilience, and reliability.
- In a few years, significant improvements in the security of both industrial and consumer IoT devices are expected, including secure default settings, publicly-verified communication protocols, and secure-by-design approaches.
- The ultimate goal is for consumers to know for sure that the IoT devices they purchase are secure, reliable, and resilient to threats throughout the entire lifecycle of those IoT devices.
Read Full Article
18 Likes
Securityaffairs
85

Image Credit: Securityaffairs
MoneyGram discloses data breach following September cyberattack
- MoneyGram disclosed a data breach following a cyberattack in September, during which threat actors stole customer data.
- The cyberattack impacted both in-person and online money transfer services, leading to a network outage.
- Customer data exposed in the breach includes contact info, government IDs, Social Security numbers, and transaction details.
- MoneyGram is working with cybersecurity experts to contain and remediate the attack, while the investigation is still in its early stages.
Read Full Article
5 Likes
Securityaffairs
413

Image Credit: Securityaffairs
American Water shut down some of its systems following a cyberattack
- American Water, the largest U.S. water and wastewater utility company, shut down some systems following a cyberattack.
- The company discovered unauthorized access to its computer networks and disconnected certain systems as part of the incident response procedure.
- Water and wastewater facilities and operations remain unaffected by the incident.
- American Water estimates minimal financial impact from the security incident.
Read Full Article
24 Likes
TechBullion
363

Image Credit: TechBullion
Scott Dylan on How AI Chatbots Are Creating Data Security Challenges for Businesses
- The increasing use of AI chatbots in the workplace has brought undeniable advantages in terms of productivity and customer service.
- However, AI chatbots are not inherently secure and may expose sensitive business information and lead to severe security breaches.
- For instance, a marketing team may use an AI chatbot to manage customer queries and inadvertently expose customer contact details or purchase histories.
- Companies must develop a proactive approach to data security that involves AI chatbot management with clear, company-wide policies and employee training.
- Businesses should implement Role-Based Access Control (RBAC) for chatbot interactions to limit access to appropriate departments.
- Encryption of all data shared with AI chatbots and temporary storage solutions that automatically delete data after its intended use can significantly reduce breach risk.
- Regular audits of chatbot interactions are crucial to detecting anomalies and misuse early on as part of a broader data security strategy that includes real-time monitoring.
- The rise of shadow AI, or unauthorised use of AI systems within an organisation, poses significant vulnerabilities which can result in data breaches or compliance violations.
- To mitigate these risks, companies must encourage transparency and offer IT-approved AI alternatives to employees to ensure productivity and security.
- The challenge for businesses is to harness the power of AI while maintaining rigorous data protection standards.
- Companies like NexaTech Ventures are already developing AI solutions that integrate enhanced security protocols without compromising efficiency.
Read Full Article
21 Likes
Securityaffairs
843

Image Credit: Securityaffairs
Universal Music data breach impacted 680 individuals
- Universal Music Group is notifying 680 individuals about a data breach that compromised their personal information, including their Social Security number.
- The data breach occurred on July 15, 2024 and was discovered on August 30, 2024.
- Universal Music Group is offering impacted individuals 24 months of free credit monitoring and identity theft protection services.
- No ransomware group has claimed responsibility for the attack at this time.
Read Full Article
19 Likes
TechBullion
408

Image Credit: TechBullion
Why Many AI Projects Are Just for Show: Scott Dylan on the Pitfalls of Vanity AI Initiatives
- Many AI projects are nothing more than showpieces, lacking any meaningful contribution to business growth or strategic objectives.
- Vanity AI projects are driven by a desire to impress, often at the expense of functionality.
- Unfortunately, these projects tend to be hollow, offering little more than surface-level advancements that do not align with a company’s strategic goals.
- The resources dedicated to AI vanity projects could be better used in initiatives that genuinely enhance operational efficiency or improve customer experiences.
- When AI professionals are asked to work on projects that lack substance, they often become disillusioned.
- AI initiatives are not cheap. They require significant investment in infrastructure, talent, and time.
- Another consequence of AI-for-show is the missed opportunity to use the technology where it can truly add value.
- What differentiates successful AI initiatives from vanity projects is their alignment with business goals.
- It is also important for CIOs and CAIOs to push back when necessary.
- The companies that succeed with AI are those that adopt it with intent, focusing on real-world applications that address specific pain points and deliver measurable results.
Read Full Article
24 Likes
Qualys
44
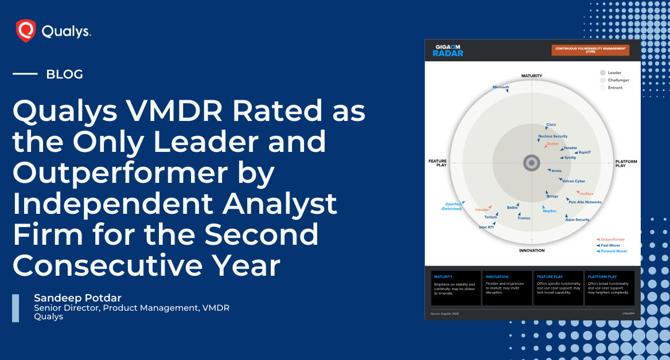
Image Credit: Qualys
Qualys VMDR Rated as the Only Leader and Outperformer by Independent Analyst Firm for the Second Consecutive Year
- Qualys VMDR has been rated as the only Leader and Outperformer by an independent analyst firm for the second consecutive year.
- Qualys VMDR received the highest scores for risk-based assessment, cloud-native and serverless function scanning, and flexibility of deployment.
- The GigaOm Radar Report for Continuous Vulnerability Management recognized Qualys VMDR as an 'Outperformer' for the second consecutive year and a 'Leader' for the fourth consecutive year.
- Qualys VMDR's comprehensive risk-based approach and integrated suite of tools provide a holistic view of an organization's vulnerability and cyber risk landscape.
Read Full Article
2 Likes
Pymnts
98

Image Credit: Pymnts
AI Chatbots Could Be A Trojan Horse in the Office
- AI chatbots in the workplace are posing security risks as employees unknowingly share sensitive work information with these tools without employer permission.
- Younger workers, especially Generation Z and millennials, are more likely to engage in this behavior.
- The lack of awareness about data exposure risks and inadequate guidance from employers contribute to the problem.
- Experts recommend encrypting data, limiting chatbot access, addressing the unauthorized use of AI tools by employees, and closely monitoring AI activity to mitigate risks.
Read Full Article
5 Likes
Infoblox
269

Image Credit: Infoblox
Master Your Cloud Ecosystem with Infoblox Universal DDI Management
- Managing a multi-cloud environment can be challenging, with organizations adopting these strategies to modernize their infrastructure.
- Delivering critical network services, like DNS, DHCP, and IP address management across the hybrid and multi-cloud environment can be difficult.
- Infoblox Universal DDI Management is the first comprehensive, fully SaaS solution for managing critical network services across hybrid and multi-cloud networks.
- Infoblox separates the management and service planes of DDI, offering greater flexibility and choice.
- Infoblox Universal DDI Management integrates with APIs of DNS products, simplifying network management.
- The Infoblox Portal is your single management interface for all DDI operations, even when other DDI products provide the service.
- Infoblox Universal Asset Insights provides automated discovery and analysis of hybrid and multi-cloud networks.
- NIOS-X as a Service allows you to serve DNS and DHCP without deploying infrastructure, offering speed and agility.
- Universal DDI 3-Part Webinar Series is now available for IT professionals and decision-makers to discover how to tackle complexities of network management.
- Exchange 2024 will unveil groundbreaking solutions empowering across cloud and on-premises infrastructure.
Read Full Article
16 Likes
For uninterrupted reading, download the app