Info. Security News News
Kaspersky
203

Image Credit: Kaspersky
How to protect schools from cyberthreats | Kaspersky official blog
- The number of cyberattacks targeting educational institutions is on the rise, with schools becoming attractive targets for cybercriminals.
- Factors contributing to schools' vulnerability include dependence on technology, valuable data, scarce resources, and low user awareness.
- Successful cyberattacks on schools can disrupt education, impact academic performance, and cause inconvenience for students and parents.
- To protect schools from cyberthreats, robust security measures, such as using dedicated cybersecurity software and conducting staff training, are recommended.
Read Full Article
12 Likes
Securityaffairs
117
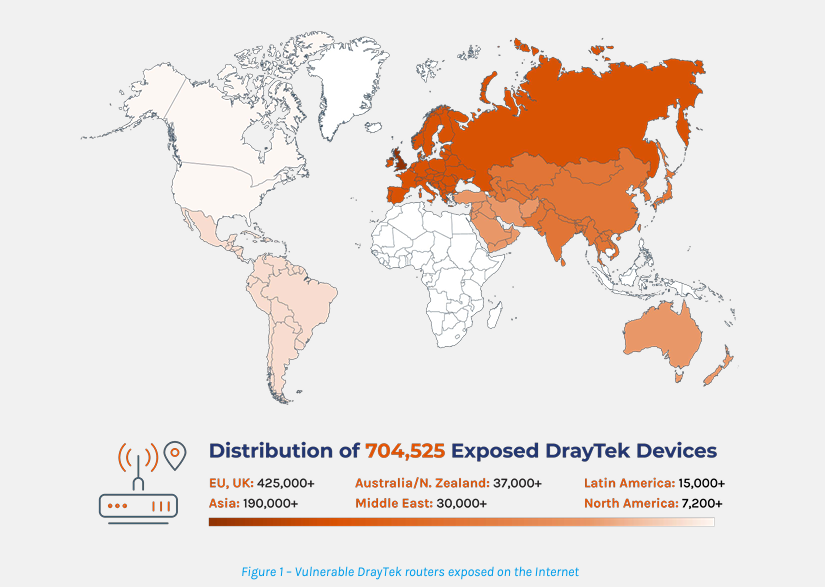
Image Credit: Securityaffairs
14 New DrayTek routers’ flaws impacts over 700,000 devices in 168 countries
- Multiple flaws in DrayTek routers can be exploited to compromise vulnerable devices.
- Forescout researchers discovered 14 new vulnerabilities, with two rated as critical.
- Over 704,000 DrayTek routers in 168 countries are exposed online, posing a serious risk.
- The vulnerabilities could lead to cyber espionage, data theft, ransomware, and DoS attacks.
Read Full Article
7 Likes
Qualys
411

Image Credit: Qualys
Threat Brief: Understanding Akira Ransomware
- Akira is a ransomware operated as Ransomware as a Service (RaaS) that has been targeting organizations in North America, the UK, and Australia since March 2023. It exfiltrates data before encrypting it, enabling double extortion attacks. The group claims to have infected over 196 organizations.
- Akira affiliates use various methods to gain initial access to victims' environments, including by exploiting vulnerabilities or using compromised credentials from initial access brokers. They then perform reconnaissance, use different tools and persistence techniques to maintain their access, and perform lateral movement with valid accounts or remote shares.
- The ransomware uses several command-line arguments, deletes shadow copies, and employs the ChaCha algorithm for file encryption. Encryption notes have a code for victims to log in to Akira's chat messenger. Qualys's EDR and EPP offering provides comprehensive coverage against advanced threats like Akira and has behavioral detections to identify such threats.
- RaaS has emerged as a significant threat, enabling low-skilled actors to deploy highly sophisticated ransomware attacks. Organizations must secure their perimeter by using defenses like multi-factor authentication and relying on EDR products to protect against such threats on the endpoint.
- The article also provides a list of MITRE ATT&CK techniques used by Akira and Indicators of Compromise (IoCs).
Read Full Article
24 Likes
Infoblox
230

Image Credit: Infoblox
DNS Early Detection – RansomHub – Breaking the Kill Chain
- On August 29, 2024, RansomHub Ransomware advisory was issued by FBI, CISA, MS-ISAC, and HHS.
- RansomHub emerged in February 2024 and targeted various critical infrastructure sectors.
- It is a ransomware-as-a-service variant with high-profile affiliates from other ransomware variants.
- Double-extortion model is used by RansomHub affiliates, encrypting systems and exfiltrating data.
- Infoblox Threat Intel identified the RansomHub IOCs and protected the customers running blocking mode using high-risk feeds.
- DNS Indicators of Compromise (IOCs) can reveal a wide range of malicious activities and provide early indicators of compromise.
- Infoblox Threat Intel uses proprietary techniques to identify potentially malicious domains much earlier.
- Infoblox threat data minimizes false positives, so you can be confident in what you are blocking.
- To learn more about Infoblox Threat Defense visit www.infoblox.com.
- To learn more about protective DNS guidance visit the provided link.
Read Full Article
13 Likes
Hackingblogs
370
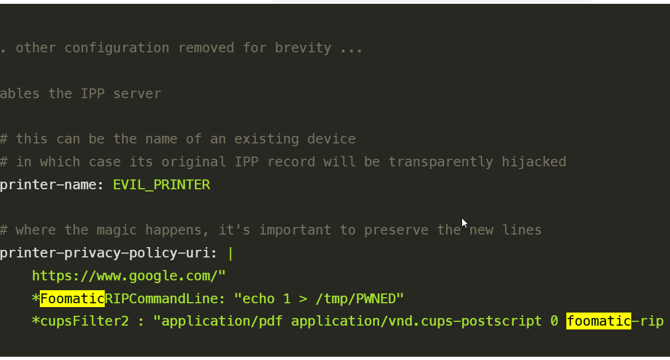
Image Credit: Hackingblogs
Critical printing issues Cups put hundreds of thousands of Linux systems at risk: How to Mitigate
- Linux systems are at risk due to multiple unpatched vulnerabilities in the CUPS printing system.
- Attackers can execute remote code on vulnerable Linux computers using the CUPS system.
- The cups-browsed daemon, part of CUPS, automatically adds discovered printers to the system.
- Mitigation steps include stopping and disabling the cups-browsed service on Linux systems.
Read Full Article
22 Likes
Amazon
36

Image Credit: Amazon
Enhancing data privacy with layered authorization for Amazon Bedrock Agents
- Generative AI models adds new considerations in the threat model of an application.
- In this blog post, we discuss the current challenges faced when using generative AI services and how to overcome them using native solutions within Amazon Bedrock and layered authorization.
- Amazon Bedrock Agents can enrich data and make decisions based on input.
- Layered authorization is the practice of using multiple authorization checks across application components beyond the point of ingress.
- Amazon Verified Permissions is a fully managed authorization service that allows building more secure applications.
- Without proper security controls, a threat actor from one tenant could manipulate data belonging to another tenant.
- Using strong authentication and multi-factor authentication can govern access to invoke the agents at the API gateway.
- An additional layer can be added to the Lambda function triggered by invoking the agent.
- Verified Permissions must have pre-built policies to dictate how authorization should occur when data is being accessed.
- In this post, you will learn how AWS native services can enforce layered authorization and improve data protection for applications using Amazon Bedrock agents.
Read Full Article
2 Likes
Securityaffairs
230
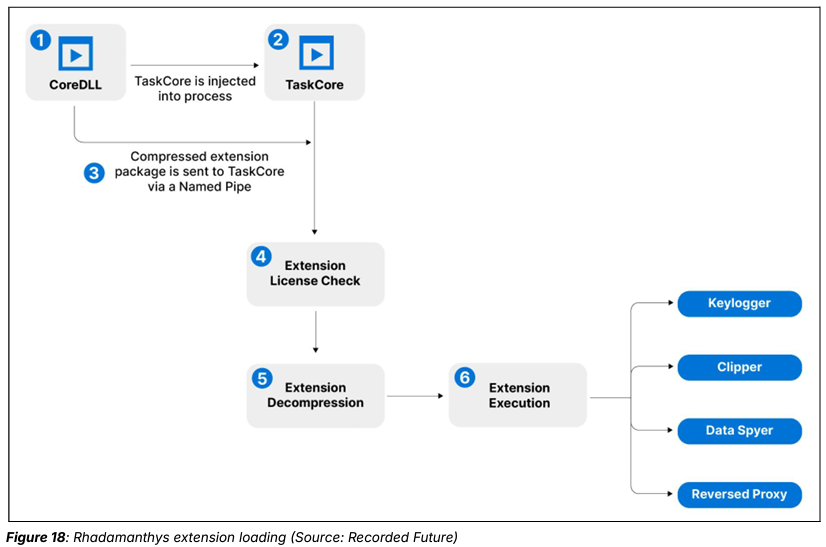
Image Credit: Securityaffairs
Rhadamanthys information stealer introduces AI-driven capabilities
- The Rhadamanthys information stealer has been upgraded with advanced features, including the use of artificial intelligence (AI) for optical character recognition (OCR).
- The latest version 0.7.0 introduces AI-driven capabilities for extracting cryptocurrency seed phrases from images.
- The malware can steal credentials, system information, and financial data and is being sold on underground forums.
- Rhadamanthys uses a three-stage attack chain and has implemented additional plugins in its latest version 0.7.0.
Read Full Article
13 Likes
Sentinelone
253

Image Credit: Sentinelone
Adaptive Threat Hunting | Adopting a Multi-Directional Approach
- Adaptive threat hunting benefits from a multi-directional approach, which integrates memory, logs, and file system analysis to identify and respond to a broader spectrum of threats.
- Automating the collection of memory dumps, process information, system files, and event logs helps organizations adopt a proactive approach to adaptive threat hunting.
- Telemetry-only hunting may not provide a complete picture of advanced or stealthy attacks as it lacks visibility into system memory, event logs, registries, and file system activities.
- Sampling is a technique that enables a broader reach, adding speed and scale to hunts. This consists of automated examination of a selected group of systems to gain deeper insights into potential threats that exist in the environment.
- Combining the insights from endpoint telemetry data analysis with triage scans and event logs provides a more comprehensive view of the threat landscape and helps identify both known and unknown threats.
- Threat hunting is supported by both automated processes and manual investigation. Automation helps quickly sift through large datasets and prioritize alerts, while manual investigation allows analysts to triage events or clusters of events of interest, and then delve deeper into complex threats and apply human expertise.
- Security platforms offer advanced capabilities today to help organizations adopt a holistic, multi-directional approach to adaptive threat hunting.
- By automating the collection and correlation of data sources, organizations can identify the compromise, limit the impact, and prevent further exploitation.
- Implementing such an advanced strategy may be challenging for internal security teams and partnering with trained service providers or using appropriate tools may be helpful.
- For organizations willing to enhance their threat detection capabilities, SentinelOne's WatchTower Intelligence-Driven Threat Hunting service and Singularity MDR service offer comprehensive detection and analysis capabilities that surface both known and unknown threats.
Read Full Article
15 Likes
Securityintelligence
298

Image Credit: Securityintelligence
Cybersecurity Awareness Month: Cybersecurity awareness for developers
- Developers often prioritize speed and functionality, while cybersecurity teams prioritize safety and risk mitigation.
- There is a knowledge gap between developers and cybersecurity teams, leading to miscommunications and misunderstandings.
- Developers often consider security as an afterthought, leading to vulnerabilities being managed reactively.
- Developers should shift left on security by integrating security earlier in the development process through secure coding practices and regular code reviews.
Read Full Article
17 Likes
Securityaffairs
85

Image Credit: Securityaffairs
Critical Zimbra Postjournal flaw CVE-2024-45519 actively exploited in the wild. Patch it now!
- Threat actors attempt to exploit recently disclosed vulnerability CVE-2024-45519 in Synacor’s Zimbra Collaboration.
- Threat actors have been attempting to exploit the CVE-2024-45519 vulnerability to achieve remote code execution on vulnerable Zimbra instances.
- The vulnerability, discovered by security researcher Alan Li, is a remote code execution vulnerability in Zimbra mail servers.
- Users are advised to apply the latest versions of Zimbra Collaboration to protect against this vulnerability.
Read Full Article
5 Likes
Hackersking
72

Image Credit: Hackersking
How Deepfakes Are Fueling Social Media Scams: The Growing Threat of AI in Fraud
- Deepfake videos are being used by cybercriminals to execute highly convincing social engineering attacks on Instagram.
- Social engineering is a manipulation technique used by cybercriminals that tries to deceive individuals into divulging confidential information or performing actions that compromise security.
- Deepfake phishing is an advanced form of phishing that utilizes AI technology to create highly realistic digital replicas of individuals.
- These AI-generated videos closely mimic the voice, appearance, and mannerisms of real people, making them very difficult to distinguish from the original at first glance.
- Deepfake phishing is particularly dangerous because it exploits human trust, allowing attackers to impersonate anyone convincingly, and trick victims into interacting with someone they know or trust.
- As technology advances, deepfake AI is becoming increasingly dangerous, and it is expected to increase the number of attacks in the future.
- Social engineering is rising exponentially, and deepfakes are hitting social media influencers, too.
- Fake celebrity ads, romance scams, fake job offers, blackmail with fake videos, identity theft of Instagram influencers, and fake political videos are some examples of deepfake-related scams.
- To protect oneself from becoming a victim of such scams, one should know that whenever somebody asks for money, they should not give it until they cross-check the matter.
- Recognizing familiar faces, influencer impact, and emotional tricks are some common methods used to trick victims using deepfake videos.
Read Full Article
4 Likes
Hackersking
140
.jpg)
Image Credit: Hackersking
WhatsApp Web Vulnerabilities – Security Concerns About Using WhatsApp on Desktop
- WhatsApp Web is an extension of the mobile app, allowing users to chat, send files, and make voice calls through their browsers.
- WhatsApp Web has a range of security vulnerabilities that users need to be aware of such as session hijacking, QR code exploitation, man-in-the-middle attacks, cross-site scripting attacks, and malicious files and malware.
- Session hijacking is a major concern with WhatsApp Web, as attackers can gain access by injecting malware into the desktop or stealing your session cookie over a compromised network.
- Logging into WhatsApp Web requires scanning a QR code from your phone, which attackers can exploit by sending you phishing messages with fake QR codes.
- Using WhatsApp Web on unsecured networks like public Wi-Fi opens up the possibility of a man-in-the-middle (MITM) attack.
- Hackers can deliver malicious files through WhatsApp Web, containing malware or scripts designed to take over your system, steal sensitive data or perform remote code execution.
- Stay protected from vulnerabilities by using practical tips, such as keeping software updated, using secure networks, logging out after use, enabling two-step verification, and checking for unauthorized sessions.
- By staying informed about these vulnerabilities and following basic security practices, you can safely use WhatsApp Web.
- For cybersecurity professionals, these vulnerabilities should serve as a reminder of the need for vigilance in web security.
- Always be cautious of unfamiliar links or attachments, and use secure networks to prevent unauthorized access.
Read Full Article
8 Likes
Amazon
339

Image Credit: Amazon
How to perform a proof of concept for automated discovery using Amazon Macie
- Amazon Macie helps customers identify, discover, monitor, and protect sensitive data stored in Amazon S3.
- Customers need to evaluate and test the capabilities of Macie before using it to meet their data identification and protection goals.
- Macie comes with over 150 managed data identifiers and offers important features such as identifying S3 bucket securities, sensitive data discovery jobs, and automated data discovery.
- Users can define custom data identifiers, stage POC data, run a sensitive data discovery job, review the findings, and enable automated discovery.
- Users can view the individual findings that were generated for each S3 object that was identified as having sensitive data and store and retain sensitive data discovery results to analyze and query later.
- After the POC, evaluate the results to determine how much using Macie can strengthen your organization’s data protection program.
- Planning your POC using the guidance in this post can help you determine more quickly if Macie is a fit for your company.
- AWS customers of various sizes can use Macie to enhance their current data protection strategies and classify and protect the data they store in Amazon S3.
- A successful POC of Macie includes understanding what data Macie can detect and defining custom data identifiers.
- Operationalizing Macie output and refining the managed data identifiers that are required for detecting sensitive data are some of the next steps that other customers have taken after completing their POC with Macie.
Read Full Article
20 Likes
Securityaffairs
9

Image Credit: Securityaffairs
UMC Health System diverted patients following a ransomware attack
- UMC Health System had to divert patients after a ransomware attack caused a network outage.
- Investigation ongoing into the IT outage and ransomware attack.
- UMC Health System, based in Lubbock, Texas, provides a wide range of medical services and is affiliated with Texas Tech University Health Sciences Center.
- Some systems and services have been restored, but patients continue to be diverted and details about the attack are undisclosed.
Read Full Article
Like
Infoblox
27

Image Credit: Infoblox
Compressing the IPv6 Deployment Timeline
- Organizations should start their IPv6 journey now, even if they don't need IPv6 fully deployed for many years.
- An IPv6 address allocation plan and IPv6 training can help organizations kick-start their IPv6 implementation.
- Businesses don't have to assume the burden of transitioning their entire IT environment to IPv6 at once.
- IPv6 adoption has been slow but steady over the past twenty years, but IPv6 usage is already at about 50% in some regions of the world and could be closer to 85% in others by 2028.
- Deliberately delaying the IPv6 journey compresses the deployment timeline and increases the risk of not being able to deploy IPv6 at a leisurely pace in the future.
- Some enterprises refuse to embrace IPv6 and fail to plan for the inevitable, which could have serious legal and financial penalties and negatively affect shareholder value.
- IT teams need to address IPv6 implementation as one project amongst many and weave it into any new deployment or perform it in parallel with other projects.
- IPv4 re-addressing projects, overlapping address space, and increased use of NAT will continue to add to operational costs.
- Enterprises should start planning for IPv6 to give themselves more runway and ensure a successful IPv6 implementation.
- Organizations are encouraged to plan a concerted effort to get the IPv6 initiative well underway in early 2025.
Read Full Article
1 Like
For uninterrupted reading, download the app