Info. Security News News
Hackersking
325
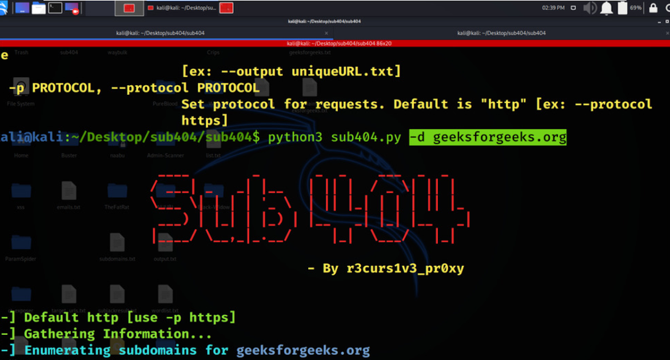
Image Credit: Hackersking
Subzy: Live Subdomain takeover vulnerability checker
- Subzy is an open-source tool designed to detect live sub-domain takeover vulnerabilities and safeguard against potential attacks on web applications.
- Sub-domain takeover vulnerability occurs when a sub-domain of a website is left unclaimed and attackers can redirect unclaimed sub-domains to their harmful sites.
- Subzy scans the domain and sub-domains, analyzes their DNS records, and assesses whether the services are unclaimed or misconfigured, which could leave them vulnerable to takeover.
- For installation, Subzy can easily be set up using the package manager for JavaScript.
- Subzy provides a comprehensive set of commands for scanning sub-domains and identifying potential vulnerabilities.
- Subzy is built with GoLang, which makes it ideal for scanning multiple sub-domains simultaneously.
- Subzy features a user-friendly CLI interface, enabling easy command and flag usage.
- Ethical hackers and cybersecurity professionals should integrate Subzy into their routine security checks to safeguard their web presence.
- Regularly checking your sub-domains with Subzy can thwart potential attacks and enhance your web application's security posture.
- Subzy is a valuable addition to any penetration testing toolkit.
Read Full Article
19 Likes
Tech Story
13

UK Government Apologizes for Leaking Bernard Arnault’s Email in Data Breach
- The UK government has issued an apology for leaking the email address of LVMH CEO, Bernard Arnault, in a data breach.
- The incident occurred during the preparation for an international investment event hosted by Britain, where other executives' email addresses were also accidentally revealed.
- The government admitted to an administrative error and promptly apologized to Arnault and the other affected parties.
- The incident highlights concerns about data security and may temporarily damage the UK government's relationship with foreign business partners.
Read Full Article
Like
Securityaffairs
214

Image Credit: Securityaffairs
Security Affairs newsletter Round 493 by Pierluigi Paganini – INTERNATIONAL EDITION
- A cyber attack hit Iranian government sites and nuclear facilities
- Ransomware operators exploited Veeam Backup & Replication flaw CVE-2024-40711 in recent attacks
- GitLab fixed a critical flaw that could allow arbitrary CI/CD pipeline execution
- Iran and China-linked actors used ChatGPT for preparing attacks
Read Full Article
12 Likes
Dev
84

Image Credit: Dev
API Security: Threats, Tools, and Best Practices
- API security refers to the practices and protocols that are used to protect APIs from misuse or malicious activity.
- APIs are vital in facilitating data exchange and functionality sharing between different systems and services.
- API security involves implementing measures to ensure that APIs are only accessible by authorized systems and cannot be abused by cybercriminals.
- API security includes encryption, authentication, monitoring, and threat detection to protect data and address vulnerabilities.
Read Full Article
5 Likes
Securityaffairs
17

Image Credit: Securityaffairs
Russia-linked group APT29 is targeting Zimbra and JetBrains TeamCity servers on a large scale
- Russia-linked cyber espionage group APT29 is targeting vulnerable Zimbra and JetBrains TeamCity servers on a large scale.
- The group has been exploiting vulnerabilities in Zimbra's CVE-2022-27924 and JetBrains TeamCity's CVE-2023-42793.
- The FBI, NSA, CNMF, and NCSC-UK have issued a joint advisory warning about the tactics employed by the Russian Federation's Foreign Intelligence Service.
- Organizations are urged to address the known vulnerabilities and apply vendor-issued patches to safeguard their systems.
Read Full Article
1 Like
Inkbotdesign
428

Small Business Automation Considerations: Boost Productivity & Growth
- Automation can help small businesses increase productivity, reduce errors, and cut costs by up to 50%. Identifying the right tasks to automate can help companies work smarter and faster. The benefits of automation include faster response times and improved customer service. Small businesses can use affordable automation tools to streamline operations, such as customer service bots and AI-powered marketing. Automation can further improve inventory management, appointment scheduling, payment processing, and employee onboarding. Tools such as HubSpot CRM, Zapier, Sendinblue, and Tidio can ease the process of automation.
- Automation requires businesses to conduct an audit of existing processes, prioritize automation opportunities, research and choose tools, and start small. Thorough testing, employee training, continuous improvement, and staying updated are essential for successful implementation. Common automation challenges can be overcome through communication, prioritizing tools with good integration capabilities, not over-automating, ensuring data security and complying with regulatory requirements.
- The future of automation includes AI and machine learning, voice-activated automation, the internet of things, blockchain for automated contracts, and augmented reality in customer service. Small businesses looking to remain competitive require staying informed and adaptable.
Read Full Article
25 Likes
Securityaffairs
84

Image Credit: Securityaffairs
A cyber attack hit Iranian government sites and nuclear facilities
- Iran faced major cyberattacks, disrupting government branches and targeting nuclear facilities.
- Sensitive information was stolen from targeted infrastructure.
- Iran's Civil Aviation Organization banned pagers and walkie-talkies on flights following sabotage attacks in Lebanon.
- The sabotage attacks in Lebanon killed 39 members of Hezbollah.
Read Full Article
5 Likes
Hackersking
267

Image Credit: Hackersking
Exploring OSINT Tools: How Ethical Hackers Gather Intelligence
- Ethical hackers rely on Open Source Intelligence (OSINT) tools for gathering publicly available information about potential targets for cybersecurity purposes.
- OSINT process involves gathering information from the internet, social media, databases, and other open channels to identify vulnerabilities.
- Maltego is a powerful OSINT tool that uses data visualization and relationship mapping to show the relationships between various entities like organizations, individuals, and phone numbers.
- Another OSINT tool, Shodan, is a specialized search engine used by ethical hackers to find devices connected to the internet, identifying weaknesses such as open ports, misconfigured devices, or unpatched software.
- Recon-ng is an OSINT framework used for conducting reconnaissance, offering built-in modules for domain, email and IP address reconnaissance, making it popular among penetration testers.
- theHarvester is another simple but effective OSINT tool used for collecting email, subdomains, and usernames from publicly available sources, making it ideal for gathering email addresses from public sources.
- SpiderFoot is a comprehensive OSINT automation tool used for reconnaissance of IP addresses, domain names and emails, gathering data from hundreds of sources.
- Utilizing OSINT tools has become essential for ethical hacking, cybersecurity professionals can conduct reconnaissance effectively and legally without direct interaction with their targets, thus reducing the risk of detection.
- OSINT tools have made it easier for cybersecurity professionals to identify weak areas, thus making penetration testing and vulnerability assessment an essential part of securing systems.
- As cyber threats continue to evolve, using advanced OSINT tools in 2024 is essential for both offense and defense in the cybersecurity space.
Read Full Article
16 Likes
Hackingblogs
62
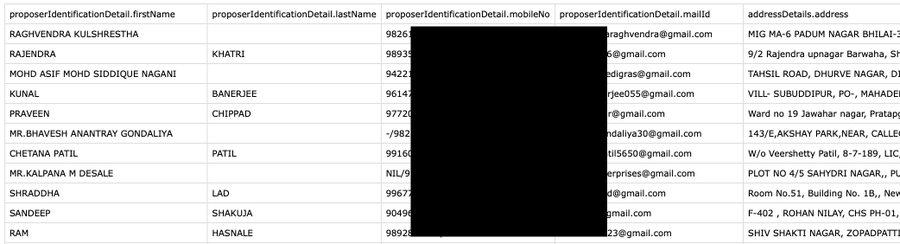
Image Credit: Hackingblogs
Star Health Insurance Breached : A Pre Planned Massive Breach of 31 Million Indian Customers
- A massive breach of Star Health Insurance data has occurred, affecting 31 million Indian customers.
- The data, including personal information, insurance details, and medical records, is being sold by a hacker.
- The breach poses risks such as financial fraud, identity theft, and targeted scams.
- CloudSek, a cybersecurity company, is accused of a cover-up in response to the breach.
Read Full Article
3 Likes
Securityaffairs
276

Image Credit: Securityaffairs
Ransomware operators exploited Veeam Backup & Replication flaw CVE-2024-40711 in recent attacks
- Ransomware operators are exploiting a critical code execution flaw in Veeam Backup & Replication.
- The flaw, CVE-2024-40711, allows for remote code execution and has a severity score of 9.8.
- Sophos X-Ops researchers observed recent attacks exploiting compromised credentials and the Veeam vulnerability to deploy ransomware.
- Sophos emphasizes the importance of patching vulnerabilities, updating/replacing unsupported VPNs, and using multifactor authentication to control remote access.
Read Full Article
16 Likes
TechBullion
35

Image Credit: TechBullion
The Future of Data Security in Fintech: Trends and Solutions
- The fintech industry has made data security a top priority with the increasing need for robust security measures.
- Data security in the fintech sector involves technologies, processes, and best practices to protect sensitive financial data.
- Virtual data rooms (VDRs) are crucial for fintech data security, employing encryption, access controls, and audit trails.
- Key trends in fintech data security include technology integration, regulatory compliance, and adopting innovative technologies.
Read Full Article
2 Likes
Veracode
89

Image Credit: Veracode
Bringing Veracode Fix to GitHub
- Many organizations struggle with finding ways to remediate flaws in their codebase while also creating new applications and updates.
- Veracode Fix, launched a year ago, has helped thousands of developers fix flaws in minutes that previously took hours.
- Developers are asking for more language and flaw-type support to accelerate flaw remediation.
- The goal is to off-load the toil from developers and provide them with tools to expedite the remediation process.
Read Full Article
5 Likes
Schneier
67

More on My AI and Democracy Book
- Author is working on a book about AI and democracy, to be published by MIT Press in fall 2025.
- The author seeks feedback on possible book titles that convey it being about AI, democracy, and optimism.
- The author provides four title options, encouraging mixing and matching.
- The book's table of contents is also shared.
Read Full Article
4 Likes
Securityaffairs
44

Image Credit: Securityaffairs
GitLab fixed a critical flaw that could allow arbitrary CI/CD pipeline execution
- GitLab issued updates for CE and EE to address multiple flaws, including a critical bug allowing CI/CD pipeline runs on unauthorized branches.
- The critical bug, tracked as CVE-2024-9164, allows running pipelines on arbitrary branches and has been mitigated in the latest release.
- GitLab also addressed four high-severity issues and two medium severity issues in the security updates.
- In mid-September, GitLab released security patches for 17 vulnerabilities in GitLab CE and EE, including a critical pipeline execution flaw.
Read Full Article
2 Likes
Dataprivacyandsecurityinsider
152

Image Credit: Dataprivacyandsecurityinsider
Three More States Sue TikTok Alleging Harm to Young Users
- Nebraska, North Carolina, California, and New Jersey filed complaints against TikTok and ByteDance, alleging harm to young users.
- TikTok is accused of manipulating youth into habitual use, mining excessive data, and promoting excessive and addictive use.
- The Chinese version of TikTok imposes usage limits for young users, while TikTok in the U.S. encourages unhealthy levels of use.
- Harmful effects on mental and physical health, including body image issues, depression, anxiety, and insufficient sleep, are highlighted in the complaints.
Read Full Article
9 Likes
For uninterrupted reading, download the app