Info. Security News News
Veracode
9

Image Credit: Veracode
Celebrating Five Years as a Customers' Choice in Application Security Testing
- Veracode has been recognized as a Customers' Choice in the 2024 Gartner Peer Insights Voice of the Customer for Application Security Testing for the fifth consecutive year.
- The recognition reflects the strong partnerships formed with customers and their feedback and engagement in shaping Veracode's solutions.
- Veracode's commitment to improving security postures and innovative solutions is driven by customers' commitment to securing applications and managing risk.
- Veracode expresses gratitude to its customers for their support and contribution in achieving this distinction.
Read Full Article
Like
Amazon
90

Image Credit: Amazon
Keep your firewall rules up-to-date with Network Firewall features
- AWS Network Firewall is a managed firewall service for VPCs on AWS.
- Network Firewall automatically scales with traffic and allows fine-grained control over network traffic.
- The article explains the mechanisms that Network Firewall uses to assist in keeping your rule sets current and effective.
- Three features – managed rule groups, prefix lists, and tag-based resource groups – are discussed in detail.
- Managed rule groups are predefined, updated rules managed by AWS to protect against evolving security threats.
- Prefix lists simplify firewall management with IP address ranges that are managed by AWS or customers.
- Tag-based resource groups simplify firewall management by applying stateful rules to resources that meet certain EC2 or ENI tag criteria.
- AWS handles much of the work associated with keeping security rules synchronized, reducing manual intervention and customer automation processes.
- Managed rule groups, prefix lists, and tag-based resource groups can enhance the efficiency and effectiveness of your Network Firewall deployments.
- If you have questions about Network Firewall, contact AWS Support.
Read Full Article
5 Likes
Securityaffairs
40

Image Credit: Securityaffairs
U.S. CISA adds D-Link DIR-820 Router, DrayTek Multiple Vigor Router, Motion Spell GPAC, SAP Commerce Cloud bugs to its Known Exploited Vulnerabilities catalog
- U.S. Cybersecurity and Infrastructure Security Agency (CISA) adds D-Link DIR-820 Router, DrayTek Multiple Vigor Router, Motion Spell GPAC, SAP Commerce Cloud bugs to its Known Exploited Vulnerabilities catalog.
- CISA added SonicWall SonicOS, ImageMagick, and Linux Kernel vulnerabilities to its KEV catalog.
- CISA identifies CVE-2023-25280, CVE-2020-15415, CVE-2021-4043, and CVE-2019-0344 as the vulnerabilities in the catalog.
- CISA orders federal agencies to fix the vulnerabilities by October 21, 2024.
Read Full Article
2 Likes
Securityintelligence
9

Image Credit: Securityintelligence
Spooky action: Phantom domains create hijackable hyperlinks
- Phantom domains” make it possible for malicious actors to exploit users’ trust in familiar websites.
- Phantom domains are active links to dot-com domains that have never been registered.
- Phantom domains emerge in two common types of mistakes – errors and placeholders.
- Errors occur when web developers or administrators make mistakes, such as misspelling the intended domain destination.
- Developers may also use placeholder domains for links.
- The web currently contains links to more than 572,000 phantom domains.
- Compromised phantom domains become potential attack vectors when purchased by malicious actors.
- When it comes to action, companies need to ensure they’re actively scanning their web pages for links that don’t lead anywhere.
- The secret to eliminating weakest links is recognizing that they’re human rather than digital.
- Companies can reduce the risk of hijacked hyperlink hacks by training staff to double-check domains before they click through.
Read Full Article
Like
Socprime
95

Image Credit: Socprime
Detecting CUPS Exploits: Critical Security Vulnerabilities in Linux and Unix Systems Allow Remote Code Execution
- Researchers have discovered critical security vulnerabilities in the OpenPrinting Common Unix Printing System (CUPS) used in Linux environments.
- These vulnerabilities, if exploited, could allow attackers to execute arbitrary code remotely and gain control over affected systems.
- The vulnerabilities affect various components of CUPS and pose a serious risk to organizations relying on the impacted products.
- Mitigation measures include disabling the cups-browsed service, updating the CUPS package, and blocking traffic to UDP port 631 and DNS-SD.
Read Full Article
5 Likes
Socprime
443

Image Credit: Socprime
Uncoder for Flexible Threat Detection: From Cloud to Air-Gapped Networks
- SOC Prime offers Uncoder, a trusted tool in the cybersecurity community that helps in enabling vendor-agnostic threat detection from cloud to air-gapped networks.
- Though air-gapped networks for mission-critical data have long been a trusted solution, they still require peripheral equipment, software updates and legitimate data transfers, which expose them to supply chain attacks, insider threats and social engineering.
- Uncoder IO allows one-click translations of generic detections to various SIEM, EDR and Data Lake formats while Uncoder AI is available for integrations and API support via the SOC Prime Platform and also supports contributions to the collective cyber defense via the Threat Bounty Program.
- Uncoder On-Prem is an on-premises version of Uncoder that supports teams that defend isolated networks and is reliable for converting detection rules and IOCs into actionable SIEM-specific queries.
- The tool helps security specialists working in air-gapped networks in handling the detection tasks more effectively, gaining operational time to focus on more complex threats and strategic objectives.
- The on-prem setup of Uncoder within an isolated network allows reacting to threats promptly without the risk of exposure of defense strategies.
- The on-prem version of the tool supports organizations that use SOC Prime Platform and the tool can be used to keep using the queries automatically converted from Sigma or Roota rules or IOCs.
- SOC teams handling classified or highly sensitive data and within strict security regulations, can deploy Uncoder IO in-house to enhance operational efficiency and security.
- Implementing Uncoder IO for operations in air-gapped environments provides significant benefits for SOC teams managing threat detections.
- Its ease of use and the ability to convert generic rules like Roota and Sigma and IOCs empower teams to maintain effective and timely detection capabilities in environments with the highest security standards.
Read Full Article
26 Likes
Securityaffairs
289

Image Credit: Securityaffairs
News agency AFP hit by cyberattack, client services impacted
- AFP suffered a cyberattack affecting its IT systems and content delivery for partners, impacting some client services.
- The global news coverage of Agence France-Presse remains unaffected, but the attack disrupted certain client services.
- AFP is collaborating with France's cybersecurity agency, ANSSI, to investigate the incident.
- The cyberattack compromised FTP credentials used to receive AFP content, prompting AFP to urge partners to change passwords and secure their reception systems.
Read Full Article
17 Likes
Inkbotdesign
312

How to Dominate Digital Strategy Without a Fortune 500 Budget
- To dominate digital strategy, you don't need a huge budget, you need to be more intelligent, focused, and agile than the competition.
- Most digital strategies fail because of the “Shiny Object” Syndrome, the “Set It and Forget It” Mentality, and the “Me, Me, Me” Approach.
- The five pillars of a successful digital strategy include customer-centric everything, content marketing, data-driven decision-making, omnichannel integration, and agility and innovation.
- On social media, choose your platforms wisely, focus on quality over quantity, engage rather than broadcast, use video content, and practice social listening.
- To turn your website into a lead-generating machine, optimize for search engines, create a clear value proposition, use strong calls-to-action (CTAs), implement live chat, and create valuable gated content.
- To leverage your data, collect the right data, personalize the customer experience, use predictive analytics, and prioritize data security and privacy.
- Continuously optimize your digital strategy through A/B testing, user feedback, and staying agile.
- Allocate 7-10% of your revenue for digital marketing, with about 50% of that going to digital. Review your digital strategy quarterly and make minor adjustments on the fly.
- SEO is still important in 2024, and email marketing can still be effective when done correctly.
- The biggest mistake businesses make with digital strategy is trying to do too much too soon. Start with focus and expand as you learn what works.
Read Full Article
18 Likes
Krebsonsecurity
76

Crooked Cops, Stolen Laptops & the Ghost of UGNazi
- Adam Iza, the founder of cryptocurrency investment platform Zort, has been accused of paying police offers to intimidate, extort and silence rivals and former business partners. Iza additionally spent much of the company's investments on luxury items and cosmetic surgeries. Iza, also known as Assad Faiq, was under FBI investigation and known to have law enforcement deputies with the Los Angeles Sheriff’s Department (LASD) on his payroll. The investigation ultimately uncovered alleged collusion between Iza and the deputies, with Iza frequently hiring them to kidnap, extort and invade the privacy of his opponents.
- The FBI obtained a search warrant executed by LASD deputies in January 2022, which had illegally included the mobile number of an unrelated firearms investigation. According to the complaint, the phones of former hackers and business partners were being used to intimidate them, prompting investigators to search for links between Iza, the false charges and his LASD deputies.
- The indictment asserts that Iza’s businesses and associated illegal activities were supported by Iris Au who helped him spend the millions from Zort investors. Iza used his influence to extort and intimidate small-time hackers and investees seeking to discover, while Au was said to have seduced Davide Sanclimenti, a 2022 co-winner on Love Island.
- In addition to his cyber activities, Iza is also accused of harassing a man identified only as T.W., who is described as one of two Americans currently incarcerated in the Philippines for murder. The FBI reported that Iza had been attempting to extort passwords from Woody Jr. and potentially have access to cryptocurrencies obtained illegally.
- The indictment also includes several cases of Iza failing to pay for services, such as a private investigator or an associate hired to throw a party. In a separate incident, R.C. - the associate who was hired to throw Iza's party - was surrounded by armed LASD officers and held up until agreeing to return half the money he was paid. In addition, while under investigation, Iza texted someone about bribing officers and expressed the thought that it was a dangerous thing to do, claiming that he pays them $280k a month.
- The crimes described in this indictment represent a disturbing trend within English-speaking cyber communities - the emergence of violence-as-a-service, which allows cybercriminals to anonymously extort and intimidate rivals. Such offerings are found on Telegram channels, where people can hire other individuals to commit any number of violent acts, including slashing tires, firebombing a home or tossing a brick through someone’s window.
Read Full Article
4 Likes
Securityaffairs
398
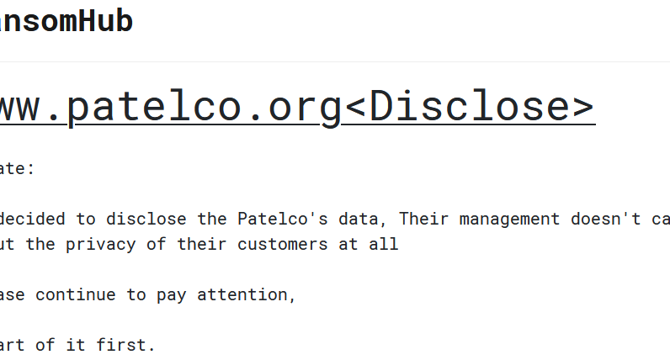
Image Credit: Securityaffairs
Patelco Credit Union data breach impacted over 1 million people
- The ransomware attack on Patelco Credit Union this summer led to a data breach affecting over 1 million individuals.
- The breach occurred in May 2024 but was only discovered and confirmed in August 2024.
- The accessed databases contained personal information such as names, Social Security numbers, driver's license numbers, dates of birth, and email addresses.
- The ransomware group, known as RansomHub, attempted negotiations with Patelco but no agreement was reached.
Read Full Article
23 Likes
Amazon
357

Image Credit: Amazon
How to implement relationship-based access control with Amazon Verified Permissions and Amazon Neptune
- In this blog post, we show you how to implement ReBAC using Verified Permissions and Amazon Neptune, a managed, serverless graph database on AWS.
- Externalized authorization for custom applications is a security approach where access control decisions are managed outside of the application logic.
- Two common access control models that you might consider when implementing your authorization system are role-based access control (RBAC) and attribute-based access control (ABAC).
- Relationship-based access control (ReBAC) offers a more nuanced approach by using the relationships between users and resources to make decisions about permitted actions, thus addressing scenarios more efficiently than other models.
- The core principle of ReBAC is that authorization decisions are based on the relationships between the principal requesting access and the resource being accessed.
- Common relationship models in ReBAC include resource ownership, resource hierarchies, and user hierarchies.
- Relationship data is stored in Neptune. Prior to requesting an authorization decision from Verified Permissions, the application runs a Neptune query that traverses the relationship graph to retrieve the set of principals that have a specific relationship with the resource.
- Verified Permissions uses the Cedar policy language to define fine-grained permissions. ReBAC policies are a great fit when you want to create access based on a relationship between the principal and the resource.
- ReBAC policies can also be combined with ABAC policies to enable more intuitive expressions of business rules.
- To learn more about this solution and the source code, visit the GitHub repository. For more information, see Cedar Policies, Amazon Verified Permissions, and Amazon Neptune.
Read Full Article
21 Likes
Hackingblogs
63
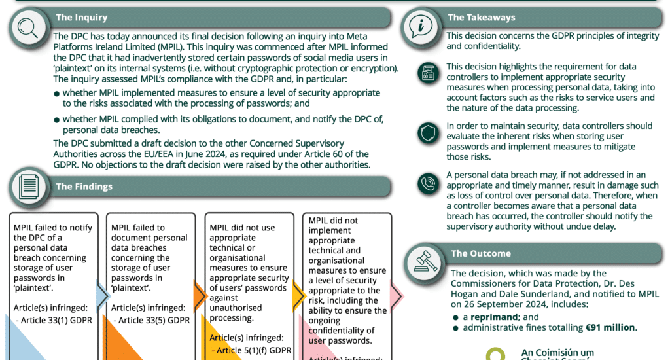
Image Credit: Hackingblogs
Violation Of GDPR Rules : Meta was Fined $100M For Storing Password In Plaintext
- Meta, the parent company of Facebook, has been fined $100 million for storing passwords in plaintext, violating GDPR rules.
- The Data Protection Commission (DPC) in Ireland found that Meta failed to implement proper security measures to protect user data.
- Meta also neglected to manage security risks associated with the data it processed and stored in its database servers.
- The company failed to report the disclosure of users' plaintext passwords in a timely manner, violating GDPR regulations.
Read Full Article
3 Likes
Cybersecurity-Insiders
294

Image Credit: Cybersecurity-Insiders
The Most Misunderstood Data Security Terms in the United States
- Malware: Malware includes various types of malicious software, not just viruses.
Read Full Article
17 Likes
Sentinelone
421

Image Credit: Sentinelone
PinnacleOne ExecBrief | Financially-Motivated Threats
- The 2023 Ransomware Task Force (RTF) reported a 73% increase in ransomware attacks from 2022 to 2023, with high-value organizations being targeted.
- Ransomware groups like CL0P and LockBit remained dominant in 2023, with the Ransomware-as-a-Service (RaaS) model proving lucrative.
- Ransomware attacks remain frequent in 2024, although the frequency has declined from the 2023 summer peak.
- The recommendation to businesses is to form a pricing cartel, underwritten by insurers, to reduce ransom prices and increase negotiation control.
Read Full Article
25 Likes
TechCrunch
235
Image Credit: TechCrunch
Everything you need to know about VPNs
- VPNs were originally designed to connect people working from home to the office network or as a way to connect several offices to the same network.
- A VPN connection starts a point-to-point connection and all your network traffic goes through this private tunnel.
- VPNs are useful when you want to work from home and still access the file servers and internal tools that you regularly use in the office.
- VPNs can also be used when you want to access a video streaming service that isn’t available in your country.
- Using VPNs can be dangerous as some free VPN apps sell your browsing habits to advertisers or inject their own ads on non-secure pages.
- Many paid VPNs log your internet traffic, share information with law enforcement, and more.
- WireGuard is considered the gold standard of VPN protocol as it is based on public and private keys.
- VPNs come in different types including VPN for working remotely, VPN for developers, and VPN services and mobile VPN apps.
- The bottom line is that VPNs can be great and can fill different needs, but it's important to choose a reputable provider.
- If you're concerned about your privacy, there are better privacy tools available that you can use to better protect your privacy online.
Read Full Article
14 Likes
For uninterrupted reading, download the app