Programming News
Medium
415

Image Credit: Medium
Variational Mode Decomposition in Python (2025 Guide)
- Variational Mode Decomposition (VMD) in Python offers a powerful signal processing tool to extract hidden signals from noisy data with surgical precision, surpassing traditional methods like Fourier transforms, wavelets, and Empirical Mode Decomposition (EMD).
- VMD minimizes total bandwidth of each mode while ensuring they reconstruct the original signal when combined, employing an augmented Lagrangian approach with ADMM.
- Dividing the process into spectral separation, Wiener filter application, frequency tuning, and reconciliation, VMD acts like a magical mixing studio to extract and refine distinct components in a signal.
- VMD outperforms EMD in scenarios with closely spaced frequencies or components with different energies, showcasing superior clarity in isolating cardiac features, industrial fault signatures, and financial data trends.
- The implementation of VMD in Python 3.8+ simplifies signal decomposition tasks, allowing for efficient extraction of specific components from complex data sets.
- VMD's global optimization approach provides stable features for prediction models, depicted by improved directional forecast accuracy in financial data analysis.
- While EMD works well for signals with separated components, VMD excels in scenarios with overlapping frequencies or energy discrepancies, requiring thoughtful parameter selection.
- Analysis reveals that VMD's FFT-based implementation ensures efficiency, especially in longer signals, with a computational advantage over EMD's complexity.
- Multivariate VMD extends the single-channel approach to multi-channel data, ensuring aligned extraction of modes across channels for applications like EEG/MEG analysis.
- Recursive VMD offers a multi-level decomposition to delve into complex nested structures for hierarchical analysis, while standard VMD suffices for most applications.
Read Full Article
24 Likes
Alvinashcraft
91

Dew Drop – June 10, 2025 (#4436)
- TechBash 2025 Early Bird Registration Extended 3 Weeks with Featured Speaker from Microsoft.
- GitHub Copilot helps beginners with code review and refactoring.
- Angular 20 updates are discussed.
- Microsoft introduces a new Start menu for Windows 11.
- Visual Studio GitHub Copilot now offers next edit suggestions.
- Recap of news from Apple's WWDC 2025 developer conference.
- Guide on importing a JavaScript string and common CSS layouts.
- Enhancements in Kubernetes event management and OAuth applications.
- Overview of the httpResource API in Angular.
- Method to create an auto-closing notification with an HTML popover.
Read Full Article
5 Likes
Dev
4.8k

Image Credit: Dev
🗂️ Master SQL from Scratch – A Step-by-Step Roadmap with Visual Guide & Progress Tracker
- Structured roadmap for mastering SQL from beginners to intermediate learners.
- Divided into three milestones: Fundamentals, Intermediate Concepts, and Advanced Techniques.
- Includes units on SQL Fundamentals, Intermediate SQL Concepts, and Advanced SQL Techniques.
- Provides hands-on exercises, visual guide, and progress tracking for organized learning.
Read Full Article
40 Likes
Dev
262

Image Credit: Dev
A Deep Dive into Arrays – Part 1: What, Why & How
- An array is a data structure that holds multiple values of the same data type in contiguous memory locations, making access very fast.
- Arrays are optimized for locality of reference, allowing for faster memory access by capitalizing on spatial and temporal locality patterns.
- Array elements are stored contiguously, which helps in preloading nearby elements into the CPU cache for quick access, making arrays ideal for storing large amounts of data and performing operations on all elements efficiently.
- The next topic to explore is dynamic arrays, which deal with growing or shrinking arrays dynamically based on needs.
Read Full Article
15 Likes
Discover more
- Software News
- Web Design
- Devops News
- Open Source News
- Databases
- Cloud News
- Product Management News
- Operating Systems News
- Agile Methodology News
- Computer Engineering
- Startup News
- Cryptocurrency News
- Technology News
- Blockchain News
- Data Science News
- AR News
- Apple News
- Cyber Security News
- Leadership News
- Gaming News
- Automobiles News
Programesecure
65

Top slots and live games for players from Poland
- Online gambling in Poland is on the rise, with players showing a preference for quality slots and live games due to their fast access and realistic casino experience.
- Slots with bonus features like freespins and multipliers are particularly popular among Polish players, with games like Sweet Bonanza and Legacy of Dead being top choices.
- Live games offer an immersive casino atmosphere with popular options like roulette, blackjack, and new game shows such as Crazy Time and Monopoly Live, attracting both luck-based and strategy-focused players.
- Irwin casino is a favored platform in Poland for its wide game selection, Polish interface, and efficient customer support, offering slots, live games, and attractive promotional deals.
Read Full Article
3 Likes
Dev
402

Image Credit: Dev
Crap, is Node.js Dead? I Barely Warmed Up My Express App!
- OpenAI announced the move of their Codex CLI tool from Node.js to Rust, sparking tech anxiety and debates among developers worldwide.
- The transition was made to enable the tool to function as a single, self-contained binary without dependencies, a task at which Rust excels.
- Rust was chosen for its performance capabilities, particularly in handling high-intensity tasks without interruptions characteristic of Node.js's garbage collector.
- Despite this shift, Node.js remains a strong player in web development and server-side tasks, while Rust was tailored to fit OpenAI's specific requirements.
- OpenAI's Rust version will support JavaScript extensions, indicating a continued connection with the JS community.
- The real challenge for developers lies in managing complex development environments with multiple languages and tools, causing workflow inefficiencies.
- ServBay offers a solution for developers to easily switch between different languages and tools, simplifying the setup and management of services like Node.js and Rust.
- The platform allows developers to run Node.js and Rust projects concurrently, ensuring a clean and efficient development environment with minimal hassle.
- Instead of getting caught up in language wars, developers are encouraged to focus on creating innovative projects using the tools that best suit their needs.
- ServBay provides a convenient and harmonious way for developers to work with various technologies without the stress of managing complex development environments.
Read Full Article
24 Likes
Medium
78

Top 5 Udemy Programming Courses For Beginners
- Top Udemy programming courses for beginners feature instructors like Dr. Angela Yu, Haris Ali Khan, Jonas Schemdtmann, Abdul Bari, and Kurt Anderson.
- Dr. Angela Yu's course is beginner-focused and includes real-world projects for aspiring software developers.
- Haris Ali Khan's course is beginner-friendly, updated for 2025, and suitable for those with no coding experience, offering clear explanations and hands-on practice for students and beginners.
- Courses by Jonas Schemdtmann, Abdul Bari, and Kurt Anderson cater to beginners and intermediate learners, covering JavaScript, Java, and computer science theory, respectively, to help build skills for web development and tech careers.
Read Full Article
4 Likes
Dev
359

Image Credit: Dev
Cookie Consent Banners: The UX Nightmare Every Developer Inherits (And How to Actually Fix It)
- Implementing cookie consent banners without focusing on UX can lead to a significant drop in conversion rates and cause various issues like accessibility problems and legal compliance challenges.
- Developers often face the dilemma of balancing legal requirements, UX best practices, technical implementation, and performance optimization when dealing with cookie consent banners.
- A good implementation of cookie consent involves smart techniques like lazy loading, event delegation, proper localStorage management, A11y compliance, and mobile-first responsive design.
- Properly implemented cookie consent banners can actually enhance user engagement, improve page performance, boost accessibility scores, and ensure legal compliance.
Read Full Article
21 Likes
Self-Learning-Java
214
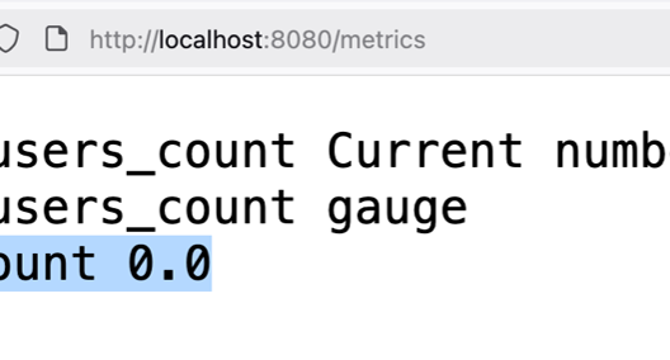
Image Credit: Self-Learning-Java
How to expose Gauge metric using Prometheus Java Client?
- Prometheus uses Gauge as a metric type to represent a single numerical value that can fluctuate.
- Gauge is used to track current values that can go up or down such as memory, CPU usage, and queue size.
- In Java with Prometheus client library, Gauges are defined and updated based on logic like setting, increasing, or decreasing values.
- An example Java application with Gauge metric for active users count is provided, demonstrating how to use Gauges to monitor and expose metrics.
Read Full Article
12 Likes
Self-Learning-Java
428

Image Credit: Self-Learning-Java
How to add labels to the exposed Prometheus metrics in Java?
- Prometheus uses labels as key-value pairs attached to metrics to provide more context.
- Labels in Prometheus help differentiate data points for a metric.
- In Java, labels can be added when building metrics using methods like 'labelNames'.
- Labels can be set and incremented for metrics to capture specific information such as endpoint and app name.
Read Full Article
25 Likes
Javacodegeeks
197

Image Credit: Javacodegeeks
Add Line Break After Log Statement Example
- Logging is crucial for understanding application behavior, but raw logs can be overwhelming without clear separation.
- Adding a line break after log statements can enhance log readability and distinguish between operations.
- Methods to add line breaks in Java logs include using System.lineSeparator() dynamically for platform-specific separators.
- By appending System.lineSeparator() to log messages, blank lines can be added effectively.
- Using SLF4J placeholders, System.lineSeparator() can be incorporated for better log formatting.
- An example code snippet demonstrates adding line breaks after log statements.
- Another approach involved pre-Java 7 usage of System.getProperty("line.separator") for line breaks.
- Configuring global blank lines in log patterns (e.g., logback.xml) can offer a consistent way to add spacing.
- Logback configuration with %n%n appends an extra blank line globally for better log layout.
- In conclusion, setting up logger patterns globally for blank lines can improve log readability, aiding in effective log analysis.
Read Full Article
11 Likes
Medium
279

Image Credit: Medium
My Node.js App Was Dying… Here’s How I Saved It
- The author shares their experience of rescuing a Node.js application that was struggling with performance issues as user traffic increased.
- Initially, the application worked well on the author's machine but started slowing down and crashing as more users accessed it.
- The author and their team developed a real-time collaboration tool that faced challenges such as requests timing out, user complaints about lag, and server logs indicating issues.
- To improve the application's performance, the author decided to delve deeper into Node.js capabilities and implement necessary changes to optimize the app.
Read Full Article
16 Likes
Insider
354

Image Credit: Insider
Tech companies have a new hiring requirement: vibe coding
- Tech companies like Visa, Reddit, DoorDash, and others are now seeking candidates with experience in vibe coding, which involves using AI tools to generate code.
- Vibe coding is being viewed as a way to boost product development speed, with companies aiming to increase their productivity by utilizing AI coding tools like Cursor and Bolt.
- While vibe coding is becoming increasingly essential for faster coding and prototype generation, it is not expected to replace senior engineers in the industry anytime soon.
- The emphasis on vibe coding in tech job ads reflects the industry's focus on accelerating product development and enhancing engineering team efficiency through AI-driven coding tools.
Read Full Article
21 Likes
Dev
187

Image Credit: Dev
AI Funding and Developments: Navigating the 2025 Landscape
- AI funding in 2025 continues to surge, with global venture capital investments surpassing $80 billion in Q1. North America leads with 86.2% of global AI capital influx.
- India emerges as a strong player in AI, with government initiatives, infrastructure enhancement, and rising startup activity propelling the nation forward.
- Notable funding highlights include OpenAI securing a $40 billion round, Anysphere raising $900 million, and Inflexor Ventures targeting a $150 million fund for AI investments.
- Investors prioritize AI ventures with proven use cases and ROI, leading to a shift towards vertical AI applications and an emphasis on ethical and governance frameworks.
Read Full Article
11 Likes
PlanetPython
192

Image Credit: PlanetPython
Django Weblog: Django bugfix releases issued: 5.2.3, 5.1.11, and 4.2.23
- Django team issues bugfix releases for Django 5.2.3, 5.1.11, and 4.2.23 to complete mitigation for CVE-2025-48432.
- The updates address potential log injection via unescaped request path by migrating remaining response logging paths to a safer implementation.
- The bugfix releases do not introduce new CVE but strengthen the original fix, urging all Django users to upgrade promptly.
- Patches to resolve the issue have been applied to Django's main, 5.2, 5.1, and 4.2 branches, with download links and checksums provided for the new releases.
Read Full Article
11 Likes
For uninterrupted reading, download the app