Programming News
Medium
43

Image Credit: Medium
Running A Decentralized Network From Your Phone: Meet Avail’s Light Client
- Full nodes in blockchain networks require high resources and technical skills, leading to centralization among less than 1% of users.
- Avail's Light Client offers full node guarantees with lower resource demands through a modular and mathematically sound approach.
- Avail's Light Client employs Data Availability Sampling (DAS) by sampling data cells with KZG commitments, ensuring data availability.
- Block Verification in Avail's Light Client involves creating a data matrix, sampling cells, and repeating the process for data confidence.
- The Light Client Network uses a peer-to-peer (P2P) structure with Kademlia DHT for data sharing and block verification.
- Developers can customize the Light Client for Execution Verification, ensuring the State Transition Function for full execution correctness.
- Sophon Network successfully implemented Avail's Light Client for decentralized verification, allowing users to participate and earn rewards.
- Avail's Light Client provides trustless verification, low hardware requirements, and scalable infrastructure, enabling decentralization for various applications.
- It stands out for its validator decentralization and empowers users on any device to contribute to network verification.
- Avail's Light Client is suited for DEXs, Validiums, L2s, DA chains, consumer apps, and more.
Read Full Article
2 Likes
RealPython
17
Image Credit: RealPython
Starting With DuckDB and Python
- The DuckDB database offers a streamlined way to manage large datasets in Python with OLAP optimization.
- Users can create databases, verify data imports, and execute efficient data queries using SQL and DuckDB's Python API.
- The video course teaches users to create DuckDB databases by importing data from files like Parquet, CSV, or JSON and storing it in a table.
- Querying a DuckDB database in Python involves utilizing standard SQL syntax through a DuckDB connection object.
- DuckDB's Python API enables method chaining for an object-oriented approach to database queries.
- Concurrent access in DuckDB allows multiple reads while limiting concurrent writes to uphold data integrity.
- DuckDB seamlessly integrates with pandas and Polars by transforming query results into DataFrames using the .df() or .pl() methods.
Read Full Article
1 Like
Medium
187

Title: “How to Become Popular on Instagram in 2025: My Honest Journey”
- 1. Posting consistently is key to gaining recognition on Instagram; using the same audio clip in Reels helped create an identifiable brand for the user.
- 2. Developing a strong visual style using tools like Figma and Behance can make an Instagram page look professional and build trust.
- 3. Engaging actively on Instagram Threads can lead to building real conversations and increase visibility on the platform.
- 4. Maintaining a consistent digital identity across all platforms is essential for users and algorithms to recognize and connect with your content.
- 5. Building your digital presence on Google through platforms like Medium and Blogger can increase discoverability and aid in becoming verified on Instagram.
- 6. Becoming popular on Instagram requires strategy and recognition rather than just amassing a large number of followers.
- 7. The user emphasizes the importance of being discoverable in the world of algorithms for achieving true popularity on social media.
Read Full Article
11 Likes
Logrocket
353

Image Credit: Logrocket
How to design apps with Apple Intelligence in mind
- Apple introduced significant advancements to Apple Intelligence at the recent WWDC Conference, shifting towards an ambient entity rather than a chatbot approach.
- Developers and designers need to adapt to these changes when designing modern web applications.
- Apple Intelligence is integrated into Apple devices, providing context-aware assistance such as replying to emails or summarizing conversations.
- AI developments include on-device Foundation Models Framework, ChatGPT integration, and Visual Intelligence for screen interaction.
- Design implications focus on intent-based design, user privacy, and the shift from chatbot-focused AI to personal assistant AI.
- Best practices highlight the importance of user control, minimizing bias, transparency, and respecting data privacy.
- Apple Intelligence signals a future of ambient intelligence, personal expression through AI, and privacy-centric AI integration into the OS.
- Overall, the article discusses the shift towards ambient AI, privacy considerations, and the future of interface design with Apple Intelligence.
- The article provides insights on Apple Intelligence's impact on interface design and the role of developers and designers in creating intelligent, user-centric applications.
- Key takeaways include a focus on intent-based interactions, privacy-first design, and embracing generative AI for personal expression and creativity.
- Embracing Apple Intelligence marks a fundamental shift in AI design towards ambient, personalized user experiences while prioritizing privacy and user control.
Read Full Article
21 Likes
Discover more
- Software News
- Web Design
- Devops News
- Open Source News
- Databases
- Cloud News
- Product Management News
- Operating Systems News
- Agile Methodology News
- Computer Engineering
- Startup News
- Cryptocurrency News
- Technology News
- Blockchain News
- Data Science News
- AR News
- Apple News
- Cyber Security News
- Leadership News
- Gaming News
- Automobiles News
Medium
235

Image Credit: Medium
Software Migrations Are Not Free
- Software migrations can be complex and costly, especially when managing multiple versions simultaneously.
- Before initiating a migration, it's crucial to involve the team in discussions about supporting multiple versions.
- Strategic planning for migrations signals leadership readiness and ensures deliberate decision-making.
- When rolling out a new version, gradual adoption and clear communication with clients are key.
- Each new version commits to maintaining the old one for a period.
- Setting a time frame for migrations helps maintain momentum and stakeholder interest.
- Partial migrations are advised over all-or-nothing approaches to reduce risks.
- Assigning ownership of the migration plan within the team ensures accountability and continuity.
- Thorough documentation of migration processes and reasons is essential for future reference.
- Migration involves both technical and organizational shifts, necessitating careful planning.
- If stuck during migration, reassess remaining tasks, set new deadlines, and designate responsibility for completion.
- Success in migrations requires planning, timeboxing, and careful execution to minimize challenges.
- Migrations can be eased with proper preparation and adherence to planned timelines.
- Managing migrations diligently can lead to smoother transitions and future project success.
Read Full Article
14 Likes
Medium
353

Image Credit: Medium
Function Calling in Large Language Models: Unlocking Practical Applications with Real-World Cases…
- ChatGLM's function calling feature enhances the model's reasoning and external operation capabilities.
- Tools are an optional parameter in the content generation API for providing function definitions to the model.
- The API generates function parameters based on user specifications without performing actual function calls.
- Developers can use the model's output parameters for executing function calls in applications.
- The tutorial covers building a student grade database, implementing query and data filtering functions, and using LLM function calls for database interactions.
- Non-technical users can interact with the database using natural language through LLM function calls.
- For technical personnel, understanding LLM function calls aids in implementing relevant functions.
- A student exam score Q&A service example demonstrates generating scores for 100 students and saving data to an SQLite database.
- Simple database query operations are implemented to ensure proper database functioning.
- Five functions are defined and structured for LLM selection, including name, description, parameter list, and descriptions.
- Function calling, obtaining return results, and using LLM for question answering are demonstrated.
- The tutorial summarizes the working principle of LLM function calls for practical applications.
- This content focuses on the application of function calling in ChatGLM for various operations and interactions.
- It emphasizes the integration of external function libraries with ChatGLM models.
- The tutorial highlights the importance of understanding LLM function calls for both technical and non-technical users.
- Overall, the tutorial showcases the potential of LLM function calls in enhancing model capabilities and real-world applications.
Read Full Article
21 Likes
Dev
136

Image Credit: Dev
The Importance of Leveraging AI to Learn
- Artificial Intelligence (AI) is crucial for tasks requiring human intelligence like reasoning and learning.
- It is essential to use AI effectively in the learning process as it is becoming increasingly prominent.
- Junior developers shouldn't depend solely on AI for generating code; it's crucial to learn from the process.
- AI should be used as a learning companion and guide to challenge understanding and support growth.
- The quality of AI-generated responses is determined by the quality of the prompts given to it.
- Six building blocks for a good prompt include clear task definition, providing relevant context, sharing exemplars, specifying persona, defining format, and deciding on tone.
- Following a prompting framework can enhance communication with AI and lead to accurate and helpful responses.
- AI should be viewed as a supportive tool in the educational journey, not as a replacement for learning.
Read Full Article
8 Likes
Medium
263
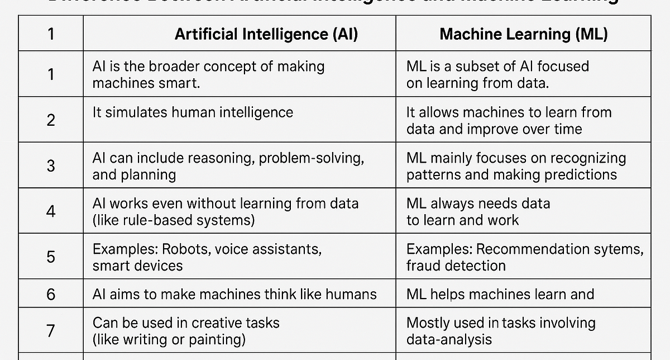
Image Credit: Medium
Difference Between Artificial Intelligence and Machine Learning
- Artificial Intelligence (AI) is a branch of computer science that aims to create intelligent machines capable of performing tasks requiring human intelligence.
- AI systems simulate human intelligence and can be rule-based or data-driven.
- Examples of AI include voice assistants like Siri, self-driving cars, and chatbots.
- Machine Learning (ML) is a subfield of AI that focuses on developing algorithms allowing computers to learn from data and make predictions without explicit programming.
- Key characteristics of ML include learning from historical data, improving accuracy over time, and requiring large datasets for training.
- Examples of ML include email spam filters, movie recommendations on Netflix, and product recommendations on Amazon.
- Real-life examples of AI vs. ML include a robot vacuum planning its cleaning path (AI) and predicting prices of used cars based on data (ML).
- Differences between AI and ML include the approach to problem-solving and the focus on learning from data.
- Understanding the distinctions between AI and ML is crucial for further advancements and application development in modern computing.
Read Full Article
15 Likes
Technically Dev
381
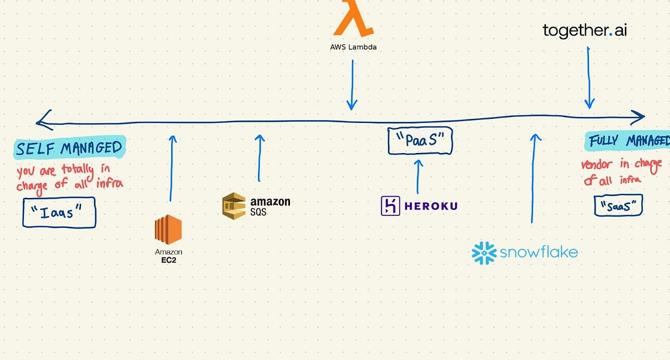
Image Credit: Technically Dev
Breakdown: the cloud infrastructure market
- Infrastructure and cloud refer to where software runs, involving hardware, networking, and systems enabling online activity.
- In the past, software primarily operated locally on individual devices, but now most software is cloud-based.
- The shift to cloud computing led to new considerations for developers, such as choosing the right cloud provider and service model.
- Different types of infrastructure include IaaS, PaaS, and SaaS, offering varying levels of management and customization.
- IaaS provides basic server resources, PaaS offers more managed services, and SaaS is fully managed.
- The choice between these options depends on the level of control and customization required by developers.
- The components of an app that need infrastructure support include frontends, backends, databases, analytics, and miscellaneous tasks.
- Companies like AWS, Cloudflare, DigitalOcean, Heroku, and Vercel cater to different infrastructure requirements.
- The evolving landscape of cloud infrastructure offers diverse solutions for developers based on their needs and preferences.
Read Full Article
22 Likes
Dev
52

Image Credit: Dev
Writing Your First Automated Test Using Python (unittest Framework)
- Python's unittest framework is a good starting point for testing journeys, as it comes bundled with Python and is an industry standard.
- unittest is a unit testing framework in Python standard library, following the xUnit style, used for writing test cases as classes and using special methods for test context.
- The article presents a step-by-step guide to building your first Python test, starting with creating a function to be tested and writing test cases using assertions.
- Testing for exceptions using methods like assertRaises( ) is highlighted, emphasizing the importance of handling edge cases in real projects.
- Maintaining scalability in test projects involves organizing the structure effectively, separating production code from test files for easy management.
- The usage of setUp() and tearDown() methods for managing test context is explained, ensuring tests run independently and cleanly.
- Running tests using verbose mode (-v flag) provides more detailed output, beneficial when dealing with numerous test cases.
- The article outlines when to use unittest versus Pytest, highlighting the significance of thinking like a tester while mastering unittest syntax.
- Mastering unittest is crucial for Python developers to write clean, testable, and production-ready code, instilling confidence in test automation processes.
Read Full Article
3 Likes
Logrocket
117

Image Credit: Logrocket
How to optimize your Next.js app with after()
- Building apps with Next.js involves optimizing server tasks post-response using the after() API of Next.js 15.
- after() allows running logic after route rendering without impacting the client's experience, beneficial for tasks like analytics or logging.
- It works in Server Components, Actions, Route handlers, and Middleware, with varying access to request info.
- Nested after() calls execute in reverse order of their rendering, providing a clean way to handle post-response tasks.
- after() runs even during errors, ensuring critical tasks like logging continue despite route failures.
- Key considerations include after()'s static nature, need for manual gating of conditional logic, and limitations in dynamic reactivity.
- alternatives to after() include waitUntil() for Edge Middleware and await for tasks that must complete pre-response.
- Utilizing after() effectively can significantly enhance web app performance and user experience by deferring non-critical tasks.
Read Full Article
7 Likes
Logrocket
335

Image Credit: Logrocket
A complete guide to AdTech for product managers
- Monetizing products with ads through AdTech can be highly profitable for high-traffic websites.
- Understanding the complexities of the advertising ecosystem and how AdTech works is crucial for maximizing ad revenue.
- AdTech involves publishers, advertisers, ad slots, inventory, ad servers, SSPs, DSPs, ad exchanges, direct deals, and more.
- Automation by ad servers streamlines the process of delivering and tracking ads on publisher websites.
- SSPs and DSPs help automate buying and selling inventory between publishers and advertisers.
- Ad exchanges function as automated online auctions, facilitating ad placements based on bids from DSPs.
- Direct deals between advertisers and publishers can occur for premium ad placements.
- All-in-one platforms like Google Ad Manager streamline ad serving and exchanges, reducing costs.
- Various other players like ad networks, data platforms, and agency trading desks play roles in the AdTech ecosystem.
- Adding ads to products involves building ad slots, utilizing ad server tags, selecting SSPs, and setting up header bidding.
Read Full Article
20 Likes
Alvinashcraft
170

Dew Drop – June 24, 2025 (#4445)
- Inside Access: Join Us at VS Live! Redmond for a Week of Deep Developer Learning (Mads Kristensen)
- LINQPad 9 Early Preview – LINQPad 9 is a major update unifying the Windows and macOS codebases (Joe Albahari)
- Build your code-first agent with Azure AI Foundry (Microsoft)
- Create a Contact Management App in .NET MAUI Using ListView and DataForm (Jayaleshwari N.)
- Introducing Mu language model and its impact on Windows Settings (Vivek Pradeep)
- Modernizing Win32 Apps with WinUI – Advanced Installer’s Approach (Renato Ivanescu)
- Technology & Friends – Scott Hanselman on New Technology and Old Friends (David Giard)
- Using SQL Server 2025 Vector Search in .NET Aspire – eShopLite Style! (Bruno Capuano)
- How to create light and dark color modes with CSS (Chris Ferdinandi)
- SSO Comes to Telerik and Kendo UI for a Simpler, More Secure Account Access (Dragan Grigorov)
Read Full Article
10 Likes
Medium
379

Image Credit: Medium
A 5-Step Prompt To Land More Data Job Interviews
- A 5-step prompt designed for Google Gemini to enhance landing more data job interviews.
- The prompt involves feeding information to an AI Agent, aligning job roles with resume summaries, updating resume for stronger applications, and ranking job matches based on descriptions.
- The strategy includes engaging in conversations with the AI agent for detailed resume refinement and highlighting key skills.
- The approach focuses on iterating over an existing resume for impactful improvements.
- The prompt aims to streamline the data recruiting process and optimize resume content.
- It encourages personalized interactions with AI to enhance application success.
Read Full Article
22 Likes
Dev
298

Image Credit: Dev
Steering Clear of Implementation Disasters: Your Guide to Successful Dynamics 365 Deployment
- Organizations embarking on Dynamics 365 deployment face common pitfalls that can hinder success.
- Thorough planning with proper business analysis and requirements gathering is crucial for success.
- Stakeholder alignment is essential to prevent conflicting priorities from derailing the project.
- Data migration is a challenging aspect due to data quality issues and requires comprehensive audits.
- Change management is critical for successful implementation, requiring more than just training.
- Creating a culture that embraces change and clear communication are key to overcoming resistance.
- Integration challenges with existing applications require detailed planning and testing.
- Testing and quality assurance are crucial to catch issues before deployment and ensure a smooth transition.
- Comprehensive testing should include functional, performance, security, and user acceptance testing.
- Parallel running periods with old and new systems aid in a safe deployment transition.
- Successful implementation involves addressing planning, data quality, change management, integration complexity, and testing.
- Investing time and resources in these areas increases the chances of realizing the full benefits of the new system.
Read Full Article
17 Likes
For uninterrupted reading, download the app