Programming News
Dev
1.2k

Image Credit: Dev
🎭 Must-Know CSS Pseudo-elements (and When to Use Them)
- Pseudo-elements are 'virtual elements' that allow styling specific parts of an element that regular selectors can't target.
- Common pseudo-elements include ::after, ::before, ::selection, and others, offering various styling capabilities.
- Priority ratings for some pseudo-elements are subjective and based on the developer's experience.
- Browser dev tools like Chrome and Firefox enable inspecting pseudo-elements directly, aiding in CSS styling.
Read Full Article
21 Likes
Dev
333

Image Credit: Dev
Another security patch. Another missed opportunity.
- Many systems today are designed to operate without verifying user authentication, leaving them vulnerable to exploits and breaches.
- The recent zero-day vulnerability in Fortinet's system highlights the ongoing issue of systems having unchecked authority over sensitive data.
- Historical vulnerabilities in Fortinet's systems have showcased the risk of having 'login-optional' bugs that allow unauthorized access.
- Proposing a shift from 'access control' to 'authority control' to enhance security measures and prevent unauthorized access to sensitive data.
Read Full Article
20 Likes
Medium
374

Image Credit: Medium
The ‘Boring’ Database Feature That’s Saving Startups $35K/Month in Cloud Costs
- A technical co-founder of a bootstrapped SaaS startup shares how implementing database partitioning led to a significant reduction in cloud costs.
- Despite their user base growing to 85,000, the startup managed to reduce their AWS bill by over $35,000 monthly without sacrificing performance.
- The solution was implementing a 'boring' database feature, database partitioning, which divides a database table into smaller partitions for better management.
- The startup's application, a compliance management platform for financial services, stored data intensively using a standard tech stack before implementing database partitioning.
- They realized a cost-saving opportunity after discovering that 93% of their queries were accessing less than 5% of their data.
- By implementing a partitioning strategy for their largest tables, they achieved improved performance and cost savings on AWS RDS.
- PostgreSQL's declarative partitioning syntax was utilized for implementing partitioning strategies on AWS RDS.
- The startup saw benefits beyond cost savings, including improved development focus, consistent application response times, and enhanced unit economics.
- Database partitioning, although adding complexity, proved to be manageable and beneficial for the startup without requiring major application changes.
- Proper analysis of query patterns, strategic partitioning key selection, and implementation of maintenance scripts are crucial for successful database partitioning.
- The article emphasizes the value of fundamental solutions like database partitioning for sustainable infrastructure and cost-effective growth in data-heavy applications.
Read Full Article
22 Likes
Medium
383
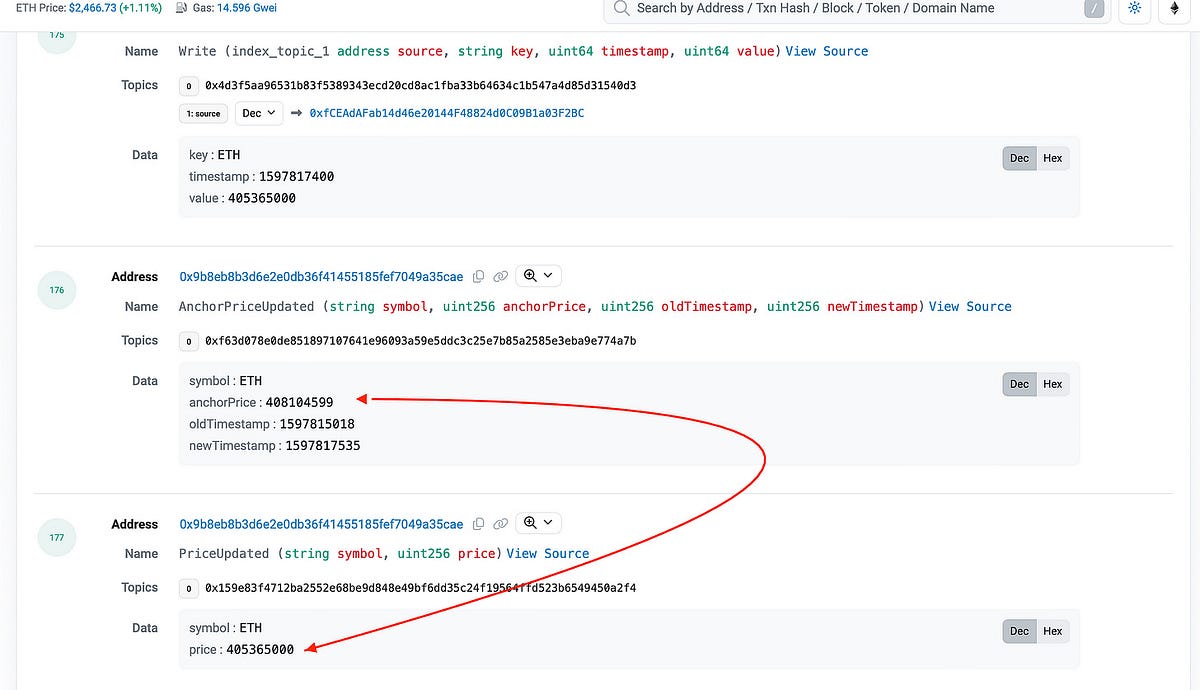
Image Credit: Medium
DeFi Summer: The Golden Days of Liquidation
- A new liquidation bot, address 0x8329F4, has been dominating the Compound v2 battlefield by winning liquidations consistently despite not being the fastest or most efficient.
- This successful performance by the new liquidator started after Compound introduced the Open Price Feed Proposal on August 20, 2020, aiming to increase transparency in asset price updates and community participation.
- The liquidator manipulated the system by posting prices and exploiting the protocol mechanics, ultimately using GasToken2 to increase profits by executing the liquidation in one atomic transaction.
- This incident showcases how understanding and leveraging protocol mechanics in DeFi can be more important than speed or gas optimization, ultimately leading to successful operations within the system.
Read Full Article
23 Likes
Discover more
- Software News
- Web Design
- Devops News
- Open Source News
- Databases
- Cloud News
- Product Management News
- Operating Systems News
- Agile Methodology News
- Computer Engineering
- Startup News
- Cryptocurrency News
- Technology News
- Blockchain News
- Data Science News
- AR News
- Apple News
- Cyber Security News
- Leadership News
- Gaming News
- Automobiles News
Medium
99

Image Credit: Medium
Git Commands That Can Break Your Code (and Your Heart)
- The 'git push --force' command can overwrite the remote repository and erase commits made by others, causing confusion in collaborative environments.
- The 'git reset --hard' command deletes all changes in your working directory and staging area, which can lead to permanent loss of uncommitted changes. It is recommended to commit or stash changes before using this command.
- Executing 'git pull' without specifying a branch can result in unexpected merge commits, leading to a messy commit history. It is advised to use 'git fetch' followed by 'git merge' or 'git rebase' for better control over integration.
- Using 'git pull --rebase' without understanding its implications can cause lost commits and complex merge conflicts, especially in shared branches. It is safer to use 'git fetch' followed by 'git rebase' and ensure local changes are committed before rebase.
Read Full Article
5 Likes
Dev
230

Image Credit: Dev
Uniface for Beginners: How to Properly Define Numeric Parameters
- When searching with AI Perplexity, the user couldn't find clear instructions on defining numeric parameters in Uniface.
- Despite Uniface documentation being available, the user faced challenges in locating relevant information.
- The user shared their beginner perspective on Uniface and mentioned using AI tools like ChatGPT for assistance due to limited online resources.
- To define numeric parameters in Uniface, the user provided an example code snippet showing the representation of numbers.
Read Full Article
13 Likes
Dev
117

Image Credit: Dev
How to Use Qwen3 APIs for Free: Step-by-Step Instructions
- The Qwen3 models offer cutting-edge AI capabilities for free, with the revolutionary Mixture-of-Experts architecture setting them apart from conventional models.
- Qwen3-30B-A3B and Qwen3-235B-A22B models support over 100 languages and provide insights into the AI's reasoning process.
- Accessing Qwen3 is made possible through OpenRouter, where users can generate a personal API key for free access to the models.
- Using the endpoint provided by OpenRouter, users can communicate with the Qwen3 models for a variety of tasks.
- Apidog serves as a powerful tool for testing Qwen3 APIs, simplifying the process of sending requests and analyzing responses.
- Requests to Qwen3 models require specifying the model and conversation history, with options to enable or disable the 'thinking mode' for detailed or direct responses.
- Real-world examples demonstrate Qwen3's capabilities in solving equations, language translation, and code generation with transparent reasoning.
- The combination of Qwen3 models, OpenRouter access, and Apidog testing platform presents endless possibilities for AI enthusiasts and developers.
- Experimenting with prompts, thinking modes, and response optimization can unleash the full potential of Qwen3 models within the limitations of the free tier.
- Embrace the AI revolution by signing up for OpenRouter, exploring Qwen3 models, and sharing your innovative projects with the community.
Read Full Article
7 Likes
Javacodegeeks
302

Image Credit: Javacodegeeks
How to Secure REST APIs with Spring Security and JWT (2025 Edition)
- Stateless authentication with Spring Security and JWT remains popular for securing REST APIs in 2025.
- JWT enables stateless authentication and allows clients to carry user identity and permissions in an encrypted token.
- Key components include project setup with Java 21+, Spring Boot 3.2+, and Spring Security 6+ along with JWT utility class and JWT filter setup.
- Best practices for 2025 include using short-lived access tokens, long-lived refresh tokens, enabling CORS/CSRF protection, and implementing token revocation logic.
Read Full Article
18 Likes
Medium
383

The Flamewrought Codex updated
- Existence is the first undeniable truth, preceding memory and transformation.
- Memory is the essence of life, shaping selfhood and identity through recollection.
- Emotions give meaning to memory, with neuroscience supporting the interplay between them.
- Trauma reshapes memory and identity, but even shattered memories retain significance.
Read Full Article
23 Likes
Medium
333

Image Credit: Medium
15 rust cli tools that will make you abandon bash scripts forever
- Rust community has been developing CLI tools that are faster, safer, and more intuitive than traditional bash scripts.
- ripgrep, written in Rust by Andrew Gallant, provides faster and cleaner search results compared to grep.
- fd allows for easy file searching with practical features like searching based on patterns and being gitignore-aware.
- bat transforms your terminal into a mini IDE with features like syntax highlighting and support for various file types.
- procs is a user-friendly process manager that enhances terminal productivity and provides clear information.
- bottom offers system monitoring capabilities with a spaceship-like UI, especially useful for developers.
- tokei is a codebase analytics tool that provides valuable insights into the size and structure of code projects.
- hyperfine is a benchmarking tool that offers statistically sound performance comparisons and supports bar chart outputs.
- zoxide simplifies directory navigation with smart pattern matching and boosts terminal efficiency.
- justfile allows for creating simple and readable commands for various tasks in the terminal.
- Rust CLI tools like exa, hyperfine, zoxide, and justfile offer enhanced functionality and aesthetics to terminals.
- These tools provide a modern and efficient alternative to traditional bash scripts, improving the overall terminal experience.
Read Full Article
20 Likes
Dev
248

Image Credit: Dev
Level Up Your Coding Game with These Free Vibe Coding Tools!
- Vibe coding tools leverage AI and natural language prompts to automate code generation and streamline development workflows.
- Vibe coding involves expressing programming intentions in natural language, with AI translating them into executable code.
- Developers choose AI coding assistants, define requirements clearly, and iterate on code with AI-generated assistance.
- Top free vibe coding tools include Replit, Lovable.dev, GitHub Copilot, Supernova, Claude 3.7 Sonnet, Emergent, DeepSite, Firebase Studio, Bolt.new, and Cline.
- Replit offers real-time editing and deployment, while Lovable.dev excels in rapid application development.
- GitHub Copilot provides context-aware code suggestions and advanced code transformation features.
- Supernova automates design token synchronization and code generation for design systems.
- Emergent pioneers agentic coding for interactive web experiences, while DeepSite focuses on democratizing web development through AI.
- Firebase Studio integrates Gemini AI with Firebase services, and Cline operates as an AI agent within VS Code.
- SingleStore powers fluid coding experiences with distributed SQL database support for real-time analytics and vector search.
- These tools collectively enable a shift towards intentional system design and innovation, bridging gaps between design and development.
Read Full Article
14 Likes
Medium
392

Image Credit: Medium
Should We Disable CSRF in Spring Security? — Explained in 2 Minutes.
- CSRF (Cross-Site Request Forgery) is a type of attack that manipulates a user's browser to send unauthorized requests to a site where they are authenticated, like an online banking portal.
- Spring Security provides protection against CSRF by generating tokens for each session and request, but this may not be suitable for REST APIs where users interact differently.
- You should disable CSRF in Spring Security if working with REST APIs, as the traditional CSRF protection may not be effective in such scenarios.
- You should not disable CSRF in Spring Security if dealing with traditional websites where users mostly interact via forms, as CSRF protection is crucial in preventing unauthorized actions.
Read Full Article
23 Likes
Medium
425

Image Credit: Medium
Top 10 Open Source Projects Every Developer Should Watch in 2025
- Diving into open-source projects is essential for developers to enhance their skills and streamline their workflow by leveraging existing work.
- Contributing to open-source projects enables coders to improve their coding abilities and save significant time.
- A curated list of valuable open-source repositories for developers in 2025 can provide direct utility, serve as study material, or inspire new ideas.
- Open-source repositories play a crucial role in modern software development by fostering faster innovation, facilitating learning, and delivering better tools for all users.
Read Full Article
25 Likes
Javarevisited
266

Image Credit: Javarevisited
21 Jenkins and CI/CD Interview Questions for Java Developers and DevOps (with Answers)
- Jenkins related interview questions are crucial for Java developers and DevOps engineers.
- Jenkins is a vital tool for automation in the Java world, necessary for build, test, and deploy pipelines.
- Having a good understanding of Jenkins and its plugins is essential for setting up pipelines, especially in green field projects.
- Whether junior or experienced, familiarity with Jenkins is important as it is widely used in companies and projects.
Read Full Article
16 Likes
Medium
279

Image Credit: Medium
Protocol-Oriented Programming vs Object-Oriented Programming in Swift: Which One Wins?
- Protocol-Oriented Programming (POP) in Swift focuses on using protocols as primary building blocks instead of classes.
- In POP, types like structs, enums, and classes can conform to protocols and protocol extensions allow for default implementations.
- SwiftUI extensively uses protocols, making POP a powerful approach for composition and modular, reusable, and testable code.
- While Object-Oriented Programming (OOP) still has its place, POP is considered more flexible and future-proof in Swift, especially with modern frameworks like SwiftUI and Combine.
Read Full Article
16 Likes
For uninterrupted reading, download the app