Programming News
Hackernoon
252

Image Credit: Hackernoon
Don't Mix Data Access Concerns With Essential Business Behavior
- Passing databases creates accidental coupling and breaks business encapsulation.
- Problems include tight coupling, mixed responsibilities, bijection violation, testability issues, business logic pollution, and violations of separation of concerns.
- Solutions recommended are to use dependency injection, avoid using the Repository Pattern, separate business logic, and design for decoupling.
- Refactorings and sample code are provided in the article to address the issue of mixing data access concerns with essential business behavior.
Read Full Article
15 Likes
Medium
292

Image Credit: Medium
Let’s dive into three super useful JavaScript functions: map(), filter(), and reduce().
- map() transforms each element of an array by applying a function and returns a new array with the transformed values.
- filter() selects elements from an array based on a condition provided by a test function and returns a new array containing only the passing elements.
- reduce() blends all elements of an array into a single output using a reducer function that combines each element with an accumulator.
- map(), filter(), and reduce() are powerful higher-order functions in JavaScript that simplify array manipulation and make code cleaner and more readable.
Read Full Article
17 Likes
Dev
121

Image Credit: Dev
Tutorial: Running Your C# Code Without a Project File
- The tutorial explains how to run C# code without a project file using the .NET 10 Preview SDK.
- This approach is helpful for quick tests, learning, and simple scripts without a full project structure.
- Using dotnet run file.cs, you can directly compile and run C# programs without a .csproj setup.
- You start by creating a C# source file named app.cs with basic code like printing to the console.
- The CLI implicitly creates a project definition based on the default dotnet new console template to compile and run the file.
- You can reference NuGet packages directly within the source file using app directives like #:package.
- Advanced options include specifying SDK, properties, and using directives for finer control.
- On Unix-like systems, you can make C# files executable like shell scripts using a shebang line.
- The file-based execution model in .NET 10 Preview is recommended for simplicity and quick tasks, not for complex applications.
- To transition to a full project structure, you can use dotnet project convert app.cs.
Read Full Article
7 Likes
Medium
153

Image Credit: Medium
Lifetimes in Rust aren’t that hard
- Rust's lifetimes play a crucial role in memory management and preventing dangling references.
- Generic lifetime annotations ensure that return values do not outlive their corresponding arguments.
- Returning references to local variables can lead to dangling references if not handled correctly.
- In Rust, 'static lifetimes are used for string literals and data intentionally leaked to live for the entire program duration.
Read Full Article
9 Likes
Discover more
- Software News
- Web Design
- Devops News
- Open Source News
- Databases
- Cloud News
- Product Management News
- Operating Systems News
- Agile Methodology News
- Computer Engineering
- Startup News
- Cryptocurrency News
- Technology News
- Blockchain News
- Data Science News
- AR News
- Apple News
- Cyber Security News
- Leadership News
- Gaming News
- Automobiles News
Medium
108
Image Credit: Medium
Federated Business Services: Escaping the Functional Monolith, One Event at a Time
- Functional monoliths in organizations, such as central billing teams, create bottlenecks and dependencies on other departments for tasks like invoicing.
- Federation in business services involves decentralizing ownership of processes like pricing, invoicing, and communication to enable autonomy and speed.
- Central teams shift from doing the work to providing tools and rules for other teams to execute tasks within boundaries in a federated model.
- Federated systems require clear ownership, well-defined events, and good observability to scale autonomy and reduce integration costs.
- Events serve as the backbone of federated business capabilities, ensuring communication and coordination among different teams.
- Contracts, clear ownership, and visibility are essential components for successful implementation of federated business capabilities.
- Federation promotes a cultural transformation in organizations by fostering trust, autonomy, and shared language among teams.
- The shift to federated business capabilities extends beyond invoicing to areas like pricing logic, communication triggers, document generation, and data ownership.
- Organizations that embrace federated models move faster, reduce coordination costs, and improve scalability and flexibility in their core business operations.
- Embracing federation in business services shifts the focus from control to empowerment, leading to more efficient, robust, and adaptable systems.
Read Full Article
6 Likes
Dev
387

Image Credit: Dev
Build a Real-Time News AI Agent Using LangChain — In Just a Few Steps!
- AI agents have emerged as powerful applications of large language models, capable of understanding natural language, reasoning, and completing tasks autonomously.
- The article explores building a sophisticated real-time news AI agent with capabilities like fetching current events, web searches, and engaging in conversations locally.
- AI agents differ from traditional chatbots by their autonomy, decision-making abilities, and access to a toolkit of specialized functions for problem-solving.
- The architectural deep dive reveals the use of LangChain for building the news agent, leveraging OpenAI's GPT models and specialized tools for various functionalities.
- The agent's toolkit includes features like web search using DuckDuckGo, news tools for fetching latest and location-specific news, calculator, and time tool.
- The implementation involves setting up Python environment, installing dependencies, and using API keys for tools like OpenAI, DuckDuckGo, and NewsAPI.
- The complete code workflow involves creating an agent, defining tools, setting up the agent prompt, processing user input, and launching the AI Agent dashboard.
- SingleStore integration is recommended for enhanced data persistence, real-time analytics, and efficient news data management to scale the news AI agent effectively.
- The repository provides guidance on integrating SingleStore for storing and retrieving information from a vector database, enhancing the agent's knowledge retrieval capabilities.
- The article showcases the power of combining large language models with practical tools, demonstrating how AI agents can provide real-time information while respecting user privacy and control.
Read Full Article
23 Likes
Dev
283

Image Credit: Dev
Fruit Memory Match Game – Boost Brainpower with Fun!
- The Fruit Memory Match Game is a powerful tool to improve memory, focus, and cognitive skills for all age groups.
- It is a digital or printable card game with bright fruit graphics, multiple difficulty levels, and timer tracking.
- Benefits include cognitive development, visual recognition, improved concentration, and it offers family fun and learning.
- The game features popular fruits like Apple, Banana, Grapes, and Strawberry, designed to be visually appealing and engaging.
Read Full Article
17 Likes
Dev
18

Image Credit: Dev
🎥Unlock Google Veo 3 Today: 3 Insider Methods You Can't Afford to Miss
- Google Veo 3 is at the forefront of the AI revolution, offering new possibilities in video production without the need for specialized training or expensive equipment.
- Veo 3's cinematic quality, realistic textures, natural motion flow, and integrated speech generation capabilities set it apart as a game-changer in AI-generated video technology.
- Industries like Klarna have witnessed a significant reduction in production time and cost savings through the implementation of Veo technology for video creation.
- Three insider methods are shared for accessing Google Veo 3: using Google Flow for intuitive interaction, leveraging Google Cloud's $300 credit, and accessing Veo 3 through the Developer's Pathway.
- Google Veo 3 offers an educational advantage with discounted or free access for verified students, making the technology accessible even on a tight budget.
- Crafting detailed prompts with Veo 3 is essential for exceptional results, impacting the quality of AI-generated videos, including specifying subjects, contexts, directions, and emotional elements.
- Veo technology represents a transformation in visual content creation, empowering creators of all levels to realize their visions without traditional barriers.
- The democratization of video production through Veo 3 signifies a significant shift towards easier access to advanced creative tools, offering multiple pathways for creators to explore and adapt to the evolving digital landscape.
- The AI video revolution has arrived with Google Veo 3 leading the way, presenting opportunities for creators to innovate and thrive in the increasingly visual digital world.
- Adapting early to AI-driven creative workflows will provide significant advantages for creators, assisting them in harnessing transformative technologies like Google Veo 3 effectively.
Read Full Article
1 Like
Medium
360

Image Credit: Medium
Best practices for using digital signs kiosk during sales and promos
- Digital signage kiosks are essential for in-store marketing strategies, especially during sales and promotional events.
- Best practices include using short and direct messages with bold fonts, compelling calls to action, and visually appealing content.
- Placement strategies suggest putting signage at eye level in high-traffic areas, using time-based scheduling, and ensuring real-time content updates for relevancy.
- To maximize ROI, align digital signage with broader marketing goals, integrate interactive features for data collection, and prioritize staff training and technical maintenance.
Read Full Article
21 Likes
Medium
198

Image Credit: Medium
The Unusual Power of TypeScript: Embracing Functional Programming for Robust Applications
- Functional programming in TypeScript involves using techniques like tagged unions, pattern matching, and Algebraic Data Types (ADTs) to write clear and reliable code.
- With TypeScript's support for union types and structural typing, developers can model entire states and flows of applications efficiently.
- Functional programming patterns like discriminated unions and pattern matching offer centralized ways to define states, ensuring all cases are handled for safety and maintainability.
- Tagged unions combined with type narrowing in TypeScript enable intelligent inference and the ability to simulate match expressions for robust code.
- Algebraic Data Types (ADTs) in TypeScript allow precise and exhaustive description of complex data structures, ensuring correctness and scalability.
- Using ADTs for actions, developers can guarantee the structure of each action, leading to increased safety and correctness in processing actions.
- Immutable design principles in functional programming, encouraged by tagged unions and ADTs, help in clearer state transitions and cleaner, safer code.
- Functional programming patterns like tagged unions and ADTs aid in explicit domain modeling, enforcing valid states and preventing unrealistic combinations.
- These patterns lead to faster development, easier testing, and more confident refactoring by providing isolated, immutable states for testing scenarios.
- Functional programming patterns in TypeScript offer advantages in managing complex app states and actions, reducing complexity and improving stability.
Read Full Article
11 Likes
Damienbod
112

Image Credit: Damienbod
Revisiting using a Content Security Policy (CSP) nonce in Blazor
- Implementing a strong Content Security Policy (CSP) in web applications using Blazor and ASP.NET Core is crucial for security.
- CSP nonce or hashes should be used to enhance security, with nonce being the recommended choice.
- Blazor offers various application types and render modes, with only certain types supporting CSP nonce.
- The NetEscapades.AspNetCore.SecurityHeaders Nuget package can be utilized to implement security headers, including CSP nonce, in ASP.NET Core applications.
Read Full Article
6 Likes
Javacodegeeks
261

Image Credit: Javacodegeeks
Using Signals in Angular 17: Goodbye NgRx for Simple State?
- Angular 17 introduces Signals, a new reactive primitive for managing local component state, offering a cleaner and more intuitive approach compared to using NgRx and RxJS.
- Signals provide a simpler API with lower complexity, minimal boilerplate, and automatic change detection, making them ideal for managing local/component state and UI-related functionalities.
- Examples provided demonstrate how Signals can be used in scenarios like managing a counter, toggling visibility, and deriving state, showcasing their advantage in readability and reactivity.
- To decide between Signals, RxJS, and NgRx, consider using Signals for local state, UI flags, and deriving state, while reserving RxJS/NgRx for asynchronous data, global state, side effects, and advanced features.
Read Full Article
15 Likes
Dev
67

Image Credit: Dev
Stay ahead in web development: latest news, tools, and insights #86
- The weeklyfoo #86 newsletter features 35 valuable links in 6 categories, offering insights into various web development topics.
- Articles cover a range of subjects including JavaScript history, AI-driven app development, and practical advice for engineers.
- Tools section highlights MCP Directory, BrowserBee AI-powered assistant, and tools like Dither me this and PicoSSG.
- The newsletter also includes articles on procrastination in software engineers, AI techniques for engineering work, and Electron app performance.
- Featured tutorials cover topics like generating short alphanumeric IDs in Postgres, while videos introduce popular JavaScript frameworks.
- Readers can explore tools like prompt-kit for AI apps, jsPad JavaScript playground, and stagewise browser toolbar.
- The newsletter is a comprehensive resource for staying updated on web development trends and tools.
- Visit weeklyfoo.com to sign up for the newsletter and receive weekly web development insights in your inbox.
Read Full Article
4 Likes
Medium
297

Image Credit: Medium
How I Stopped Worrying About AI Replacing Developers — and Started Pair Programming With It
- A backend developer shares their journey of initially worrying about AI replacing developers but eventually embracing AI through pair programming.
- Despite being experienced in backend development, the developer felt a mix of amusement and unease when seeing ChatGPT write a Python function they had written many times before.
- The developer realized that AI not only saved time but also conserved energy, allowing them to focus more on architecture, performance, and creative problem-solving.
- By leveraging AI, the developer emphasized the importance of context and knowing what not to copy-paste, leading to a realization that AI can enhance their work rather than replace it.
Read Full Article
17 Likes
Medium
355
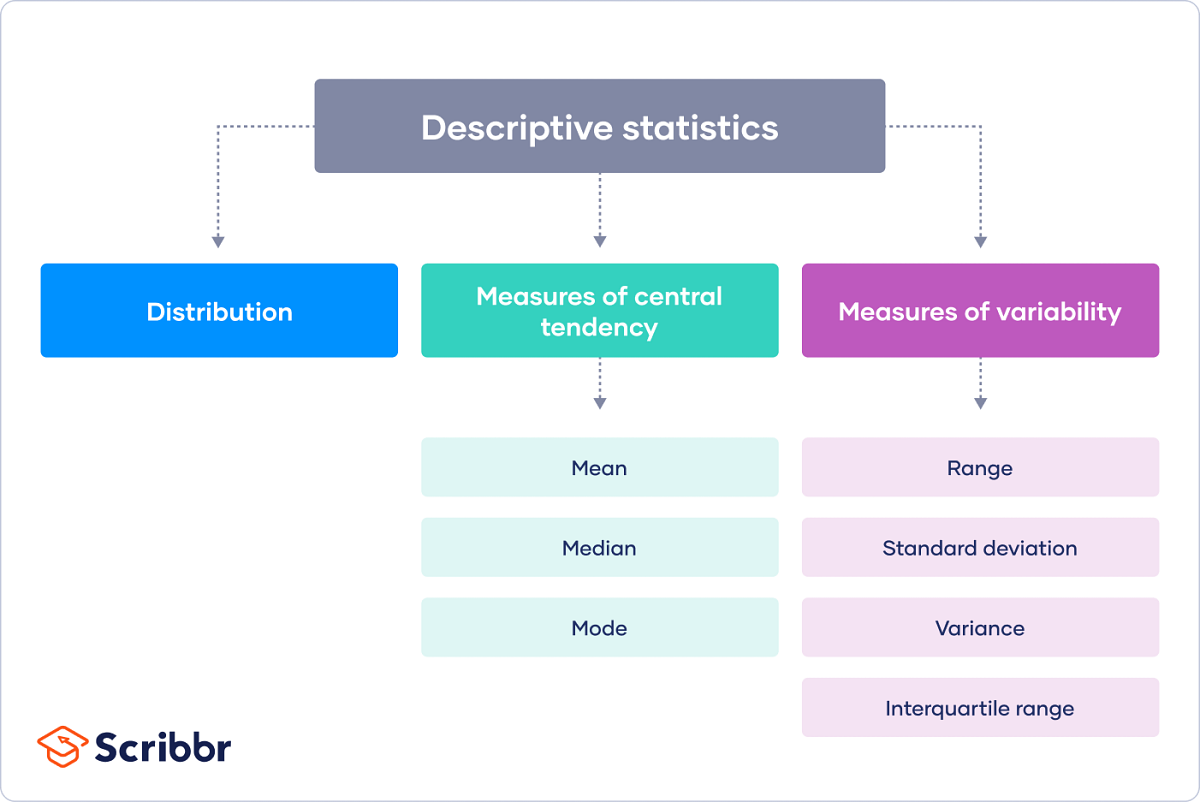
Image Credit: Medium
Descriptive Statistics : Heart of Statistics . (Part 2 )
- Descriptive statistics can be broken down into three main components: center, spread, and shape.
- Center metrics include mean (average), median (middle value), and mode (most frequent value).
- Spread metrics include range (difference between highest and lowest values), variance, standard deviation, and IQR (interquartile range).
- Shape metrics include skewness (asymmetry of data), kurtosis (tailedness of data), Z-score, and Percentile.
Read Full Article
21 Likes
For uninterrupted reading, download the app