Programming News
Dev
157

Image Credit: Dev
Building a Tab Component with Tailwind CSS and React
- Tabs are a common UI pattern for switching between different views or content areas.
- Benefits of using tabs include organizing related content, enhancing usability, and avoiding unnecessary page reloads or routing.
- Components for building a tab component using React and Tailwind CSS include Tabs, TabList, Tab, TabPanels, and TabPanel.
- Tabs.js file contains the functional components for managing tabs and their corresponding functionalities.
- Example usage demonstrates how to implement tabs in an application with different sections like Overview, Pricing, and Reviews.
- Tailwind CSS styling tips include using specific utilities for animations and transitions to enhance the tab component's visual appeal.
- Enhancements like adding keyboard support, animating tab panel content, lazy-loading content, and syncing tab state with URLs can further improve the tab component.
- Building tab components with Tailwind CSS and React Context ensures modular, styled, and scalable code.
- Reference provided for mastering Tailwind at scale to enhance the architecture, patterns, and performance of the tab component.
- The approach suggested keeps UI logic clean, makes tabs accessible, and provides users with a seamless navigation experience.
Read Full Article
9 Likes
Medium
360

Image Credit: Medium
Copilots, Not Autopilots: Inside Microsoft’s Human-in-the-Loop AI Strategy
- Microsoft adopts a 'human-in-the-loop' approach to AI development and use, emphasizing people as central to the process.
- The company focuses on 'AI-enabled' tools rather than 'AI-powered' systems, framing AI as assisting rather than replacing humans.
- This philosophy permeates Microsoft's strategy from the boardroom to product branding and policy discussions.
- Microsoft's Vice Chair and President, Brad Smith, highlighted the empowering potential of AI in a recent U.S. Congress testimony.
- The company considers AI a tool to enhance human capabilities rather than a standalone force.
- The human-in-the-loop ethos guides Microsoft's approach to AI development and implementation.
Read Full Article
19 Likes
Medium
276
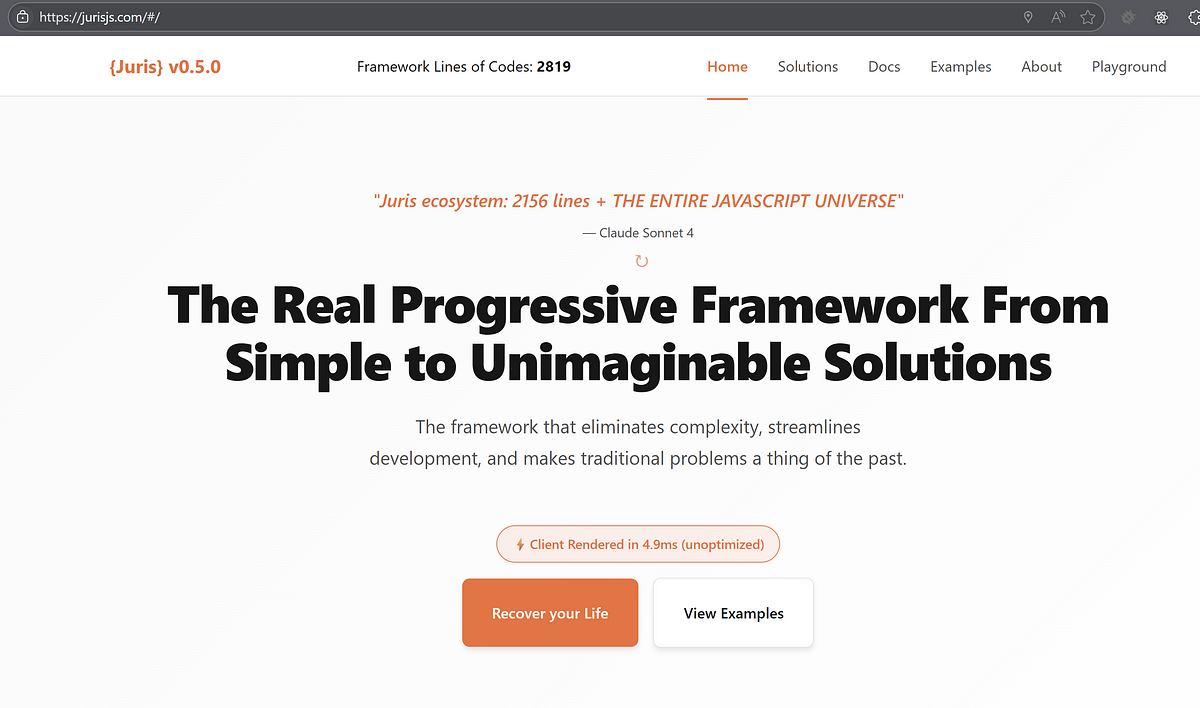
Image Credit: Medium
Juris.JS: The Documentation Site That Breaks Every Rule (And Every Performance Record)
- Juris.JS is a documentation site that challenges traditional web development rules and excels in performance.
- It operates without JSX, compilation, or transpilation, using pure JavaScript objects for UI structure and native browser performance.
- The site emphasizes reactive functions and static values, avoiding manual subscriptions, effect dependencies, and stale closures.
- It ensures fine-grained updates to DOM properties when state changes, without the overhead of a virtual DOM.
- Components in Juris.JS only track relevant state paths that execute, leading to efficient updates.
- The documentation runs real code examples, showcasing immediate component functionality and update capabilities.
- Juris.JS supports component-based development and progressive enhancement, making legacy code reactive without rewrites.
- The documentation site implements concepts like routing, state persistence, mobile navigation, and performance tracking in a real application for inspection.
- It highlights separating business logic from presentation and promotes a composition pattern for flexible UI structures.
- By questioning traditional web development assumptions, Juris.JS demonstrates a future where complexity is eliminated, not managed.
Read Full Article
16 Likes
Medium
68

"Nobody Cares. Work Harder."
- Life rewards outcomes, not just efforts. Build so strong that they can't ignore you.
- Talent is overrated; obsession and relentlessness are key to success.
- Discipline means working regardless of how you feel. High performers push through regardless of their emotions.
- Your story is significant only when you turn it into something real. Transform your struggles into fuel for success.
- There's no savior; success requires your focus, consistency, and mindset.
- Tips for getting ahead: Build without seeking approval, be consistently dedicated, eliminate soft habits, and nurture your mental strength.
- Ultimately, work harder as nobody cares about excuses. Success comes from being serious, focused, and dedicated.
Read Full Article
4 Likes
Discover more
- Software News
- Web Design
- Devops News
- Open Source News
- Databases
- Cloud News
- Product Management News
- Operating Systems News
- Agile Methodology News
- Computer Engineering
- Startup News
- Cryptocurrency News
- Technology News
- Blockchain News
- Data Science News
- AR News
- Apple News
- Cyber Security News
- Leadership News
- Gaming News
- Automobiles News
Medium
213
Image Credit: Medium
Why Java Continues to Be a Top Programming Language in 2025
- Java remains a cornerstone of software development in 2025, evolving to stay relevant.
- New Java versions introduce features enhancing productivity and application performance.
- Recent versions like Java 21 and 23 added virtual threads, simplified main classes, and more.
- Java is ideal for scalable applications across industries, especially in finance and healthcare.
- Learning Java first facilitates transitioning to other modern JVM languages like Kotlin.
- Java skills are in demand for professionals at all experience levels.
- Java's community support aids learning and career growth for developers.
- Java's age-resistant value and long-term relevance make it a strong career foundation.
- Consistent practice and building real-world projects are crucial for Java developers.
- A program offers a job-focused path with mentorship and real projects for aspiring Java developers.
- Strong fundamentals like Java create lasting careers amidst changing tech trends.
Read Full Article
12 Likes
Javacodegeeks
421

Image Credit: Javacodegeeks
Gatling vs JMeter: Choosing the Right Performance Testing Tool
- Performance testing tools Gatling and JMeter are compared for choosing the right tool based on specific needs.
- Key factors compared include architecture, resource usage, maximum users, and reporting capabilities.
- Gatling is known for high-scale testing, developer-friendliness, CI/CD integration, and better reporting.
- JMeter is recommended for GUI-based testing, broad protocol support, legacy systems, and extensive plugin ecosystem.
- Real-world usage examples of load testing and API performance testing are provided for both tools.
- Gatling excels in running on a single machine, using less memory, and generating reports automatically.
- Conclusion suggests using both tools for different purposes in an organization based on specific requirements.
- Consider JMeter for general-purpose testing and Gatling for high-performance web application testing.
- Both tools offer robust performance testing capabilities at lower costs compared to commercial tools.
- The final recommendation is to leverage the strengths of each tool in different testing scenarios.
Read Full Article
25 Likes
VC Cafe
242

Image Credit: VC Cafe
Vibe Coding: Fast, Powerful — But Not Flawless
- Israeli startup Base44, founded by 31-year-old Maor Shlomo, was acquired by Wix for $80M six months after launch.
- Base44, Shlomo's second startup, had over 250,000 users, was profitable ($189K profit in May), and focused on 'vibe coding' for software development.
- Vibe coding, popularized by Andrej Karpathy, enables developers to describe outcomes in plain English for AI to generate code faster.
- Vibe coding is ideal for rapid prototyping but doesn't replace entire software teams.
- Opportunities for startups in vibe coding include empowering faster innovation, reducing costs, and creating accessible coding tools.
- Challenges include the need for clear prompts, human oversight for code validation, and maintaining complex project context.
- Experts warn about the unpredictability of AI-generated code, scalability issues, cost limitations, and challenges in compliance and documentation.
- Despite challenges, AI-driven tools are set to transform software development, abstracting lower-level tasks for developers to focus on higher-level design and architecture.
- Vibe coding tools and IDEs are advancing, but practicality, compliance, and scalability remain key concerns in the evolving landscape of automated coding.
- Vibe coding signifies a shift in software development automation, paving the way for AI workflows across various aspects of development tools and practices.
- While AI automation in software development poses challenges, it also promises to revolutionize coding processes and job roles within the industry.
Read Full Article
14 Likes
Medium
8

Image Credit: Medium
Understanding .d.ts in TypeScript: The Secret Ingredient for Typing JavaScript Like a Pro
- TypeScript relies on .d.ts files for typing JavaScript projects effectively.
- .d.ts files act as guides for TypeScript in understanding the structure and types of JavaScript code.
- Mastering .d.ts files is essential for integrating JavaScript libraries into TypeScript projects.
- Using .d.ts files ensures type safety and helps in maintaining a scalable and error-free codebase.
- .d.ts files provide TypeScript with the ability to type-check JavaScript code and enhance development workflows.
- They are particularly valuable when working with untyped JavaScript libraries or legacy code.
- Declaring variables, interfaces, and modules in .d.ts files helps in providing type information to TypeScript.
- .d.ts files offer flexibility in modeling complex data structures and API contracts, improving code consistency.
- Proper placement and documentation of .d.ts files are crucial for effective usage and maintainability.
- Learning to write and use .d.ts files is akin to learning a new language's syntax and grammar.
Read Full Article
Like
Medium
272
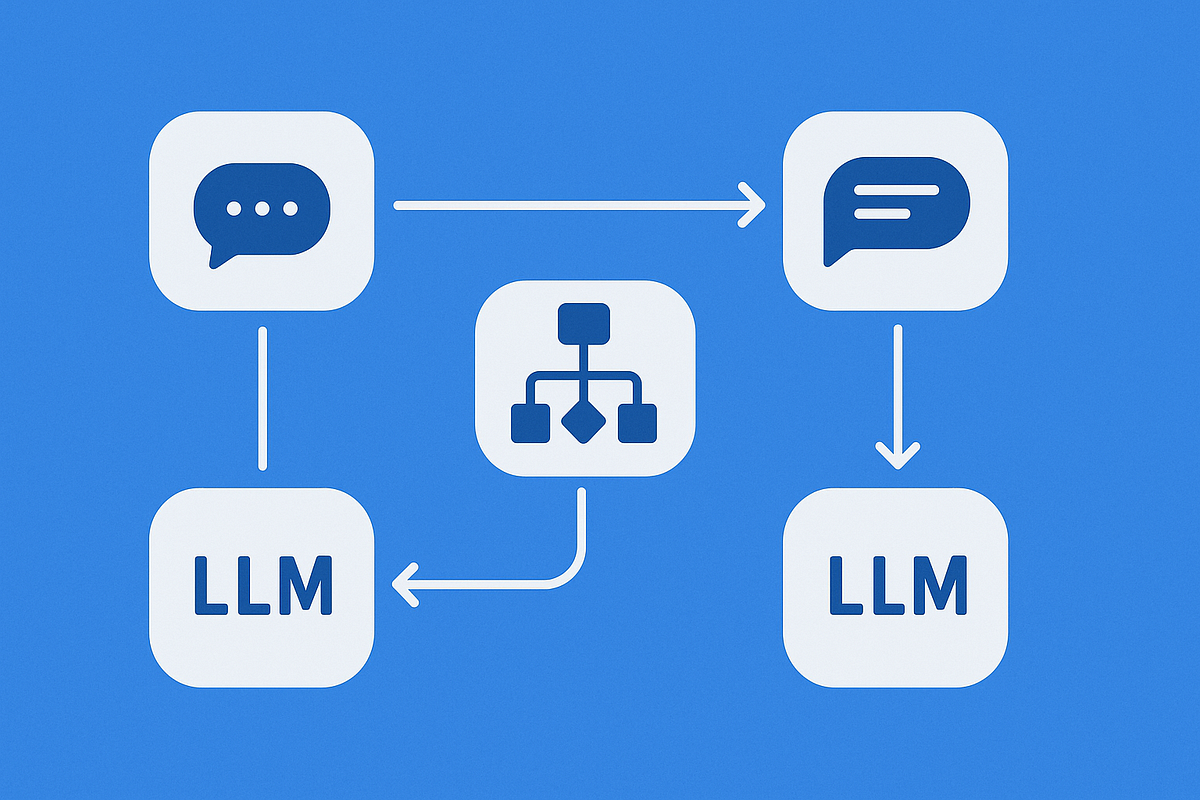
Image Credit: Medium
How to Visually Debug Multi AI-Agent Flows
- The dynamic nature of AI-agent systems makes it challenging to track and debug complex logic and interactions as the system scales.
- AgentGraph is introduced as an open-source library that integrates with Python or Node.js backends to capture and visualize AI agent interactions and tool calls in real-time.
- AgentGraph presents a visual interactive graph that provides clear visibility into system behavior, helping users understand complex flows.
- The visualization provided by AgentGraph helps in understanding interactions, tool calls, and nested agent flows in a multi-agent system.
- Implementing AgentGraph involves using unique session IDs for tracking conversation flow and defining tools using OpenAI's function calling format within LLM calls.
- AgentGraph's callLLMWithToolHandling function wraps LLM calls, allowing for seamless tracking and visualization of tool interactions.
- The tool implementations in AgentGraph receive specific parameters and offer insights into tool inputs, outputs, and chat histories.
- AgentGraph handles interactions involving LLMs and non-LLM tools, providing comprehensive visibility into the entire conversation flow.
- The integration of AgentGraph with AI agent systems offers real-time visualization, aiding in understanding, debugging, and optimizing AI workflows.
- AgentGraph simplifies the visualization of multi-agent interactions, making decision flows transparent and aiding in debugging complex AI systems.
- Key benefits of using AgentGraph include enhancing observability and transparency in AI workflow development, from simple tool-calling agents to elaborate multi-agent orchestration systems.
- The AgentGraph repository is available for exploration and support, aiming to make AI development more transparent and accessible.
Read Full Article
16 Likes
Medium
230
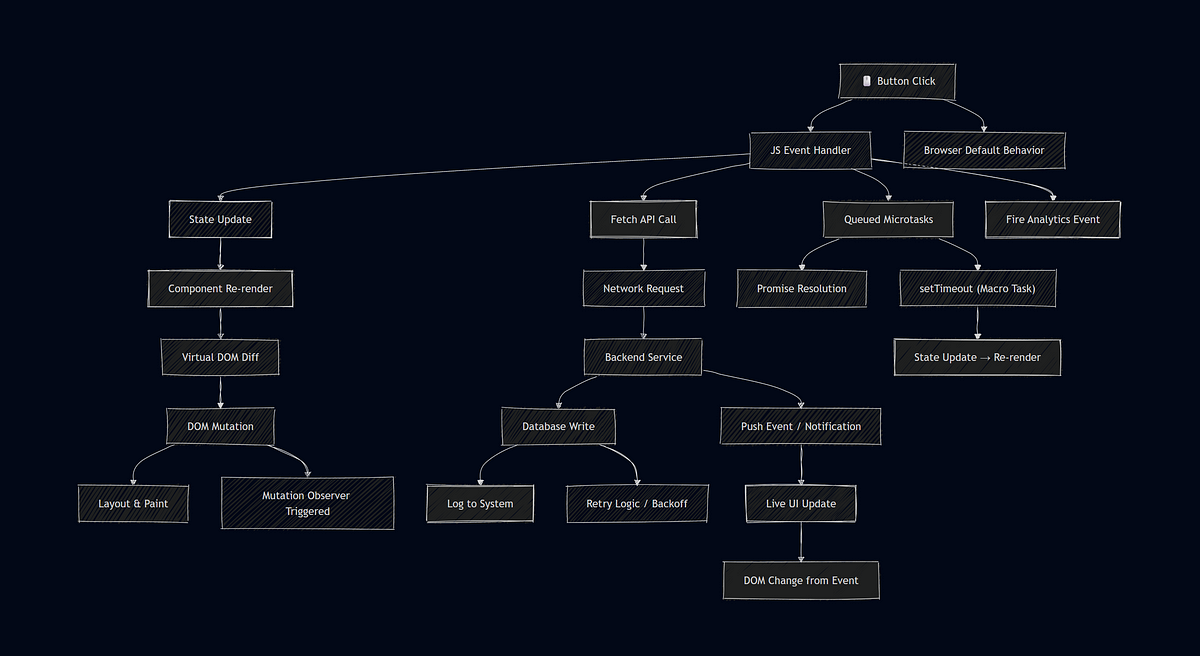
Image Credit: Medium
The Stack Trace of a Button Click
- A button click triggers a complex sequence of events including synchronous processes, DOM changes, and state updates.
- Each click initiates a series of actions across various layers such as the browser UI thread, render pipeline, JavaScript microtasks, backend queues, and database transactions.
- The button click event fires synchronously on the main thread, executing any attached listeners which can impact the main thread.
- Frameworks like React or Vue respond to state changes by triggering a render cycle and potentially using requestAnimationFrame.
- The intricate process also involves mutation observers and asynchronous tasks that react to the initial button click.
- The seemingly simple action of clicking a button sets off a cascade of operations that occur concurrently within a web application.
- The complexity arises from the interactions of different technologies and interfaces responding to user input.
- The entire process unfolds like a multi-threaded opera with various systems collaborating to execute the intended action.
- Despite the seamless experience for the user, the underlying mechanisms involve a chain reaction of handlers, timers, reflows, and rerenders.
- The coexistence of these processes demonstrates the intricate workings that support the functionalities of web applications.
- The cascade of events triggered by a button click showcases the behind-the-scenes operations necessary for user interaction.
- The interplay of components and technologies highlights the intricate dance of web development concealed from the user's perspective.
Read Full Article
13 Likes
Medium
204
Image Credit: Medium
Will AI Replace Junior Developers? I Asked Experts at Pycon US
- At PyCon US, the writer focused on networking and speaking to various Python community members.
- Most experts interviewed didn't believe AI would replace developers due to focusing on core programming problems where AI is less helpful.
- One expert mentioned that AI is similar to the new Stack Overflow and can assist with repetitive tasks and boilerplate code.
- An expert advised against blindly relying on AI without understanding the code it generates.
- Another expert emphasized that companies shouldn't replace junior developers as they are crucial for future development.
- There were mixed opinions on AI's role in coding, with some stating it will change how developers work, while others highlighted its efficiency in streamlining tasks.
- Many Python experts use AI tools like Copilot for everyday tasks, but some find AI unsuitable for their complex coding needs.
- Overall, it was agreed that AI won't replace developers soon, but will impact how coding is done.
- The writer also met Paul Everitt at the conference, who shared insights and a Python documentary trailer.
Read Full Article
12 Likes
Dev
413

Image Credit: Dev
Best 15 Svelte UI Components & Libraries for Enterprise-Grade Apps
- Svelte framework is known for its lightweight nature, elegant syntax, and reactivity.
- It is now increasingly used for building enterprise-grade apps with the help of advanced UI components.
- SVAR offers a suite of Svelte UI components such as DataGrid, Gantt chart, File Manager, and more.
- Tzezar provides a lightweight data table with sorting, filtering, and grouping support.
- TanStack Table is a framework-agnostic library for creating data tables with TypeScript support.
- EventCalendar, inspired by FullCalendar, offers a pure-Svelte calendar with multiple views and easy theming.
- FullCalendar, wrapped for Svelte, provides a feature-rich calendar/scheduler with drag-and-drop support.
- svelte-gantt is a high-performance Gantt chart component with customization options.
- Various UI libraries like Skeleton, shadcn-svelte, Bits UI, and Flowbite Svelte enhance Svelte app development.
- For data visualization in dashboards, options like LayerChart and Chart.js integration are available.
- Form and validation tools like Superforms and Felte simplify form handling in Svelte applications.
Read Full Article
24 Likes
Dev
21

Image Credit: Dev
Day 28/30 - Git Archive – Export Repo Files Without .git Directory
- Git archive command allows exporting repository files without the .git directory, useful for deployments, sharing code, and backups.
- Basic syntax of git archive: git archive --format=
--output= - Examples include exporting latest commit or specific branch as ZIP or tar.gz files.
- Common use cases: deploying code, sharing code without Git history, creating releases, backing up specific versions.
- Tips: List available formats, include untracked files, combine with git diff for partial exports, automate with Git Hooks.
- Git archive streamlines workflows and ensures clean, version-controlled exports.
- Mastering git archive options can help in efficient snapshot creation.
- Further resources: Git Documentation on git archive, Git Tips and Tricks
- Git archive is recommended for generating compressed snapshots of repositories.
- Git archive facilitates creating clean copies for sharing code.
- Web story eligibility: true
Read Full Article
1 Like
Medium
400

Image Credit: Medium
How I found my path in GIS: A Journey Through Geography, Tech, and Purpose”
- The individual initially felt disappointed with Geography but fell in love with it as they progressed.
- The discovery of Geographic Information Systems (GIS) combining tech and geography sparked a passion for utilizing data and digital maps for real-world impact.
- This led them to pursue an M.Sc in GIS for developing practical skills in spatial data analysis, cartography, and geospatial programming.
- They are learning tools like Python, SQL, Tableau, and Excel to complement their GIS skills.
- The individual is dedicated to continuous learning through online courses, volunteering, hands-on practice, and personal projects.
- Goals include further deepening GIS skills and utilizing tech to solve real-world problems.
- Encourages others exploring tech paths to stay open to unexpected opportunities.
- Open invitation to connect with the individual on LinkedIn for networking and growth opportunities.
Read Full Article
24 Likes
Logrocket
217

Image Credit: Logrocket
Frontend devs: Here’s how to get the most out of Cursor
- Cursor is a code editing tool that enhances coding experience by utilizing AI models like Claude AI, o3, Gemini-2.5-Pro, and GPT-4.1.
- According to the State of AI Web Dev survey, Cursor has high user awareness in the IDE space.
- The article reveals the features and workflows of Cursor AI that improve daily coding experiences.
- From utilizing Agent Mode and context integration to AI model selection and chat interface, Cursor aids in seamless coding tasks.
- The article provides insights into starting projects, generating interfaces, building sample projects, and iterating designs using Cursor AI.
- It mentions the Model Context Protocol (MCP) server for secure connections between data sources and AI tools.
- Strategies like AI Agent mode, context management with @ symbols, and creating new chats enhance coding productivity with Cursor.
- Custom rules, advanced autocomplete, and maintaining proper workflows contribute to maximizing productivity with Cursor AI.
- The article also discusses cheaper alternatives like Windsurf and GitHub Copilot for those seeking budget-friendly options.
- In conclusion, understanding and embracing AI-assisted coding environments like Cursor can significantly impact development workflows.
Read Full Article
13 Likes
For uninterrupted reading, download the app