Programming News
Medium
389

Earn More with Roam App: Simple Ways to Maximize Your Roam Points
- Roam's core feature, the Roam Miner, allows users to passively earn Roam Points by running the app and scanning WiFi signals.
- Adding new WiFi networks through the app can increase earnings and contribute to improving location services for everyone.
- Consistent daily check-ins on the Roam App can earn users extra Roam Points with just one tap.
- Roam offers a referral program where users can earn bonus points for successful referrals, helping the network grow and getting rewarded.
- Participants in Roam's community events, challenges, and campaigns can earn extra Roam Points and token rewards.
- Joining the Roam community allows users to engage in events, meet fellow users, and boost their earnings.
- Roam App provides an opportunity to earn crypto rewards by mining, connecting WiFi, referring friends, and participating in community events.
Read Full Article
23 Likes
Javacodegeeks
98

Image Credit: Javacodegeeks
How to Replace a Specific Word in a File Using Java
- The article discusses various methods to replace a specific word in a text file using Java.
- The first method involves java.nio.file.Files for reading and writing files, replacing the target word and updating the file using Streams.
- The second method uses classic java.io classes BufferedReader and BufferedWriter for memory efficiency, replacing the word and updating the file securely.
- The third method showcases the use of Apache Commons IO for simplified file reading and writing with utility methods.
- Each method demonstrates how to replace occurrences of a word in a file with another specified word.
- The article provides code snippets and explanations for implementing each method.
- The Java program using java.nio.file.Files reads all lines of the file, replaces the target word, and writes the updated content back to the file.
- The Java program using BufferedReader and BufferedWriter processes the file line by line, replaces the word, and updates the file securely.
- The Java program using Apache Commons IO simplifies file reading and writing, making word replacement more concise.
- The article concludes by summarizing the different approaches discussed in the text.
Read Full Article
5 Likes
Nordicapis
12

APIs and Identity in the Age of the Sovereign Cloud
- Peter Steiner’s 1993 cartoon in The New Yorker humorously depicted online anonymity with the famous phrase 'On the Internet, nobody knows you're a dog.' The rise of the sovereign cloud movement, emphasizing control and compliance, is impacting identity management in the digital space.
- The sovereign cloud movement, gaining traction in the EU, focuses on ensuring proper authorization amid new legislation and federated login systems, sparking significant changes in authentication standards and API access with regional restrictions.
- European lawmakers aim to reduce reliance on foreign-owned digital services, favoring 'sovereign digital infrastructure' to enhance economic independence and security, reflecting global concerns around data jurisdiction and control.
- Sovereign clouds, tailored for specific regulatory environments like the EU's GDPR, require compliance with data processing laws of their respective regions, leading major providers like Amazon and Google to engage in such initiatives.
- In the context of digital sovereignty, ensuring cross-border compliance for API data transfers between jurisdictions becomes crucial, with GDPR-inspired practices such as access controls and encryption playing a key role in meeting regulatory standards.
- The emergence of regional identity providers like itsme and SwissID challenges existing authentication protocols, potentially necessitating a shift towards decentralized identity standards to address interoperability and compliance hurdles.
- The shift towards enhanced identity verification, potentially via self-sovereign identity and verifiable credentials, may lead to greater data security but also raise concerns about privacy and anonymity, as seen in recent legal and ethical debates.
- While sovereign cloud initiatives aim to improve security and control over data access, the trade-off with online anonymity is evident, prompting discussions on how to balance identity verification without compromising individual privacy.
- The move towards stricter data controls and regional identity verification may offer opportunities to innovate in secure authentication methods, leveraging technology like zero trust architecture and decentralized identifiers via APIs.
- In this evolving landscape of digital sovereignty and identity management, APIs could serve as a vital tool in maintaining online security and privacy while adapting to changing regulatory landscapes and technological advancements.
- The article delves into the implications of the sovereign cloud movement on digital identity, highlighting the tension between enforcing compliance and protecting user privacy in an increasingly regulated and interconnected online environment.
Read Full Article
Like
Dev
17

Image Credit: Dev
Setting up a Python project with CMake
- CMake can be used to set up and run Python applications in mixed-language projects.
- The unique approach allows for running any application with a single command.
- Project structure includes separate directories for each application, each with its own CMakeLists.txt file.
- CMakeLists.txt file includes functions to create Python virtual environments and install dependencies from requirements.txt.
- Individual app directories contain CMakeLists.txt files to setup virtual environments and run applications.
- Running 'cmake .' in the build folder initiates the setup of virtual environments and downloads dependencies.
- Build all targets using 'cmake --build .' command.
- Applications can be run using 'make run_app1', 'make run_app2', and 'make run_app3' commands.
- Targets can also be executed in VS Code using the CMake GUI interface.
- Ninja can be used as an alternative to 'make' for generating configuration.
- Generate Ninja configuration with 'cmake .. -G Ninja' and build with 'cmake --build .'.
- Run applications using 'ninja run_app1', 'ninja run_app2', and 'ninja run_app3' commands.
Read Full Article
1 Like
Discover more
- Software News
- Web Design
- Devops News
- Open Source News
- Databases
- Cloud News
- Product Management News
- Operating Systems News
- Agile Methodology News
- Computer Engineering
- Startup News
- Cryptocurrency News
- Technology News
- Blockchain News
- Data Science News
- AR News
- Apple News
- Cyber Security News
- Leadership News
- Gaming News
- Automobiles News
Dev
299

Image Credit: Dev
Reusable React Components: Easier Said Than Done
- Creating reusable React components can be tricky, as many components break under slight changes if not designed to scale.
- A better approach involves making components configurable with props, interactive with state, and communicative through custom events.
- Define the structure using props to allow adaptability to different use cases like a welcome banner or error message.
- Add interaction by using state to control internal visibility, like displaying a close button if needed.
- Enable communication by including custom events like onClose prop to notify the parent when the component is dismissed.
- The key to scalable components involves customizing with props, behavior with state, and communication with events.
- Using TypeScript with React enhances component development by providing strict typing to prevent runtime bugs and ensure clarity.
- Resource: React Documentation – useState, Learn React with TypeScript on Amazon.
Read Full Article
18 Likes
Javacodegeeks
398

Image Credit: Javacodegeeks
Low-Latency Edge Networks with 5G: Leveraging 5G for Real-Time Edge Computing
- 5G networks are enhancing edge computing by providing ultra-low latency and high throughput, enabling new classes of real-time applications.
- Edge computing reduces latency by processing data closer to the source, and 5G networks with <1ms latency, high throughput, and network slicing complement this approach.
- Real-time use cases of 5G and edge computing include autonomous vehicles, AR/VR, smart manufacturing, remote healthcare, and smart cities, leveraging sub-millisecond latency for various applications.
- The architecture of a 5G edge network involves IoT devices/sensors, 5G RAN, MEC, and optionally, cloud/data centers to support real-time processing.
- Challenges in 5G edge networks include limited edge node resources, increased security risks, and managing distributed infrastructure complexity.
- Developer tools and ecosystem contributions from companies like AWS, Google, NVIDIA, and Intel facilitate application deployment and orchestration at the 5G edge.
- 5G and edge computing combined offer low-latency networks for autonomous driving, AR/VR experiences, smart factories, emphasizing rapid data processing and decision-making.
Read Full Article
23 Likes
Dev
136

Image Credit: Dev
Day 27/30 - Git Grep: How to Search for Text Across Commits and Branches
- Git grep is a powerful tool for searching text patterns within Git repositories.
- It can search through different versions of files, branches, and commit histories efficiently.
- The basic syntax for git grep includes the pattern, optional commit hash/branch/tag, and optional file path.
- Examples of using git grep include searching in the working directory, specific branches, all branches, case-insensitive search, and more.
- Common use cases for git grep involve finding TODOs, debugging errors, refactoring code, searching deleted code, and locating configuration values.
- Tips and tricks for git grep include excluding files, searching only in certain file types, counting matches, showing context around matches, and searching in staged changes.
- git grep is essential for tasks like debugging, refactoring, and exploring code efficiently.
Read Full Article
8 Likes
Dev
226

Image Credit: Dev
Mastering Event Propagation in JavaScript: Bubbling vs Capturing
- Event propagation in JavaScript involves the order in which event handlers are invoked in the DOM.
- There are two phases of event propagation: Bubbling and Capturing.
- Event Bubbling is the default phase where the event moves from the target element to its ancestors.
- Event Capturing starts at the topmost ancestor and moves down to the target element.
- Example code shows event propagation using capturing and bubbling phases.
- Parent and child event handlers using capturing execute before the one using the bubbling phase.
- Bubbling is useful for parent components reacting to child actions or event delegation.
- Capturing is suitable for intercepting events early or preventing default actions.
- You can control event flow using event.stopPropagation() and event.stopImmediatePropagation().
- Understanding event propagation is essential for building efficient JavaScript applications.
- Mastering bubbling and capturing helps in debugging and designing reusable components.
Read Full Article
13 Likes
Medium
316
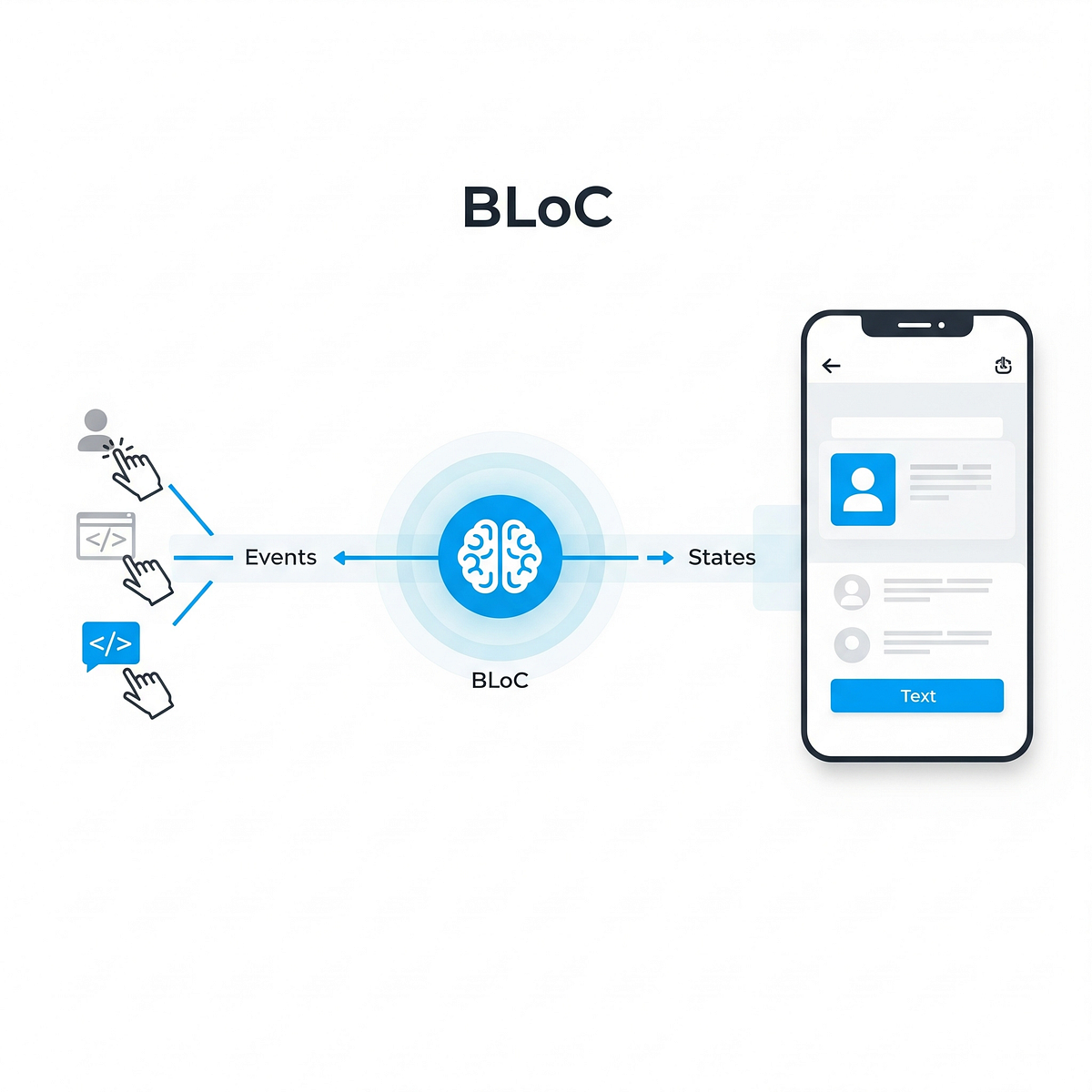
Image Credit: Medium
Understanding State Management in Flutter: An Analogy for Writers and Programmers
- State management in Flutter can be compared to writing a novel, where the state of the manuscript represents the current condition of the writing process.
- BLoC acts as the bridge between actions (events) and the manuscript's condition (state), making decisions on how the manuscript should evolve.
- The analogy extends to a barista in a coffee shop, illustrating the separation of requests (events), processes (BLoC), and outputs (states) for organized workflow.
- By applying this concept to a Flutter application for jotting down writing ideas, users can interact with events like adding new ideas and viewing loading indicators.
- The states in such an application could include initial loading, loaded with ideas, idea saving in progress, and error states.
- The BLoC takes events and translates them into corresponding states to manage application behavior.
- On the UI side, BlocBuilder is used to update the view based on changes in state from IdeaBloc, maintaining a reactive UI.
- Structuring code with the BLoC pattern offers clarity and organization similar to structuring a story for writers, enhancing application functionality and elegance.
- Despite an initial learning curve, the BLoC pattern proves beneficial for complex applications requiring long-term development, similar to outlining a novel before writing.
- In conclusion, understanding and implementing state management with BLoC can lead to cleaner, scalable, and testable applications for writers and programmers alike.
Read Full Article
19 Likes
Dev
175

Image Credit: Dev
10+ Best Next.js eCommerce Templates for 2025
- Creating an eCommerce online store from scratch can be challenging, but using Next.js eCommerce templates can simplify the process.
- These templates offer modern designs, advanced UI elements, and powerful features for building functional online stores with simple and scalable codebases.
- 10+ best Next.js eCommerce templates are highlighted in the post, each with unique features and designs to aid in creating impressive online stores.
- Key reasons to choose a complete Next.js eCommerce template include fast loading times, readiness for growth, modern tech stacks, mobile-friendly designs, and developer-friendly setups.
- The templates mentioned in the post leverage advanced technologies like Next.js, React, TypeScript, Tailwind CSS, Stripe, and more to streamline the eCommerce development process.
- Examples of the featured templates include NextMerce, CozyCommerce, Bazaar Pro, Medusa + Next.js, Next Shopify Starter, Hot-Kicks, Clare, Boundless Commerce, Singitronic, Shopware Frontend, Dstoneva E-commerce, and Tech Bazar.
- These templates cater to various needs, such as polished storefront layouts, integrated CMS capabilities, headless eCommerce setups, tech store optimizations, and more.
- Each template offers different tech stacks and functionalities tailored to launch online stores efficiently and effectively.
- Next.js simplifies the process of developing fast and scalable eCommerce sites, and the templates mentioned provide a solid foundation for building successful online stores.
- Customizing these templates to fit a specific brand and launching an online store with confidence is encouraged by trying out the highlighted Next.js eCommerce templates.
Read Full Article
10 Likes
Dev
342

Image Credit: Dev
Day 9: Supercharge FastAPI with Async Programming
- Day 9 of the FastAPI Zero to Hero series explores Async Programming, a powerful tool in web development.
- Async programming allows programs to continue working on other tasks while waiting for slow operations.
- In FastAPI, using async functions enables managing numerous requests concurrently and optimizing server resources.
- A comparison between synchronous and asynchronous code in FastAPI highlights the efficiency and scalability of async programming.
- Async programming is beneficial for interacting with external services, improving response times, and scalability.
- By simulating delayed external API calls, the article demonstrates how async programming in FastAPI can significantly enhance performance.
- Async programming in FastAPI is recommended for tasks like calling external APIs, fetching data with async drivers, and network I/O.
- The article concludes that async programming is a game-changer for creating scalable and responsive online APIs.
- Async programming can greatly enhance backend performance and user experience in various applications.
- The article is eligible for web story generation as it provides concise insights into utilizing Async Programming in FastAPI for improved performance.
Read Full Article
20 Likes
Logrocket
124

Image Credit: Logrocket
Leader Spotlight: Cascading down a product-led culture, with Mike Fantigrassi
- Mike Fantigrassi is the Head of Product at National Academy of Sports Medicine (NASM), leading the transition to a product-led growth model.
- NASM is part of Ascend Learning, focusing on fitness and wellness certifications, which recently shifted to a product-led approach.
- The transition was supported by leadership, implemented through cross-functional product delivery teams led by product managers.
- Challenges in delivering products were highlighted, including the importance of customer discovery and internal alignment.
- Change management aspects such as role clarity and communication were crucial during the transition.
- Prioritization and executing big initiatives were discussed, emphasizing the need for foundational processes to support higher-level initiatives.
- An early win in the transition was offering a payment option for a membership program, leading to increased subscriptions.
- Benefits of the product-led approach included improved output, revenue increase, and better understanding of the customer journey.
- Advice for other leaders looking to transition included company-wide training, leadership alignment, proactive communication, and fostering a culture of sharing and learning.
Read Full Article
7 Likes
Dev
17

Image Credit: Dev
How to Set Up GitHub Login in SafeLine
- SafeLine now supports GitHub authentication for users to securely log in using their GitHub identity.
- To set up GitHub OAuth application, users need to create a GitHub OAuth application on GitHub's official documentation and obtain ClientID and ClientSecret.
- Steps to configure the GitHub OAuth application include creating the app, setting the application name, homepage URL, and authorization callback URL.
- The Authorization callback URL is formed by appending /.safeline/auth/api/callback/github to the Homepage URL.
- In SafeLine, users should go to the Safeline Console, navigate to Auth -> Settings, and choose GitHub under Third-Party Login Configuration.
- Configuration fields in SafeLine include ClientID (GitHub application ID) and ClientSecret (GitHub application secret).
- After configuring, users should click the Submit button in SafeLine to complete the binding.
- Users can select the GitHub login method after enabling the AUTH feature for the application.
- New users will be prompted for authentication, and Safeline administrators must review and confirm in the console.
- Authorized users will not need extra reviews for subsequent access; they can log in successfully.
- Users who haven't passed the review will be blocked from accessing the application.
Read Full Article
1 Like
Dev
64

Image Credit: Dev
Building Robust API Rate Limiters: A Comprehensive Guide for Developers
- API rate limiting is crucial for controlling traffic to prevent performance issues, costs, and service outages.
- Rate limiting restricts the number of API calls per specified time period to maintain system stability.
- Benefits of implementing API rate limiting include preventing resource exhaustion, enhancing security, and cost control.
- Common rate limiting algorithms include Token Bucket, Leaky Bucket, Fixed Window Counter, and Sliding Window Log.
- Implementing rate limiting in Node.js, Python with Flask, and Java with Spring Boot is demonstrated.
- Best practices include communicating limits clearly, using proper response headers, and implementing graduated rate limiting.
- Standardized rate limiting headers and status codes facilitate effective API communication.
- Testing rate limiters with comprehensive tests ensures they function correctly under different scenarios.
- Advanced strategies like Dynamic Rate Limiting, Machine Learning-Based Rate Limiting, and Client-Side Rate Limiting provide more flexibility.
- API rate limiting is essential for protecting services, ensuring fair resource distribution, and maintaining high availability.
- Implementing robust and scalable APIs with effective rate limiting strategies is key to handling real-world traffic patterns.
Read Full Article
3 Likes
Dev
235

Image Credit: Dev
🛠️ End-to-End CI/CD with AWS — Test, Build & Deploy to S3
- The article provides a guide on setting up an end-to-end CI/CD process on AWS.
- The setup includes AWS CodePipeline, AWS CodeBuild, and S3 for hosting a static website.
- It features a separate unit testing stage before the build process.
- This project covers steps for running unit tests, building various types of web apps, and deploying to an S3 bucket.
- The automation is achieved using AWS CodePipeline.
- A dedicated CodeBuild project is used for running unit tests and ensuring code quality before proceeding to build and deploy stages.
- After successful testing, a second CodeBuild stage is triggered for the build and deployment to S3.
- The built files are uploaded to S3 for hosting static websites either through a public endpoint or CloudFront.
- The article also provides a link to the GitHub repository with step-by-step instructions.
- The setup is recommended for frontend developers, DevOps engineers, or anyone interested in AWS CodeBuild, CodePipeline, and S3.
- Key tools used include AWS CodePipeline, AWS CodeBuild, AWS S3, and GitHub for source control.
- Readers are encouraged to clone the repository, test the setup, and seek further assistance.
- The process emphasizes proper testing, automation, and eliminating manual deployment hassles.
- The end-to-end CI/CD process aims to streamline web application deployments effectively using AWS services.
Read Full Article
14 Likes
For uninterrupted reading, download the app