Cloud News
Tech Radar
332

Image Credit: Tech Radar
Some Meta Quest headsets are being bricked by a software update – but a fix is rolling out
- Some Meta Quest headsets, including Quest 2, 3, and 3S, are being bricked by a software update.
- Users have complained that applying updates leads to their headsets not starting.
- Meta has acknowledged the issue and is rolling out a fix.
- Affected users are advised to contact the support team for assistance.
Read Full Article
19 Likes
Dev
36

Image Credit: Dev
High Availability Database Architecture on AWS: A Deep Dive
- This post explores a highly available database architecture deployed on AWS, showcasing its components, deployment strategies, and best practices.
- The architecture consists of a multi-AZ design using Amazon RDS for PostgreSQL, with VPC, public and private subnets, RDS instances, EC2 instance, security groups, and NAT Gateway as key components.
- Deployment involves steps like VPC creation, subnet configuration, NAT Gateway deployment, RDS setup, EC2 instance launch, security group configuration, database replication, and testing and monitoring.
- Best practices include multi-AZ deployment, security group restrictions, regular backups, IAM roles, monitoring and alerting, automated scaling, and disaster recovery planning.
Read Full Article
2 Likes
Dev
31
Image Credit: Dev
Troubleshooting HTTP/3 QUIC Reverse Proxy for Chunked Uploads to S3 Pre-Signed URLs
- A developer is troubleshooting a QUIC-based reverse proxy for chunked uploads to S3 pre-signed URLs.
- The developer has set up a custom HTTP/3 QUIC server to receive PUT requests with chunked data and a custom header containing the S3 pre-signed URL.
- The server extracts the pre-signed URL and forwards the request body to the S3 URL using a reverse proxy mechanism.
- However, the proxy to S3 fails with a '502 Bad Gateway' error and a 'http3: parsing frame failed' error.
Read Full Article
1 Like
Medium
236

Image Credit: Medium
Notable State Laws Taking Effect in 2025
- California has enacted measures to regulate artificial intelligence, prohibiting AI systems from making certain decisions related to employment or housing.
- Delaware has strengthened reproductive rights by ensuring access to comprehensive healthcare services for women, including family planning and maternal health.
- Montana allows individuals to carry concealed firearms without permits, while Oregon has made it a misdemeanor crime to possess a firearm on public transit.
- Kentucky has established a framework for medical marijuana use, requiring patients to obtain written certification from a healthcare provider.
Read Full Article
14 Likes
Discover more
- Programming News
- Software News
- Web Design
- Devops News
- Open Source News
- Databases
- Product Management News
- Operating Systems News
- Agile Methodology News
- Computer Engineering
- Startup News
- Cryptocurrency News
- Technology News
- Blockchain News
- Data Science News
- AR News
- Apple News
- Cyber Security News
- Leadership News
- Gaming News
- Automobiles News
Dev
173

Image Credit: Dev
Wildcards in Federated Credentials Entra ID (OIDC)
- Microsoft Entra ID has started the public preview of the feature Federated Credentials.
- Federated Credentials allow the definition of trusted external security credentials.
- Entra ID supports secretless authentication via Federated Credentials.
- Wildcards can now be used to define matching expressions for authentication in Entra ID using Federated Credentials.
Read Full Article
10 Likes
Dev
409
Image Credit: Dev
Configuring AWS Vault with the Pass Backend for Secure Credential Management on Linux
- AWS Vault is a tool for securely storing and accessing AWS credentials.
- This guide explains how to configure AWS Vault with the pass backend on Linux.
- It covers steps like installing AWS CLI, installing AWS Vault, configuring the pass backend, and adding AWS credentials to AWS Vault.
- By following this guide, users can enhance the security of their AWS credential management on Linux.
Read Full Article
24 Likes
Dev
305

Image Credit: Dev
Configuring AWS Vault for Secure Credential Management on Linux
- AWS Vault is a tool that enhances credential security on Linux by securely storing and accessing AWS credentials.
- To configure AWS Vault, first install the AWS CLI and verify the installation.
- Then, install AWS Vault on Linux and configure it to use the file backend.
- Finally, add AWS credentials to AWS Vault and test the configuration using an AWS CLI command.
Read Full Article
18 Likes
Tech Radar
305
Image Credit: Tech Radar
Quordle today – my hints and answers for Sunday, December 29 (game #1070)
- Quordle today is the 1070th game of the word game.
- There are 4 different vowels in Quordle today.
- 2 of today's Quordle answers contain repeated letters.
- None of the letters Q, Z, X, or J appear in Quordle today.
- There are no Quordle answers starting with the same letter.
Read Full Article
18 Likes
Tech Radar
309
Image Credit: Tech Radar
NYT Strands today — my hints, answers and spangram for Sunday, December 29 (game #301)
- NYT Strands today (game #301) has a theme of Festival of Lights delights.
- The clue words for today's game are STOKE, DIAL, BROKEN, SLAG, CALL, and LADS.
- The spangram hint for today is 'Jewish feast'.
- The two sides of the board that the spangram touches are the left side of the 4th row and the bottom side of the 2nd column.
Read Full Article
18 Likes
Dev
141

Image Credit: Dev
Unveiling Amazon Nova Models: The Future of Generative AI 🚀
- Amazon has unveiled its Nova Models, a series of foundational models designed to power a wide range of generative AI tasks.
- The Nova Models include four cutting-edge models: Nova Micro, Nova Lite, Nova Pro, and the upcoming Nova Premier.
- Key features of the Nova Models include text summarization, translation, content classification, and multimodal capabilities.
- The Nova Models can be fine-tuned and customized to optimize speed, cost-efficiency, and accuracy for various applications.
Read Full Article
8 Likes
Dev
227
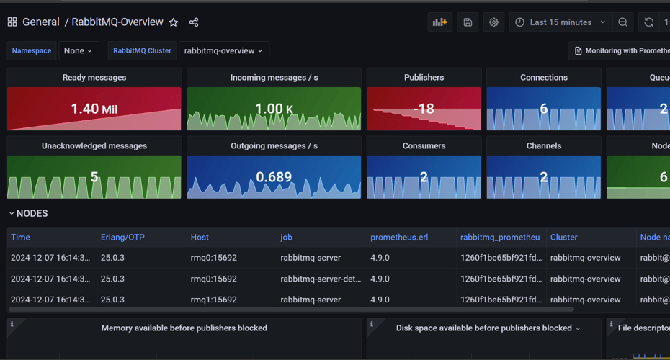
Image Credit: Dev
RabbitMQ Monitoring with Prometheus and Grafana
- This project focuses on RabbitMQ monitoring with Prometheus and Grafana.
- It includes a local Docker Compose setup for quick testing and a 3-node RabbitMQ cluster setup on AWS EC2 for scalability.
- The project covers the steps for setting up RabbitMQ locally using Docker Compose, configuring RabbitMQ on a 3-node cluster on AWS EC2, and monitoring RabbitMQ using Prometheus and Grafana.
- Additionally, Python scripts are used to test message queuing functionality.
Read Full Article
13 Likes
Medium
200

Image Credit: Medium
Securing Hybrid Cloud: Strategies for a Resilient IT Infrastructure
- Hybrid cloud environments have increased the attack surface and exposed organizations to a broader set of threats. Misconfigurations in cloud resources and shared responsibility models in cloud services create vulnerabilities.
- Visibility into a hybrid cloud environment can be a major challenge. Monitoring tools that cater to on-premises environments often lack the visibility required to monitor public cloud environments, and vice versa.
- Organizations operating in hybrid cloud environments must navigate a complex landscape of regulatory requirements, making compliance management essential.
- Identity and Access Management (IAM) is one of the most critical security challenges in hybrid cloud environments. IAM systems must include MFA, RBAC, and regular access audits to minimize the risk of data breaches.
- Unified security policies across both public and private components of the infrastructure are critical to reduce the chances of gaps in security.
- Enhanced visibility and monitoring are critical in detecting and responding to potential threats in hybrid cloud environments. Businesses can implement comprehensive monitoring platforms, SIEM systems and real-time analytics to identify patterns and anomalies that could signal a breach.
- Robust IAM solutions are vital for securing hybrid cloud infrastructures. Organizations should deploy IAM solutions that offer centralized management and integrate seamlessly across cloud and on-premises systems and audit access control policies regularly.
- The benefits of hybrid cloud architectures are undeniable, but so are the risks. By implementing effective strategies, such as unified security policies, enhanced visibility, and robust IAM solutions, organizations can create a resilient IT infrastructure.
- It is crucial that businesses stay proactive and adaptive to the evolving security landscape, ensuring that their hybrid cloud environments are both secure and compliant.
Read Full Article
12 Likes
Medium
63
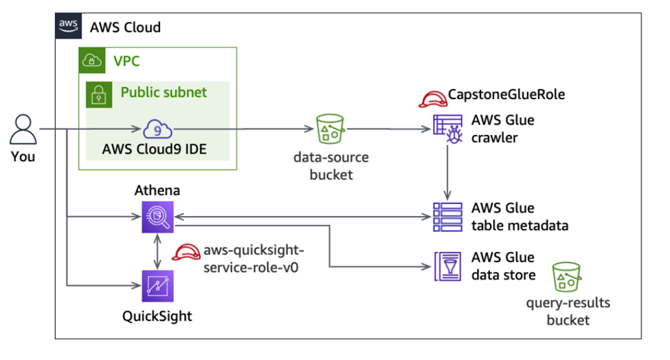
Image Credit: Medium
Building a Comprehensive Data Pipeline on AWS: From Raw Ingestion to Interactive Insights
- AWS services used: S3, AWS Cloud9, IAM, AWS Glue, Amazon Athena, Amazon QuickSight, S3 Select
- Tasks performed: Create S3 buckets, set up AWS Cloud9, download CSV source files, convert CSV to Parquet, configure Athena Query Editor, run queries in Athena
- Challenge query: Finding the Catch Value for Fiji
- Final steps: Add IAM permissions, build dataset in QuickSight, create visualizations, share dashboard
Read Full Article
3 Likes
Medium
446

Deploying a Django Application: A Step-by-Step Guide to AWS, Custom Domains, and HTTPS
- Setting up the hosting environment on an AWS EC2 instance.
- Configuring and deploying the Django application.
- Configuring Nginx as a reverse proxy.
- Linking the custom domain and enabling HTTPS with Let's Encrypt.
Read Full Article
26 Likes
Medium
209

Image Credit: Medium
Log Strata — Redefining Observability with Infra Monitor
- The Log Strata Infra Monitor Challenge by STGI empowers developers to embrace observability transformation by designing their own observability platform.
- Participants in the challenge can tackle real-world problems in a simulated environment, laying the foundation for impactful solutions in production-scale systems.
- The challenge enables developers to build an observability platform from scratch.
- Kubernetes, a powerful tool for orchestrating containers, enabled the developers to streamline the deployment and scaling of their system.
- The challenge required tackling the collection, storage, and analysis of logs in real-time to ensure quick identification and resolution of issues within the system.
- Developers gained valuable experience in building intuitive user interfaces for effective monitoring and visualization of logs, metrics and transaction tracing.
- Developers encountered and resolved complex challenges on the way, gaining essential problem-solving and prioritization skills.
- The hackathon provided an opportunity for developers to innovate and solve real-world problems with a complete observability platform.
- The challenge went beyond mastering tools and technologies, inspiring creativity and new approaches to contribute to the evolution of cloud systems.
- Developers are excited to continue building platforms that drive meaningful insights and transformation in the world of cloud monitoring.
Read Full Article
12 Likes
For uninterrupted reading, download the app