Cyber Security News
TechJuice
302

Image Credit: TechJuice
Hacked by Ads? WordPress Sites Spreading Malware to Millions!
- WordPress malware is becoming a significant threat as hackers use legitimate ad networks to distribute malicious payloads.
- Research uncovered coordination between hacked WordPress sites and ad networks like Los Pollos and RichAds.
- The malware delivery mechanism impacts regular browsing experiences.
- Infoblox identified the VexTrio traffic distribution system used to redirect visitors to malware download pages.
- Infected WordPress sites display fake captchas that lead to push notification subscriptions.
- Users are exposed to scam links and drive-by downloads through push notifications.
- Ad networks such as Partners House and BroPush are central to VexTrio's operations.
- These networks profit by promoting gift card scams, phishing sites, and malware installers.
- Over 40 percent of hacked WordPress sites redirect users to malicious destinations through these networks.
- Adtech companies' vetting processes may expose hackers to detection by authorities.
- Site owners are advised to check for suspicious plugins, DNS entries, and JavaScript.
- Visitors should avoid interacting with suspicious pop-ups and captcha prompts requesting notification access.
- Strengthened endpoint security and partnership between adtech firms and cybersecurity experts are recommended to combat WordPress malware.
- The post was published on TechJuice.
- The news article qualifies for web story generation due to its relevance and potential for user engagement.
Read Full Article
18 Likes
TechJuice
131

Image Credit: TechJuice
Crypto Wallets At Risk Following 16 Billion Passwords Leak Online
- A monumental data breach has occurred, with 16 billion passwords leaked online, many of which are fresh and not seen before.
- Credentials from major platforms like Apple, Facebook, Google, Gmail, Telegram, GitHub, and even government portals are affected.
- The leaked data was scraped by info-stealer malware and exposed through vulnerable Elasticsearch servers.
- Crypto holders are particularly at risk, as the breach includes wallet-linked emails, active session cookies, browser tokens, and 2FA bypass metadata.
- Attackers could exploit this data to drain hot wallets, exchange accounts, and DeFi platforms.
- Security analysts warn of potential crypto wallet theft through phishing attacks and session hijacking.
- Urgent actions advised by experts include password changes, revoking session access, using password managers, and adopting hardware-based 2FA solutions.
- Monitoring blockchain wallets for unauthorized access is recommended.
- Global regulators may focus on strengthening KYC systems, email-based recovery, and cybersecurity practices in crypto exchanges.
- Experts suggest decentralized identity (DID) solutions could become more popular for secure authentication tied to the blockchain.
- This breach underscores the seriousness of potential financial losses from drained wallets and stolen digital assets.
- The breach has repercussions for regulation and accountability in the crypto wallet space.
- Lawmakers may push for stricter security measures and on-chain fraud detection in exchanges.
- The leak's impact extends beyond ordinary account access to direct financial harm.
- Immediate action is crucial to mitigate risks posed by the leaked data.
- Experts emphasize the need for strong, unique passwords and enhanced security measures for crypto assets.
Read Full Article
7 Likes
TechBullion
148

Image Credit: TechBullion
Bhanu Prakash Reddy Mettu: Cybersecurity Leader and Strategic Advisor Driving Transformation in the Digital Age
- Bhanu Prakash Reddy Mettu is a cybersecurity leader and strategic advisor at Verizon Business Group, with over 15 years of experience in shaping digital security strategies for global enterprises.
- Mettu guides Fortune 500 companies across various industries through transformative security journeys, aligning security programs with evolving cyber threat landscapes.
- He holds a Bachelor's degree in Electrical and Electronics Engineering and a Master of Science in Information Systems, providing him a dual perspective on infrastructure and data ecosystems.
- Mettu started his career at RSA Security, contributing to transforming the enVision platform into a market-leading product and supporting RSA's recognition in Gartner's SIEM Magic Quadrant.
- He later advanced to leadership roles in incident response and network forensics at KPMG before joining Verizon Business Group.
- In his role at Verizon, Mettu spearheaded projects that modernized cyber resilience for major organizations, including migrating security systems to Managed Detection and Response models and forming cybersecurity teams for multinational conglomerates.
- Known for his precision, collaboration, and strategic foresight, Mettu crafts tailored security roadmaps by immersing himself in client environments, integrating teams, and communicating risks effectively.
- Mettu's influence is evident in projects like leading the establishment of a region-wide cybersecurity team for a Japanese conglomerate and advising a transportation giant on advanced threat modeling and detection strategies.
- His work has led to tangible outcomes, such as enhancing threat visibility for a British manufacturer transitioning to a Verizon MDR solution and improving operational efficiency post-merger between two healthcare entities.
- Mettu has earned accolades at Verizon for his excellence, with spotlight awards recognizing his commitment to delivering value and impact.
- His certifications, including CISSP, GPEN, GWAPT, affirm his expertise at the intersection of academic rigor and applied innovation in cybersecurity.
- Mettu envisions proactive defense models driven by AI, unified SOCs, and scalable frameworks to adapt to sector-specific risks, aiming to shape the future of digital defense.
- Through his combination of hands-on expertise and strategic advisory skills, Bhanu Mettu is safeguarding organizations against modern threats and architecting the next generation of cyber resilience.
Read Full Article
8 Likes
Securityaffairs
109

Image Credit: Securityaffairs
A ransomware attack pushed the German napkin firm Fasana into insolvency
- A ransomware attack has pushed the German napkin firm Fasana into insolvency, exacerbating its financial troubles.
- The cyberattack occurred on May 19, shutting down Fasana's systems and causing a halt in orders worth over €250K the next day.
- Fasana, located in Stotzheim, Germany, with 240 employees, had to cease production and postpone May salaries.
- The company estimates a €2 million loss within two weeks of the cyberattack and is now seeking a new buyer after being acquired in March.
- The attack rendered Fasana incapable of printing delivery notes, leading to a complete paralysis of business operations.
- The insolvency administrator Maike Krebber highlighted the severe consequences of the cyberattack on Fasana and its employees.
- The ransomware attack by an unidentified group encrypted files and locked Fasana's systems, but no gang has claimed responsibility.
- Although the hackers sought financial gain, the exact method of their entry remains unclear.
- Operations have resumed, and deliveries and invoicing restarted the prior week.
- Reportedly, a known police-monitored group was involved in sending ransomware to Fasana's systems.
- The malware circulated rapidly, locking data until a ransom was paid, with printers displaying extortion messages during the attack.
- No ransomware group has officially admitted to the cyberattack as of now.
- Fasana is under pressure to find a buyer within eight weeks as it looks to recover from the insolvency caused by the ransomware attack.
Read Full Article
6 Likes
VoIP
271

Image Credit: VoIP
Digicel and Symptai Unite to Boost Caribbean Business Solutions
- Digicel Group and Symptai Consulting have partnered to enhance business solutions in the Caribbean.
- Symptai, known for technology advisory and cybersecurity services, will broaden Digicel's offerings.
- Liam Donnelly of Digicel sees the partnership as strengthening capabilities in cybersecurity and digital transformation.
- Symptai's CEO, Marlon Cooper, values Digicel's resources and ability to serve businesses of all sizes.
- The collaboration between Digicel and Symptai aims to improve services and reach businesses across the Caribbean.
- The unified approach seeks to empower Caribbean companies for global competitiveness in the digital landscape.
Read Full Article
16 Likes
Dev
271

Image Credit: Dev
Ollama Exposed: Unauthenticated Access Vulnerability Could Leak Your LLM Models
- Ollama is an open-source toolkit for large language models, but an unauthenticated access vulnerability on the default port 11434 can expose sensitive API endpoints to the public internet.
- The vulnerability allows attackers to access private models, cause resource abuse, or even execute remote code, posing serious risks like data theft and server compromise.
- Changing Ollama's default settings to enable remote access without authentication can lead to significant security flaws, including the CVE-2024-37032 path traversal issue for remote code execution.
- Mitigation steps include restricting public access, implementing access control via firewall rules or a reverse proxy like NGINX with basic auth, and updating to fixed versions like v0.1.34.
- All Ollama versions are vulnerable if exposed to 0.0.0.0 without authentication, with related flaws addressed in v0.1.34. The issue has been observed being exploited in real-world scenarios.
Read Full Article
16 Likes
Dev
333

Image Credit: Dev
Day 11 : FastAPI Auth: Login with JWT & Route Protection
- Day 11 of the FastAPI Zero to Hero series covers authentication and route protection, essential for a production-ready app.
- Authentication is crucial to prevent unauthorized access to sensitive data and actions.
- Topics covered include Basic Auth vs OAuth2 Password Flow, JWT (JSON Web Token) usage, login endpoint creation, and route protection.
- Basic Auth sends username and password with every request, while OAuth2 Password Flow issues JWT tokens for subsequent requests.
- JWT is a self-contained token with user data, expiry time, and issuer information signed for server verification.
- Libraries like python-jose handle JWT encoding, decoding, and verification, while passlib with bcrypt ensures secure password hashing.
- The project structure includes main.py for app definition, /token login route, /dashboard protected route, and auth.py for JWT utility functions.
- The article provides code snippets for creating access tokens, decoding tokens, user authentication, and protecting routes using JWT tokens in FastAPI.
- Steps to run the app locally with Uvicorn, access Swagger UI for testing endpoints, and authentication flow testing are outlined.
- By understanding these concepts, you can build a robust authentication system in FastAPI for securing APIs.
Read Full Article
20 Likes
Moneyweb
320

Construction mafia won’t derail Acsa’s R22bn infrastructure build – CEO
- Acsa is taking secrecy measures to protect its R21.7 billion infrastructure programme from the 'construction mafia.'
- Briefings are being held across South Africa to address risks and precautions regarding public project information.
- Concerns raised about how the construction mafia gains access to Acsa properties.
- There are amendments in place to prevent disclosing project costs due to security threats.
- Acsa's infrastructure budget emphasizes maintenance, refurbishment, and new capacity.
- Mpofu highlighted challenges faced during the pandemic and the subsequent recovery.
- Acsa aims to restore public confidence by sharing project timelines and improved customer experiences.
- Collaboration with Air Traffic and Navigation Services to address air traffic control issues.
- Jet fuel supply problems emerged after a refinery shutdown, impacting Acsa's operations.
- Maintenance projects at OR Tambo and Cape Town International airports include various upgrades and improvements.
Read Full Article
19 Likes
Medium
135

Image Credit: Medium
Decoding the Oracle Cloud-Health Attack: Did legacy gateways expose medical records for millions?
- The article explores the potential connection between the breach of Oracle Cloud login servers and the theft of Protected Health Information (PHI) from Oracle Health/Cerner, impacting millions of patient records.
- Credentials for subdomains related to 'cerner.com' were compromised, allowing access to sensitive patient information across healthcare providers.
- The report suggests a 'chain attack' scenario penetrating Oracle Cloud servers for breaching Oracle Health/Cerner servers, emphasizing the need for further investigation.
- Pre-Authentication Remote Code Execution (RCE) on Oracle Cloud login servers facilitated data exfiltration by threat actors.
- The breach highlights concerns about Oracle's legacy Fusion Middleware and the vulnerabilities it poses in cloud-native platforms.
- The incident signifies the critical importance of timely and transparent communication from organizations to address sophisticated cyber threats effectively.
- The potential shift to open source EHR systems like OpenEMR and Ottehr is recommended for enhanced security and interoperability in healthcare settings.
- Ottehr, a newly introduced open source EHR, is highlighted as a promising solution with scalability and modern technologies to support millions of patient visits.
- The article underscores the need for healthcare providers to consider migrating to modern cloud-native architectures to mitigate risks associated with legacy systems.
- The interconnectedness of Oracle's legacy systems and AI-driven cyber threats pose significant challenges, necessitating a shift towards more secure platforms.
- Overall, the incident serves as a wakeup call for improving cybersecurity measures within the healthcare industry and promoting open source solutions for enhanced data protection.
Read Full Article
8 Likes
Medium
407

Image Credit: Medium
Silent Guardians: Advanced Threat Hunting in Critical Infrastructure
- Critical infrastructure, vital for our world, faces growing cyber threats targeting life-sustaining systems.
- Passive defense strategies are insufficient against sophisticated adversaries.
- Threat hunters play a crucial role in proactively identifying and thwarting attacks.
- Key drivers include creativity and precision in threat hunting.
- Techniques such as Time Drift Detection and Firmware Integrity Validation are deployed.
- ICS Command Frequency Heatmaps and Out-of-Band Wireless Scanning are used to detect anomalies.
- USB Device Traps are employed to identify insider threats or malicious activities.
- Threat hunting in critical infrastructure is a multi-tiered strategy to protect lives.
- ICS threat hunters are more than technicians - they are strategists and scientists.
- Global policy should mandate proactive threat detection in infrastructure.
- Threat hunters face challenges in ICS/OT environments and play a vital role in defending civilization.
Read Full Article
24 Likes
Siliconangle
315

Image Credit: Siliconangle
Security researchers find 16B stolen credentials from malware in open cloud storage
- Security researchers at Cybernews have discovered 16 billion stolen login credentials from about 30 different datasets, mainly comprised of data harvested by infostealer malware.
- The credentials were found exposed in unsecured cloud storage instances and Elasticsearch repositories, not stemming from a single major data breach.
- The data likely includes duplicate entries and reused passwords, impacting a substantial but smaller number of unique individuals.
- The freshness of the harvested credentials poses a significant threat, as they are likely still valid for cyberattacks like credential stuffing and phishing.
- These credentials were obtained from compromised devices infected with malware via phishing emails, malicious downloads, or cracked software.
- Unlike traditional breaches, these credentials did not come from direct compromises of major platforms but from infected users whose data was exposed in insecure storage.
- Although the 16 billion records are worrying, they are different from the largest known breach 'Mother of All Breaches' disclosed in early 2024, which contained over 26 billion records in one dataset.
- While the new credentials are of smaller absolute numbers and not in one dataset, their recency and organization make them particularly dangerous for cyberattacks.
- The well-organized and tailored data structure enables immediate use in cybercriminal activities, raising concerns for widespread account takeovers.
- The exposed databases were removed after Cybernews reported them, but the data might have been downloaded and redistributed by others during the exposure period.
- The discovery highlights the potential for attackers to exploit cloud services and SaaS platforms, bypassing traditional security measures with ease.
Read Full Article
18 Likes
Tech Radar
74

Image Credit: Tech Radar
WordPress hackers are teaming up with commercial adtech firms to distribute malware to millions of users - here's how to stay safe
- Recent investigations have uncovered an alliance between WordPress hackers and adtech firms for distributing malware globally.
- VexTrio, a traffic distribution system, serves as a key player rerouting users through deceptive ads and push notifications.
- Commercial companies like Los Pollos, Partners House, and RichAds are implicated in this malicious network.
- Los Pollos' ties to VexTrio were highlighted in Russian disinformation campaigns.
- Malicious activities persisted post Los Pollos' shutdown as attackers shifted to a new TDS called Help, linked back to VexTrio.
- WordPress vulnerabilities were exploited for malware campaigns using DNS TXT records for malicious redirects.
- Multiple malware strains shared infrastructure patterns leading to VexTrio or its proxies.
- Adtech platforms embed malicious scripts deterring browser controls and luring users with fake sweepstakes.
- Hackers leverage fake CAPTCHA prompts to trick users into enabling push notifications for phishing and malware links.
- Users are advised to avoid suspicious alerts, use ZTNA tools, update WordPress, and monitor DNS for anomalies.
- Adtech firms hold the power to shut down these operations.
- Users must stay cautious to mitigate risks associated with malware distribution.
- Security measures like ZTNA and WordPress updates are crucial to prevent compromises.
- Adtech companies could play a vital role in dismantling such operations.
- Users need to be vigilant against fake CAPTCHA prompts and suspicious browser alerts.
- Preventive measures include monitoring DNS activities and relying on ZTNA tools.
- The overlap between different adtech platforms complicates attribution and detection.
Read Full Article
4 Likes
Samsung
407

Your Privacy, Secured: How Galaxy AI Protects Privacy With Samsung Knox Vault
- Samsung Electronics ensures privacy and security for Galaxy devices through the multi-layered Samsung Knox Matrix approach.
- Samsung Knox Vault, a hardware-based security solution, safeguards sensitive information on Galaxy devices.
- Knox Vault creates a physical barrier with its own processor and memory to encrypt and protect personal data.
- It isolates private information such as passwords, PINs, biometrics, and financial details.
- With AI integration in devices, concerns also include data privacy, which Knox Vault addresses by securely storing personal data.
- Galaxy AI processes data directly on-device to maintain privacy and security, like with the Audio Eraser and Call Transcript functions.
- Knox Vault ensures user data is confidential, protected, and safe from physical or remote tampering.
- The hardware-level security of Knox Vault is crucial as AI becomes more integrated into daily user experiences.
- Samsung's Knox Vault promises to secure user privacy as devices advance and AI technology evolves.
- Galaxy AI learns from user behavior to offer personalized experiences while respecting data privacy.
- AI needs personal data for tailored experiences, making Knox Vault vital in safeguarding sensitive information.
- Knox Vault's role in securing privacy will expand as Samsung integrates AI further into their ecosystem.
- The security feature of Knox Vault helps prevent unauthorized access to personal and confidential information.
- Knox Vault's protection extends to various AI features like Call Transcript and Audio Eraser, ensuring data remains private and secure.
- Samsung emphasizes the importance of user privacy with Knox Vault in the era of advanced devices and evolving AI technology.
- Knox Vault operates silently in the background, ensuring data security while users go about their daily tasks.
- Samsung's Knox Vault is fundamental in maintaining data privacy and security as AI becomes more integrated into devices.
Read Full Article
24 Likes
Securityaffairs
355
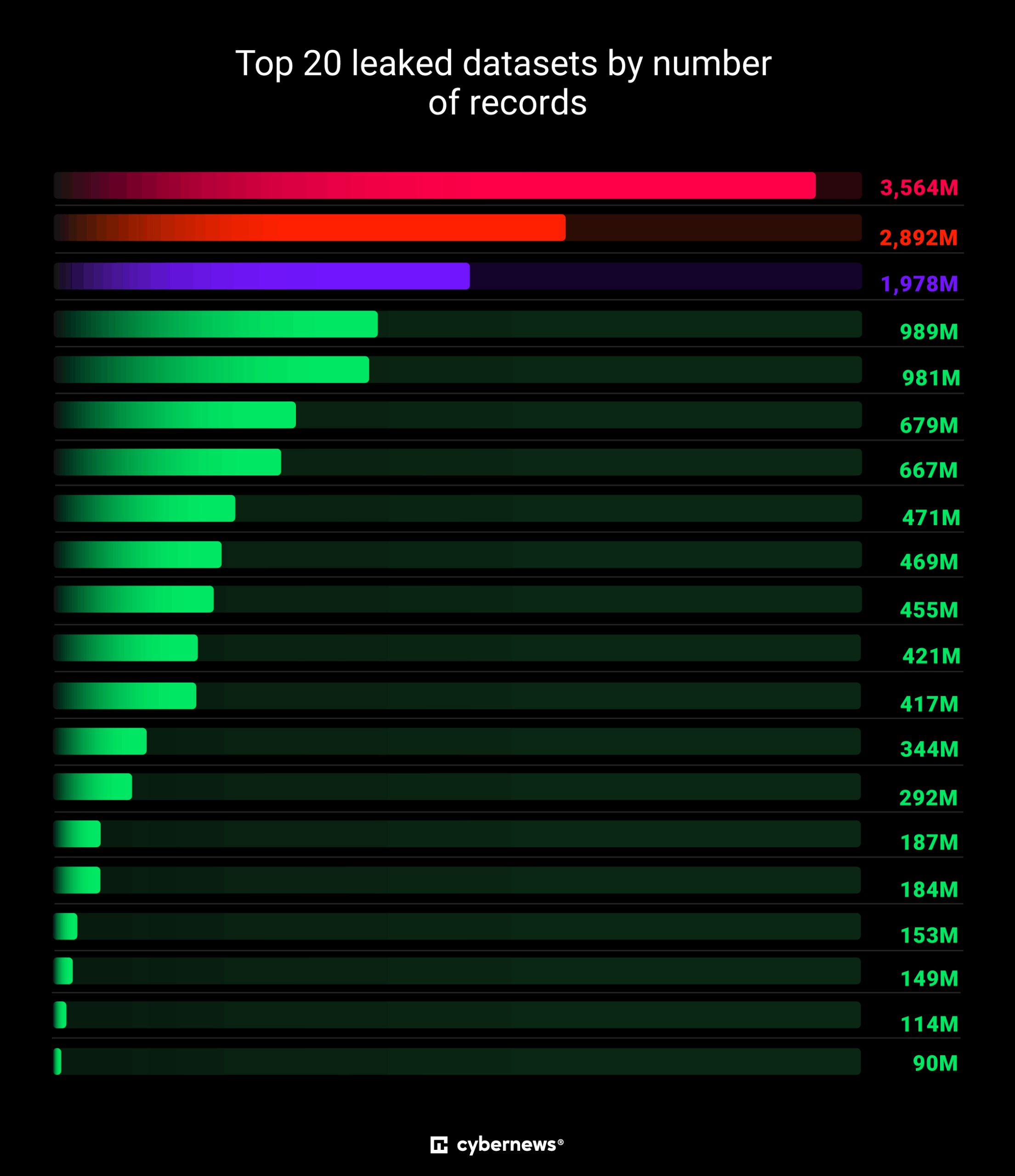
Image Credit: Securityaffairs
Researchers discovered the largest data breach ever, exposing 16 billion login credentials
- Researchers discovered the largest data breach ever, exposing 16 billion login credentials likely due to multiple infostealers.
- The discovery of the data breach, consisting of 30 massive leaked datasets totaling 16 billion exposed login records, was announced by Cybernews researchers.
- Most of the leaked datasets were newly discovered, with infostealer malware being widespread as alarming new leaks continue to surface.
- The exposed data was briefly accessible, mainly on unsecured Elasticsearch or storage instances, making it a blueprint for mass exploitation.
- The leaked data includes 16 million to 3.5 billion records targeting services like Apple, Google, Facebook, Telegram, GitHub, and government portals.
- The data likely gathered by infostealers includes tokens, cookies, and sensitive metadata, posing significant risks for phishing, ransomware, and account takeovers.
- In 2024, CyberNews also uncovered the largest password compilation called RockYou2024 containing almost 10 billion unique plaintext passwords.
- RockYou2024 is an expansion of the RockYou2021 collection discovered in 2021, hinting at a massive collection of passwords from old and new data breaches.
Read Full Article
21 Likes
TechJuice
276

Image Credit: TechJuice
Google, Apple, Meta’s18bn Passwords leaked! Do this now to Secure your account
- Cybersecurity researchers discover 30 exposed datasets with 18 billion login credentials, involving major tech giants like Google, Apple, Meta, and YouTube.
- The exposed data includes information from infostealer malware, credential stuffing sets, and repackaged leaks, posing a significant threat to online security.
- Exposed records include service URLs, login details, and passwords, making them directly usable for unauthorized access.
- Researchers highlight the continuous and evolving threat posed by these datasets.
- The presence of tokens, cookies, and metadata in the data allows attackers to bypass security measures and gather deeper insights into user accounts.
- The risk of account takeover is increased significantly due to widespread credential exposure.
- Proactive steps to secure online accounts include changing passwords, using strong and unique passwords, enabling MFA, monitoring accounts, being wary of phishing, and checking for compromise.
- Services like 'Have I Been Pwned?' can help users check if their email addresses or phone numbers have been involved in data breaches.
- Constant vigilance and strong cybersecurity practices are crucial in combating threats like infostealer malware.
Read Full Article
16 Likes
For uninterrupted reading, download the app